brainless (OP)
Member
 
 Offline Offline
Activity: 316
Merit: 34

|
 |
April 22, 2021, 09:05:52 PM |
|
abc
023ef30130654689a64c864d6dd38760481c55fc525e2c6c7084e2d2d3d4d51be9
043ef30130654689a64c864d6dd38760481c55fc525e2c6c7084e2d2d3d4d51be9f7d86b288c09d db5311f292285168000e43e4b62201bd8de23a391daa8e00ce8
def
036a6e1dc6f203f7fdd97965892301e5fb995a37318c410543835f0edcd3456c49
046a6e1dc6f203f7fdd97965892301e5fb995a37318c410543835f0edcd3456c492a072b9898b93 e9eb05f9ad86a97546d83b579bf6efd3482f93baca13784496b
abcdef
0312faae608bd6562562b8f85564664cd1fdcd667f6b24b2b221ef86b9231f4d74
0412faae608bd6562562b8f85564664cd1fdcd667f6b24b2b221ef86b9231f4d74512ee8cd9b343 31afd05ccb8d81d1393c150c73ec5695845b731f7e6e0086719
here abc is 1 point, and 2nd point is def
if we can join or merge like abc add to def
where result would be abcdef point
abc+def = 18AB
one new func could be inside
like abc+def = abcdef
like point +point = pp ( line extended) ( not 2p)
point 1
point 2
a =1+2 = 3
more advance looking func
point 1
point 2
a =1+2 = 12
any ecc expert, can explain about this addition apply?
maybe it will called Point concatenate
|
13sXkWqtivcMtNGQpskD78iqsgVy9hcHLF
|
|
|
|
|
|
|
|
|
|
|
|
Even if you use Bitcoin through Tor, the way transactions are handled by the network makes anonymity difficult to achieve. Do not expect your transactions to be anonymous unless you really know what you're doing.
|
|
|
Advertised sites are not endorsed by the Bitcoin Forum. They may be unsafe, untrustworthy, or illegal in your jurisdiction.
|
NotATether
Legendary

 Offline Offline
Activity: 1596
Merit: 6726
bitcoincleanup.com / bitmixlist.org


|
 |
April 23, 2021, 06:37:12 AM |
|
See this thread. I quote a post from there: To get C = A + B, where A != B (in other words A and B must not be the same point. If that's the case, use point doubling instead):
- lambda = (By - Ay)/(Bx - Ax) (Note: no a term, even if the curve is not secp256k1!)
- Cx = lambda2 - Ax - Bx
- Cy = lambda*(Ax - Cx) - Ay
So point addition isn't concatenation or arithmetic addition, you simply take their uncompressed form, extract the X and Y values and perform the above operations on them and embed the X and Y result into an uncompressed point. Note: "abc" and "def" don't look like curve points, because they are just hex numbers with no X and Y value. |
.
.BLACKJACK ♠ FUN. | | | ███▄██████
██████████████▀
████████████
█████████████████
████████████████▄▄
░█████████████▀░▀▀
██████████████████
░██████████████
█████████████████▄
░██████████████▀
████████████
███████████████░██
██████████ | | CRYPTO CASINO &
SPORTS BETTING | | │ | | │ | ▄▄███████▄▄
▄███████████████▄
███████████████████
█████████████████████
███████████████████████
█████████████████████████
█████████████████████████
█████████████████████████
███████████████████████
█████████████████████
███████████████████
▀███████████████▀
███████████████████ | | .
|
|
|
|
|
MixMAx123
|
 |
April 23, 2021, 07:42:06 AM |
|
The points are coded like a public key:
abc A: 3ef30130654689a64c864d6dd38760481c55fc525e2c6c7084e2d2d3d4d51be9
abc B: f7d86b288c09ddb5311f292285168000e43e4b62201bd8de23a391daa8e00ce8
def A: 6a6e1dc6f203f7fdd97965892301e5fb995a37318c410543835f0edcd3456c49
def B: 2a072b9898b93e9eb05f9ad86a97546d83b579bf6efd3482f93baca13784496b
abc + def:
15cb9594ee936bd14b98139460879bee6f33b0f7c0ccb293825794d985f595be
aaad772a2ec81ab6013775e9edb274efe2e133e65e58949ac7f25429fb1bb152
|
|
|
|
|
brainless (OP)
Member
 
 Offline Offline
Activity: 316
Merit: 34

|
 |
April 23, 2021, 07:51:37 PM |
|
P + G = PG
hex prvkey is abc
x: 3ef30130654689a64c864d6dd38760481c55fc525e2c6c7084e2d2d3d4d51be9
y: f7d86b288c09ddb5311f292285168000e43e4b62201bd8de23a391daa8e00ce8
hex prvkey is def
x: 6a6e1dc6f203f7fdd97965892301e5fb995a37318c410543835f0edcd3456c49
y: 2a072b9898b93e9eb05f9ad86a97546d83b579bf6efd3482f93baca13784496b
result = hex prvkey is abcdef:
x: 12faae608bd6562562b8f85564664cd1fdcd667f6b24b2b221ef86b9231f4d74
y: 512ee8cd9b34331afd05ccb8d81d1393c150c73ec5695845b731f7e6e0086719
|
13sXkWqtivcMtNGQpskD78iqsgVy9hcHLF
|
|
|
brainless (OP)
Member
 
 Offline Offline
Activity: 316
Merit: 34

|
 |
April 25, 2021, 04:11:46 PM |
|
|
13sXkWqtivcMtNGQpskD78iqsgVy9hcHLF
|
|
|
NotATether
Legendary

 Offline Offline
Activity: 1596
Merit: 6726
bitcoincleanup.com / bitmixlist.org


|
 |
April 25, 2021, 04:44:37 PM |
|
The formulas in that post are for compressing an X,Y pair into an x- coordinate, and has nothing to do with point addition. I have already given the formula for that in my first post, and that's what I'm going to assume you used to derive your answer: x: 12faae608bd6562562b8f85564664cd1fdcd667f6b24b2b221ef86b9231f4d74
y: 512ee8cd9b34331afd05ccb8d81d1393c150c73ec5695845b731f7e6e0086719
|
.
.BLACKJACK ♠ FUN. | | | ███▄██████
██████████████▀
████████████
█████████████████
████████████████▄▄
░█████████████▀░▀▀
██████████████████
░██████████████
█████████████████▄
░██████████████▀
████████████
███████████████░██
██████████ | | CRYPTO CASINO &
SPORTS BETTING | | │ | | │ | ▄▄███████▄▄
▄███████████████▄
███████████████████
█████████████████████
███████████████████████
█████████████████████████
█████████████████████████
█████████████████████████
███████████████████████
█████████████████████
███████████████████
▀███████████████▀
███████████████████ | | .
|
|
|
|
brainless (OP)
Member
 
