|
DonYo
|
 |
September 23, 2014, 06:08:27 AM |
|
I only said I didn't DDOS Poloniex  Having a functioning exchange is vital for the plan. ~BCX~ So... you want cheap coins |
██████████
██████████████████
██████████████████████
██████████████████████████
████████████████████████████
██████████████████████████████
████████████████████████████████
████████████████████████████████
██████████████████████████████████
██████████████████████████████████
██████████████████████████████████
██████████████████████████████████
██████████████████████████████████
████████████████████████████████
██████████████
██████████████
████████████████████████████
██████████████████████████
██████████████████████
██████████████████
██████████
Monero
|
| "The difference between bad and well-developed digital cash will determine
whether we have a dictatorship or a real democracy." David Chaum 1996
"Fungibility provides privacy as a side effect." Adam Back 2014
|
| | |
|
|
|
|
|
|
|
|
|
|
|
|
"If you don't want people to know you're a scumbag then don't be a scumbag." -- margaritahuyan
|
|
|
Advertised sites are not endorsed by the Bitcoin Forum. They may be unsafe, untrustworthy, or illegal in your jurisdiction.
|
|
|
|
|
BitcoinEXpress (OP)
Legendary

 Offline Offline
Activity: 1210
Merit: 1024

|
 |
September 23, 2014, 06:09:07 AM |
|
BCX, was that you in the polo chat under a different name?
For the record I did not DDOS Poloniex. If I did I promise you I would have told you. I have nothing against Poloniex. As was pointed out by a few other posters, this is not my style. More than likely some poser that was going to try and get some coins out of you. Believe what you want to believe but anybody that has been here for any time knows, that wasn't me. ~BCX~ It seems it was the same account as the one that you proved you used yesterday Not from the screen caps that was just sent to me. The person was blatantly a non English speaker and couldn't verify here in this forum when asked by the mod. ~BCX~ |
|
|
|
|
robinwilliams
Member
 
 Offline Offline
Activity: 112
Merit: 10

|
 |
September 23, 2014, 06:12:00 AM |
|
So u r first test was? Confused ...
|
|
|
|
|
BitcoinEXpress (OP)
Legendary

 Offline Offline
Activity: 1210
Merit: 1024

|
 |
September 23, 2014, 06:13:42 AM |
|
So u r first test was? Confused ...
I did not DDOS Poloniex period. I have no reason to. ~BCX~ |
|
|
|
|
TheFascistMind
Newbie

 Offline Offline
Activity: 42
Merit: 0

|
 |
September 23, 2014, 06:23:48 AM |
|
3) Frankly, there is at least one person who probably contributed mightily to this situation who appears to have a significant personality disorder. I'm not talking about any of the MEW folks or major players, and I won't name him/her, but it's easy to imagine how this person contributed to pissing off BCX. That person probably has SERIOUS issues, but BCX couldn't have known about that, IMO.
...
I'm not trying to defend behaviors, here, but I will say I sure don't understand some of them. And there is likely a reason behind those behaviors, somewhere.
I think you are referring to a username that ends with 88 and not me. For the record, I didn't want to get involved because I didn't like expending effort then being dependent on promises about a bounty. I try to avoid conflict by being in control of my own destiny at all times. I really, really, really hate being dependent on what other people do. So when jl777 asked me if I could go deeper and try to find the attack, I really wanted to tell him no. Because I don't have the resources nor the desire to mount an attack to force my maximum restitution. But jl777 is such a nice guy, and he did offer 5 BTC, so I felt obligated to try. Once I had found something, I spoke with smooth, jl777, and crypto0_zoidbery (cc'd to rpietila and tacotime) about the terms of the 10 BTC bounty. We agreed that if I showed there is a vulnerability for which they don't already have a mitigation underway, then I get the bounty. Once they agreed, I proceeded. So when rpietila and fluffypony seemed to indicate that I had found nothing, I felt they were trying to spin what I had provided to them, that is why I got pissed off. Then they explained to me that was not the case and they were awaiting further clarification on whether I had really found something or not. And that my effort is appreciated. I had not provided to them running code for an attack. I have only provided pseudocode. And my latest insights were written in 3 paragraphs and not yet incorporated into the pseudocode. Smooth sees my algorithm can in theory find the sender of some of the rings. What is not clear is how it will perform. Will it take 1 million years to find 1 sender? I don't think so, but the math of the algorithm seems difficult to quantify. I suggested we code it and run it. I told smooth I can't do all the work, because that wasn't the terms of the 11 BTC bounty and frankly I've paid other programmers and earned myself $300 per hour. I for example paid Jeff Stock (former main programmer of Borland C), $30,000 for one week of work in 2000 on my CoolPage software. I explained to smooth that I didn't want to put a lot more work in without knowing from them what is the limit of my contribution so I can be paid, move on with my other work, and they can take it forward from there. So now I am waiting for the feedback from smooth after he consults with everyone involved. I would code it if I had a good understanding of the CN blockchain format. I don't. My attack is purely from a conceptual basis. So I think it is best I write the pseudocode only and they code and test it. If they feel they need to lower the bounty they pay me, then I want them to tell me now, before I do further effort on it. Any way, what ever happens I want to move on asap. I hope we can find an outcome that delivers mutual respect, delivers value to CN, and everyone is happy. I hope rpietila can afford 11 BTC. Actually jl777 offered 5 BTC, crypto_zoidberg 1 BTC, and rpietila et al 5 BTC. I am not begging for money. It is a matter of principle only. If my algorithm fails testing, then I am owed nothing. |
|
|
|
|
TheFascistMind
Newbie

