 Show Posts Show Posts
|
|
Pages: [1] 2 »
|
Edit: La cuenta era falsa
Me sigue Chun en X (antes twitter), se me hacía raro colocar como título solo "Me sigue Chun en X" valla que es un nombre muy ambigüo. Pues si!, tengo twitter: https://twitter.com/albertobsd aunque casi no publico mucho ahi generalmente doy retuits de noticias o publicaciones interesantes. En fin el post es solo para comentar el hecho de que recientemente me ha seguido Chun, dirán ustedes Chun quien? Bueno su usuario en X es @satofishi y a lo que tengo entendido es Co-fundador de F2Pool Sinceramente no lo conocía hasta que salió la noticia de la transacción de bitcoin con casi 20 BTC en comisiones : TX de BTC envía 0,0740544 BTC … y paga 19,82108632 BTCs en fees de hecho me toco hacer retuit a una de sus publicaciones pero de ahi en mas no interactúa mucho con sus publicaciones en esa red. Se me hace raro que me siguiera, no se si solo sean de esos seguimientos temporales para después dejar de seguirme, en cualquier caso me da igual a no ser que me quiera ofrecer empleo o algo asi. Quizás el post vaya mejor en esquina libre, pero tal vez ahí no note mucho la publicación |
|
|
|
Hi guys, I wonder when we are going to be able to set the fees of our transactions under 1 sat/vB. Actually we can set some random amount of fees above that amount like 1.01, ... 2.17 etc.. or something like that example: 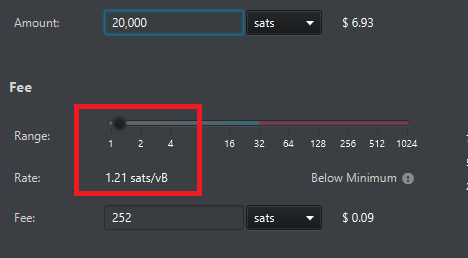 We only drag the bar or we typed manually the amount of fess etc... I know that this actually is not fair for miners but lets to said that bitcoin hits 1 Million USD some day ( Hypothetically speaking ) that means that 100 satoshis will worth 1$ USD So now imagine a regular Transaction with some high fee of ~30 Sats/vB with one input and two outputs 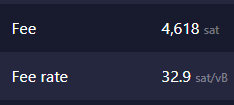 . Currently that is 1.6$ USD, but in our Hypothetic example that is going to be like 46$ USD per transaction So the question here: Is there some mechanics in the consensus of bitcoin to start accepting fees under 1 sat/vB ? example... 