DaveF (OP)
Legendary

 Offline Offline
Activity: 3458
Merit: 6234
Crypto Swap Exchange


|
 |
March 24, 2022, 03:47:59 AM |
|
https://hak5.org/products/omg-adapterBeen working with someone and we think we might have a MITM attack working against a certain hardware wallet. For now I can't talk about it, but I can say (and have said in the past) don't trust anything you plug into your PC to verify anything else. With more and more laptops only coming with the USB C connector and more and more people needing the C to A adapter, it's going to be much easier to drop compromised cables like this into the environment. More in a few weeks (hopefully). -Dave
|
|
|
|
|
|
|
|
Advertised sites are not endorsed by the Bitcoin Forum. They may be unsafe, untrustworthy, or illegal in your jurisdiction.
|
jackg
Copper Member
Legendary

 Offline Offline
Activity: 2856
Merit: 3071
https://bit.ly/387FXHi lightning theory

|
 |
March 24, 2022, 05:31:57 AM |
|
Normally to recover a wallet you'd also have to put in a mnemonic, which would be sent down the cable too so there's added reason to make sure you can trust your connectors.
Do you know how easy the vulnerability you found would be to patch - is it likely to not remain one for long or is it quite well embedded (feel free to wait on answering this)?
|
|
|
|
|
witcher_sense
Legendary

 Offline Offline
Activity: 2310
Merit: 4313
🔐BitcoinMessage.Tools🔑


|
https://hak5.org/products/omg-adapterBeen working with someone and we think we might have a MITM attack working against a certain hardware wallet. For now I can't talk about it, but I can say (and have said in the past) don't trust anything you plug into your PC to verify anything else. With more and more laptops only coming with the USB C connector and more and more people needing the C to A adapter, it's going to be much easier to drop compromised cables like this into the environment. More in a few weeks (hopefully). -Dave Cables and adapters able to steal user's data have been around for a while, here is some articles regarding this topic: https://www.vice.com/en/article/k789me/omg-cables-keylogger-usbc-lightninghttps://plugavel.com/3025/tech/this-usb-c-cable-can-steal-your-data/https://fossbytes.com/not-so-innocent-usb-cable-uses-wifi-to-hack-your-device/https://fossbytes.com/usbharpoon-usb-cable-malware-transfer/https://shop.hak5.org/collections/mischief-gadgets/products/o-mg-cable-usb-aWith these USB cables, hackers can steal passwords and record pretty much everything you type with your keyboard, inject malicious payloads, reflash the system's firmware, remotely execute different commands, etc. However, I have never heard that any hardware wallet has been hacked this way. Hardware wallets generally transfer neither private keys nor any other sensitive information through a USB connection, so there is nothing hackers can intercept via cables like this. I don't know maybe it is possible to install malicious custom firmware on the device which will allow for seed extraction. They won't extract a passphrase though, because it is not stored anywhere and usually typed on a device itself. Normally to recover a wallet you'd also have to put in a mnemonic, which would be sent down the cable too so there's added reason to make sure you can trust your connectors.
Normally, the entire recovery process takes place or should take on a device itself, typing your seed on a computer is a terrible practice in principle. As an example: https://wiki.trezor.io/User_manual:Recovery |
|
|
|
NeuroticFish
Legendary

 Offline Offline
Activity: 3654
Merit: 6365
Looking for campaign manager? Contact icopress!

|
 |
March 24, 2022, 08:20:37 AM |
|
a MITM attack working against a certain hardware wallet.
Since the only valid uses for a cable are for signing transactions and maybe for charging, I'd guess that the transaction info going to the HW could be altered with the "right" cable (wouldn't such a cable be too bulky?!) But even then, such an attack could work only if one doesn't pay attention what the HW screen shows before signing (unless it's Jack's screenless future HW lol). However, I guess that the validation (or not) for my theory may have to wait "a few weeks"... |
.
.HUGE. | | | | | | █▀▀▀▀
█
█
█
█
█
█
█
█
█
█
█
█▄▄▄▄ | ▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀
.
CASINO & SPORTSBOOK
▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ | ▀▀▀▀█
█
█
█
█
█
█
█
█
█
█
█
▄▄▄▄█ | | |
|
|
|
|
PrivacyG
|
(wouldn't such a cable be too bulky?!)
I just wanted to ask this. Is there no way to tell a compromised cable from a non malicious one? One thing I never do is use any cable other than those I have always trusted or that came with the product. I understand it is possible to be targeted and have a cable compromised but besides what Neurotic's scenario of an attack, I do not think there is any way you could be attacked? If there was a way to do something malicious due to the cable being compromised, then I suppose it would also be possible to attack a Hardware Wallet through any computer infected with the right malware. Right? - Regards, PrivacyG |
|
|
|
NeuroticFish
Legendary

 Offline Offline
Activity: 3654
Merit: 6365
Looking for campaign manager? Contact icopress!

|
(wouldn't such a cable be too bulky?!)
I just wanted to ask this. Is there no way to tell a compromised cable from a non malicious one? I remembered that I've seen here in the past a discussion about malicious cables and I've found it: https://bitcointalk.org/index.php?topic=5186863It looks like the cable is not really different from normal ones; at least no visible difference. So it's a real problem. |
.
.HUGE. | | | | | | █▀▀▀▀
█
█
█
█
█
█
█
█
█
█
█
█▄▄▄▄ | ▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀
.
CASINO & SPORTSBOOK
▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ | ▀▀▀▀█
█
█
█
█
█
█
█
█
█
█
█
▄▄▄▄█ | | |
|
|
|
PawGo
Legendary

 Offline Offline
Activity: 952
Merit: 1367

|
Very interesting, I can't wait. It reminds me the famous "USB Ninja" project : https://usbninja.com or USBHarpoon. And makes me thing about all that people who connects their smartphones to "free chargers". |
|
|
|
|
DaveF (OP)
Legendary