 Offline Offline
Activity: 42
Merit: 0

|
 |
September 23, 2014, 06:29:51 AM |
|
Smooth sees my algorithm can in theory find the sender of some of the rings. What is not clear is how it will perform. Will it take 1 million years to find 1 sender? I don't think so, but the math of the algorithm seems difficult to quantify. I suggested we code it and run it.
I made the point that no matter how much computation my algorithm requires, CN coins will have to devote as much computation to it as an attacker can. Because afaics the only way to mitigate the attack, is to precompute the combinatorial intersections and disallow such combinations of inputs in rings before they can occur. Thus I am thinking this computation will need to become part of the PoW. I am expecting CN will have all the mining clients computing the mitigation. The caveat is that if the algorithm finds negligible senders in known realistic computational power, then my algorithm can be ignored. I doubt it. |
|
|
|
|
smooth
Legendary

 Offline Offline
Activity: 2968
Merit: 1198

|
 |
September 23, 2014, 06:30:42 AM |
|
I had not provided to them running code for an attack. I have only provided pseudocode. And my latest insights were written in 3 paragraphs and not yet incorporated into the pseudocode. Smooth seems my algorithm can in theory find the sender of some of the rings. What is not clear is how it will perform. Will it take 1 million years to find 1 sender? I don't think so, but the math of the algorithm seems difficult to quantify. I suggested we code it and run it. I told smooth I can't do all the work, because that wasn't the terms of the 11 BTC bounty and frankly I've paid other programmers and earned myself $300 per hour. I for example paid Jeff Stock (former main programmer of Borland C), $30,000 for one week of work in 2000 on my CoolPage software. I explained to smooth that I didn't want to put a lot more work in without knowing from them what is the limit of my contribution so I can be paid, move on with my other work, and they can take it forward from there.
So now I am waiting for the feedback from smooth after he consults with everyone involved.
Confirm all of this. I'd add there was some feedback from crypto_zoidberg along similar lines but I don't want get into the details of private conversations; we will work all this out. Many of the players right now are understandbly busy, others are in different time zones, etc. It takes time. I would code it if I had a good understanding of the CN blockchain format. I don't. My attack is purely from a conceptual basis. So I think it is best I write the pseudocode only and they code and test it. If they feel they need to lower the bounty they pay me, then I want them to tell me now, before I do further effort on it.
All of this is entirely reasonable and consistent with my understanding. I've heard nothing about lowering the bounty, not sure where that even came from. Coding could take the form of a simulation along the lines of the code tacotime gave you BTW, with analysis of scaling parameters to suggest how it would extrapolate to a real blockchain. That is how our lab people produced MRL-0001. I doesn't have to be from a live blockchain. |
|
|
|
|
TheFascistMind
Newbie

 Offline Offline
Activity: 42
Merit: 0

|
 |
September 23, 2014, 06:32:54 AM |
|
I've heard nothing about lowering the bounty, not sure where that even came from.
Only from my paranoid mind. Apologies. I've had a rough life, and have been backstabbed so many times in life... |
|
|
|
|
smooth
Legendary

 Offline Offline
Activity: 2968
Merit: 1198

|
 |
September 23, 2014, 06:33:28 AM |
|
I made the point that no matter how much computation my algorithm requires, CN coins will have to devote as much computation to it as an attacker can. This is only true if the attack is feasible at all. As you said, if it takes a million years (using all feasibly available computing power) to find one link, then neither the attacker nor the defender need to do that. EDIT: I see you added a similar condition to your post. There may also be practical asymmetric defenses that mathematically ensure no unacceptable scope of weaknesses without actually finding the links, as there are against the MRL-0001 vulnerabilities. But we don't know until there is further analysis. |
|
|
|
|
smooth
Legendary