 Offline Offline
Activity: 316
Merit: 34

|
 |
April 25, 2021, 05:10:17 PM |
|
The formulas in that post are for compressing an X,Y pair into an x- coordinate, and has nothing to do with point addition. I have already given the formula for that in my first post, and that's what I'm going to assume you used to derive your answer: x: 12faae608bd6562562b8f85564664cd1fdcd667f6b24b2b221ef86b9231f4d74
y: 512ee8cd9b34331afd05ccb8d81d1393c150c73ec5695845b731f7e6e0086719
your formula if write in python, will help me to understand, kindly write python script, thankx |
13sXkWqtivcMtNGQpskD78iqsgVy9hcHLF
|
|
|
NotATether
Legendary

 Offline Offline
Activity: 1596
Merit: 6726
bitcoincleanup.com / bitmixlist.org


|
 |
April 25, 2021, 06:13:23 PM
Last edit: April 25, 2021, 07:01:46 PM by NotATether |
|
your formula if write in python, will help me to understand, kindly write python script, thankx
def point_add(Ax, Ay, Bx, By):
"""Point addition of points (Ax, Ay) and (Bx, By)"""
l = (By - Ay)//(Bx - Ax)
Cx = l**2 - Ax - Bx
Cy = l*(Ax - Cx) - Ay
return Cx, Cy # Point (Cx, Cy) = (Ax, Ay) + (Bx, By) Note that you will have to unserialize your hex numbers into integers before you can pass them here. The integer type in Python (unlike in other languages) is infinite-precision.
File "main.py", line 33
lambda = (By - Ay)/(Bx - Ax)
^
SyntaxError: invalid syntax
Right. lambda is a keyword in Python so I have to name it something else. See the edited code. |
.
.BLACKJACK ♠ FUN. | | | ███▄██████
██████████████▀
████████████
█████████████████
████████████████▄▄
░█████████████▀░▀▀
██████████████████
░██████████████
█████████████████▄
░██████████████▀
████████████
███████████████░██
██████████ | | CRYPTO CASINO &
SPORTS BETTING | | │ | | │ | ▄▄███████▄▄
▄███████████████▄
███████████████████
█████████████████████
███████████████████████
█████████████████████████
█████████████████████████
█████████████████████████
███████████████████████
█████████████████████
███████████████████
▀███████████████▀
███████████████████ | | .
|
|
|
|
brainless (OP)
Member
 
 Offline Offline
Activity: 316
Merit: 34

|
 |
April 25, 2021, 06:29:35 PM |
|
your formula if write in python, will help me to understand, kindly write python script, thankx
def point_add(Ax, Ay, Bx, By):
"""Point addition of points (Ax, Ay) and (Bx, By)"""
lambda = (By - Ay)/(Bx - Ax)
Cx = lambda**2 - Ax - Bx
Cy = lambda*(Ax - Cx) - Ay
return Cx, Cy # Point (Cx, Cy) = (Ax, Ay) + (Bx, By) Note that you will have to unserialize your hex numbers into integers before you can pass them here. The integer type in Python (unlike in other languages) is infinite-precision. File "main.py", line 33 lambda = (By - Ay)/(Bx - Ax) ^ SyntaxError: invalid syntax |
13sXkWqtivcMtNGQpskD78iqsgVy9hcHLF
|
|
|
brainless (OP)
Member
 
 Offline Offline
Activity: 316
Merit: 34

|
 |
April 25, 2021, 06:32:32 PM |
|
if
Ax = 28472748655393009267694063518808149386163109418078082138878164433505686461417 #3ef30130654689a64c864d6dd38760481c55fc525e2c6c7084e2d2d3d4d51be9
Ay = 112103652146063681709271542430359369857619412145509508700963842184555907779816 #f7d86b288c09ddb5311f292285168000e43e4b62201bd8de23a391daa8e00ce8
Bx = 48139720641152563685347991770512702742210610129134046538275528729266911276105 #6a6e1dc6f203f7fdd97965892301e5fb995a37318c410543835f0edcd3456c49
By = 19009808459039115948789087270292949097337312255656245874893769987807919753579 #2a072b9898b93e9eb05f9ad86a97546d83b579bf6efd3482f93baca13784496b
what result will be back from your formula ?
x: 9858272149801355672780957992190489068105775500642985285161445958802893804990
y: 77199671246421658177371783275117138254582110578372826724463426751083822428498
or
x: 8584546547439194144767466770313806210515315127328165539072185327841223593332
y: 36720222448510784205200470825713773455378994828752011866054770511274779895577
|
13sXkWqtivcMtNGQpskD78iqsgVy9hcHLF
|
|
|
o_e_l_e_o
In memoriam
Legendary

 Offline Offline
Activity: 2268
Merit: 18509

|
 |
April 25, 2021, 07:02:07 PM Merited by NotATether (1) |
|
-snip- If your two points are: 043EF30130654689A64C864D6DD38760481C55FC525E2C6C7084E2D2D3D4D51BE9F7D86B288C09DDB5311F292285168000E43E4B62201BD8DE23A391DAA8E00CE8
046A6E1DC6F203F7FDD97965892301E5FB995A37318C410543835F0EDCD3456C492A072B9898B93E9EB05F9AD86A97546D83B579BF6EFD3482F93BACA13784496B Then adding them together gives you the following point: 0415CB9594EE936BD14B98139460879BEE6F33B0F7C0CCB293825794D985F595BEAAAD772A2EC81AB6013775E9EDB274EFE2E133E65E58949AC7F25429FB1BB152 If you want to break that in to an x and y coordinate and convert to decimal as you have done, then the coordinates are: x = 9858272149801355672780957992190489068105775500642985285161445958802893804990
y = 77199671246421658177371783275117138254582110578372826724463426751083822428498 |
|
|
|
|
brainless (OP)
Member
 