 Offline Offline
Activity: 3458
Merit: 6234
Crypto Swap Exchange


|
 |
March 24, 2022, 11:43:50 AM
Last edit: March 24, 2022, 12:47:06 PM by DaveF |
|
Normally to recover a wallet you'd also have to put in a mnemonic, which would be sent down the cable too so there's added reason to make sure you can trust your connectors.
Do you know how easy the vulnerability you found would be to patch - is it likely to not remain one for long or is it quite well embedded (feel free to wait on answering this)?
I don't know, I'm a network and hardware guy. I got about 20% of the way into his explanation before my eyes glazed over. a MITM attack working against a certain hardware wallet.
Since the only valid uses for a cable are for signing transactions and maybe for charging, I'd guess that the transaction info going to the HW could be altered with the "right" cable (wouldn't such a cable be too bulky?!) But even then, such an attack could work only if one doesn't pay attention what the HW screen shows before signing (unless it's Jack's screenless future HW lol). However, I guess that the validation (or not) for my theory may have to wait "a few weeks"... (wouldn't such a cable be too bulky?!)
I just wanted to ask this. Is there no way to tell a compromised cable from a non malicious one? One thing I never do is use any cable other than those I have always trusted or that came with the product. I understand it is possible to be targeted and have a cable compromised but besides what Neurotic's scenario of an attack, I do not think there is any way you could be attacked? If there was a way to do something malicious due to the cable being compromised, then I suppose it would also be possible to attack a Hardware Wallet through any computer infected with the right malware. Right? - Regards, PrivacyG Actually, the screen shows on the device shows the correct information as does the screen of your PC. Remember not only can it record keyboard strokes it can play them back. As in edit webpages. What it can't do at this point is generate QR codes / graphics. Not only do the cables look the same, since USB C to A cables are still new to a lot of people they would not know the difference anyway. This is one of the few times BIP 70 would have actually been useful. -Dave |
|
|
|
dkbit98
Legendary

 Offline Offline
Activity: 2212
Merit: 7068
Cashback 15%


|
Been working with someone and we think we might have a MITM attack working against a certain hardware wallet. Please try doing that with airgapped hardware wallets like Passport or Keystone that don't use any cable connection with computer... I can't wait to see the results  With more and more laptops only coming with the USB C connector and more and more people needing the C to A adapter, it's going to be much easier to drop compromised cables like this into the environment. I am not a big fan of using USB-C as universal USB connector for all devices but it looks like we are going in that direction. They are even using same usb type c for charging devices like laptops and smartphones, and I've seen that making problems on some laptops, because people confuse power cable with usb and they blow up the board. It's not that hard to imagine some malware cables could target hardware wallet users, that is why I would only use original cables made by manufacturers. |
.
.HUGE. | | | | | | █▀▀▀▀
█
█
█
█
█
█
█
█
█
█
█
█▄▄▄▄ | ▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀
.
CASINO & SPORTSBOOK
▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ | ▀▀▀▀█
█
█
█
█
█
█
█
█
█
█
█
▄▄▄▄█ | | |
|
|
|
DaveF (OP)
Legendary

 Offline Offline
Activity: 3458
Merit: 6234
Crypto Swap Exchange


|
Been working with someone and we think we might have a MITM attack working against a certain hardware wallet. Please try doing that with airgapped hardware wallets like Passport or Keystone that don't use any cable connection with computer... I can't wait to see the results  With more and more laptops only coming with the USB C connector and more and more people needing the C to A adapter, it's going to be much easier to drop compromised cables like this into the environment. I am not a big fan of using USB-C as universal USB connector for all devices but it looks like we are going in that direction. They are even using same usb type c for charging devices like laptops and smartphones, and I've seen that making problems on some laptops, because people confuse power cable with usb and they blow up the board. It's not that hard to imagine some malware cables could target hardware wallet users, that is why I would only use original cables made by manufacturers. It will do those easier if it's just putting in an address. It's actually trivial. Remember it not just a key logger, it can also run apps and put stuff into the PC. So if he can get to the page inspector in chrome (or whatever it is in that particular browser) he can modify a BTC address at a known location. Since it's always in the same space here: https://bitcointalk.org/index.php?action=credit;promote it's a known spot in code that can change to his address. For now it can only change the address QR codes cannot be done (yet) The trick with the HW wallet is that it's breaking the encryption loop with their app. As I said WAY over my head in programming. As for only using the original cables, it's like you said USB A on a lot of machines is going away till they give you a cable that is USB C you need one of these adapter things. -Dave |
|
|
|
jackg
Copper Member
Legendary

 Offline Offline
Activity: 2856
Merit: 3071
https://bit.ly/387FXHi lightning theory

|
 |
March 24, 2022, 05:33:14 PM |
|
Normally to recover a wallet you'd also have to put in a mnemonic, which would be sent down the cable too so there's added reason to make sure you can trust your connectors.
Normally, the entire recovery process takes place or should take on a device itself, typing your seed on a computer is a terrible practice in principle. As an example: https://wiki.trezor.io/User_manual:RecoveryOhhhhh it's been updated! Afaik the last time I tried to recover my trezor it asked me to input the mnemonic in a different order (based on what the device said and asked for some extra words but I wasn't sure how much I trusted that - this was 3 or 4 years ago). |
|
|
|
|
m2017
Legendary

 Offline Offline
Activity: 1792
Merit: 1299
keep walking, Johnnie

|
 |
March 24, 2022, 05:56:59 PM |
|
And makes me thing about all that people who connects their smartphones to "free chargers".
Wow. But really, this is a great way to get malware on your phone. In modern times, in addition to the usual software hygiene of your device, it will include "do not charge in suspicious places and with unfamiliar cables." With more and more laptops only coming with the USB C connector and more and more people needing the C to A adapter, it's going to be much easier to drop compromised cables like this into the environment. I am not a big fan of using USB-C as universal USB connector for all devices but it looks like we are going in that direction. Looks like there's a new reason to keep an extra PC/laptop to interact with crypto. Of course, with USB type A, even then no adapters are required. This means that the threat described in this topic will be excluded. More and more manufacturers are refusing to use USB A in their devices, and over time this will lead to a shortage of such devices. The market for used devices will not be endless either. |
|
|
|
NeuroticFish
Legendary

