|
BTC guy (OP)
|
 |
March 01, 2012, 09:00:47 AM |
|
Im getting to the point where i have so many coins im starting to worry about them. Im wondering what you guys do to protect yours. I have mine spread around. Some in deepbit, some in MTgox, a few different wallets, on several hard drives, and USB sticks. But despite all that im still concerned with their safety. Is there anything else i can do to play it safe?
|
|
|
|
|
|
|
|
|
|
|
"The nature of Bitcoin is such that once version 0.1 was released, the
core design was set in stone for the rest of its lifetime." -- Satoshi
|
|
|
|
|
|
|
Revalin
|
 |
March 01, 2012, 10:13:12 AM |
|
I think the best is to keep an encrypted Satoshi-client wallet with enough funds for daily use, then store the rest in a small pile of offline wallets (either USB or paper), and only import as many as you need on a known-clean computer when you're ready to spend. Think of it like a checking and savings account.
The level of physical security you use to protect the paper/USB should correspond to the level of measures you'd use to protect that much cash or gold. 100BTC = file folder. 1000 = home safe. 10,000 = safe deposit box. 100,000 = a proper vault.
|
War is God's way of teaching Americans geography. --Ambrose Bierce
Bitcoin is the Devil's way of teaching geeks economics. --Revalin 165YUuQUWhBz3d27iXKxRiazQnjEtJNG9g |
|
|
|
D.H.
|
 |
March 01, 2012, 11:55:37 AM |
|
Download bitaddress.org or a similar tool that will create a private key by doing a SHA256 hash of a passphrase. Use it offline to be sure that noone ever sees the private key.
Create a long passphrase and repeat it to yourself 10 times every night when you go to bed. It's not hard to remember a long passphrase as long as it makes any sort of sense and by repeating it every night it will be virtually impossible to forget it. Write a little poem or something.
This is a passphrase
and it might be lame
but it is the key
to my fortune and fame
You'll feel pretty safe when the phrase you chose is stuck in your head. Also, you don't have to rely on any service to still be there, knowing that it's simply a matter of doing a SHA256 hash.
|
www.bitcoin.se - Forum, nyheter och information på svenska! (Forum, news and information in Swedish)
|
|
|
etotheipi
Legendary

 Offline Offline
Activity: 1428
Merit: 1093
Core Armory Developer


|
 |
March 01, 2012, 12:47:26 PM |
|
Im getting to the point where i have so many coins im starting to worry about them. Im wondering what you guys do to protect yours. I have mine spread around. Some in deepbit, some in MTgox, a few different wallets, on several hard drives, and USB sticks. But despite all that im still concerned with their safety. Is there anything else i can do to play it safe?
This is exactly why I made Armory Offline Wallets. (1) Get a super-cheap laptop. Disable all ethernet/wifi adapters (2) Generate a wallet (3) Make a watching-only copy of the wallet, transfer to online computer with USB key (4) Generate addresses and monitor transactions the same way as a full wallet If someone steals your online wallet, they get nothing! When you want to spend the coins, get out your USB key (1) Create the transaction as normal, but "Send" button will be grey'd out. (2) Click "create unsigned transaction" (3) Copy it to a USB key, take it to the offline computer (4) Click "Offline Transactions-->Sign Transaction" (5) Save the signed transaction (automatically overwrites the unsigned one) (6) Take to online computer and "Broadcast" The process of spending coins from an offline wallet is less than 60 seconds once you get the process down, and the whole interface walks you through the process.  The Armory Offline Wallets page describes not only how to use the feature, but also has a section titled "I'm Scared!" which describes a process you can follow to convince yourself it works. You should always make a backup (paper is best), put a few BTC in it, and then once or twice a day execute a small offline tx, to yourself if necessary. You'll find that it always works, 100% of the time. After 3-100 days, you'll eventually realize that there's nothing to be scared about and that it actually works -- flawlessly. Not to mention you have a backup just in case! There is no better way to secure large amounts of Bitcoins. I made the interface because so many people have complained about not feeling safe. This way, you don't have to rely on any external service. You can keep your money stored on a computer without any internet access... and anyone who gets your online (watching-only) wallet gets nothing, except knowing what addresses you own -- but they can't spend your Bitcoins! |
|
|
|
coretechs
Donator
Sr. Member