 Offline Offline
Activity: 316
Merit: 34

|
 |
April 25, 2021, 07:11:51 PM |
|
-snip- If your two points are: 043EF30130654689A64C864D6DD38760481C55FC525E2C6C7084E2D2D3D4D51BE9F7D86B288C09DDB5311F292285168000E43E4B62201BD8DE23A391DAA8E00CE8
046A6E1DC6F203F7FDD97965892301E5FB995A37318C410543835F0EDCD3456C492A072B9898B93E9EB05F9AD86A97546D83B579BF6EFD3482F93BACA13784496B Then adding them together gives you the following point: 0415CB9594EE936BD14B98139460879BEE6F33B0F7C0CCB293825794D985F595BEAAAD772A2EC81AB6013775E9EDB274EFE2E133E65E58949AC7F25429FB1BB152 If you want to break that in to an x and y coordinate and convert to decimal as you have done, then the coordinates are: x = 9858272149801355672780957992190489068105775500642985285161445958802893804990
y = 77199671246421658177371783275117138254582110578372826724463426751083822428498 if we convert back into hexprvkey as per your addition abc def abc+def = 18AB but what i am looking addition like example in hex prvkeys based on x,y points abc def abc+def = abcdef |
13sXkWqtivcMtNGQpskD78iqsgVy9hcHLF
|
|
|
o_e_l_e_o
In memoriam
Legendary

 Offline Offline
Activity: 2268
Merit: 18509

|
 |
April 25, 2021, 07:47:27 PM |
|
but what i am looking addition like example in hex prvkeys based on x,y points
abc
def
abc+def = abcdef Well first, these aren't private keys but rather points on the curve, which would be public keys if anything. Yes, I guess you could concatenate two points together. You could take the two x coordinates: 3EF30130654689A64C864D6DD38760481C55FC525E2C6C7084E2D2D3D4D51BE9
6A6E1DC6F203F7FDD97965892301E5FB995A37318C410543835F0EDCD3456C49 Concatenate them together: 3EF30130654689A64C864D6DD38760481C55FC525E2C6C7084E2D2D3D4D51BE96A6E1DC6F203F7FDD97965892301E5FB995A37318C410543835F0EDCD3456C49 Modulo p:* 0D1C311FC0BD9915B98E45F586FE55821BAE99FB78ADB182BCCDC84652001073 And then calculate the two corresponding y coordinates: 76C85E288DE490C4281D4E5C94F930900FABA66B47B4CF1788C657BAF15C9BBA
8937A1D7721B6F3BD7E2B1A36B06CF6FF0545994B84B30E87739A8440EA36075 I have no idea why you would want to do such a thing though. Care to explain what you are trying to achieve here?
* p is the finite field over which the secp256k1 curve is defined: FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFEFFFFFC2F |
|
|
|
|
|
|
o_e_l_e_o
In memoriam
Legendary

 Offline Offline
Activity: 2268
Merit: 18509

|
 |
April 25, 2021, 08:05:21 PM |
|
if its not 1+1 = 2
then could be 1+1 = 11 No, it is neither 1+1 = 2 nor is it 1+1 = 11. The correct answer has been given by NotATether in the first reply in this thread. Graphically, you plot the two points on the curve, draw a straight line between them, extend that straight line to find the third point where it intersects the curve, and then reflect that third point across the x axis to find your answer. Algebraically, you use the equations given above. This is explained on page 8 of the link you gave, with the (slightly more complicated) equations given on page 10. |
|
|
|
|
|
mrxtraf
|
 |
April 26, 2021, 09:10:53 AM |
|
Here you write 1 + 1 = 11
And in what system should this be applied? Decimal, hex, or maybe binary?
For example, two numbers in hex b(11) and d(13)
In hex
b + d = bd
But in dec
11 + 13 = 1113
But
hex bd = dec 189 and not equal 1113 from previso result
So which system should you use as a basis for concatenation?
If decimal
X + Y = XY
in mathematic
X*strpad('1', len(Y)+1, '0', right) + Y
But in Hex it is completely different!
But if we transfer this to the points of coordinates, then nothing will work, because the length of Y is not known.
|
|
|
|
|
brainless (OP)
Member
 
 Offline Offline
Activity: 316
Merit: 34

|
 |
April 26, 2021, 03:02:16 PM |
|
Here you write 1 + 1 = 11
And in what system should this be applied? Decimal, hex, or maybe binary?
For example, two numbers in hex b(11) and d(13)
In hex
b + d = bd
But in dec
11 + 13 = 1113
But
hex bd = dec 189 and not equal 1113 from previso result
So which system should you use as a basis for concatenation?
If decimal
X + Y = XY
in mathematic
X*strpad('1', len(Y)+1, '0', right) + Y
But in Hex it is completely different!
But if we transfer this to the points of coordinates, then nothing will work, because the length of Y is not known.
here we are taking as hex b+d =bd where b is one point and d is 2nd point, result should be bd point in concatenation for your easy dec result will be 189 not 1113 |
13sXkWqtivcMtNGQpskD78iqsgVy9hcHLF
|
|
|
brainless (OP)
Member
 
 Offline Offline
Activity: 316
Merit: 34

|
 |
April 26, 2021, 04:57:00 PM |
|
hex b dec 11
x: 774ae7f858a9411e5ef4246b70c65aac5649980be5c17891bbec17895da008cb
y: d984a032eb6b5e190243dd56d7b7b365372db1e2dff9d6a8301d74c9c953c61b
hex d dec 13
x: f28773c2d975288bc7d1d205c3748651b075fbc6610e58cddeeddf8f19405aa8
y: 0ab0902e8d880a89758212eb65cdaf473a1a06da521fa91f29b5cb52db03ed81
result should be
hex bd dec 189
x: 6d7ef6b17543f8373c573f44e1f389835d89bcbc6062ced36c82df83b8fae859
y: cd450ec335438986dfefa10c57fea9bcc521a0959b2d80bbf74b190dca712d10
|
13sXkWqtivcMtNGQpskD78iqsgVy9hcHLF
|
|
|
|
mrxtraf
|
 |
April 26, 2021, 05:28:20 PM |
|
Impossible, not real and not logical.
|
|
|
|
|
brainless (OP)
Member
 
 Offline Offline
Activity: 316
Merit: 34

|
 |
April 26, 2021, 06:22:37 PM |
|
Impossible, not real and not logical.
movie name mission impossible, always done at possible, i believe some math expert have solution,  |
13sXkWqtivcMtNGQpskD78iqsgVy9hcHLF
|
|
|
NotATether
Legendary