0.58 sat/vBWhen bitcoin started a lot of miners used to acept transactions with NO fee. Now if you manually craft a transacction with lower fee that will be rejected by the network. |
|
|
|
I know that those aren't a common kind of posts here but i today i saw one more of them, so here is the compilation: Bitcoin puzzle (3,350.00 BTC's )The user bytcoin offers a bounty of 3350 BTC to anyone who can solve his forged signature he explain the relationship between the original signature and the forged one. math puzzle - if solve I pay:)The user ecdsa123 offers a small bounty of 2000$ USD to anyone who can provide an algorithm to break ECDSA having two random signatures. Some BTC to whom solve the puzzleThe user itiswhatitis12345 offers a bounty of 0.1 BTC to anyone that can reverse some specific sha256 hash, his only hint is that the original text is a "meaningful sentence" If you know some other challenge/puzzle and you believe that it is fake/unsolvable please let me know. |
|
|
|
Muy buen dia, recientemente estoy haciando tradeos aqui y alla y tengo varios contactos que utilizan una u otra red, es una verdadera molestia pero asi es la cosa... Hoy estoy tratando de utilizar la red TRON por primera vez y me encuentro con un comportamiento curioso en dicha red. Si quiero mandar TRX sobre la misma red la cartera me indica que no cobra comision de RED (Imagino que a de ser una comision pequeña que no esta en los 2 puntos decimales que se ven ahi) 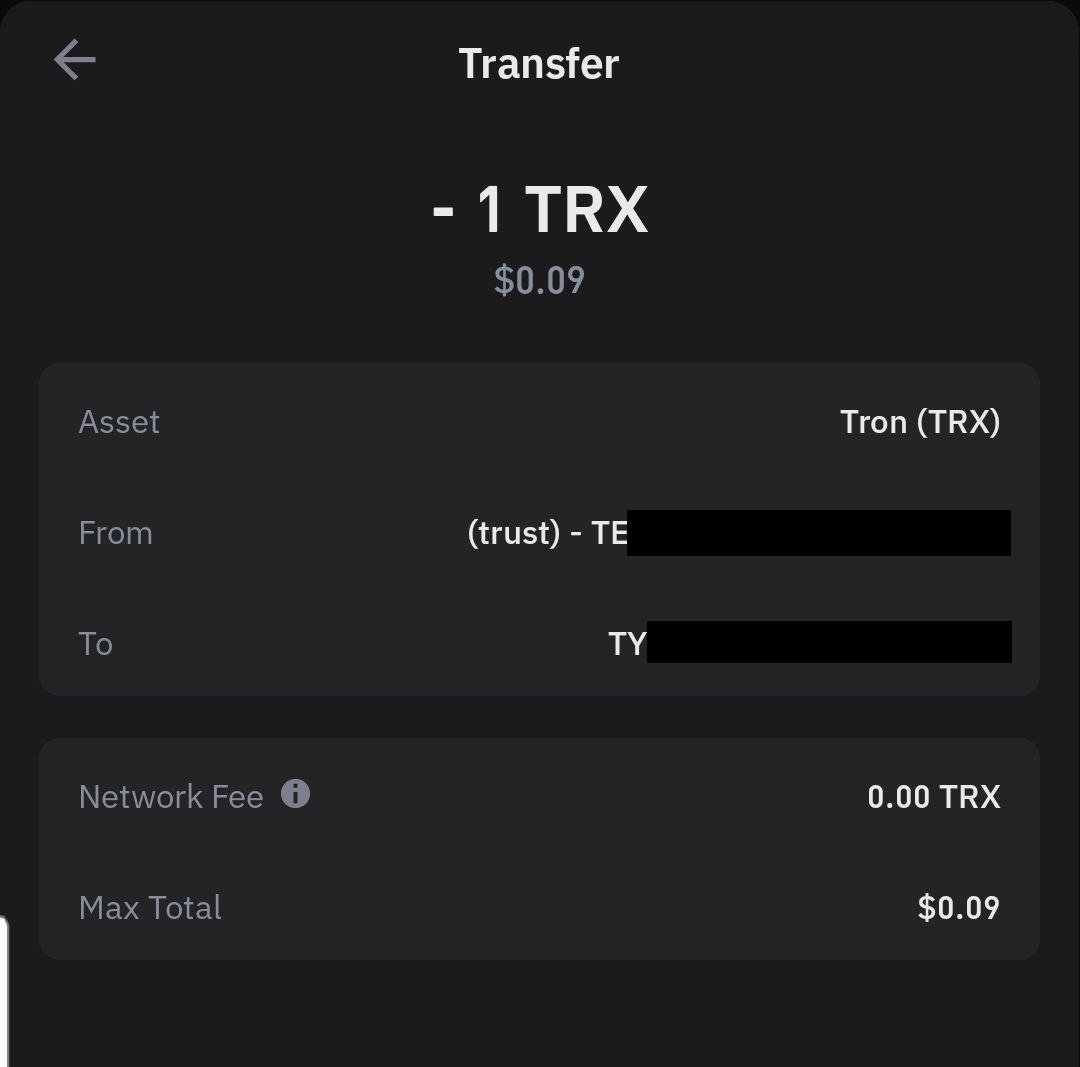 Pero si quiero mandar USDT sobre esta RED la cartera me indica que la comision son sobre 27 TRX  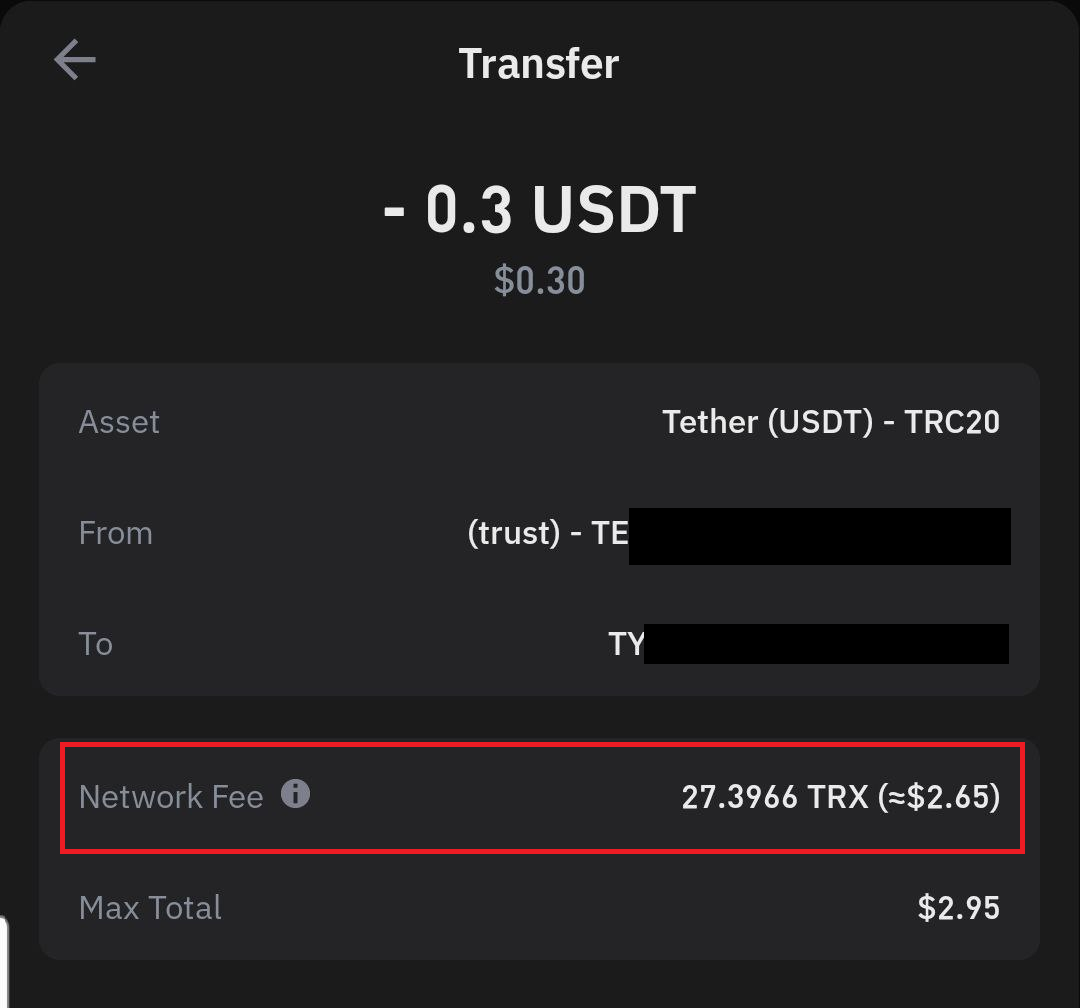 Entonces no se si es cosa de que la cartera esta haciendo mal el calculo, o realmente existe dicha diferencia de comision.