 Offline Offline
Activity: 362
Merit: 250

|
 |
March 01, 2012, 01:01:44 PM |
|
Download bitaddress.org or a similar tool that will create a private key by doing a SHA256 hash of a passphrase. Use it offline to be sure that noone ever sees the private key.
Create a long passphrase and repeat it to yourself 10 times every night when you go to bed. It's not hard to remember a long passphrase as long as it makes any sort of sense and by repeating it every night it will be virtually impossible to forget it. Write a little poem or something.
This is a passphrase
and it might be lame
but it is the key
to my fortune and fame
You'll feel pretty safe when the phrase you chose is stuck in your head. Also, you don't have to rely on any service to still be there, knowing that it's simply a matter of doing a SHA256 hash.
I prefer this method, but make the passphrase better... This is a frasspase 27 beetles
and it might be lame
but it is the key l1m3 p13
2toTWOt00 my fortune and fame |
|
|
|
etotheipi
Legendary

 Offline Offline
Activity: 1428
Merit: 1093
Core Armory Developer


|
 |
March 01, 2012, 01:07:10 PM |
|
Download bitaddress.org or a similar tool that will create a private key by doing a SHA256 hash of a passphrase. Use it offline to be sure that noone ever sees the private key.
Create a long passphrase and repeat it to yourself 10 times every night when you go to bed. It's not hard to remember a long passphrase as long as it makes any sort of sense and by repeating it every night it will be virtually impossible to forget it. Write a little poem or something.
This is a passphrase
and it might be lame
but it is the key
to my fortune and fame
You'll feel pretty safe when the phrase you chose is stuck in your head. Also, you don't have to rely on any service to still be there, knowing that it's simply a matter of doing a SHA256 hash.
I prefer this method, but make the passphrase better, like this: This is a passphrase 27 beetles
and it might be lame
but it is the key l1m3 p13
2toTWOt00 my fortune and fameUnfortunately, this is a disaster waiting to happen. No matter how much you try to memorize it: you will forget it. I have a 16 character password at work protecting my encrypted hard-drive. It was trivial to remember it for 3 months straight, because I typed it in every day. But then I got a new primary system and didn't touch the old one more than once in 6 months -- by then, finger muscle memory was the only thing that saved me, but it took me about 20 tries to get it. Fwhew! From then on, I have it written down in a sealed envelope inside a safe. The method described here is safe only if you write it down and store it safely somewhere. But you won't be able to access the funds at all. Sure, you can send money to it, and use blockexplorer to watch it: but how do you spend any of the money? How do you monitor incoming transactions? Sit there refreshing blockexplorer every 10 seconds? |
|
|
|
etotheipi
Legendary

 Offline Offline
Activity: 1428
Merit: 1093
Core Armory Developer


|
 |
March 01, 2012, 02:06:57 PM |
|
by then, finger muscle memory was the only thing that saved me, but it took me about 20 tries to get it.
That's awesome! So cool. Regarding the OP, I did everything required to use Armory offline transactions a year ago. Obtain sterile offline computer, create new wallet, etc.. I'm just waiting for Armory to catch up so I can spend my coins!  Holliday, What are you waiting for? The offline wallets work already! I use it for all my funds. That doesn't mean you should dive in blindly... but it is 100% usable, you only need to follow the "I'm Scared" section of the Offline Wallets Page to convince yourself to use it, too. If there's something missing, let me know what it is! |
|
|
|
|
Revalin
|
 |
March 01, 2012, 02:11:32 PM |
|
Also, obvious substitutions like: 2 for to|too|two|Z 3 for E 5 for S 0 for O ! for i etc add only about 1-1.5 bits worth of entropy each and are hard to remember long term. You are much better off including a random number (about 3.3 bits per digit), a random lowercase letter (4.7 bits each), or best of all, some random words from the Diceware list (12.9 bits each). When the only copy of the key is in your brain you don't want to make one that ends up being secure even from you.  In my opinion keeping a backup copy on paper is a good idea. Edit: to drive the point home, a 10-word (all-lowercase, no punctuation or substitutions) Diceware password has 129 bits of entropy, which is enough security to last forever. There is no quantum algorithm to crack your die rolls.  |
War is God's way of teaching Americans geography. --Ambrose Bierce
Bitcoin is the Devil's way of teaching geeks economics. --Revalin 165YUuQUWhBz3d27iXKxRiazQnjEtJNG9g |
|
|
etotheipi
Legendary