 Offline Offline
Activity: 3654
Merit: 6365
Looking for campaign manager? Contact icopress!

|
 |
March 24, 2022, 06:33:03 PM
Last edit: May 14, 2023, 02:59:11 PM by NeuroticFish |
|
Looks like there's a new reason to keep an extra PC/laptop to interact with crypto. Of course, with USB type A, even then no adapters are required. This means that the threat described in this topic will be excluded.
USB A can easily handle exploits for PC/laptops, see the link from my other post here. So by making the wrong assumptions, instead of protecting one, you can end up getting malware on the other. More and more manufacturers are refusing to use USB A in their devices, and over time this will lead to a shortage of such devices. The market for used devices will not be endless either.
This doesn't really make sense. USB A is still widely used for PCs, I don't think they'll get no-longer-produced too soon. And, if you want to, you can easily buy cheap and straightforwards adapters from USB A to micro USB or USB-C like this one:  |
.
.HUGE. | | | | | | █▀▀▀▀
█
█
█
█
█
█
█
█
█
█
█
█▄▄▄▄ | ▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀
.
CASINO & SPORTSBOOK
▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ | ▀▀▀▀█
█
█
█
█
█
█
█
█
█
█
█
▄▄▄▄█ | | |
|
|
|
DaveF (OP)
Legendary

 Offline Offline
Activity: 3458
Merit: 6234
Crypto Swap Exchange


|
Looks like there's a new reason to keep an extra PC/laptop to interact with crypto. Of course, with USB type A, even then no adapters are required. This means that the threat described in this topic will be excluded.
USB A can easily handle exploits for PC/laptops, see the link from my other post here. So by making the wrong assumptions, instead of protecting one, you can end up getting malware on the other. More and more manufacturers are refusing to use USB A in their devices, and over time this will lead to a shortage of such devices. The market for used devices will not be endless either.
This doesn't really make sense. USB A is still widely used for PCs, I don't think they'll get no-longer-produced too soon. And, if you want to, you can easily buy cheap and straightforwards adapters from USB A to micro USB or USB-C like this one: 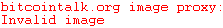 <Cough> MacBooks </cough> And any of the ultra portable PC ones (Microsoft surface, etc.) are all USB A only. Having one of those small adapters is nice. But people are people, and people forget things. If I drop a few of those cables around a show like BlackHat or Defcon probably nobody is going to plug them into anything. Leave a few around Bitcoin Miami and you could probably get someone to plug them in. Buy a few dozen (yes it's expensive) but then put a logo on for something that looks like a giveaway and you know people are going to use it.... -Dave |
|
|
|
NeuroticFish
Legendary

 Offline Offline
Activity: 3654
Merit: 6365
Looking for campaign manager? Contact icopress!

|
 |
March 24, 2022, 06:42:51 PM |
|
Leave a few around Bitcoin Miami and you could probably get someone to plug them in.
Well, we know that most aren't into Bitcoin because of the tech  And then I can guess the horror (and the bad publicity) if such exploit indeed happens at a big Bitcoin event  |
.
.HUGE. | | | | | | █▀▀▀▀
█
█
█
█
█
█
█
█
█
█
█
█▄▄▄▄ | ▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀
.
CASINO & SPORTSBOOK
▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ | ▀▀▀▀█
█
█
█
█
█
█
█
█
█
█
█
▄▄▄▄█ | | |
|
|
|
|
n0nce
|
 |
March 25, 2022, 12:44:24 AM |
|
Having one of those small adapters is nice. But people are people, and people forget things.
If I drop a few of those cables around a show like BlackHat or Defcon probably nobody is going to plug them into anything.
Leave a few around Bitcoin Miami and you could probably get someone to plug them in.
Buy a few dozen (yes it's expensive) but then put a logo on for something that looks like a giveaway and you know people are going to use it....
You'd be surprised how often you do find USB freebies at conferences such as BlackHat and similar.  Infecting PCs using free USB devices is a very common practice and even part of the toolbelt of lots of professional pentesting companies. Until now, I was under the impression that if you only transmit PSBTs through USB, a simple corrupting / replacing attack would definitely lead to the wrong address showing on the hardware device's screen. I'm very excited to see how you're going to circumvent this for hacking USB hardware wallets, though! It will do those easier if it's just putting in an address. It's actually trivial. Remember it not just a key logger, it can also run apps and put stuff into the PC. So if he can get to the page inspector in chrome (or whatever it is in that particular browser) he can modify a BTC address at a known location. Since it's always in the same space here: https://bitcointalk.org/index.php?action=credit;promote it's a known spot in code that can change to his address. For now it can only change the address QR codes cannot be done (yet) From this text it appears to me that you're just replacing the address shown on screen with a malicious one as well as sending that address to the hardware device; thus the user sees the same one on both devices. That's quite smart and should be relatively simple to do, sounds good to me! The trick with the HW wallet is that it's breaking the encryption loop with their app.
I don't understand this however. You're breaking encryption now? Why? |
|
|
|
DaveF (OP)
Legendary