Edit. Intente cambiar de cartera para validar si era solo problema de esta Wallet pero resulta que tambien en la otra Wallet cobran una comision Exagerada. 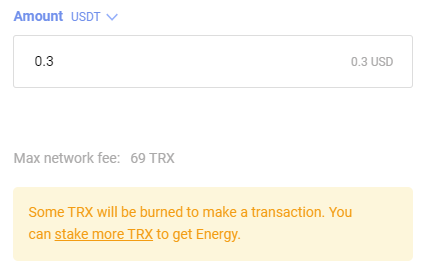 WTF?  ? Sinceramente no se que pensar de esta red de Mierda... Alguien puede explicar que esta pasando? |
|
|
|
Hoy fui a la ciudad a realizar algunos pendientes, normalmente tardo en llegar a la ciudad motivo por el que casi no voy, ya que queda muy lejos del pueblo donde vivo. En uno de los centros comerciales me tocó ver un cajero de bitcoin, primera vez que veo uno en persona.  De entrada solo ofrece comprar o vender Bitcoin y USDT en la red de TRON.  Los precios están muy inflados Se alcanza a ver el tipo de cambio de de 36589$ USD por Bitcoin (No le pierden?) Independientemente de que el precio era una estafa no resiste la tentación de cambiar algo de fiat por bitcoin, lamentablemente el cajero no acepto mis billetes, supongo que ya estaba lleno o no se. Sin duda es una forma muy interesante de cambiar tu Fiat por bitcoin, así mismo es una forma fácil de "lavar" el dinero. Hubiese sido interesante ver de donde provienen los fondos de ese cajero. La proxima vez que me toque ir a la ciudad voy a intentar comprar de nuevo. Saludos! |
|
|
|
Concerns about Samourai Wallet (Access to Clipboard without permission) Hi guys i just want to let you know that I am deinstalling Samourai wallet from my android device, an also i am moving my utxos from that Seed to my cold wallet Why? I just noticed that Samourai wallet is Accessing to the clipboard with permission and without asking and without trigger.. How? Some days ago I just activate one android option to alert me every time that an APP access to the clipboard, so when i do a long press in the touch to paste some informacion in the clipboard i get an screen notification " APPNAME pasted from your clipboard". 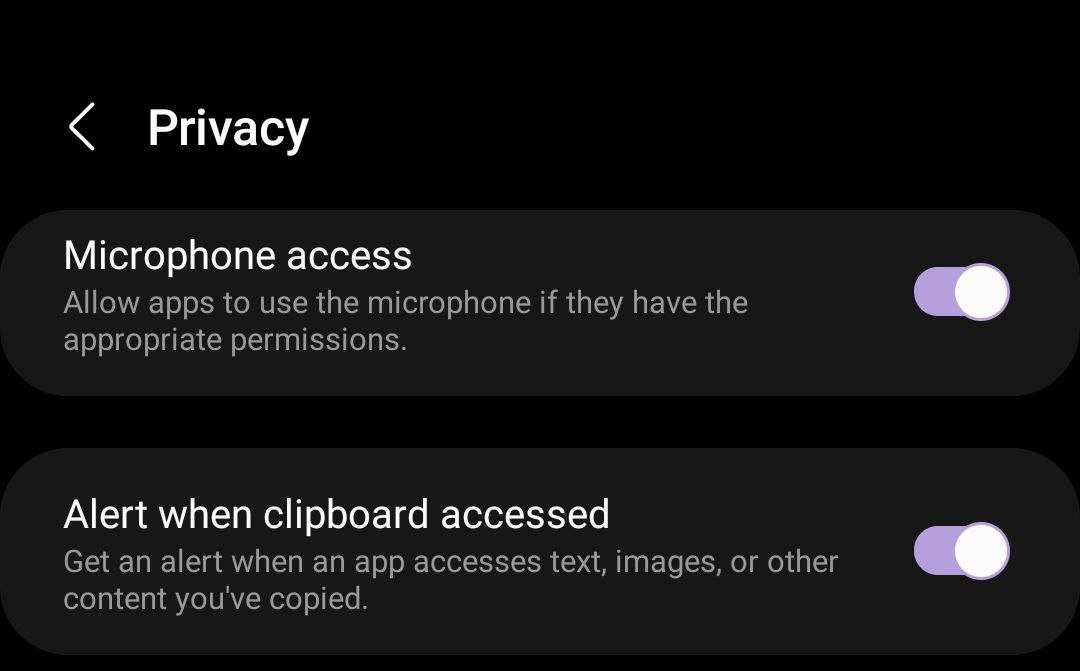 Almost all Apps work fine without any suspicious activity in this way, BUT i just notice that Samourai Wallet just do that at when you open it check the image: 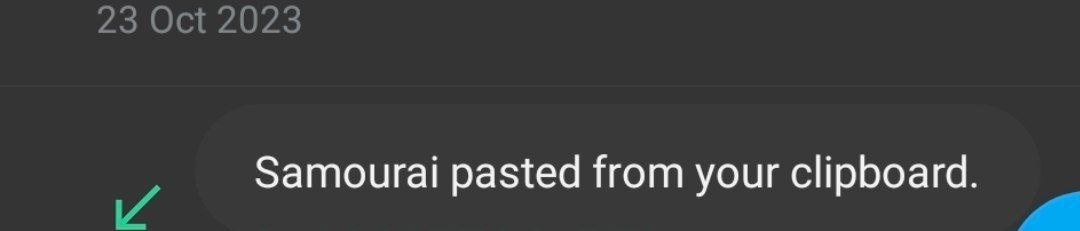 When that notificacion pops? When I start the samourai wallet for the first time after unlock the pin screen, without doing anything else, that notification appears What do you thing about this behaivor of that APP ?