 Offline Offline
Activity: 1596
Merit: 6726
bitcoincleanup.com / bitmixlist.org


|
 |
April 26, 2021, 06:31:12 PM
Last edit: April 27, 2021, 08:49:49 AM by NotATether |
|
here we are taking as hex
b+d =bd
where b is one point and d is 2nd point, result should be bd point in concatenation
for your easy dec result will be 189 not 1113
I guess you do understand that this concatenation you're doing is not point addition but rather a different operation (which makes me feel better), so now you're looking for math properties of this concatenation thing? Well for starters the operation you're doing is equal to a*len(b)* 4 16 + b [there are 4 bits in a hex char] in terms of the real addition so so you should be able to use it almost anywhere you need an Ax + B style expression. |
.
.BLACKJACK ♠ FUN. | | | ███▄██████
██████████████▀
████████████
█████████████████
████████████████▄▄
░█████████████▀░▀▀
██████████████████
░██████████████
█████████████████▄
░██████████████▀
████████████
███████████████░██
██████████ | | CRYPTO CASINO &
SPORTS BETTING | | │ | | │ | ▄▄███████▄▄
▄███████████████▄
███████████████████
█████████████████████
███████████████████████
█████████████████████████
█████████████████████████
█████████████████████████
███████████████████████
█████████████████████
███████████████████
▀███████████████▀
███████████████████ | | .
|
|
|
|
brainless (OP)
Member
 
 Offline Offline
Activity: 316
Merit: 34

|
 |
April 26, 2021, 08:15:24 PM |
|
|
13sXkWqtivcMtNGQpskD78iqsgVy9hcHLF
|
|
|
brainless (OP)
Member
 
 Offline Offline
Activity: 316
Merit: 34

|
 |
April 26, 2021, 11:52:50 PM |
|
here we are taking as hex
b+d =bd
where b is one point and d is 2nd point, result should be bd point in concatenation
for your easy dec result will be 189 not 1113
I guess you do understand that this concatenation you're doing is not point addition but rather a different operation (which makes me feel better), so now you're looking for math properties of this concatenation thing? Well for starters the operation you're doing is equal to a*len(b)*4 + b [there are 4 bits in a hex char] in terms of the real addition so so you should be able to use it almost anywhere you need an Ax + B style expression. this is simple math operation to calc, a*len(b)*16 + b but based on x,y points, there will be 2 snaorio, if concatenate under mod p, will be calculated, and result will apear on curve other not at curve, that will be apear based on point formula, and if operation everything will be on curve always |
13sXkWqtivcMtNGQpskD78iqsgVy9hcHLF
|
|
|
bytcoin
Member
 
 Offline Offline
Activity: 211
Merit: 20
$$$$$$$$$$$$$$$$$$$$$$$$$

|
 |
April 27, 2021, 11:55:12 AM |
|
P + G = PG
hex prvkey is abc
x: 3ef30130654689a64c864d6dd38760481c55fc525e2c6c7084e2d2d3d4d51be9
y: f7d86b288c09ddb5311f292285168000e43e4b62201bd8de23a391daa8e00ce8
hex prvkey is def
x: 6a6e1dc6f203f7fdd97965892301e5fb995a37318c410543835f0edcd3456c49
y: 2a072b9898b93e9eb05f9ad86a97546d83b579bf6efd3482f93baca13784496b
result = hex prvkey is abcdef:
x: 12faae608bd6562562b8f85564664cd1fdcd667f6b24b2b221ef86b9231f4d74
y: 512ee8cd9b34331afd05ccb8d81d1393c150c73ec5695845b731f7e6e0086719
Let me see if I understand .... Instead: 2 + 1 = 3 3 + 4 = 7 You want this: 2 + 1 = 21 3 + 4 = 34 ? |
|
|
|
|
brainless (OP)
Member
 
 Offline Offline
Activity: 316
Merit: 34

|
 |
April 27, 2021, 12:09:32 PM |
|
P + G = PG
hex prvkey is abc
x: 3ef30130654689a64c864d6dd38760481c55fc525e2c6c7084e2d2d3d4d51be9
y: f7d86b288c09ddb5311f292285168000e43e4b62201bd8de23a391daa8e00ce8
hex prvkey is def
x: 6a6e1dc6f203f7fdd97965892301e5fb995a37318c410543835f0edcd3456c49
y: 2a072b9898b93e9eb05f9ad86a97546d83b579bf6efd3482f93baca13784496b
result = hex prvkey is abcdef:
x: 12faae608bd6562562b8f85564664cd1fdcd667f6b24b2b221ef86b9231f4d74
y: 512ee8cd9b34331afd05ccb8d81d1393c150c73ec5695845b731f7e6e0086719
Let me see if I understand .... Instead: 2 + 1 = 3 3 + 4 = 7 You want this: 2 + 1 = 21 3 + 4 = 34 ? yes |
13sXkWqtivcMtNGQpskD78iqsgVy9hcHLF
|
|
|
bytcoin
Member
 
 Offline Offline
Activity: 211
Merit: 20
$$$$$$$$$$$$$$$$$$$$$$$$$

|
 |
April 27, 2021, 12:25:45 PM |
|
@brainless I don't see any advantage in calculating this ... Maybe just out of curiosity? Any personal projects or research? Or did you discover something interesting?
|
|
|
|
|
|
ymgve2
|
 |
April 27, 2021, 02:27:46 PM Merited by NotATether (1) |
|
your formula if write in python, will help me to understand, kindly write python script, thankx
def point_add(Ax, Ay, Bx, By):
"""Point addition of points (Ax, Ay) and (Bx, By)"""
l = (By - Ay)//(Bx - Ax)
Cx = l**2 - Ax - Bx
Cy = l*(Ax - Cx) - Ay
return Cx, Cy # Point (Cx, Cy) = (Ax, Ay) + (Bx, By) Note that you will have to unserialize your hex numbers into integers before you can pass them here. The integer type in Python (unlike in other languages) is infinite-precision.
File "main.py", line 33
lambda = (By - Ay)/(Bx - Ax)
^
SyntaxError: invalid syntax
Right. lambda is a keyword in Python so I have to name it something else. See the edited code. Did you just convert the Wikipedia equations to code? This will not work at all, because the calculation has to be done modulo the characteristic of the elliptic curve's field, everything should be done mod 0xfffffffffffffffffffffffffffffffffffffffffffffffffffffffefffffc2f Also this code does not account for the special cases where points have the same X coordinates. Instead, take a look at https://stackoverflow.com/questions/31074172/elliptic-curve-point-addition-over-a-finite-field-in-python(I still have no idea what OP is trying to do, and I suspect they don't know themselves either) |
|
|
|
|
NotATether
Legendary

