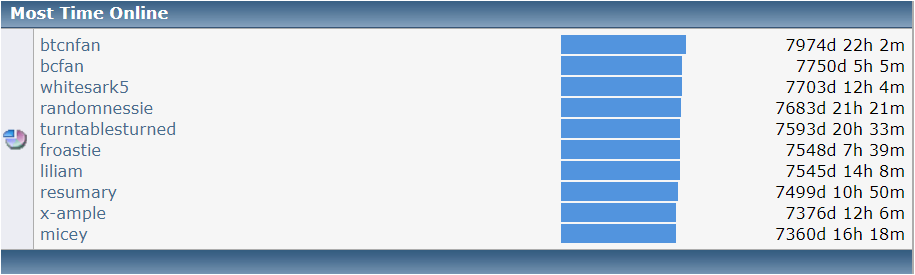
Earlier Bitcoin Wallet used to be a bunch of private keys. In order to use new address, user had to generate new private key which made the whole process cumbersome because user had to backup each and every private key. Hierarchical Deterministic (HD) wallet made the process easier. Deterministic wallet means the wallet uses a single starting point to derive all the addresses. That single starting point is known as 'mnemonic seed' or 'seed phrase'. Today, more than 95% non-custodial wallets generate addresses deterministically and if they aren't, you shouldn't be using those wallets.
Considering that the seed phrase has become integral part of Bitcoin Wallet, I will explain the whole process on how bitcoin addresses are derived from seed phrase along-with Javascript code so you can easily test the process in your computer without downloading or installing any utility.
Table of Contents1. Generate Random Sequence or Entropy2. Create Checksum and Prepare Final Sequence3. Convert Sequence into Mnemonic Codes4. PBKDF2 Key-Stretching Function5. Master Private Key, Master Public Key and Chain Code6. Derivation Path and BIP-447. Child Private Key Derivation8. Generate Bitcoin Addresses from Private Keys9. Javascript Codes1. Generate Random Sequence or Entropy
Earlier I said that the mnemonic (or seed phrase) is the starting point of the wallet which may not be entirely true. In order to derive mnemonic, we first need to generate entropy. In easier words, entropy is nothing but the measure of randomness. In order to secure wallet, we need it to be based on something unpredictable, hence entropy of 128-256 bits is used. The easiest way to generate entropy is by flipping the coin. Take a coin and toss it 128 times, write 0 when heads come while write 1 when tails come. After 128 flips, you will have the random sequence of 0s and 1s which is your entropy. You can do the same 256 times to increase the security of your wallet (longer the entropy, higher the security). Check the image below to understand the process better:

The 0 and 1 sequence you see above is the distinct point. This should be generated as random as possible. If weak random generator is used then hackers can easily brute-force your sequence and steal the funds.
2. Create Checksum and Prepare Final Sequence
Now, as we have the 128-bit entropy, we need to generate checksum. Checksum is nothing but a fingerprint attached at the end of something to ensure user has made no mistake is copying that thing. In our case, we will generate fingerprint of our entropy. As defined in BIP-39, we take SHA-256 hash of the entropy as the fingerprint. Before moving forward, let's convert our entropy from Base2 to Base16 or hexadecimal. Base2 means we use 2 symbols to express our number, as we saw in Step 1, those numbes are '0' and '1'. Similarly, Base16 (or hexadecimal) uses 16 symbols to express the number, those are: 0,1,2,3,4,5,6,7,8,9,a,b,c,d,e,f. Check the image below to understand how conversion works:

You can see that 0001 in Base2 is equal to 1 in hexadecimal, 0010 is equal to 2 and so on. So, our entropy in hexadecimal is represented as 91d3785bf884c639f600b3e587083265. But important point here is that both are same, just representation is different.