Edit: Looks like they do a clipboard check for your "security". In my Opnion this should be optional and only activated at the user request. |
|
|
|
Note for the moderator, since there is no one cyber-security Board i put this topic here because i believe that this tool can be used to backup seeds, passwords, passphrases, privatekeys and other secrets
Hello everyone, I want to share with you one simple tool to store passwords securely.https://www.passwordstore.org/If you don’t know it, password store is an open source project written in bash that uses GPG to store passwords encrypted with your GPG private key, that means that only you will be able to decrypt them. I like this tool because it is a command line tool, i can use it on Linux, Windows (WSL) and Android (Termux) . It can be synchronized between devices with a git, so that means you can have a unique password repository in all your devices. You only need to have the same GPG private key between them. You can edit the password store using ordinary unix shell commands alongside the pass command. There are no funky file formats or new paradigms to learn. There is bash completion so that you can simply hit tab to fill in names and commands, as well as completion for zsh and fish available in the completion folder. The very active community has produced many impressive clients and GUIs for other platforms as well as extensions for pass itself.
So it’s a simple a bash tool to organize password stored in individual files encrypted with GPG Password store already have some years: Initial release: September 4, 2012; 11 years ago GnuPG also have more years: Initial release: 7 September 1999; 24 years ago With those years in the market most common bugs should be already fixed and almost all security flags also were already catched I am using this tools to manage my passwords and other secrets like seeds and private keys, maybe some of you will point to keepass or some other private solution like 1Password, but i like this because its originally a command line tool and I can use it on all my devices, Linux, windows and android. Obviously it needs to have its precautions, like backing up the GPG private key securely and other things all depending on how paranoid you are with all those things.
|
|
|
|
Muy buen dia dejare aqui una guia express para utilizar GPG, Aqui doy por entendido que ya lo tienen instalado en su sistema. Crear una llave paso por paso:gpg --full-gen-key --expert Con este comando podremos crear una llave paso a paso, personalmente recomiendo una llave ed25519 ya que son llaves pequeñas, seguras para los estandadres modernos y muy rapidas de generar/firmar/cifrar Para generar una llave ed25519 hay que seleccionar las opciones: Luego Y el detalle de la expieracion de la key se lo dejo al criterio de cada quien. NOTA IMPORTANTE, el proceso te va a pedir un password, Trata de que sea un password que recuerdes muy bien y de preferencia tenerlo respaldado, ya que si lo pierdes no habra manera de recuperar tu llave privada.Listar llaves privadasEsta es la llave que recien generamos solo con las llaves que aparecen en esta lista podremos firmar y cifrar documentos Listar llaves publicasEsta es una lista de todas las llaves publicas que estan guardardas, generalmente solo aparece nuestra llave publica, pero si ya hemos importado la llave publica de alguien mas, esta tambien aparecera listada. Importar llaves publicas de alguien masgpg --import their_public_key.asc en el archivo their_public_key.asc (Que podria tener cualquier otro nombre) se encuentra la llave publica de otra persona y la podremos importar a nuestra lista para en el futuro poder cifrar mensajes que solo el destinatario pueda leer.
Pudes tratar de impotar mi llave publica, guarda el siguiente texto en un archivo de texto y luego importarlo con el comando anterior:
Mi llave publica es:
-----BEGIN PGP PUBLIC KEY BLOCK-----
mDMEZSGE8hYJKwYBBAHaRw8BAQdAVaD+e9jobVYRJtg0hs/FOaED+2U3WRMoNmzU
fVXrvaO0IWFsYmVydG9ic2QgPGFsYmVydG9ic2RAZ21haWwuY29tPoiQBBMWCAA4
FiEEcPyyF88mxDTnyu++7UQ4Plx1G84FAmUhhPICGwMFCwkIBwIGFQoJCAsCBBYC
AwECHgECF4AACgkQ7UQ4Plx1G87l+gD/QS6Pc9lafJIpl4v1sOJOG8nr5zg8/gep
lKx5evXvXMMBAOFupEvid0juHvIowTA090jophE49NNGuoJRw3FAGjgFuDgEZSGE
8hIKKwYBBAGXVQEFAQEHQCthQ0Ma0WnygqMLe9zBU9TZ4Blc0/nbBPBWKHWcTjdL
AwEIB4h4BBgWCAAgFiEEcPyyF88mxDTnyu++7UQ4Plx1G84FAmUhhPICGwwACgkQ
7UQ4Plx1G87wHQEAi8xRkg0MgFdVXXzIxckSdblvb5HV0un96fmBPZo1WOwA/0Xn
jyqFAOn1bvQrgo3oxN7sOjfpsaKhUaupv7/yvNMM
=GFvH
-----END PGP PUBLIC KEY BLOCK----- gpg --export --armor "Name or Email or KEY ID" > public_key.asc Con este comando podras exportar tu llave publica o la de alguin mas (Previamente tu ya deberia de haberla importado). Nota que la salida es redirigida a un archivo de texto public_key.asc. Firmar un archivo de Textogpg --clearsign --local-user "Name or Email or KEY ID" -o signed_message.txt message.txt Si quieres firmar un archivo de texto para autenticar que tu lo generaste o demotrar que tu tienes el control de determinada llave privada utiliza el comando anterior. Al archivo a firmar es menssage.txt y el archivo resultando es signed_message.txt menssage.txt albert0bsd signing a message for bitcointalk post on Oct 7, 2023
signed_message.txt -----BEGIN PGP SIGNED MESSAGE-----
Hash: SHA256
albert0bsd signing a message for bitcointalk post on Oct 7, 2023
-----BEGIN PGP SIGNATURE-----
iHUEARYIAB0WIQRw/LIXzybENOfK777tRDg+XHUbzgUCZSGILAAKCRDtRDg+XHUb
zhKvAQDLvqt3wEhiIK+P5umf5HJNqgPDchgndg8JRLHWsC5U2QD/fv8FEQZQr75K
68BsHna/htaTBMOnfPOuZGYJzmr4WQE=
=1C8J
-----END PGP SIGNATURE-----
gpg --verify signed_message.txt Puedes verificar mi mensaje firmado o el de alguien mas con el comando anterior gpg: Signature made Mon Oct 9 07:46:40 2023 CST
gpg: using EDDSA key 70FCB217CF26C434E7CAEFBEED44383E5C751BCE
gpg: Good signature from "albertobsd <...>" [unknown]
gpg: WARNING: This key is not certified with a trusted signature!