 Offline Offline
Activity: 3458
Merit: 6234
Crypto Swap Exchange


|
I don't understand this however. You're breaking encryption now? Why?
Once again, I'm not he is :-) But he is not sending the bad address to the device, that is the issue. The user can copy / paste the info, but leaving the manufacturer out of it, there is a browser plug in they use to talk to the hardware wallet. As of now THAT is not fooled by the find / replace on the web page since it sees it as it loads or something. Explained to me but as I said I lost it after the 1st few minutes of the explanation. Just so you know how dangerous devices like this are here are just the PUBLIC DOWNLOADABLE things you can load on it. https://hak5.org/blogs/payloads (7 pages of fun) -Dave |
|
|
|
|
n0nce
|
 |
March 25, 2022, 12:15:19 PM |
|
I don't understand this however. You're breaking encryption now? Why?
Once again, I'm not he is :-) But he is not sending the bad address to the device, that is the issue. The user can copy / paste the info, but leaving the manufacturer out of it, there is a browser plug in they use to talk to the hardware wallet. As of now THAT is not fooled by the find / replace on the web page since it sees it as it loads or something. Explained to me but as I said I lost it after the 1st few minutes of the explanation. Just so you know how dangerous devices like this are here are just the PUBLIC DOWNLOADABLE things you can load on it. https://hak5.org/blogs/payloads (7 pages of fun) Honestly, I don't get why the attacker would 'talk to the hardware wallet' directly; it would be the most trivial and easy thing, if you have a way to manipulate webpages locally, to just replace the address, so the user himself copies the 'bad address' to the wallet and signs a transaction that spends money to it. This should also work pretty 'universally' against a variety of wallets, whereas other methods might be restricted to specific manufacturers / wallets only. But I'll just wait and see once more information can be released publicly; no hurry.  Oh, I know about these devices, they're really good, I used them in the past, too. |
|
|
|
Pmalek
Legendary

 Offline Offline
Activity: 2744
Merit: 7095

|
 |
March 26, 2022, 08:36:02 AM |
|
Depending on how severe this vulnerability or bug is, will the two of you reveal and discuss this with the manufacturing company first before releasing any details to the public? I think you should and I hope you will. There might be a bug bounty in it for you if you do. But more importantly, you won't be making life easier for those who want to destroy everything and steal money from people.
|
.
.BLACKJACK ♠ FUN. | | | ███▄██████
██████████████▀
████████████
█████████████████
████████████████▄▄
░█████████████▀░▀▀
██████████████████
░██████████████
█████████████████▄
░██████████████▀
████████████
███████████████░██
██████████ | | CRYPTO CASINO &
SPORTS BETTING | | │ | | │ | ▄▄███████▄▄
▄███████████████▄
███████████████████
█████████████████████
███████████████████████
█████████████████████████
█████████████████████████
█████████████████████████
███████████████████████
█████████████████████
███████████████████
▀███████████████▀
███████████████████ | | .
|
|
|
|
|
n0nce
|
 |
March 26, 2022, 01:38:27 PM |
|
Depending on how severe this vulnerability or bug is, will the two of you reveal and discuss this with the manufacturing company first before releasing any details to the public? I think you should and I hope you will. There might be a bug bounty in it for you if you do. But more importantly, you won't be making life easier for those who want to destroy everything and steal money from people.
It would also get them into big legal trouble if they don't make a responsible disclosure. In cybersecurity it's either that, or selling the exploit. Releasing online without notice to the manufacturer brings you 0 benefits and >0 troubles.  |
|
|
|
DaveF (OP)
Legendary

 Offline Offline
Activity: 3458
Merit: 6234
Crypto Swap Exchange


|
If he can get it working, it will be disclosed to them with an "X" number of days to acknowledge the issue and discuss with him.
The trouble is, it's not vulnerable until the user plugs in a malicious piece of hardware inline with their device. So, there might not really be a way to fix it if what he thinks is happening, is really the way it works.
It's like using a wireless keyboard to type sensitive information. There may not be a way to fix it.
As for what is working now, i.e. change an address in a known location that the user copy & pastes. There is nothing to really disclose. This device can run an app that can create predefined keyboard inputs. Short of unplugging the power to your PC it can't be fixed.
Edit to add: if it can't be fixed, it will not be given out or discussed (even to me and I'm the one who paid for the damn cables to test with)
If it can be fixed but they don't want to or just don't I'm not sure.
If it can be fixed and they have a timeline it will not be disclosed till after an agreed upon time has passed.
-Dave
|
|
|
|
|
n0nce
|
~
Right, so going the responsible disclosure route then. Definitely the best thing for the users and by many claimed the more moral thing to do. I can see how this may be unfixable. If I am on the right track with my idea about this exploit, it should be possible to e.g. construct a 'toy scenario' with a software wallet or so, and show the attack on that, without revealing a real manufacturer where this also works. And letting people figure that out by themselves; that should be 'green light', legally. It will be interesting nonetheless. The 'exploit' just uses keypresses though, so a mitigation would be providing a software that requires the user to allow new USB HID devices explicitly. It could be a service that runs in the background and shows a pop-up 'do you want to use this keyboard?' when plugging in a new device. |
|
|
|
Pmalek
Legendary

 Offline Offline
Activity: 2744
Merit: 7095

|
 |
March 26, 2022, 06:26:07 PM |
|
It would also get them into big legal trouble if they don't make a responsible disclosure. In cybersecurity it's either that, or selling the exploit. I wanted to say that as well, but I couldn't remember the damn term  . Responsible disclosure, that's it. Dave doesn't seem to me like the person who is looking yo exploit this, otherwise I don't think we would even have this thread. His post above confirms just that. Dave also doesn't know how it works. Only the person who discovered this bug knows the specifics. |
.
.BLACKJACK ♠ FUN. | | | ███▄██████
██████████████▀
████████████
█████████████████
████████████████▄▄
░█████████████▀░▀▀
██████████████████
░██████████████
█████████████████▄
░██████████████▀
████████████
███████████████░██
██████████ | | CRYPTO CASINO &
SPORTS BETTING | | │ | | │ | ▄▄███████▄▄
▄███████████████▄
███████████████████
█████████████████████
███████████████████████
█████████████████████████
█████████████████████████
█████████████████████████
███████████████████████
█████████████████████
███████████████████
▀███████████████▀
███████████████████ | | .
|
|
|
|
DaveF (OP)
Legendary