 Offline Offline
Activity: 1596
Merit: 6726
bitcoincleanup.com / bitmixlist.org


|
 |
April 27, 2021, 05:58:10 PM |
|
Did you just convert the Wikipedia equations to code? This will not work at all, because the calculation has to be done modulo the characteristic of the elliptic curve's field, everything should be done mod 0xfffffffffffffffffffffffffffffffffffffffffffffffffffffffefffffc2f
Yes that's what I did, I kind of got the idea something was wrong when these calculations made large negative numbers for OP's output instead of points on the curve. I guess I have to mod each addition/subtraction by this, and can't defer it to the end of the line right? E.g l = ((By - Ay) mod p) / ((Bx - Ax) mod p) mod p versus: l = (By - Ay)/(Bx - Ax) mod p (I'll get to the edge cases later, for now let's get this clarified.) |
.
.BLACKJACK ♠ FUN. | | | ███▄██████
██████████████▀
████████████
█████████████████
████████████████▄▄
░█████████████▀░▀▀
██████████████████
░██████████████
█████████████████▄
░██████████████▀
████████████
███████████████░██
██████████ | | CRYPTO CASINO &
SPORTS BETTING | | │ | | │ | ▄▄███████▄▄
▄███████████████▄
███████████████████
█████████████████████
███████████████████████
█████████████████████████
█████████████████████████
█████████████████████████
███████████████████████
█████████████████████
███████████████████
▀███████████████▀
███████████████████ | | .
|
|
|
|
o_e_l_e_o
In memoriam
Legendary

 Offline Offline
Activity: 2268
Merit: 18509

|
-snip- You need to use the multiplicative inverse, which every number will have since p is prime. So, using your notation, you would do: (By - Ay) * (Bx - Ax) -1 mod pSo, as an example let's use the curve y 2 = x 3 + 7 mod 31, and lets use points (5,16) and (7,28) s = (28-16)/(7-5) mod 31 s = 12/2 mod 31 The multiplicative inverse of 2 mod 31 is 16, so s = 12*16 mod 31 = 6 Cx = 6 2 - 5 - 7 mod 31 = 24 Cy = 6*(5 - 24) - 16 mod 31 = -6 = 25 So the point C is (24,25). The python command you would be looking for is: l=(By-Ay) * libnum.invmod(Bx-Ax,p) |
|
|
|
|
brainless (OP)
Member
 
 Offline Offline
Activity: 316
Merit: 34

|
 |
April 27, 2021, 08:38:06 PM |
|
these all are simple math ecc addition, remain Q is point concatenate base on formula, where at curve or not at curve, my logics are beyond your thinking by point concatenate, where i have reach is same address with x same 2 difrent y's see below 1FQYNQGz32BDLcSBC4Kz54mErjzB7kbL1N 1FQYNQGz32BDLcSBC4Kz54mErjzB7kbL1N 1NWYqgBKDgJ3X8JnxynVRJeHxpsabPAcK8 1MfnBBkWkcXTQSvSucgCrh3D1WpvdV7DCM see compressed address 04eb611af1fd2e89e5361028f25d1a5510a4bc477757be925a594ce17436afe40370ac8110203e9 f95f8d832964b58ccc2c712bb1c6cd58e861134b48f456c9b53 at y is 70ac8110203e9f95f8d832964b58ccc2c712bb1c6cd58e861134b48f456c9b53 03eb611af1fd2e89e5361028f25d1a5510a4bc477757be925a594ce17436afe403 see uncompressed address 04eb611af1fd2e89e5361028f25d1a5510a4bc477757be925a594ce17436afe40384125d3056d83 64cf8962165f479d3da6f2ebc096f792df0ba484d8d703c0667 at y is 84125d3056d8364cf8962165f479d3da6f2ebc096f792df0ba484d8d703c0667 where y is difrent but in both cases compressed address is same uncompressed addresses are difrent check here https://iancoleman.io/bitcoin-key-compression/ |
13sXkWqtivcMtNGQpskD78iqsgVy9hcHLF
|
|
|
|
ymgve2
|
 |
April 27, 2021, 09:09:51 PM |
|
I don't know where you got 0x70ac8110203e9f95f8d832964b58ccc2c712bb1c6cd58e861134b48f456c9b53 from, but (x,y) = (0xeb611af1fd2e89e5361028f25d1a5510a4bc477757be925a594ce17436afe403, 0x70ac8110203e9f95f8d832964b58ccc2c712bb1c6cd58e861134b48f456c9b53) is NOT a valid point on the secp256k1 curve.
The valid y coordinates for x = 0xeb611af1fd2e89e5361028f25d1a5510a4bc477757be925a594ce17436afe403 are:
0x84125d3056d8364cf8962165f479d3da6f2ebc096f792df0ba484d8d703c0667 (you got that one) and
0x7beda2cfa927c9b30769de9a0b862c2590d143f69086d20f45b7b2718fc3f5c8
Since point compression takes just the lower bit of the y coordinate to set the prefix to either 0x02 or 0x03, the fact that you have an INVALID y coordinate which has the same lowest bit as the valid one, means point compression of course gives the same result.
|
|
|
|
|
|
ymgve2
|
 |
April 27, 2021, 10:05:04 PM |
|
I got curious and wondered where you got 0x70ac8110203e9f95f8d832964b58ccc2c712bb1c6cd58e861134b48f456c9b53 from, and discovered that it's what happens when you try to decompress a point with the x coordinate set to 0. Note that there are NO points on the secp256k1 curve with 0 as a valid x coordinate, this just happens because that iancoleman site doesn't check point validity at all.
If you enter 030000000000000000000000000000000000000000000000000000000000000000 into the iancoleman site, you get x=0 and y=0x70ac8110203e9f95f8d832964b58ccc2c712bb1c6cd58e861134b48f456c9b53 - which makes me yet again wonder what the hell you are trying to do.
Could you try to explain a bit more what your goal is?
|
|
|
|
|
brainless (OP)
Member
 
 Offline Offline
Activity: 316
Merit: 34

|
 |
April 27, 2021, 11:40:22 PM |
|
I got curious and wondered where you got 0x70ac8110203e9f95f8d832964b58ccc2c712bb1c6cd58e861134b48f456c9b53 from, and discovered that it's what happens when you try to decompress a point with the x coordinate set to 0. Note that there are NO points on the secp256k1 curve with 0 as a valid x coordinate, this just happens because that iancoleman site doesn't check point validity at all.
If you enter 030000000000000000000000000000000000000000000000000000000000000000 into the iancoleman site, you get x=0 and y=0x70ac8110203e9f95f8d832964b58ccc2c712bb1c6cd58e861134b48f456c9b53 - which makes me yet again wonder what the hell you are trying to do.
Could you try to explain a bit more what your goal is?
btw i mention valid points, as compress address same and uncompressed address changed when you construct x1, x2, x3 from y1 or y2 your x=0 vanish y1 = 8f537eefdfc1606a0727cd69b4a7333d38ed44e3932a7179eecb4b6fba9360dc y2 = 70ac8110203e9f95f8d832964b58ccc2c712bb1c6cd58e861134b48f456c9b53 x1 = eb611af1fd2e89e5361028f25d1a5510a4bc477757be925a594ce17436afe403 x2 = 8a80022196a21dcf65edb784fabedce993aba053f77169c814b61f30be356589 x3 = 8a1ee2ec6c2f584b64021f88a826ce05c7981834b0d003dd91fcff590b1aaed2 i am simple playing with bits and curves  |
13sXkWqtivcMtNGQpskD78iqsgVy9hcHLF
|
|
|
|
ymgve2
|
 |
April 27, 2021, 11:48:53 PM |
|
None of the combinations of those points are on the secp256k1 curve. Whatever you are doing, it is simply wrong.
Try it yourself, to be a valid point it has to satisfy the equation (x**3 + A*x + B) % N == (y**2) % N and for secp256k1 N = 0xfffffffffffffffffffffffffffffffffffffffffffffffffffffffefffffc2f, A = 0, B = 7
|
|
|
|
|
brainless (OP)
Member
 