gpg: There is no indication that the signature belongs to the owner.
Primary key fingerprint: 70FC B217 CF26 C434 E7CA EFBE ED44 383E 5C75 1BCE
Haz caso omiso del warning lo que nos interesa es: gpg: Signature made Mon Oct 9 07:46:40 2023 CST
gpg: using EDDSA key 70FCB217CF26C434E7CAEFBEED44383E5C751BCE Primary key fingerprint: 70FC B217 CF26 C434 E7CA EFBE ED44 383E 5C75 1BCE Si la llave coincide con la llave esperada entonces la persona que firmo el mensaje tiene control sobre la llave privada ligada al mismo. Cifrar un mensaje para que solo pueda ser visto por un solo destinatariogpg --encrypt --recipient "Recipient Name or Email or KEY ID" --armor --local-user "Recipient Name or Email or KEY ID" -o encrypted_message.asc message.txt El archivo de entrada es message.txt y el de salida es encrypted_message.asc Aqui pueden cifrar un mensaje para mi y si lo puedo descifrar les mandarare un mensaje para que lo descifren ustedes, si hacen esto solo respondan a este mensaje con el mensaje cifrado, no se olviden de publicar su llave publica tambien, aqui o de preferencia en el siguiente hilo: https://foro.elhacker.net/criptografia/pgpgpg_public_key_database_guarda_tu_llave_publica_aqui-t518947.0.htmlDescifrar un mensaje Que te enviarongpg --decrypt encrypted_message.asc No hay mucho que decir, si tu tienes la llave privada asociada a la llave publica que se utilizo como destinatario del mensaje cifrado, entonces tu seras capas de descifrar el mensaje. Y por ultimo Respaldar tu llave privadagpg --export-secret-keys "Recipient Name or Email or KEY ID" > backup-key.asc |
|
|
|
Muy buen días, hoy les quiero compartir una de las que creo es la mejores herramienta para administrar sus passwords de forma segura. https://www.passwordstore.org/Si es que no lo conocen, password store es un proyecto de código abierto escrito en bash. Este te permite administrar tus contraseñas de forma segura cifradas mediante tu llave privada de GPG (Por lo cual tu y solo tu podras decifrar). Por lo que básicamente se convierte en una llave para gobernarlas a todas. Lo cual y estoy conciente es un riesgo, pero si ya le confiamos nuestros password y estos están cifrados mediante GPG por que no confiarle otros secretos como llaves privadas o mnemonicos de bitcoin y otras criptomonedas? GPG es una herramienta que ya tiene su tiempo en la comunidad de Open source: https://es.wikipedia.org/wiki/GNU_Privacy_GuardPor lo que el tema de seguridad de la misma ya esta bastante depurado. Temas de seguridad a tener en cuenta. - Tienes que tener respaldada tu llave privada GPG - Tienes que tener respaldo tu password de tu llave privada - Es conveniente tener una máquina y cuenta separada para respaldar seeds con este método (Esto ya depende de cada quien y que tan paranoico sea uno) En lo personal he dejado de utilizar el gestor de contraseñas de google y he terminado de pasar todos los password a este gestor con mis respectivas precauciones, Llave GPG respaldada offline, Password respaldado. Muchos tal vez confían en gestores como 1Password y otros, sin embargo estos al ser de código cerrado y con un largo historial de hackeos a empresas similares, Por lo siento Password store es una alternativa más segura que los anteriores. |
|
|
|
|
I know that this is not a specific of bitcoin topic but let me change the question a little
If you want to organize your UTXOS in some way with some specific denominations/balance, which one do you want to choose?
For example some mixers use utxos of
0.001BTC
0.01BTC
0.1 BTC
...
And maybe others denominations
I remember to see some time ago the chips from chipmixer in some base of two denominations:
0.001 BTC
0.002 BTC
0.004 BTC
0.008 BTC
….