Back to checksum now, like I said earlier, SHA-256 of the entropy is used as checksum, let's generate the SHA-256 of our entropy:
SHA-256 hash of 0x91d3785bf884c639f600b3e587083265 = effdb98e4c4ac27c670f704c39a2e0ba8b85bc4561a7a02a6297e465ed155d30
The hash is 256-bit long number represented by 64 hexadecimal characters. In other words, each hexadecimal character represents 4 bits. As per BIP-39, instead using the whole hash, only first (entropy length / 32) bits of the hash are used as checksum. In our case, the length of entropy is 128 which when divided by 32 gives 4. So, we will only take first four bits of the hash as checksum. If the length of your entropy is 256, checksum would be 256/32 or first 8 bits of the hash.
As I said earlier, each hexadecimal character represents four bits, the first four bits of our hash in hexadecimal are represented by 'e'. So, our checksum is 'e' in hexadecimal and 1110 in Base2 (or binary). Now, we append checksum at the end of the sequence which will make our final sequence in hexadecimal as, 0x91d3785bf884c639f600b3e587083265e. Or in Base2 as:
3. Convert Sequence into Mnemonic Codes
Now the length of the sequence is 132 bits. Next step involves splitting the sequence into the chunk of 11 bits. Since, our sequence is of 132 which when divided by 11 gives 12, so we will get 12 chunks. We will get 24 chunks if 256-bit entropy is used.
Here are the chunks of our entropy:
10010001110
10011011110
00010110111
11110001000
01001100011
00011100111
11011000000
00010110011
11100101100
00111000010
00001100100
11001011110
As you can notice, each chunk is a binary number. The lowest value of the chunk can be 00000000000 which is 0 in decimal. Whereas, maximum value can be 11111111111 which is 2047 in decimal. So, each chunk is valued between 0-2047. BIP-39 defined 2048 words, each word representing one number from 0 to 2047. I have prepared a table so you can see which word is used for which value, visit the link below to view the table:
From the table, you can see that the decimal values of our chunks are: 1166, 1246, 183, 1928, 611, 231, 1728, 179, 1836, 450, 100, 1630
Picking the adjacent words from the link, we got the following mnemonic code:
mushroom orange black valve erase brother submit biology tortoise debate arrive slim
4. PBKDF2 Key-Stretching Function
Password-based Key Derivation Function 2 (or PBKDF2) is used as a security measure in the process. This function allows the use of 'passphrase' to further increase the security of our mnemonic code. You can read more about PBKDF2 function on:
Wikipedia.
In our bitcoin address derivation process, PBKDF2 is used to stretch mnemonic code by using 2048 rounds of HMAC-SHA512 algorithm. The algorithm takes two parameters, one is mnemonic code and second is salt. If user decides to opt for no passphrase then salt is the string with the value - 'mnemonic'. But, if user decides, let say, 'webby' as the passphrase. Then, salt will become- 'mnemonicwebby'. We concat passphrase at the end of 'mnemonic' string in salt.
Hence, our PBKDF2 function will become:
DK = PBKDF2(PRF, Password, Salt, c, dkLen)
Putting value for: PRF, Password, Salt, c and dkLen:
DK = PBKDF2(HMAC, 'mushroom orange black valve erase brother submit biology tortoise debate arrive slim', 'mnemonic', 2048, 64)
where, PRF is pseudorandom function (here HMAC)
Password is our mnemonic code
Salt is string 'mnemonic' without any passphrase
c is the number of iteration. In our case, 2048
dkLen is the desired length of derived key (we want 512-bit seed so we selected 64 byte since 1 byte = 8 bits)
DK refers to the final key or seed we derived from the process. In our case, we will get 512-bit value as the result. The key for our mnemonic code with no passphrase is:
65729d81d461591bac7384dea43dbd44438053cd1fdc113e0769c49c5fde025ba331eed2077497634e619948437d0448e769a86c0cbbecf01b13fd53540743b3
5. Master Private Key, Master Public Key and Chain Code
As I discussed in the starting of the thread, the main purpose of using seed phrase is to get hierarchical tree like structure, where each private or public key is derived from its parent and can derive its children. Master Private Key is the top of the hierarchy. It is a private key at first level with no parent.