 Offline Offline
Activity: 3458
Merit: 6234
Crypto Swap Exchange


|
 |
March 26, 2022, 08:18:14 PM |
|
It would also get them into big legal trouble if they don't make a responsible disclosure. In cybersecurity it's either that, or selling the exploit. I wanted to say that as well, but I couldn't remember the damn term  . Responsible disclosure, that's it. Dave doesn't seem to me like the person who is looking yo exploit this, otherwise I don't think we would even have this thread. His post above confirms just that. Dave also doesn't know how it works. Only the person who discovered this bug knows the specifics. Apple = "It's not a bug, it's a feature" Seriously, it's not a bug. You are plugging something inline between your PC and your hardware device that can manipulate data. When HW wallets were 1st made there was no way that a device with all this storage and Wi-Fi could be put into a cable that does not look any different then a regular cable. So, it's just a vulnerability not a bug. In the real world it's the same thing to the end user. Dealing with security discussions it's different. A bug indicates they made a mistake, a vulnerability is something they do not defend against. To most of us it does not make a difference. To others it could cost them their job. A bug is "what the f--k were you thinking, get out of the office you idiot" a vulnerability is "This came up can you fix it or code around it" -Dave |
|
|
|
DaveF (OP)
Legendary

 Offline Offline
Activity: 3458
Merit: 6234
Crypto Swap Exchange


|
Just a bit of an update since it's been 2 months:
He contacted the comp any and they responded promptly and have been discussing options of how / if it's possible to fix it.
The biggest issue is that it is working as intended and now they are trying to figure out a way to stop a USB device that from behaving like a USB device should.
All without increasing the chance of user error. That was something we did not think of when talking about it. The more steps / checks you put in that a person has to do, the more possibility of said person making a mistake.
Next update when I know more.
-Dave
|
|
|
|
Tibu
Full Member
  
 Offline Offline
Activity: 303
Merit: 140
Hardware and open source software solutions.


|
 |
May 24, 2022, 12:19:50 PM |
|
This is a good reminder...
Always be careful.
Dont trust, verify. And a good way to verify a cable is to open it. If you see suspicious board -> trash it.
|
|
|
|
|
n0nce
|
This is a good reminder...
Always be careful.
Dont trust, verify. And a good way to verify a cable is to open it. If you see suspicious board -> trash it.
But then the cable is broken. And how to distinguish a suspicious board from a legit one? Sure, plain old USB-to-USB cables were just wires, so a silicon chip would stick out - but nowadays with USB-C, Lightning and whatnot, there are usually little circuit boards in the plugs anyway. I reckon it's pretty hard to tell if they're legit or not, even if inspected at a chip level. It is explained in great detail for instance in this talk: '36C3 - Open Source is Insufficient to Solve Trust Problems in Hardware' https://www.youtube.com/watch?v=Hzb37RyagCQA screencap about one attack method:  |
|
|
|
Tibu
Full Member
  
 Offline Offline
Activity: 303
Merit: 140
Hardware and open source software solutions.


|
 |
May 24, 2022, 12:44:49 PM |
|
This is a good reminder...
Always be careful.
Dont trust, verify. And a good way to verify a cable is to open it. If you see suspicious board -> trash it.
But then the cable is broken. And how to distinguish a suspicious board from a legit one? Sure, plain old USB-to-USB cables were just wires, so a silicon chip would stick out - but nowadays with USB-C, Lightning and whatnot, there are usually little circuit boards in the plugs anyway. I reckon it's pretty hard to tell if they're legit or not, even if inspected at a chip level. It is explained in great detail for instance in this talk: '36C3 - Open Source is Insufficient to Solve Trust Problems in Hardware' https://www.youtube.com/watch?v=Hzb37RyagCQA screencap about one attack method:  Thanks for the video. Really interesting. |
|
|
|
dkbit98
Legendary

 Offline Offline
Activity: 2212
Merit: 7068
Cashback 15%


|
Dont trust, verify. And a good way to verify a cable is to open it. If you see suspicious board -> trash it.
I would agree with this, but you should also be aware that warranty for most devices would be voided if device was opened, and you could not replace it if malfunction happens. Opening cables means that you are cutting and destroying them, and you can't use them anymore... I mean you can sort off, but question is how long this frankenstein cable will survive. Sad fact is that most people won't even notice anything suspicious, unless someone tells them what to look for. Recently I saw interesting products and topics related with this subject of USB connection with computers, you can always make your own cables and make them power only. How (and why) to make your own power-only USB cable: https://www.cultofmac.com/632796/how-and-why-to-make-your-own-power-only-usb-cable/USB Data Blocker: https://portablepowersupplies.co.uk/product/usb-data-blocker |
.
.HUGE. | | | | | | █▀▀▀▀
█
█
█
█
█
█
█
█
█
█
█
█▄▄▄▄ | ▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀
.
CASINO & SPORTSBOOK
▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ | ▀▀▀▀█
█
█
█
█
█
█
█
█
█
█
█
▄▄▄▄█ | | |
|
|
|
|
n0nce
|
 |
May 25, 2022, 12:41:42 PM |
|
Well, you do need data in most cases, like when using a hardware wallet or a mouse / keyboard, but you can indeed just make a regular USB cable yourself. But it's a brilliant idea, I really like it! USB plugs of all sizes and materials are sold online (easy to inspect and solder wires to), cables too and you probably just need some solder and a bit of time. I just found there are even kits [1] sold online with everything you need. It will not be possible to make a USB-C fast charging one with 12 (or more?) inside wires though, I guess. But you can just use those store-bought and plug them directly into wall bricks. [1] https://jujucables.com/product/diy-usb-cable-kit/ |
|
|
|
dkbit98
Legendary