1.024 BTC
2.048 BTC
4.092 BTC
8.196 BTC
In the Fiat money that we use almost daily there are denominations of 1,2,5 for coins and banknotes, example for some bank notes:
€5, €10, €20, €50
$1, $2, $5, $10, $20, $50, and $100
Just to mention some of them…
This is only for the first organization for some mixing.. After this it will be as usual some 1 or 2 inputs to 1 to more outputs and the change address with any random amount - fees
So here is the question again.
If you want to organize your UTXOS in some way with some specific denominations/balance, which one do you want to choose and why?
I would like to read your answers.
My favorite option is ther first option: 0.001BTC 0.01BTC and 0.1 BTC
Regards!
|
|
|
|
|
Well, I am just asking.
Do you consider this important? Usually when we request some payment in bitcoin, we don't care where those funds comes from. But what happens when some of us try to cash out that balance through some CEX to your bank account
I've readed histories here where people get their funds stuck for weeks or months and that would be frustatransing.
So again the question: Is it important to check addresses for AML before doing transactions with it?
Most of the AML checks services offer only a few checks per month, why?
Obviously if we don’t have any plan to cashout that balance we don’t care much about AML checks.
Is there some free unlimit service to check for AML?
What are your thoughts about this?
Regards!
|
|
|
|
Good day, i want to buy bitcoin periodically from 50$, 100$ or 200$ USD periodically in times of 1 week, 15 days or one month respectively Only one of the previous options. Price listed on https://mempool.space/tools/calculatorConditions: - Your accound must be an active account. - You need to be atleast Full member Trust: - Only full members or above user, account need to be active in the forum. - No negative/red trust I pay the bitcoin network fees! - You can use this transaction to consolidate your utxos, up to 3 inputs and only 2 outpus (One of those output is to my address) - I send the total amount + the fee that you pay for the Transaction, if and only if the it is an optimal fee +/- 2 sat/vB according to the average fee by the transactions in the same block where the transaction was mined (Page use to check it is mempool.space) I pay after receiving the bitcoin on my address with at least one confirmation. - Payment method to be determined, i have only a few options here (I send you USDT to your Binance account), maybe paypal, suggestions? Privacy - To keep the privacy for both sides, the address and txid will not be disclosed unless there is some dispute (In that case open new topic in reputation) - I will provide a different address for each period, that address will be in a signed message with my public address in the forum. Verification - We need to provide a signed message with the address to deposit and other relevant instructions. - The signed message should be signed with a PGP Public key or Bitcoin public address. - For PGP public key see topic: The BCT PGP/GPG Public Key Database: Stake Your PGP Key Here- For Bitcoin address see topic: Stake your Bitcoin address here- My PGP public key is on Re: The BCT PGP/GPG Public Key Database: Stake Your PGP Key Here - My public address is on my profile and in that same topic: Re: Stake your Bitcoin address here - If you don't have a verified bitcoin public address or PGP public kry, please publish it on those topic. Questions: Why do I offer this outside of a CEX? - To avoid biggers fees (CEX charge fees when you buy it and also when you retire to an auto-custodial wallet) - To avoid KYC (On the bitcoin side) - To gain a little of Trust Send me a Direct message if you have doubts or if you are interested in trading with me. |
|
|
|
|
¡Hola a todos!
Necesito algunos consejos sobre cómo comprar Bitcoin sin perder una gran parte de su valor. Aquí está la situación: compré algunos Bitcoins en CEX, pero cada vez que los transfiero a mi billetera no custodial, termino perdiendo alrededor del 7 al 10% de su valor, esto incluye las comisiones pro compra en red P2P dentro del exchange, retito y comisiones de red. Eso es mucho, y quiero encontrar una mejor manera de comprar Bitcoin en la que no pierda tanto durante las transferencias.
¿Alguien puede compartir su experiencia o sugerir una plataforma o método que ofrezca tarifas más bajas al comprar y transferir Bitcoin? ¡Realmente apreciaría su ayuda.
Gracias!
|
|
|
|
|
Hey everyone.
I need some advice on buying Bitcoin without losing a chunk of its value. So, here's the deal: I bought some Bitcoin on CEX, but every time I move it to my non-custodial wallet, I end up losing around 7 to 10% of its value this include bank fees, exchange fees and network fees. That's a lot, and I want to find a better way to buy Bitcoin where I don't lose so much during transfers.
Can anyone share their experience or suggest a platform or method that offers lower fees when buying and transferring Bitcoin? I'd really appreciate your help! Thanks!