We have generated DK or 512-bit seed in the last step. This seed will now be used in HMAC-SHA512 function to derive private key and chain code. HMAC-SHA512 function takes two parameters - message and secret key. In our case, 512-bit seed from the last step is message and as defined in BIP-32, string 'Bitcoin seed' is used as secret key. So,
HMAC(seed, 'Bitcoin seed') = Hash
The resulting hash will be a 512-bit value. In our case, it is the following:
a0ccf14c939faa07b896cd5fb306a37fb3f9cb041196c5364d0cca9dbd82e53a5bc9d1368631ae579f02ed8e46a56dd9dd9de8ac59e3c4e18247ff96988bdf1f
Note that the length of the output is 512 bits or 128 hexadecimal characters. The first 256 bits (represented by the first 64 hexadecimal characters) will become our Master Private Key whereas next 256 bits will become our Chain Code.
Hence,
Master Private Key: a0ccf14c939faa07b896cd5fb306a37fb3f9cb041196c5364d0cca9dbd82e53a
Chain Code: 5bc9d1368631ae579f02ed8e46a56dd9dd9de8ac59e3c4e18247ff96988bdf1f
Master Public Key can be derived from Master Private Key using Elliptic Curve Cryptography. I have written detailed thread on ECC. You can follow this thread:
THE THREAD and see how public key is derived from private key. Process is same for the Master Public Key as well.
Using the same logic,
our Master Public Key: 03d1cc1f6bdea4d17eb7f2573d676f9ddb087f8b784c912c4466407781d8acfe38
6. Derivation Path and BIP-44
To easily understand the meaning of derivation path, you can assume it as a map which guides us how should be go through the children from the master private key to finally reach the bitcoin address. BIP-44 defines the following path for Bitcoin Mainnet:
Path format: m / purpose' / coin_type' / account' / change / address_index
Bitcoin Main-net format: m / 44' / 0' / 0' / 0 / address_index
To understand the above, first look at the image below:
It's like we will go to the master private key and ask, who is your 45th hardened child. Then we will go to the 45th child and ask it, who is your first hardened child. Then we will go to the first hardened child of the first hardened child of the master private key and ask it who is your first child. Then we will go and catch the first child and take its children one-by-one as our private keys. First child will become our first private key which will be used to derive our first bitcoin address and so on.
Now you maybe wondering what's the difference between hardened child and normal child. When we say first hardened child, it's actually (2
31+1)th child. For easy understanding, we replace 2
31 and use the symbol of prime ( ' ). So, 2
31+1 or 2147483649th child of the parent is first hardened or 0' child. (Notice the sign of prime at the right top of 0)
For more serious discussion about Derivation Path, check this thread from Blue Snow:
https://bitcointalk.org/index.php?topic=52433507. Child Private Key Derivation
Okay, now as we know which child keys are to be derived, let's see how child key is derived:
To derive the child key, again HMAC-SHA512 hashing algorithm is used. As we discussed earlier, HMAC-SHA512 algorithm requires 2 params - message and secret key. Here, message is our master private or public key concatenated with the child number (also known as child index) and secret key is the chain code. So,
Hash = HMAC(master key + index, chain code)
Important Point: When we are deriving hardened child, master private key will be used as message. Whereas, master public key will be used in case we are deriving normal child.