 Offline Offline
Activity: 2212
Merit: 7068
Cashback 15%


|
 |
May 25, 2022, 03:09:07 PM |
|
Well, you do need data in most cases, like when using a hardware wallet or a mouse / keyboard, but you can indeed just make a regular USB cable yourself.
Yeah I know. I think I once tried experiment connecting Trezor device with usb power-only cable, and it didn't work properly  I just found there are even kits [1] sold online with everything you need.
It will not be possible to make a USB-C fast charging one with 12 (or more?) inside wires though, I guess. But you can just use those store-bought and plug them directly into wall bricks.
That is a nice find, I am checking it out now. God knows how much money I wasted on cables in my life, and most of them were terrible quality especially 3.5mm audio cables used for headphones and speakers. One friend recently wanted to start cable making business for his personal use and for selling, but I think he is busy with other stuff in his life now. I am not a big fan of USB-C connection (known to create problems and confusion with some laptops) but I guess it's slowly taking over, liked it or not :/ |
.
.HUGE. | | | | | | █▀▀▀▀
█
█
█
█
█
█
█
█
█
█
█
█▄▄▄▄ | ▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀
.
CASINO & SPORTSBOOK
▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ | ▀▀▀▀█
█
█
█
█
█
█
█
█
█
█
█
▄▄▄▄█ | | |
|
|
|
|
n0nce
|
Well, you do need data in most cases, like when using a hardware wallet or a mouse / keyboard, but you can indeed just make a regular USB cable yourself.
Yeah I know. I think I once tried experiment connecting Trezor device with usb power-only cable, and it didn't work properly  Of course, how else can it communicate if not using the two inner USB wires?  I just found there are even kits [1] sold online with everything you need.
It will not be possible to make a USB-C fast charging one with 12 (or more?) inside wires though, I guess. But you can just use those store-bought and plug them directly into wall bricks.
That is a nice find, I am checking it out now. I believe it's an American shop, but these kinds of kits exist in Europe too. Apparently these high quality DIY cables are popular in use with keyboards. God knows how much money I wasted on cables in my life, and most of them were terrible quality especially 3.5mm audio cables used for headphones and speakers.
One friend recently wanted to start cable making business for his personal use and for selling, but I think he is busy with other stuff in his life now.
How's the saying? Buy cheap = buy twice - something like that. Exists in many languages interestingly. And if you make it yourself you're also shielded from 'Bad USB cable' attacks [1] and cable implants (though it's a very targeted attack I must admit, so unlikely for majority of people). I am not a big fan of USB-C connection (known to create problems and confusion with some laptops) but I guess it's slowly taking over, liked it or not :/
What's good about USB-C is that it's backwards-compatible. I found out you can even make your DIY USB-C cables; just only wire up positive, negative and the two data wires. Here in this shop they sell a kit with PDF instructions [2] where it's clear they give you a USB-C connector with just the 4 classic USB-2.0 pads. 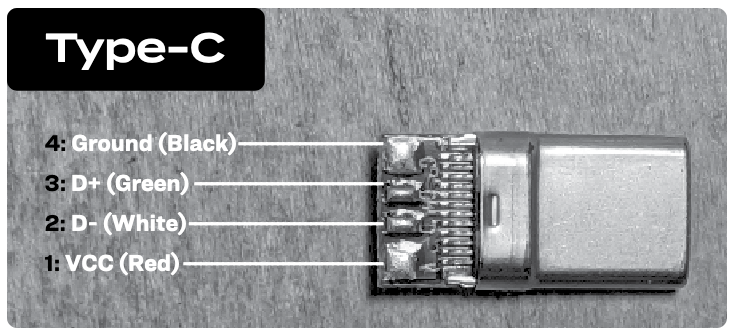 [1] https://mg.lol/blog/badusb-cables/[2] https://www.zapcables.com/products/diy-usb-cable-kit |
|
|
|
|
PrivacyG
|
 |
May 25, 2022, 09:04:29 PM |
|
Of course, how else can it communicate if not using the two inner USB wires?  I know Bluetooth has some security flaws. I am interested in your input. In this case, what do you think? Would you say it is safer to use a Hardware Wallet over Bluetooth connection rather than an unknown or new USB cable? - Regards, PrivacyG |
|
|
|
|
n0nce
|
Of course, how else can it communicate if not using the two inner USB wires?  I know Bluetooth has some security flaws. I am interested in your input. In this case, what do you think? Would you say it is safer to use a Hardware Wallet over Bluetooth connection rather than an unknown or new USB cable? Oh that's a good question. On one hand, technologically cable is better than wireless; assuming you know your cable. Wireless always remains attackable on the physical layer, although good high-level protocols can fix this attack vector. So to really answer it, you would also need to take into account whether the information sent over Bluetooth is encrypted on application-level and which Bluetooth implementation is used. Fact of the matter though, the [1] whole Bluetooth 5.3 specification has grown into a single, 3,000 (three-thousand) page 27MB PDF document, which should be telling enough. It's really really difficult to be sure about the security of such a single, huge protocol stack that has organically evolved over the years and not been built from the ground up with security in mind. Compared to other wireless technologies, I'd rate Bluetooth as less secure since it's this proprietary single standard that encompasses all layers from physical to application, whereas for instance WiFi has different segregated layers that can be analyzed and replaced independently. And this is only talking about protocol and possible protocol bugs. Add to this the huge (also single-project) Bluetooth implementations which are riddled of bugs and vulnerabilities; both on the device side ('mini' / 'IoT' type devices are typically less secure due to limited space - so often pure C code with sketchy optimizations) and even the host side. Literally one of the most widely used Bluetooth implementations, BlueZ [2] (besides having an expired TLS certificate) has had numerous attacks; though I'm not sure how many protocol bugs and how many implementation-specific ones. This is all theory, though. I haven't seen specialized, stealthy Bluetooth attacking devices so far, whereas the aforementioned bad USB cable does exist and is used. So it's hard to say what's more secure in practice, with which device (which BT implementation) and in which security / attack scenario you should use what hardware wallet. I'd personally go for cable and make sure I use one of my own cables, though. One reason is that when using a cable, you can only be infected when actually plugging the device in, so at the location / time you are trying to use it. However, a Bluetooth device can be infected at any time someone walks nearby as long as it's turned on. An example for this is the BlueBorne attack [3] where you might get infected by simply having a Bluetooth-capable HW wallet in your pocket while walking around town. So even using Bluetooth-enabled hardware wallets with a cable is less secure than devices that don't have BT at all, due to the larger attack surface. [1] https://www.bluetooth.com/specifications/specs/core-specification-5-3/[2] https://www.bluez.org/[3] https://www.armis.com/research/blueborne/ |
|
|
|
NeuroticFish
Legendary