 Offline Offline
Activity: 2968
Merit: 1198

|
 |
September 23, 2014, 06:34:12 AM |
|
I've heard nothing about lowering the bounty, not sure where that even came from.
Only from my paranoid mind. Apologies. I've had a rough life, and have been backstabbed so many times in life... You will learn if you continue to deal with me that I'm not a backstabber. I'll pay the bounty out of my own pocket if need be (which have no reason to believe) if the conditions are met. |
|
|
|
|
TheFascistMind
Newbie

 Offline Offline
Activity: 42
Merit: 0

|
 |
September 23, 2014, 06:34:44 AM |
|
Smooth sees my algorithm can in theory find the sender of some of the rings. What is not clear is how it will perform. Will it take 1 million years to find 1 sender? I don't think so, but the math of the algorithm seems difficult to quantify. I suggested we code it and run it.
I made the point that no matter how much computation my algorithm requires, CN coins will have to devote as much computation to it as an attacker can. Because afaics the only way to mitigate the attack, is to precompute the combinatorial intersections and disallow such combinations of inputs in rings before they can occur. Thus I am thinking this computation will need to become part of the PoW. I am expecting CN will have all the mining clients computing the mitigation. The caveat is that if the algorithm finds negligible senders in known realistic computational power, then my algorithm can be ignored. I doubt it. So, it seems all CN coins are in for a necessary hardfork in the future We don't know until we have a simulation. It is possible we do nothing, because also for example there is the wrinkle of Sybil attack. I will not say more. Let's not give advice to a potential attacker in public messages. Let them work on it. |
|
|
|
|
BitcoinEXpress (OP)
Legendary

 Offline Offline
Activity: 1210
Merit: 1024

|
 |
September 23, 2014, 06:34:55 AM |
|
No one believe a word you say, you piece of crap, first you said you have nothing against Monero then you said you were going to kill it, there are logs with the same nick you used when you tried to bet 500 btc against Risto, if you try anything against Polo they will go after you, whatever you kill Monero or not.
Like it or not, your belief isn't required or needed. ~BCX~ |
|
|
|
|
robinwilliams
Member
 
 Offline Offline
Activity: 112
Merit: 10

|
 |
September 23, 2014, 06:35:05 AM |
|
What does this have to do with bcx attack?
|
|
|
|
|
smooth
Legendary

 Offline Offline
Activity: 2968
Merit: 1198

|
 |
September 23, 2014, 06:36:30 AM |
|
So, it seems all CN coins are in for a necessary hardfork in the future
Realistically all of these coins are immature solutions in a rapidly developing space. Any of them that fails to have multiple hard forks will be dead IMO. |
|
|
|
|
E66BEN
Newbie

 Offline Offline
Activity: 5
Merit: 0

|
 |
September 23, 2014, 06:36:53 AM |
|
He got scared of the FBI thingy and decided to deny what he did.. haha
|
|
|
|
|
smooth
Legendary