Now let's get started with the process:
LEVEL 1: Deriving 45th hardened child of the Master Key (Since it's hardened, Master Private Key will be used)Master Private Key = a0ccf14c939faa07b896cd5fb306a37fb3f9cb041196c5364d0cca9dbd82e53a (taken from the fifth step)
Index = 8000002c (value of 2147483692 i.e. 2^31+44 in hexadecimal)
Chain Code = 5bc9d1368631ae579f02ed8e46a56dd9dd9de8ac59e3c4e18247ff96988bdf1f (taken from the fifth step)
So,
Message = 00a0ccf14c939faa07b896cd5fb306a37fb3f9cb041196c5364d0cca9dbd82e53a8000002c
(important thing to notice here, the length of message should be 296 bits. Since, the length of master private key is 256 bits and index is 32 bits,
we need additional 8 bits, hence we added 00 i.e. 8 empty bits in the starting)
Key = 5bc9d1368631ae579f02ed8e46a56dd9dd9de8ac59e3c4e18247ff96988bdf1f
HMAC(message, key) = 7fc9ce32a6aeffbeaf5057f266f0d6ed6383ed84f21c96d53c0c1e3838a87e2481d4b120fcd3a11837e5d035fc508bb8b31c47285fdd7506d8d264144b4d8df7
Note, we got the output of 512 bits. Similar to what we discussed in fifth step, the left 256 bits of the output will be used for the private key of our 45th hardened child and right 256 bits will become the chain code of the child. The left 256 bits are assumed as a hexadecimal number and added to the parent private key. Then we take the modulus of the addition with 'n' parameter as defined by SECG in this document:
SECG Vol 2Left 256 bits = 7fc9ce32a6aeffbeaf5057f266f0d6ed6383ed84f21c96d53c0c1e3838a87e24
Parent Private Key = a0ccf14c939faa07b896cd5fb306a37fb3f9cb041196c5364d0cca9dbd82e53a
N = FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFEBAAEDCE6AF48A03BBFD25E8CD0364141 (n as defined)
Private Key of 45th Hardened Child of Master Private Key = ( Left 256 bits + Parent Private Key ) % N
Private Key of 45th Hardened Child of Master Private Key = 2096bf7f3a4ea9c667e7255219f77a6e5ccedba2546abbcfc9468a4925f5221d
Chain Code of 45th Hardened Child of Master Private Key = 81d4b120fcd3a11837e5d035fc508bb8b31c47285fdd7506d8d264144b4d8df7 (right 256 bits)
Private Key = 2096bf7f3a4ea9c667e7255219f77a6e5ccedba2546abbcfc9468a4925f5221d
Index = 80000000 (value of 2147483648 i.e. 2^31 in hexadecimal)
Chain Code = 81d4b120fcd3a11837e5d035fc508bb8b31c47285fdd7506d8d264144b4d8df7
So,
Message = 002096bf7f3a4ea9c667e7255219f77a6e5ccedba2546abbcfc9468a4925f5221d80000000
Key = 81d4b120fcd3a11837e5d035fc508bb8b31c47285fdd7506d8d264144b4d8df7
HMAC(message, key) = dee4c4cb625b27f231194cf3befea6e67a73122f77a748b987fded5333ca63f7d665636fd64693411687f8d4deeb8382d14deb3d9937e72635e77af48c4da4e6
Left 256 bits = dee4c4cb625b27f231194cf3befea6e67a73122f77a748b987fded5333ca63f7
Parent Private Key = 2096bf7f3a4ea9c667e7255219f77a6e5ccedba2546abbcfc9468a4925f5221d
N = FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFEBAAEDCE6AF48A03BBFD25E8CD0364141 (n as defined)
Private Key of first hardened child of Level 1 Child = ( Left 256 bits + Parent Private Key ) % N
Private Key of first hardened child of Level 1 Child = ff7b844a9ca9d1b899007245d8f62154d741edd1cc1204895144779c59bf8614
Chain Code of first hardened child of Level 1 Child: d665636fd64693411687f8d4deeb8382d14deb3d9937e72635e77af48c4da4e6