 Offline Offline
Activity: 3654
Merit: 6365
Looking for campaign manager? Contact icopress!

|
 |
May 26, 2022, 08:20:25 AM |
|
Would you say it is safer to use a Hardware Wallet over Bluetooth connection rather than an unknown or new USB cable?
Imho it's not. But really, it's not that difficult to buy a proper USB data cable from a proper shop if, by (some rather unlikely) chance, the one from the HW manufacturer got damaged or lost. So why risk anyway? And while I do agree that this problem with USB cables is a growing problem, I don't think that if you just buy a new cable there's a real chance for troubles. So yeah, just stop using cables that aren't yours. And no, I don't trust at all the wireless connections, no matter it's NFC, Bluetooth or WiFi. |
.
.HUGE. | | | | | | █▀▀▀▀
█
█
█
█
█
█
█
█
█
█
█
█▄▄▄▄ | ▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀
.
CASINO & SPORTSBOOK
▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ | ▀▀▀▀█
█
█
█
█
█
█
█
█
█
█
█
▄▄▄▄█ | | |
|
|
|
vapourminer
Legendary

 Offline Offline
Activity: 4312
Merit: 3506
what is this "brake pedal" you speak of?

|
|
|
|
|
|
dkbit98
Legendary

 Offline Offline
Activity: 2212
Merit: 7068
Cashback 15%


|
 |
May 26, 2022, 06:01:10 PM |
|
How's the saying? Buy cheap = buy twice - something like that. Exists in many languages interestingly. And if you make it yourself you're also shielded from 'Bad USB cable' attacks [1] and cable implants (though it's a very targeted attack I must admit, so unlikely for majority of people).
Exactly that, and even when I purchased better quality audio cables, I destroy them as well... I need some military grade cables, or instructions how to make them, because I am terminator for cables  What's good about USB-C is that it's backwards-compatible. I found out you can even make your DIY USB-C cables; just only wire up positive, negative and the two data wires.
Here in this shop they sell a kit with PDF instructions [2] where it's clear they give you a USB-C connector with just the 4 classic USB-2.0 pads.
I know USB type C have advantages compared to older USB, and good thing about them is they can work on both sides and you can't plug it incorrectly. Problem I have is there is a push for all devices to use this for everything including power cables, that means all older cables are becoming obsolete, unless you use some adapter. I know Bluetooth has some security flaws. I am interested in your input. In this case, what do you think? Would you say it is safer to use a Hardware Wallet over Bluetooth connection rather than an unknown or new USB cable?
No it's not safer, and I personally don't like Bluetooth or other wireless type of communication used in hardware wallets. Better option than cables is using QR codes, and airgapped hardware wallets like Passport, Keystone, Coldcard or DIY SeedSigner. |
.
.HUGE. | | | | | | █▀▀▀▀
█
█
█
█
█
█
█
█
█
█
█
█▄▄▄▄ | ▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀
.
CASINO & SPORTSBOOK
▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ | ▀▀▀▀█
█
█
█
█
█
█
█
█
█
█
█
▄▄▄▄█ | | |
|
|
|
|
n0nce
|
How's the saying? Buy cheap = buy twice - something like that. Exists in many languages interestingly. And if you make it yourself you're also shielded from 'Bad USB cable' attacks [1] and cable implants (though it's a very targeted attack I must admit, so unlikely for majority of people).
Exactly that, and even when I purchased better quality audio cables, I destroy them as well... I need some military grade cables, or instructions how to make them, because I am terminator for cables  At least you're keeping the cable manufacturers in business!  But I encourage you to try such a DIY kit; I'll do too when I find the time, maybe those are more sturdy indeed. I saw people put paracord and other materials around the wires to make them more durable and get a custom look. That way it will also be easy to spot if someone replaced your cable. Opposed to a standard all white or black cable which might be replaced without notice in an evil maid attack [1] scenario. I know USB type C have advantages compared to older USB, and good thing about them is they can work on both sides and you can't plug it incorrectly.
Problem I have is there is a push for all devices to use this for everything including power cables, that means all older cables are becoming obsolete, unless you use some adapter.
On one hand, it's a pretty cool idea not having to carry a separate cable for almost every device, instead having a single cable that can charge your laptop, your phone, connect your phone to your laptop, connect your hardware wallet to your phone or connect your laptop to a monitor and much more. But there's already been a few practical issues like some cables not speaking all protocols. So therefore some features don't work with certain cables and certain devices, but do work on others and these sorts of annoyances. I believe it comes down to the chips used in the connectors and the actual number of leads that are actually connected. In the screencap I shared earlier, you can see the USB-C plug only having USB 2.0 (!!) standard connection pads, so from the outside it seems just like a USB-C cable but it will obviously barely charge a laptop (if at all - at 5V, 0.9A). But this may already be way too off-topic for this thread - sorry about that! [1] https://en.wikipedia.org/wiki/Evil_Maid_attack |
|
|
|
DaveF (OP)
Legendary