 Offline Offline
Activity: 2968
Merit: 1198

|
 |
September 23, 2014, 06:37:52 AM |
|
He got scared of the FBI thingy and decided to deny what he did.. haha
Plausibile deniability is smart. If I were him my Polo password would be "secret123" |
|
|
|
|
|
Kuriso
|
 |
September 23, 2014, 06:42:30 AM |
|
So u r first test was? Confused ...
I did not DDOS Poloniex period. I have no reason to. ~BCX~ OldManKidd banned for 10 hours after you threatened the exchange (or what seemed like a threat). See the quotes below. Shortly after this, Polo had a DDoS attack. "BitcoinEXpress" was the user. This is the same user you confirmed was you earlier on. See this post: https://bitcointalk.org/index.php?topic=789978.msg8907819#msg8907819How did this user gain access to your account? Shit about to hit the fan 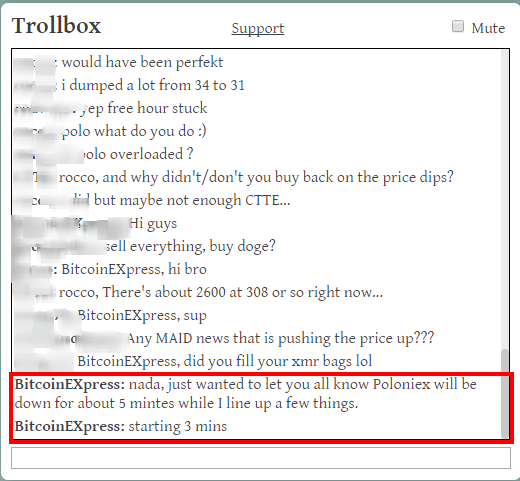 all i have... redwine: yep free hour stuck rocco: polo what do you do  maqa71: polo overloaded ? CTTE: rocco, and why didn't/don't you buy back on the price dips? rocco: i did but maybe not enough CTTE... BitcoinEXpress: Hi guys godofdefire: sell everything, buy doge? rocco: BitcoinEXpress, hi bro CTTE: rocco, There's about 2600 at 308 or so right now... maqa71: BitcoinEXpress, sup chickundinner: Any MAID news that is pushing the price up??? maqa71: BitcoinEXpress, did you fill your xmr bags lol BitcoinEXpress: nada, just wanted to let you all know Poloniex will be down for about 5 mintes while I line up a few things. BitcoinEXpress: starting 3 mins rocco: BitcoinEXpress, aight twotimer: BitcoinEXpress, good luck wid dat maqa71: WTF CTTE: BitcoinEXpress, so, you're attacking polo? BitcoinEXpress: just testing for the monent BitcoinEXpress: 2 mins twotimer: he's a trolll... good luck DB BitcoinEXpress: will be down 5 mins CTTE: someone has a "god " complex Then this new user, bitc-2af6 comes on and tries to threaten the exchange again. trollboxMessage,2015502,bitc-2af6,busoni@poloniex, I only wanted to get your attention earlier, notice I did no real damage
...
trollboxMessage,2015607,bitc-2af6,busoni@poloniex, did you see my earlier message
trollboxMessage,2015608,busoni@poloniex,bitc-2af6, which one?
trollboxMessage,2015615,bitc-2af6,busoni@poloniex, notice on TW
...
trollboxMessage,2015621,bitc-2af6,busoni@poloniex, So I take it you wish to do this the hard way?
...
trollboxMessage,2015637,bitc-2af6,30 minute time out for your whole site. Whne I bring you back up I suggest you get serious.
...
trollboxMessage,2015645,busoni@poloniex,bitc-2af6, you can attack all you want, I still won't know what you're talking about until you tell me.
...
trollboxMessage,2015697,bitc-2af6,Zohann, in 2 minutes you guys are going down hard for 30 mins, I came to speak and get ignored.
...
trollboxMessage,2015718,bitc-2af6,Ignore me agin in 30 minutes and I wil take you down for days I'm betting this bitc-2af6 guy is just a troll but was the first part not you? |
|
|
|
|
|
adept
|
 |
September 23, 2014, 07:00:43 AM |
|
Why does anyone give a shit about this "FUD"?
If there is any exploit in Monero, the coin will be forked again and the hole plugged, this will all be forgotten in a week.
He'll show his cards and that's that.
BcX is just a lonely bored wanker with nothing better to do than cash in on his Hero profile super-FUD for cheap XMR.
|
|
|
|
|
|
adept
|
 |
September 23, 2014, 07:05:50 AM |
|
Why does anyone give a shit about this "FUD"?
If there is any exploit in Monero, the coin will be forked again and the hole plugged, this will all be forgotten in a week.
He'll show his cards and that's that.
BcX is just a lonely bored wanker with nothing better to do than cash in on his Hero profile super-FUD for cheap XMR.
Is it just me or does this guy look familiar LOL ~BCX~ @Kuriso, PM sent. Not sure what's funny, you just got pwned. kthx im outta here. incredibly boring and way too tedious to analyze further. i would try and trade this situation but XMR has barely moved. If you want to make money people, set some bids. I predict a dip and instant recovery from 0.0027-29 tomorrow back to 0.004 after this is laughed off. |
|
|
|
|
cAPSLOCK
Legendary

 Offline Offline
Activity: 3738
Merit: 5127
Whimsical Pants

|
 |
September 23, 2014, 07:06:01 AM |
|
Why does anyone give a shit about this "FUD"?
If there is any exploit in Monero, the coin will be forked again and the hole plugged, this will all be forgotten in a week.
He'll show his cards and that's that.
BcX is just a lonely bored wanker with nothing better to do than cash in on his Hero profile super-FUD for cheap XMR.
Is it just me or does this guy look familiar LOL Sock puppetmaster target acquired.  |
|
|
|
|
|