Private Key = ff7b844a9ca9d1b899007245d8f62154d741edd1cc1204895144779c59bf8614
Index = 80000000 (value of 2147483648 i.e. 2^31 in hexadecimal)
Chain Code = d665636fd64693411687f8d4deeb8382d14deb3d9937e72635e77af48c4da4e6
So,
Message = 00ff7b844a9ca9d1b899007245d8f62154d741edd1cc1204895144779c59bf861480000000
Key = d665636fd64693411687f8d4deeb8382d14deb3d9937e72635e77af48c4da4e6
HMAC(message, key) = 2839a8f276409794544cdc9f4d2748a3ea3ca988b64f82e72414d67dedaf751bfb106a1896e38ddc80b3d3b4fdaba9b003d1e6caa08c6cbbdc5d63fa6836b613
Left 256 bits = 2839a8f276409794544cdc9f4d2748a3ea3ca988b64f82e72414d67dedaf751b
Parent Private Key = ff7b844a9ca9d1b899007245d8f62154d741edd1cc1204895144779c59bf8614
N = FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFEBAAEDCE6AF48A03BBFD25E8CD0364141 (n as defined)
Private Key of first hardened child of Level 2 Child = ( Left 256 bits + Parent Private Key ) % N
Private Key of first hardened child of Level 2 Child = 27b52d3d12ea694ced4d4ee5261d69fa06cfba73d318e734b586ef8d7738b9ee
Chain Code of first hardened child of Level 2 Child: fb106a1896e38ddc80b3d3b4fdaba9b003d1e6caa08c6cbbdc5d63fa6836b613
Private Key = 27b52d3d12ea694ced4d4ee5261d69fa06cfba73d318e734b586ef8d7738b9ee
Public Key = 03fc371a6939557697a438cca5c81fc899d611d41f605d1b6d1a8096fd5e3e0343 (using ECC)
Index = 00000000 (value of 0 in hexadecimal)
Chain Code = fb106a1896e38ddc80b3d3b4fdaba9b003d1e6caa08c6cbbdc5d63fa6836b613
So,
Message = 03fc371a6939557697a438cca5c81fc899d611d41f605d1b6d1a8096fd5e3e034300000000
(Since we are using Public Key which is already of 264 bits, we needn't concat additional bits in the starting)
Key = fb106a1896e38ddc80b3d3b4fdaba9b003d1e6caa08c6cbbdc5d63fa6836b613
HMAC(message, key) = bd63f3fe2daf72bd61d983477a8330e377ecc1fa664bee4a90da90003de9ef8c29a2907541b35ab602c72d52c330184a2e7908060b98acca9b17ebfaea0135a8
Left 256 bits = bd63f3fe2daf72bd61d983477a8330e377ecc1fa664bee4a90da90003de9ef8c
Parent Private Key = 27b52d3d12ea694ced4d4ee5261d69fa06cfba73d318e734b586ef8d7738b9ee
N = FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFEBAAEDCE6AF48A03BBFD25E8CD0364141 (n as defined)
Private Key of first normal child of Level 3 Child = ( Left 256 bits + Parent Private Key ) % N
Private Key of first normal child of Level 3 Child = e519213b4099dc0a4f26d22ca0a09add7ebc7c6e3964d57f46617f8db522a97a
Chain Code of first hardened child of Level 3 Child: 29a2907541b35ab602c72d52c330184a2e7908060b98acca9b17ebfaea0135a8
Private Key = e519213b4099dc0a4f26d22ca0a09add7ebc7c6e3964d57f46617f8db522a97a
Public Key = 0321bd38eb2f97c56762b82f22e9677d6aa205a73664b93aaf8ed087bd9fc26420 (using ECC)
Index = 00000000, 00000001 and 00000002
Chain Code = 29a2907541b35ab602c72d52c330184a2e7908060b98acca9b17ebfaea0135a8
So,
Message1 = 0321bd38eb2f97c56762b82f22e9677d6aa205a73664b93aaf8ed087bd9fc2642000000000
Message2 = 0321bd38eb2f97c56762b82f22e9677d6aa205a73664b93aaf8ed087bd9fc2642000000001
Message3 = 0321bd38eb2f97c56762b82f22e9677d6aa205a73664b93aaf8ed087bd9fc2642000000002
Key = 29a2907541b35ab602c72d52c330184a2e7908060b98acca9b17ebfaea0135a8