 Offline Offline
Activity: 3458
Merit: 6234
Crypto Swap Exchange


|
 |
July 03, 2022, 11:23:10 PM |
|
So was talking about this while burgers & beers earlier.
The fix they sent him barely works and causes errors and when it does work it's still not right. But as he put it "was more of a proof of concept then finished coding"
However, they are working on it so I'll give them that.
And yes it's a What's App burgers and beers meeting since he is several time zones away....
-Dave
|
|
|
|
|
n0nce
|
 |
July 03, 2022, 11:42:41 PM |
|
So was talking about this while burgers & beers earlier.
The fix they sent him barely works and causes errors and when it does work it's still not right. But as he put it "was more of a proof of concept then finished coding"
However, they are working on it so I'll give them that.
And yes it's a What's App burgers and beers meeting since he is several time zones away....
-Dave
Interesting; so the bug / exploit you guys found is going to be fixed by the manufacturer now? I was under the impression that due to its nature it was not vendor-specific to just one brand and that it was going to be hard to fix. The attack I imagined from your rough description, wouldn't be easy to fix outside the OS level. |
|
|
|
DaveF (OP)
Legendary

 Offline Offline
Activity: 3458
Merit: 6234
Crypto Swap Exchange


|
 |
July 04, 2022, 01:40:15 AM |
|
So was talking about this while burgers & beers earlier.
The fix they sent him barely works and causes errors and when it does work it's still not right. But as he put it "was more of a proof of concept then finished coding"
However, they are working on it so I'll give them that.
And yes it's a What's App burgers and beers meeting since he is several time zones away....
-Dave
Interesting; so the bug / exploit you guys found is going to be fixed by the manufacturer now? I was under the impression that due to its nature it was not vendor-specific to just one brand and that it was going to be hard to fix. The attack I imagined from your rough description, wouldn't be easy to fix outside the OS level. The editing of the webpage with an address in a fixed known position is not going to be a fixable, that just is what it is. The other thing that can be fixed that I have been evasive about discussing is more along the lines of changing the way the apps on the computer talk to the device. Without getting to into it because: 1) I promised not to and 2) I don't understand it fully... The desktop app says to the hw wallet lets send funds to this address 1234 the cable sends to the device lets send funds to 5678 at that point the user should stop. But the issue is a lot of people get complacent and don't check. The other issue is at certain times and certain conditions he can FORCE 1234 to be displayed on the device. Don't ask how I got as far as "you plug in the cable and then......it's all gibberish" I am not ashamed to admit it's over my head. I can fake PHP work, really know linux and like to think I am fairly good at routing. And in general tend to be the go-to person for dealing with many system issues. But this, nope, I get the basic concept of how it works. But don't get it past there. -Dave |
|
|
|
|
n0nce
|
 |
July 05, 2022, 12:07:38 AM |
|
[...]
Alright, so those are 2 different things at play then, right. Bug #1 is about replacing Bitcoin address A on screen and clipboard simultaneously with address B, so when the user copies it into the wallet software (which cannot know where that address comes from, so no way to verify it hasn't been tampered with), the address on the device's screen (B) will match with what's on the computer screen (B) and what was pasted into the wallet software (address B), so no suspicion will be raised. This can't be fixed by wallet applications. Bug #2 is about a user copying address A from a webpapge (unmodified / untampered) into the software, address A being displayed on the device's screen, but getting the device to sign transaction that spends to address B? Don't worry if you don't know / can't tell / aren't allowed to tell more details; I'm just very intrigued..  |
|
|
|
NotATether
Legendary

 Offline Offline
Activity: 1582
Merit: 6679
bitcoincleanup.com / bitmixlist.org


|
 |
July 05, 2022, 05:33:52 AM |
|
This whole "use cables to connect your legacy devices" nonsense is not going to cause most people to go out and buy cables to connect their peripherals to netiher macbooks or their cheap ultrabook competitors, particularly since there is no go-to vendor for buying plugs (like how there is Best Buy for electronics).
That philosophy might have worked with DisplayPort but I don't see people going out and buying cables or new USB-C devides anytime soon.
It's not too difficult to put two USB-A ports, one on each side of ultrabooks, and without increasing the thickness.
It's just due to lemmings copying Apple's fanatical minimalism really that the industry is threatening to go into a situation where we must buy cables for everything. [As you can see, this design philosophy doesn't work every well when transferred to Windows, hence the manufacturer resistance to going all-USB-C.]
|
.
.BLACKJACK ♠ FUN. | | | ███▄██████
██████████████▀
████████████
█████████████████
████████████████▄▄
░█████████████▀░▀▀
██████████████████
░██████████████
█████████████████▄
░██████████████▀
████████████
███████████████░██
██████████ | | CRYPTO CASINO &
SPORTS BETTING | | │ | | │ | ▄▄███████▄▄
▄███████████████▄
███████████████████
█████████████████████
███████████████████████
█████████████████████████
█████████████████████████
█████████████████████████
███████████████████████
█████████████████████
███████████████████
▀███████████████▀
███████████████████ | | .
|
|
|
|
|
n0nce
|
 |
July 05, 2022, 11:58:05 PM |
|
[...]
It's just due to lemmings copying Apple's fanatical minimalism really that the industry is threatening to go into a situation where we must buy cables for everything. [As you can see, this design philosophy doesn't work every well when transferred to Windows, hence the manufacturer resistance to going all-USB-C.]
I'm not a big fan of USB-C either, but honestly the whole point of it is to have a single (or a few) USB-C <> USB-C cables, which work for everything, from charging your phone, tablet, headphones, connecting your keyboard, connecting your display; anything, really. It should result in less cables being bought, carried around and replaced. Of course, there is a transition period as always. I'm certainly glad USB was introduced as opposed to having parallel port, serial port, PS/2, even Ethernet can run fairly well on a modern USB-A port - while we needed so many different ports in the past. So stuff moving towards less different connectors and cables in my opinion is a good thing in general. I have no idea how we got to this topic though; this is so off-topic..  |
|
|
|
|