|
|
|
|
|
to be deleted, moved to archive
|
|
|
|
Muy buen dia como dice el titulo Busco comprar bitcoin de forma periodicaAproximadamente 50$, 100$ o 200$ con periodicidades de 1 semana , 15 dias o un mes respectivamente. Solo una de las opciones anteriores. CondicionesTrust - Tienes que ser al menos Full member y tener cuenta con actividad reciente en el foro - No tienes que tener reputacion negativa Las comisiones de la red de bitcoin van por mi cuenta - Puedes utilizar esa transaccion para consolidar tus utxos hasta 3 inputs, 2 ouputs (Uno de estos es mi direccion) - Te envio en fiat el total de lo pactado mas las comision que pages por la transferencia siempre y cuando sea una comision optima +/- 2 sat/vB deacuerdo al promedio de las comisiones de bloque minado donde se encuentre la transaccion, indicado en la pagina de mempool.space) Yo pago una vez recibido el bitcoin en mi direccion, minimo una confirmacion. - La forma de pago a convenir: Transferenca bancaria (Solo usuarios de MX), Transaferencia en tokens USDT a su cuenta de Binance, paypal, otra? sugerencias? Privacidad - Con el fin de conservar la privacidad de ambas partes, las direcciones y los ID de las transacciones finales no seran revelados en publico a no ser que exista alguna disputa. (Abrir nuevo tema en el tablero de reputacion) - En cada periodo pactado para compra, mandare una direccion de destino diferenteVerificacion - Con el fin de poder tener evidencia y forma de verificar las direciones proporcionadas para deposito de los fondos de ambas partes se utilizaran mensajes de texto firmados con las direcciones publicadas en Stake your Bitcoin address here- Mi direccion publica en el foro esta en Re: Stake your Bitcoin address here y en mi perfil - Si no tienes direccion publica verificada puedes publicarla en este momento en ese mismo hilo. Preguntas: Por que hago esto esto fuera del exchange? Debido a las altas comisiones cobradas por los mismos cuando tratas de sacar el balance a una cartera autocustodiada. Otro motivo es hacerlo en el foro y ganar algo de reputacion. Enviame un Mensaje Directo si tienes dudas o estas interesado en tradear conmigo. |
|
|
|
This days there is low congestion on the mempool, and that is good for users tha want to consolidate their utxos, recently some 3 sat/vB transactions has been accepted in some blocks Anyway regardless this low fee hours, there are some poor managed exchanges or entities that looks they don't know what are they doing or how the fees works on the bitcoin mining process looks like they think that if they keep sending more fees the miner is going to mine faster or something like that. AND THAT IS NOT TRUE. The miner actually don't care how much fee you pay they are going to mine at their same speed proof of that is that the ~19.82 Bitcoin fee stay almost 7 minutes on mempool before being mined: Broadcasted on 10 Sep 2023 5:02:56
Mined on September 10, 2023 5:10:01 Almost 7 minutes on mempool I know that those entities have enough to throw away hundreds of sat/vB without care about of it, but Is not their main goal to maximize their profit?I think that this problem is generated by a poor fee estimator in some cases, but in others i think that it is a problem of a really bad developer or business policies. But in any case, if you need to make a RBF or a FullRBF Transaction you only need to increment your Fee by 1 sat/vB, not by hundreds: 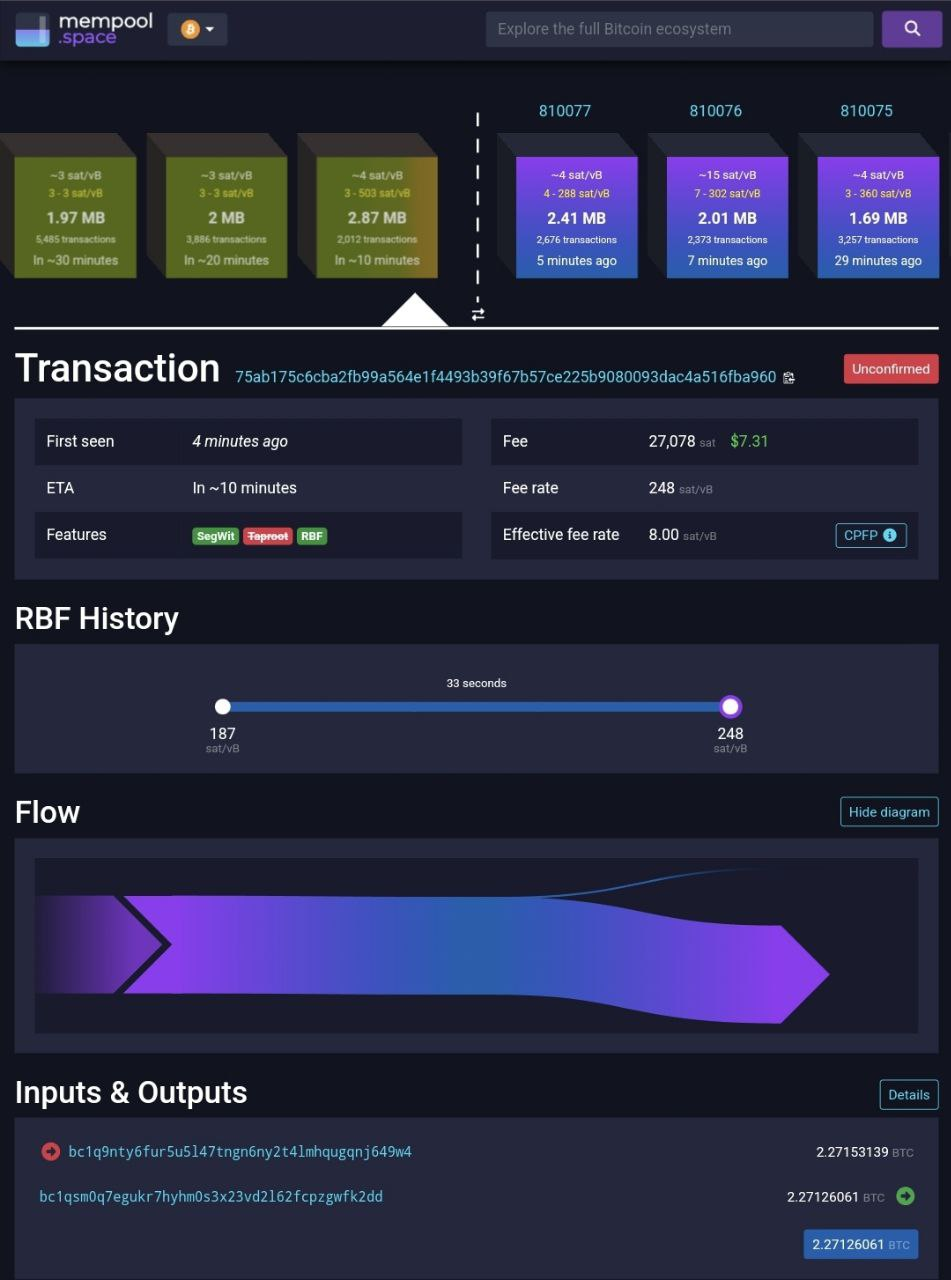 Just to put an example of it, for more you only need to go to the rbf page of the mempool.space page: https://mempool.space/rbfIn this post i only want to express my discomfort with all those developers and poor automated entities/business What do you think about this? Is there some developer working for those organizations that can explaint why they do that?