 Offline Offline
Activity: 1428
Merit: 1093
Core Armory Developer


|
 |
March 01, 2012, 02:27:05 PM |
|
Oh, sorry. It's been a while since I've read the complete Armory thread. I've probably purposely tried to ignore it because of how excited I've been to use it! The last time I read it (probably over a month ago!) you were still suggesting not to use Armory on the live Bitcoin network. I will definitely update myself today!  I guess I never gave an official "Go-Ahead" for main-network. But people have been using it, and I've only encouraged caution about using it with lots of money. That's exactly why I encourage following the "I'm Scared" procedure, so that you don't have to trust me: you can prove to yourself that it's reliable! |
|
|
|
|
MaxSan
|
 |
March 01, 2012, 02:47:45 PM |
|
I resort to buying an ironkey and storing on there. Seems to be a safe enough method.
|
|
|
|
|
DeathAndTaxes
Donator
Legendary

 Offline Offline
Activity: 1218
Merit: 1079
Gerald Davis

|
 |
March 01, 2012, 02:48:10 PM
Last edit: March 01, 2012, 02:58:52 PM by DeathAndTaxes |
|
Also, obvious substitutions like: 2 for to|too|two|Z 3 for E 5 for S 0 for O ! for i etc add only about 1-1.5 bits worth of entropy each and are hard to remember long term. You are much better off including a random number (about 3.3 bits per digit), a random lowercase letter (4.7 bits each), or best of all, some random words from the Diceware list (12.9 bits each). When the only copy of the key is in your brain you don't want to make one that ends up being secure even from you.  In my opinion keeping a backup copy on paper is a good idea. Edit: to drive the point home, a 10-word (all-lowercase, no punctuation or substitutions) Diceware password has 129 bits of entropy, which is enough security to last forever. There is no quantum algorithm to crack your die rolls.  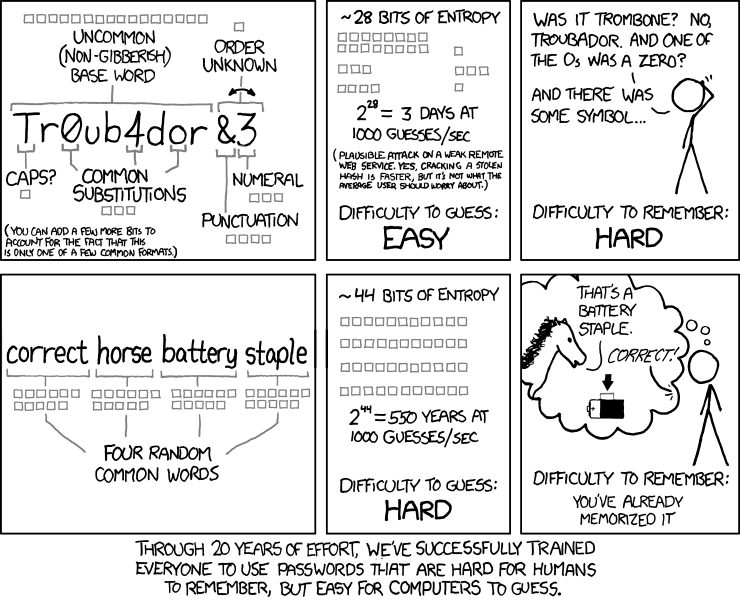 Yup it is ironic that the things people think are secure are very easy to forget or mess up and provide little hardening. They are harder on humans than computers (a poor trade). Things people assume would be easy have much more entropy and are difficulty to forget. Diceware is one method but any random word list of decent size is effective. A word list w/ 850 words will have about 9bits of entropy per word. A word list w/ 2000 words has about 11 bits. The key is to pick words AT RANDOM. If you pick words by choice you introduce bias and reduce entropy. Reason I said 850 is because here is a standardized basic english worldlist containing 850 words. For example I randomly (using an RNG) picked 5 words from this list: http://www.langmaker.com/wordlist/basiclex.htmchance owner bone market waiting = ~2^45 bits of entropy I would recommend adding a salt to prevent precomputation & shared key attacks. This doesn't have to be a secret (you can even email a copy to youself). It can be purely random of something like your email address chance owner bone market waiting myemail@email.comNot the strongest password but with the key hardening computationally infeasible to brute force. For more security use no wallet. Make a public address from a private key derived from hashing the passphrase a large number of times. Do it in a non-persistent linux environment (CD image or USB key) to prevent data recovery. With key hardening and salt the computational power to brute force this makes it uneconomical for sums less than $1 mil USD. |
|
|
|
|
Gabi
Legendary