HMAC(message1, key) = a8764acda4ebc575ff750e113353a805186febf32372deb4fab9ed180a7b4db3a3e1295ec9c664d73d77841b263d019306d914e431fdc84973cf53abaa0883cb
HMAC(message2, key) = fb58f1f53183d06aed97ba85ad30fc89d4500bb3c5d47880cc96c368f044618743a1580a9757af12b8597450ff8a5b37e9a51660b0a30e672b736464f4cdb7d0
HMAC(message3, key) = b30db2ea8ad0e61c43acf2052ecc0d3c174cf5a57655ba038ba8894f3bc2f0d8c140e5f51589c16e3d3502b08fc005e8a9acfa5a56dda2e08b520b3179c1f163
Left 256 bits of HMAC1 = a8764acda4ebc575ff750e113353a805186febf32372deb4fab9ed180a7b4db3
Left 256 bits of HMAC2 = fb58f1f53183d06aed97ba85ad30fc89d4500bb3c5d47880cc96c368f0446187
Left 256 bits of HMAC3 = b30db2ea8ad0e61c43acf2052ecc0d3c174cf5a57655ba038ba8894f3bc2f0d8
Parent Private Key = e519213b4099dc0a4f26d22ca0a09add7ebc7c6e3964d57f46617f8db522a97a
N = FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFEBAAEDCE6AF48A03BBFD25E8CD0364141 (n as defined)
Private Key of first normal child of Level 4 Child = 8d8f6c08e585a1804e9be03dd3f442e3dc7d8b7aad8f13f881490e18ef67b5ec (to be used for deriving first bitcoin address)
Private Key of second normal child of Level 4 Child = e0721330721dac753cbe8cb24dd19768985dab3b4ff0adc45325e469d530c9c0 (to be used for deriving second bitcoin address)
Private Key of third normal child of Level 4 Child = 9826d425cb6ac22692d3c431cf6ca81adb5a952d0071ef471237aa5020af5911 (to be used for deriving third bitcoin address)
8. Generate Bitcoin Addresses from Private Keys
In the last step, we derived 3 private keys at Level 5 using index 00000000, 00000001 and 00000002. If you want to derive more private keys in the hierarchy, just keep on incrementing index by 1. So, 00000003 will be used for next private key and so on. Also, remember that this is hexadecimal number so after 00000009, next index will be 0000000a, not 00000010.
Now, let's generate the bitcoin addresses from our private key. I have already created a thread explaining how to generate Legacy addresses (starting with '1') from private key in detail here:
How Bitcoin Addresses are generated? Understand the Math behind BitcoinYou can follow the above thread and you will be able to generate first 3 Legacy Bitcoin Addresses of the hierarchy using private keys from Step 7, which will be:
1MbJqqvN8ZPYsUch45HdRAxKbH6bJeGfZi
1GMpMNYwhb7Wvu8q1Zy52MtZUGWvLgCXak
12fv5eg3kzBgZQy7ue2yYmC9xXohmKWGR3
I will use the current thread to explain how to generate P2SH Address. P2SH is very different from the P2PKH (or Legacy) address. In Legacy address, we simply generate the hash of the public key and use it as the address. But in P2SH, we first create a script, then generate hash of the script. Then, transaction is made to the script. Now, script can literally be anything. Sender of the transaction don't have to know what does the script mean. Bitcoin has its own
scripting language and the script has defined many opcodes such as OP_ADD, OP_EQUAL and many more. So, I can literally create a script, let say, 'what when added to 3 makes 5'. Create hash of this script and use it as P2SH Address. Then the payment made to that P2SH address can be spent by providing original script i.e. 'what when added to 3 makes 5' and solution script i.e. '2' along with the hash.