 Offline Offline
Activity: 316
Merit: 34

|
 |
April 27, 2021, 11:52:03 PM |
|
None of the combinations of those points are on the secp256k1 curve. Whatever you are doing, it is simply wrong.
Try it yourself, to be a valid point it has to satisfy the equation (x**3 + A*x + B) % N == (y**2) % N and for secp256k1 N = 0xfffffffffffffffffffffffffffffffffffffffffffffffffffffffefffffc2f, A = 0, B = 7
get three x1, x2, x3 from x=0 tell me what y's and x's you get result |
13sXkWqtivcMtNGQpskD78iqsgVy9hcHLF
|
|
|
brainless (OP)
Member
 
 Offline Offline
Activity: 316
Merit: 34

|
 |
April 27, 2021, 11:54:23 PM |
|
from x = 8a80022196a21dcf65edb784fabedce993aba053f77169c814b61f30be356589
y1 = 84125d3056d8364cf8962165f479d3da6f2ebc096f792df0ba484d8d703c0667
y2 = 7beda2cfa927c9b30769de9a0b862c2590d143f69086d20f45b7b2718fc3f5c8
x1 = 8a80022196a21dcf65edb784fabedce993aba053f77169c814b61f30be356589
x2 = 8a1ee2ec6c2f584b64021f88a826ce05c7981834b0d003dd91fcff590b1aaed2
x3 = eb611af1fd2e89e5361028f25d1a5510a4bc477757be925a594ce17436afe403
|
13sXkWqtivcMtNGQpskD78iqsgVy9hcHLF
|
|
|
|
ymgve2
|
 |
April 28, 2021, 12:00:04 AM |
|
None of the combinations of those points are on the secp256k1 curve. Whatever you are doing, it is simply wrong.
Try it yourself, to be a valid point it has to satisfy the equation (x**3 + A*x + B) % N == (y**2) % N and for secp256k1 N = 0xfffffffffffffffffffffffffffffffffffffffffffffffffffffffefffffc2f, A = 0, B = 7
get three x1, x2, x3 from x=0 tell me what y's and x's you get result There are no results, because x=0 is not on the curve. The y values you get from x=0 do not as far as I can tell have any solution on the curve. from x = 8a80022196a21dcf65edb784fabedce993aba053f77169c814b61f30be356589
y1 = 84125d3056d8364cf8962165f479d3da6f2ebc096f792df0ba484d8d703c0667
y2 = 7beda2cfa927c9b30769de9a0b862c2590d143f69086d20f45b7b2718fc3f5c8
x1 = 8a80022196a21dcf65edb784fabedce993aba053f77169c814b61f30be356589
x2 = 8a1ee2ec6c2f584b64021f88a826ce05c7981834b0d003dd91fcff590b1aaed2
x3 = eb611af1fd2e89e5361028f25d1a5510a4bc477757be925a594ce17436afe403
These, though, are valid, but what is the point? What is the relevance of finding other points with the same y coordinates? |
|
|
|
|
brainless (OP)
Member
 
 Offline Offline
Activity: 316
Merit: 34

|
 |
April 28, 2021, 12:07:31 AM |
|
0379be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798
+
0279be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798
result
valid curve x=0 and y=8f53.....
base on these strategy, going to find point concatenate, where result will be on curve or not at curve (if outside of modulo p),
|
13sXkWqtivcMtNGQpskD78iqsgVy9hcHLF
|
|
|
|
ymgve2
|
 |
April 28, 2021, 12:15:33 AM |
|
0379be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798
+
0279be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798
result
valid curve x=0 and y=8f53.....
base on these strategy, going to find point concatenate, where result will be on curve or not at curve (if outside of modulo p),
That's not the way to do this point addition, if you add two points with the same X coordinate but opposite Y coordinates, you get the curve's infinity point, which is a special case and can't be represented as a public key. Also you still haven't explained what this "concatenation" is supposed to accomplish. |
|
|
|
|
brainless (OP)
Member
 
 Offline Offline
Activity: 316
Merit: 34

|
 |
April 28, 2021, 12:29:33 AM |
|
0379be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798
+
0279be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798
result
valid curve x=0 and y=8f53.....
base on these strategy, going to find point concatenate, where result will be on curve or not at curve (if outside of modulo p),
That's not the way to do this point addition, if you add two points with the same X coordinate but opposite Y coordinates, you get the curve's infinity point, which is a special case and can't be represented as a public key. Also you still haven't explained what this "concatenation" is supposed to accomplish. point concatenation will help me to generate new public addresses in new security level, like multi pubkeys "3" p2wsh, p2sh, similar, finding new paring, diffrent level secure, but must know, 0 point loop holes example if x=0 and not at curve then where from y -y comes, as its not satisfy Equation, Q is where from y-y comes ? |
13sXkWqtivcMtNGQpskD78iqsgVy9hcHLF
|
|
|
o_e_l_e_o
In memoriam
Legendary