 Offline Offline
Activity: 1148
Merit: 1008
If you want to walk on water, get out of the boat

|
 |
March 01, 2012, 03:07:44 PM |
|
Encrypt wallet.dat with Truecrypt, put a GOOD password and backup it in various hard disk/usb things and put it also online, like email or cloud storage services. <-make sure the password is a good one.
|
|
|
|
etotheipi
Legendary

 Offline Offline
Activity: 1428
Merit: 1093
Core Armory Developer


|
 |
March 01, 2012, 03:17:17 PM |
|
Encrypt wallet.dat with Truecrypt, put a GOOD password and backup it in various hard disk/usb things and put it also online, like email or cloud storage services. <-make sure the password is a good one.
Users don't use "good" passwords, regardless of whether they know it's a good idea or not. Additionally, I hate the idea of scattering your encrypted wallet all over the internet... what if there's a bug in the wallet encryption that actually leaves the private keys unencrypted? You probably won't even know until your coins are gone, and you know you can never remove your wallets entirely from these online storage places. You can transfer the coins immediately to a new wallet, but then you have to store/backup those somehow. And of course, even if you get all this right... see my previous comment about how easy it is to forget passwords... EDIT: I overlooked the comment about TrueCrypt ... it removes most of the is-this-encryption-really-secure-? uncertainties, but there's still plenty of other reasons to not like it I think the better way is to use wallet encryption on your own computer, and print off a paper backup. Paper is cheap, easy to store, and visually verifiable: if you can read the letters on the piece of paper, your backup is safe. Keep it in a book on your bookshelf, or store it away securely in a safe-deposit box. If you don't have a printer, you can backup to USB key instead, but there's always a risk that that key isn't going to work when you plug it in the first time two years later. And, with the Satoshi client, backups are not "forever." This may change in the future with deterministic wallets in the Satoshi client, but it's not currently there. This is one of the key features of alternative clients like Armory, and Electrum -- you only need to create a backup once when you create the wallet, and never again. With the Satoshi client, you need to create a new backup every 100 addresses, and thus you have to have some kind of regular backup solution which users are notoriously bad at doing (especially when you have to manually re-encrypt each time and redistribute it to your various backup locations). |
|
|
|
|
Revalin
|
 |
March 01, 2012, 03:22:20 PM |
|
-1 IronKey
+1 TrueCrypt
Hardware encryption doesn't improve security; it actually makes it worse because there's no way to audit it. How would you know if they added a back door? I recommend sticking to TrueCrypt, GPG, FreeOTFE, or other open-source, software-based encryption based on AES or 3DES.
Edit: And +1 paper. The biggest threats right now are automated viruses collecting your data. Keeping it in a form they can't easily steal is a big benefit. You can GPG-encrypt your paper wallet if you want to protect against people stealing the paper.
|
War is God's way of teaching Americans geography. --Ambrose Bierce
Bitcoin is the Devil's way of teaching geeks economics. --Revalin 165YUuQUWhBz3d27iXKxRiazQnjEtJNG9g |
|
|
etotheipi
Legendary