P2SH can be used to create a lot more complex scripts but one of the most common type of P2SH is our P2WPKH-in-P2SH. It simply means using P2PKH in the P2SH script. This is the type of addresses you see while creating a wallet (the ones starting with '3'). Now, let's see, how are these created:
The scheme for P2WPKH-in-P2SH format is defined in BIP-49. In step 6, we discussed that the 45th hardened child of Master Private Key is used in the hierarchy. That's true for Legacy addresses but for P2WPKH-in-P2SH, we use the 50th hardened child, so, derivation path becomes:
m / 49' / 0' / 0' / 0 / address_index
Except this, rest of the process is same as discussed in Step 6 and 7. I have repeated the Step 7 with our Master Private Key, i.e. a0ccf14c939faa07b896cd5fb306a37fb3f9cb041196c5364d0cca9dbd82e53a and got the following three private keys as the first 3 normal child of m/49'/0'/0'/0 path i.e. Level 5:
Private Key of first normal child of Level 4 Child = 26e1061459e7961eeac018efa765339d785bd30de91f8fade64c639b275d74c4 (to be used for deriving first bitcoin address)
Private Key of second normal child of Level 4 Child = 501a42ccd834bf61c211f5277bcbebe4120eea952efc91fd71125f61a1e7eec4 (to be used for deriving second bitcoin address)
Private Key of third normal child of Level 4 Child = 13ae95a5d643b9ebe355d103679ad4bcf3863efef78873f4e4f20a57cf044a51 (to be used for deriving third bitcoin address)
Using ECC, I got the following Public Keys (second reminder, if you wanna know how public key is derived from private key, check out my thread I mentioned in Step 5):
Public Key of first normal child of Level 4 Child = 021549dd72d89cbc844bb74ab6247239cf60d184cbfb0cfc4d024150a4985412fe (to be used for deriving first bitcoin address)
Public Key of second normal child of Level 4 Child = 02e589abcbdbcf7b9746d1e2f5d97e5d2836c82b5910c5716f094801c0178ecfc2 (to be used for deriving second bitcoin address)
Public Key of third normal child of Level 4 Child = 020711fb2e08e67c13bcfb2cca60ff5ac3b7c6fb9e902722127ef776e5d2db6046 (to be used for deriving third bitcoin address)
First check the image below to understand how public key is converted into Bitcoin Address:

Now time for the explanation:
Firstly, we create SHA-256 hash of the public key:
SHA-256(public key) = Hash
SHA-256(021549dd72d89cbc844bb74ab6247239cf60d184cbfb0cfc4d024150a4985412fe) = 189a3015638daa02871973bf840b434aad92cb71775b65680acd266b81e85e3f
Then, we create ripemd160 hash of the sha256 hash:
RIPEMD160(hash) = Hash160
RIPEMD160(189a3015638daa02871973bf840b434aad92cb71775b65680acd266b81e85e3f) = 2bf545ff88c159408f5ba759f99e78566763fe1a
Then, we concat 0x0014 before the hash:
serialization = 0x0014 + Hash160
serialization = 00142bf545ff88c159408f5ba759f99e78566763fe1a
Note: 0x00 represent OP_0 and 0x14 is the size of the data to be pushed on stack in hexadecimal. Hence, OP_0 PushData<hash> represents our P2WPKH-P2SH script.
Now, as we have our script, next step involves creating hash of the script:
SHA-256(script) = Hash
SHA-256(00142bf545ff88c159408f5ba759f99e78566763fe1a) = c2d24e021347966656ed4b0312f9b3a49498c257294bd75e9bc84ba8353deb9a
Then,
RIPEMD160(hash) = Hash160
RIPEMD160(c2d24e021347966656ed4b0312f9b3a49498c257294bd75e9bc84ba8353deb9a) = 2d7193893e4143fc11bb69c7f004452198bdf6cd
Then add 0x05 before the hash160 i.e. encoding byte for script hash
serialization = 0x05 + Hash160
serialization = 052d7193893e4143fc11bb69c7f004452198bdf6cd
Creating checksum of the hash
checksum = first four bytes of SHA-256(SHA-256(hash))
SHA256(SHA256(052d7193893e4143fc11bb69c7f004452198bdf6cd)) = dcd3b30cd36dcef8265fbe414e435fc7841ced941f93ef86afd86e344c4a700e
First four bytes = dcd3b30c
Adding checksum at then end of hash and encoding it into Base58:
final serialization = 052d7193893e4143fc11bb69c7f004452198bdf6cddcd3b30c
Base58(052d7193893e4143fc11bb69c7f004452198bdf6cddcd3b30c) = 35qJPbZX23wt3uuB9nz4pxhoouUfG28zxB
Hence, 35qJPbZX23wt3uuB9nz4pxhoouUfG28zxB is our first Bitcoin Address in the hierarchy.









 Anyhow, it defeated the purpose of using different bitcoin receiving addresses when I am going to send most of it to the single exchange address. (privacy-killer)
Anyhow, it defeated the purpose of using different bitcoin receiving addresses when I am going to send most of it to the single exchange address. (privacy-killer)