 Offline Offline
Activity: 2268
Merit: 18509

|
 |
April 28, 2021, 07:56:14 AM |
|
0379be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798
+
0279be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798
result
valid curve x=0 and y=8f53.....
Your result is wrong. Consider graphically what is happening. The two points you have given above are the same point reflected over the x axis. To add these points you draw a line between them and mark the third point where it intersects the curve. The line you are drawing is vertical and therefore there is no y coordinate. As an example, look at this picture: 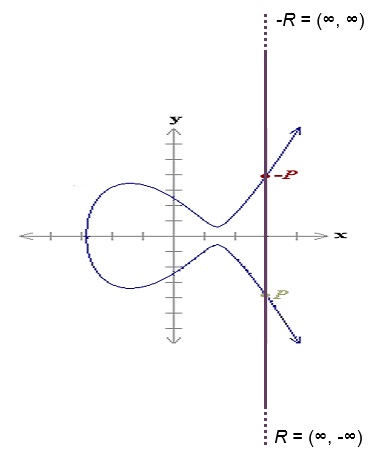 And now consider the equations I gave above. If the two x coordinates are the same, then Bx - Ax gives zero, meaning you must divide by zero to obtain the slope of the line. |
|
|
|
|
|
ymgve2
|
 |
April 28, 2021, 02:51:50 PM |
|
0379be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798
+
0279be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798
result
valid curve x=0 and y=8f53.....
base on these strategy, going to find point concatenate, where result will be on curve or not at curve (if outside of modulo p),
That's not the way to do this point addition, if you add two points with the same X coordinate but opposite Y coordinates, you get the curve's infinity point, which is a special case and can't be represented as a public key. Also you still haven't explained what this "concatenation" is supposed to accomplish. point concatenation will help me to generate new public addresses in new security level, like multi pubkeys "3" p2wsh, p2sh, similar, finding new paring, diffrent level secure, but must know, 0 point loop holes example if x=0 and not at curve then where from y -y comes, as its not satisfy Equation, Q is where from y-y comes ? Your y values comes from the fact that the math behind the recovery of y values always gives some answer, even if the original x coordinate is invalid. Also, you as saying you want to use this to generate new public addresses, but do you have any way to find the private key for these? Because without someone knowing the private key, having a public key is pretty useless. |
|
|
|
|
brainless (OP)
Member
 
 Offline Offline
Activity: 316
Merit: 34

|
 |
April 28, 2021, 03:29:39 PM |
|
0379be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798
+
0279be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798
result
valid curve x=0 and y=8f53.....
base on these strategy, going to find point concatenate, where result will be on curve or not at curve (if outside of modulo p),
That's not the way to do this point addition, if you add two points with the same X coordinate but opposite Y coordinates, you get the curve's infinity point, which is a special case and can't be represented as a public key. Also you still haven't explained what this "concatenation" is supposed to accomplish. point concatenation will help me to generate new public addresses in new security level, like multi pubkeys "3" p2wsh, p2sh, similar, finding new paring, diffrent level secure, but must know, 0 point loop holes example if x=0 and not at curve then where from y -y comes, as its not satisfy Equation, Q is where from y-y comes ? Your y values comes from the fact that the math behind the recovery of y values always gives some answer, even if the original x coordinate is invalid. Also, you as saying you want to use this to generate new public addresses, but do you have any way to find the private key for these? Because without someone knowing the private key, having a public key is pretty useless. person a have prvkey = abc person b have prvkey = def both person have there prvkeys and pubkeys, then concatenate pubkeys points to get next pubkeys, .. so on word... both dont know each other prvkeys, only pubkeys known each other ... its all next level of works, first level work is point concatenate formula, consider on it to make point concatenate with it |
13sXkWqtivcMtNGQpskD78iqsgVy9hcHLF
|
|
|
o_e_l_e_o
In memoriam
Legendary

 Offline Offline
Activity: 2268
Merit: 18509

|
 |
April 28, 2021, 03:46:20 PM |
|
person a have prvkey = abc
person b have prvkey = def
both person have there prvkeys and pubkeys, then concatenate pubkeys points to get next pubkeys, .. so on word... And then what? Knowing the private keys to two public keys that you have added together, concatenated, whatever, will not let you spend any coins sent to that resulting public key's address. both dont know each other prvkeys, only pubkeys known each other ... If this is what you want to achieve, then why not just use multi-sig? Trying to roll your own system like this is going to end up with you locking coins in an address or behind a script that you cannot access. |
|
|
|
|
brainless (OP)
Member
 
 Offline Offline
Activity: 316
Merit: 34

|
 |
April 28, 2021, 04:19:25 PM |
|
person a have prvkey = abc
person b have prvkey = def
both person have there prvkeys and pubkeys, then concatenate pubkeys points to get next pubkeys, .. so on word... And then what? Knowing the private keys to two public keys that you have added together, concatenated, whatever, will not let you spend any coins sent to that resulting public key's address. both dont know each other prvkeys, only pubkeys known each other ... If this is what you want to achieve, then why not just use multi-sig? Trying to roll your own system like this is going to end up with you locking coins in an address or behind a script that you cannot access. multisig requird both person sign/verify, in my new system, address and pubkey multi control, but could sign fro both and/or single, etc, anyway debate on every new system is always long, but first we need point con tests,  |
13sXkWqtivcMtNGQpskD78iqsgVy9hcHLF
|
|
|
|
ymgve2
|
 |
April 28, 2021, 04:33:30 PM |
|
Multisig does not require all participants to sign, you can generate any N-of-M schemes, like 1-of-2 where only a single participant needs to sign to spend. Or 2-of-3 where a majority needs to sign, but not everyone.
|
|
|
|
|
NotATether
Legendary

 Offline Offline
Activity: 1596
Merit: 6726
bitcoincleanup.com / bitmixlist.org


|
 |
April 29, 2021, 09:38:04 AM |
|
-snip- You need to use the multiplicative inverse, which every number will have since p is prime. ~ l=(By-Ay) * libnum.invmod(Bx-Ax,p) D'oh!  Yeah something felt wrong about using that division operator but I totally forgot it was doing numerical division. I have some code somewhere for performing a mod-inverse since apparently libnum's PyPI page says it should not be used in crypto implementations. #credits: https://gist.github.com/nlitsme/c9031c7b9bf6bb009e5a
def inverse(x, p):
"""
Calculate the modular inverse of x ( mod p )
the modular inverse is a number such that:
(inverse(x, p) * x) % p == 1
you could think of this as: 1/x
"""
inv1 = 1
inv2 = 0
while p != 1 and p!=0:
inv1, inv2 = inv2, inv1 - inv2 * (x / p)
x, p = p, x % p
return inv2 Some more functions for convenience: def add(x, y, p):
return (x + y) % p
def sub(x, y, p):
return (x - y) % p
def mul(x, y, p):
return (x * y) % p
def div(x, y, p):
return (x * inverse(y, p)) % p
def exp(x, y, p):
z = 1
for i in range(1, y+1):
z = mul(z, x, p)
return z
p = 2**256 - 2**32 - 977
#TODO edge cases
def point_add(Ax, Ay, Bx, By):
"""Point addition of points (Ax, Ay) and (Bx, By)"""
l = div(sub(By, Ay,p), sub(Bx, Ax, p), p)
Cx = sub(sub(exp(l, 2, p), Ax, p), Bx, p)
Cy = sub(mul(l, sub(Ax, Cx, p), p), Ay, p)
return Cx, Cy # Point (Cx, Cy) = (Ax, Ay) + (Bx, By)
I'll just assume that all ops have to be done mod p instead of line-by-line. |
.
.BLACKJACK ♠ FUN. | | | ███▄██████
██████████████▀
████████████
█████████████████
████████████████▄▄
░█████████████▀░▀▀
██████████████████
░██████████████
█████████████████▄
░██████████████▀
████████████
███████████████░██
██████████ | | CRYPTO CASINO &
SPORTS BETTING | | │ | | │ | ▄▄███████▄▄
▄███████████████▄
███████████████████
█████████████████████
███████████████████████
█████████████████████████
█████████████████████████
█████████████████████████
███████████████████████
█████████████████████
███████████████████
▀███████████████▀
███████████████████ | | .
|
|
|
|
o_e_l_e_o
In memoriam
Legendary