 Offline Offline
Activity: 1428
Merit: 1093
Core Armory Developer


|
 |
March 01, 2012, 03:34:43 PM
Last edit: March 01, 2012, 03:45:55 PM by etotheipi |
|
Paper is cheap, easy to store, and visually verifiable: if you can read the letters on the piece of paper, your backup is safe.
The one problem with this is, if someone obtains the paper, they have your savings. Multi-sig paper back ups stored at several physical locations would be fantastic. You are correct. Most of my focus in Armory development has been online threats, not physical threats. But that doesn't mean I've ignored it: I just think that having someone break into your house and going through your bookshelf to find the paper backup is 100x less likely than the random online attacker scanning millions of computers looking for open ports/vulnerabilities and getting access to your system. In the future, I can add a feature in Armory to allow you to add a passphrase/encryption to your paper backup, but I honestly think that just adds more risk than it adds value: your paper backup will likely not be used for years, and you're bound to forget the passphrase by then. If you're really concerned, put your paper backup in a safe-deposit box. Or back it up to 5 different USB keys and put them all in your safe-deposit box. Again, for the average user, I am most concerned about online threats, especially since a highly-targeted physical attack against your wallet will likely not be stopped by anything anyone can put in a Bitcoin client (keyloggers, especially). Multi-sig paper back ups stored at several physical locations would be fantastic.
Multi-signature transactions and two-factor authentication w/o third-party will become part of Armory. But I have a few other priorities to implement first. |
|
|
|
Jan
Legendary

 Offline Offline
Activity: 1043
Merit: 1002

|
 |
March 01, 2012, 04:07:21 PM |
|
Paper is cheap, easy to store, and visually verifiable: if you can read the letters on the piece of paper, your backup is safe.
The one problem with this is, if someone obtains the paper, they have your savings. Multi-sig paper back ups stored at several physical locations would be fantastic. You are correct. Most of my focus in Armory development has been online threats, not physical threats. But that doesn't mean I've ignored it: I just think that having someone break into your house and going through your bookshelf to find the paper backup is 100x less likely than the random online attacker scanning millions of computers looking for open ports/vulnerabilities and getting access to your system. In the future, I can add a feature in Armory to allow you to add a passphrase/encryption to your paper backup, but I honestly think that just adds more risk than it adds value: your paper backup will likely not be used for years, and you're bound to forget the passphrase by then. If you're really concerned, put your paper backup in a safe-deposit box. Or back it up to 5 different USB keys and put them all in your safe-deposit box. Again, for the average user, I am most concerned about online threats, especially since a highly-targeted physical attack against your wallet will likely not be stopped by anything anyone can put in a Bitcoin client (keyloggers, especially). Storing your private key on paper is IMO the way to go for long term storage. However if I were to store my life savings I would not trust just one piece of paper. There are elegant solutions to this. Shamir's Secret SharingShamir's Secret Sharing is a mechanism where you split a secret into N pieces and decide for a number K which is less than N. If you have K different pieces of the original N it is trivial to calculate the secret. If you have K-1 pieces the secret is completely undetermined, meaning that any possible value is likely. Details here: Shamir's Secret SharingExample Choosing N=3 and K=2: You split your secret into 3 pieces. You then store those pieces in three different secure locations. You delete any other trace of the secret. If you ever want to recreate the secret you can do so by retrieving any 2 of the 3 pieces. If an attacker gets hold of one of your pieces he will not be able to determine the secret. Or if one of the pieces are lost you can still rebuild the secret from the other two. You may also want to choose N=5 and K=3 or whatever makes you feel safe. This could be an awesome addition to the paper backups of Armory, or even better, a small standalone tool that spits out: N pieces of paper each containing its share of the private key as a QR-code and in HEX plus a description of the math on how to combine the shares One piece of paper with the Bitcoin address as a QR code and in base58. Believe it or not. I was once a consultant on a project where a similar procedure was done (paper shares, stored in various banks in different locations), where as a safety procedure the printer used had to be blown to pieces by the military afterwards. This was a backup for the root key of a CA. I guess they were paranoid of what you can get off a printer roller. |
Mycelium let's you hold your private keys private.
|
|
|
cbeast
Donator
Legendary

 Offline Offline
Activity: 1736
Merit: 1006
Let's talk governance, lipstick, and pigs.