A little of humor/offtopic:  |
|
|
|
Mirror del hilo en Ingles ( Keyhunt - development requests - bug reports) Quiero abrir este Tema para hablar de la herramienta para CPU de Codigo abierto que he dessarrollado Keyhunt disponible en github Keyhunt utiliza el algoritmo BSGS para intentar encontrar llaves privadas mediante el uso de la llave publica de una direccion de bitcoin. El principal objetivo de esta herramienta es tratar de encontrar los desafios/rompecabezas de bitcoin descritos en Bitcoin puzzle transaction ~32 BTC prize to who solves it Acutalmente los desafios tienen mas de 800 bitcoin pendientes por reclamar Keyhunt tambien utiliza otros metedos tambien como: address, rmd160, xpointVersion actual 0.2.230430 Satoshi QuestComo UtilizarloDescarga y compila (Sigue la documentacion en Ingles  ) Ejecutalo contra el puzzle 66 (modo address)./keyhunt -m address -f tests/66.txt -b 66 -l compress -R -q -s 10 Se necesita agregar el parametro -t <Numero de Hilos> para mejorar la velocidad Ejecutalo contra el puzzle 130 (modo BSGS)./keyhunt -m bsgs -f tests/130.txt -b 130 -q -s 10 -R Se necesita agregar el parametro -t <Numero de Hilos> para mejorar la velocidad, asi mismo como el parametro -k <factor> |
|
|
|
Before to all i want to remember to everybody that TESTNET coins are worthless and never supposed to have any real value.Quoting: https://en.bitcoin.it/wiki/TestnetTestnet coins are separate and distinct from actual bitcoins, and are never supposed to have any value. The only value that they provide are experience for developers, testers and other people that want to undertand and practice how bitcoin works without spend real bitcoins. I am doing recently some test on testnet to test features like CPFP, RBF and FullRBF, testing scripts and a long etc... But something change in the difficult of testnet in the last hours, somebody is mining like 5 blocks per second, so if someone wants to learn how to mining they can try Testnet on this momment. 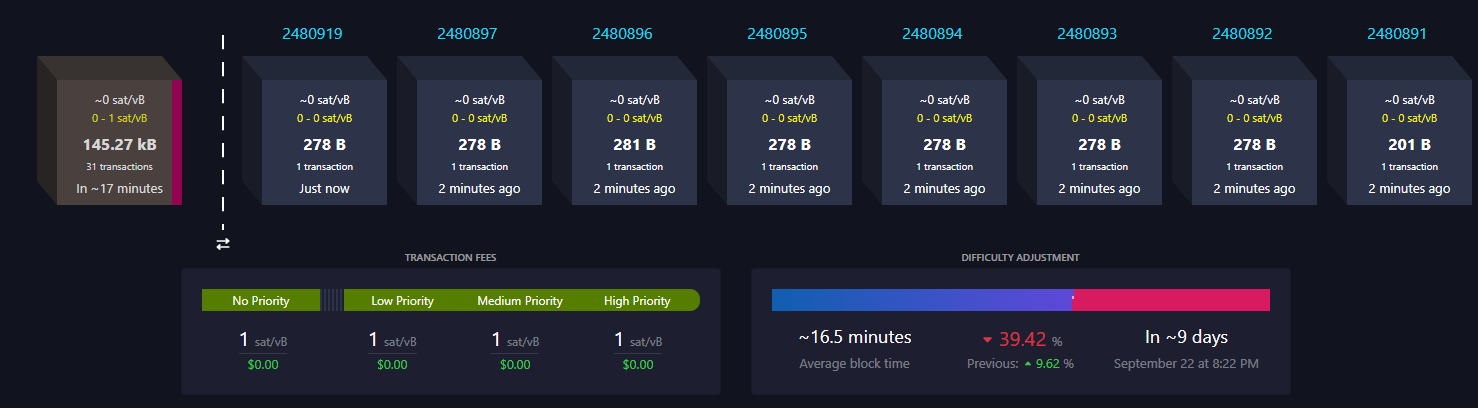 Quoting againt the bitcoin.it page Minimum difficulty of 1.0 on testnet is equal to difficulty of 0.5 on mainnet. This means that the mainnet-equivalent of any testnet difficulty is half the testnet difficulty. In addition, if no block has been found in 20 minutes, the difficulty automatically resets back to the minimum for a single block, after which it returns to its previous value. According to it, the difficulty is reset to the minimum for a single block and then ir should return to the minimum. But in this ocassion that doesn't happend, i guess that the difficulty just drop to the minimun. See it on real time on https://mempool.space/testnetThe block mined by a single addres are from 2477663 to 2481082 up to this time, not much just like 4 thousand blocks. Anyway this is just a little interesting for me because mining is a new topic for me. Regards |
|
|
|
|



 .
.









 )
)