 Offline Offline
Activity: 2268
Merit: 18509

|
 |
April 29, 2021, 12:45:10 PM Merited by NotATether (1) |
|
I'll just assume that all ops have to be done mod p instead of line-by-line.
It actually makes no difference. In modulo arithmetic, the following all hold true: ( x mod p + y mod p) mod p = ( x + y) mod p( x mod p)( y mod p) mod p = xy mod p( x mod p)( y mod p) -1 mod p = x/ y mod pSo whether you do [(By - Ay) mod p / (Bx - Ax) mod p] mod p or just [(By - Ay) / (Bx - Ax)] mod p, your result will be the same. |
|
|
|
|
pooya87
Legendary

 Offline Offline
Activity: 3444
Merit: 10535

|
 |
April 30, 2021, 03:28:26 AM |
|
(x mod p)(y mod p)-1 mod p = x/y mod p
This doesn't look right to me. The problem is that I don't think we have division defined in modular arithmetic. In the following 3 divided by 7 is 0.4 and we can't work with that. However we have modular multiplicative inverse that can't be converted to a division:
3/7 ≡ 6 (mod 13)
7*2 ≡ 1 -> 7-1 ≡ 2 (mod 13)
3/7 ≡ 3 * 7-1 ≡ 3 * 2 ≡ 6 (mod 13)
|
.
.BLACKJACK ♠ FUN. | | | ███▄██████
██████████████▀
████████████
█████████████████
████████████████▄▄
░█████████████▀░▀▀
██████████████████
░██████████████
█████████████████▄
░██████████████▀
████████████
███████████████░██
██████████ | | CRYPTO CASINO &
SPORTS BETTING | | │ | | │ | ▄▄███████▄▄
▄███████████████▄
███████████████████
█████████████████████
███████████████████████
█████████████████████████
█████████████████████████
█████████████████████████
███████████████████████
█████████████████████
███████████████████
▀███████████████▀
███████████████████ | | .
|
|
|
|
NotATether
Legendary

 Offline Offline
Activity: 1596
Merit: 6726
bitcoincleanup.com / bitmixlist.org


|
 |
April 30, 2021, 03:56:28 AM |
|
(x mod p)(y mod p)-1 mod p = x/y mod p
This doesn't look right to me. The problem is that I don't think we have division defined in modular arithmetic. They both look like the same operation since technically every variable has to be mod p, so it's like writing ( x mod p)( y-1 mod p) mod p which would be the same as x * y -1 nonetheless (mod p of course). |
.
.BLACKJACK ♠ FUN. | | | ███▄██████
██████████████▀
████████████
█████████████████
████████████████▄▄
░█████████████▀░▀▀
██████████████████
░██████████████
█████████████████▄
░██████████████▀
████████████
███████████████░██
██████████ | | CRYPTO CASINO &
SPORTS BETTING | | │ | | │ | ▄▄███████▄▄
▄███████████████▄
███████████████████
█████████████████████
███████████████████████
█████████████████████████
█████████████████████████
█████████████████████████
███████████████████████
█████████████████████
███████████████████
▀███████████████▀
███████████████████ | | .
|
|
|
|
o_e_l_e_o
In memoriam
Legendary

 Offline Offline
Activity: 2268
Merit: 18509

|
 |
April 30, 2021, 08:20:31 AM |
|
The problem is that I don't think we have division defined in modular arithmetic. That's correct, but that's kind of my point. When performing point addition on an elliptic curve, you must use division to calculate the slope of the line. Since we can't do that modulo p, we instead convert to multiplying the multiplicative inverse, again modulo p. As NotATether says, perhaps it would have been more accurate to write: ( x mod p)( y-1 mod p) mod p = x * y-1 mod pSo if we take 23/27 mod 17, for example (23 mod 17 / 27 mod 17) mod 17 (6 / 10) mod 17 (6 * 12) mod 17 72 mod 17 4 Or (23 / 27) mod 17 (23 * 12) mod 17 276 mod 17 4 |
|
|
|
|
mausuv
Jr. Member

 Offline Offline
Activity: 70
Merit: 1

|
 |
December 21, 2021, 06:15:49 AM |
|
iknow r s1s2 value i need z1z2 how to calculate i read this post explain testnet ,i am not understad https://bitcointalk.org/index.php?topic=5327054.msg56686056#msg56686056https://bitcointalk.org/index.php?topic=977070.msg10669517#msg10669517 #read 1,3page please explain stepy by step calulate z1z2 from bitcoin mainet or write code #mybadenglish run this script https://github.com/FoxxD3V/btc-rsz/blob/master/RawTX_RSZ.pyoutput : show r s1s2 z1,z2 but i got error what my mistake https://tbtc.bitaps.com/raw/transaction/ff948290ff332aed8f0e5d767118a02e8671578c6775a333bb4ee4d6ccfcf639i am enter raw tx i got error https://github.com/FoxxD3V/btc-rsz/blob/master/RawTX_RSZ.pyTraceback (most recent call last):
File "RawTX_RSZ.py", line 13, in
s = keyUtils.derSigToHexSig(m[1][:-2])
File "/home/runner/btc-rsz/keyUtils.py", line 32, in derSigToHexSig
x, s = ecdsa.der.remove_integer(s)
File "/usr/local/lib/python2.7/dist-packages/ecdsa/der.py", line 218, in remove_integer
raise UnexpectedDER("Negative integers are not supported")
ecdsa.der.UnexpectedDER: Negative integers are not supported
i know r s1s2 i need z1z2 value please how to get z1z2 #mybadenglish |
|
|
|
|
|