|
 |
March 01, 2012, 04:09:12 PM |
|
Brain Wallet will be a killer app. I am choosing multiple encryption methods including mnemonics, music notation, a personally developed cryoptogrphic algorithm, and motor memory. It will be interesting to see how many keys I can create and remember, maybe enough to last a lifetime.
|
Any significantly advanced cryptocurrency is indistinguishable from Ponzi Tulips.
|
|
|
etotheipi
Legendary

 Offline Offline
Activity: 1428
Merit: 1093
Core Armory Developer


|
 |
March 01, 2012, 04:21:46 PM |
|
Shamir's Secret SharingShamir's Secret Sharing is a mechanism where you split a secret into N pieces and decide for a number K which is less than N. If you have K different pieces of the original N it is trivial to calculate the secret. If you have K-1 pieces the secret is completely undetermined, meaning that any possible value is likely. Details here: Shamir's Secret Sharing This is actually already possible for N=K using Armory's elliptic curve calculator (meaning that you need all of the pieces of paper to recover it). For instance, you create 3 private keys and use the calculator to multiply them together. The result is the final private key where the money is stored. Then you print off all three keys separately. To recover your wallet, you collect all three, and use the calculator again. Even better, this can be implemented without any two keys ever touching the same computer! Computer A produces a key, and gives the public key to Computer B. Computer B mulitiplies PublicKey(A) by its own private key to make PublicKey(A*B). Then this is given to computer C which multiplies it by his private key to make PublicKey(A*B*C). This is now a public key which can be converted to an address and funded. The only way to recover the private key, is to collect all three sheets of paper and multiply the private keys together! I don't promote this as the best solution, but it's one that is already available with Armory 0.55-alpha. In the future, this will all be unnecessary by simply putting all of your funds into a M-of-N multi-signature transaction. If it's a 2-of-3 transaction, you backup all 3 private keys separately, and any two will work. It's a protocol-level implementation of Samir's or Reed-Solomon. Believe it or not. I was once a consultant on a project where a similar procedure was done (paper shares, stored in various banks in different locations), where as a safety procedure the printer used had to be blown to pieces by the military afterwards. This was a backup for the root key of a CA. I guess they were paranoid of what you can get off a printer roller.
I totally believe it. A root CA key requires the highest level security, especially if it will be used for military operations. I'm surprised thermite wasn't involved  Brain Wallet will be a killer app. I am choosing multiple encryption methods including mnemonics, music notation, a personally developed cryoptogrphic algorithm, and motor memory. It will be interesting to see how many keys I can create and remember, maybe enough to last a lifetime.
I have considered brain wallets, but I think they are too risky, unless you include extra entropy stored on the computer (which partially defeats the purpose). As mentioned above, too many users use passphrases that are way too simple, and will end up sharing wallets (or make it too easy for an attacker to create the same wallet without ever accessing your computer). When their coins disappear, don't count on the user admitting that they used a weak passphrase. Instead, it will make the protocol/program look insecure. |
|
|
|
coretechs
Donator
Sr. Member

 Offline Offline
Activity: 362
Merit: 250

|
 |
March 01, 2012, 04:56:39 PM |
|
If you are worried about your memory consider that pass phrases can also be easily printed. There doesn't need to be any indication that it is a bitcoin wallet/PK either, just gibberish on paper. You can spend it pretty easily by importing the key with pywallet or the native privkey import coming in 0.6. edit: I do agree that a lot of people may screw up using passphrase wallets but for the rest of us it's very easy and very secure.  |
|
|
|
cbeast
Donator
Legendary

 Offline Offline
Activity: 1736
Merit: 1006
Let's talk governance, lipstick, and pigs.

|
 |
March 01, 2012, 05:01:38 PM |
|
If you are worried about your memory consider that pass phrases can also be easily printed. There doesn't need to be any indication that it is a bitcoin wallet/PK either, just gibberish on paper. You can spend it pretty easily by importing the key with pywallet or the native privkey import coming in 0.6.
If you're really worried, you can make pictographic tattoos to remind you. |
Any significantly advanced cryptocurrency is indistinguishable from Ponzi Tulips.
|
|
|
|



