 Show Posts Show Posts
|
|
Pages: [1] 2 3 4 5 »
|
 https://www.justice.gov/usao-cdca/pr/socal-man-arrested-federal-charges-alleging-he-schemed-advertise-and-sell-hive https://www.justice.gov/usao-cdca/pr/socal-man-arrested-federal-charges-alleging-he-schemed-advertise-and-sell-hiveSo they caught the individual selling it to undercover employee, just the old and traditional way of catching criminals After advertising the Hive RAT, according to the indictment, Chakhmakhchyan exchanged electronic messages with purchasers and explained to one buyer that the malware “allowed the Hive RAT user to access another person’s computer without that person knowing about the access.” After this purchaser told Chakhmakhchyan that “the point” of using the Hive RAT was because the victim had “20k in bitcoin on a blockchain wallet” and “project files worth over 5k,” Chakhmakhchyan agreed to sell the Hive RAT, the indictment alleges. Later, Chakhmakhchyan allegedly also sold a license for the Hive RAT to an undercover employee of a law enforcement agency.
And he was charge with,
- to advertise a device as an interception device
- to transmit a code to intentionally cause damage to a protected computer
- and to intentionally access a computer to obtain information
- as well as one count of advertising a device as an interception device
Each count carries a statutory maximum penalty of five years in federal prison.
Good riddance, hopefully he will get the maximum sentence and who knows, maybe him and SBF will be in the same jail,  . Kidding aside, good work by the authorities, tracking and the undercover for doing his job. |
|
|
|
I'm sure majority of us are into AI, at least for me I have been trying to learn a lot of tools, like Mid Journey, Capcut, In-video, Leonardo AI, Elevenlabs, Runway and others. So when I say this reports, I was taken aback as how cyber criminals is also leveraging AI tools now to steal our crypto credentiasl as most of them are info stealer. The way it works is that this threat actor will take over a Facebook account, hack it specially those who have a lot of followers and then turn it into face site similar to the original AI tools. - Cybercrooks have taken over Facebook profiles to run sponsored malvertising campaigns impersonating Midjourney, Sora AI, DALL-E 3, Evoto, ChatGPT 5 and many others
- The malicious pages on Facebook are meticulously designed to trick users into downloading purportedly official desktop versions of popular AI software. The cybercriminals behind these campaigns regularly change and adapt the malicious payloads in an attempt to avoid further detection from security software
- The links direct users to malicious webpages that download a variety of intrusive stealers to harvest sensitive information from compromised systems, including credentials, autocomplete data, credit card information, and even crypto wallet information.
- The analyzed campaigns employ malicious ads that contain links to executable files that serve Rilide, Vidar, IceRAT, Nova Stealers. The entire batch of malicious software is often offered as malware-as-a-service by threat actors on specialized forums and channels.
- The malvertising campaigns have tremendous reach through Meta’s sponsored ad system and have actively been targeting European users from Germany, Poland, Italy, France, Belgium, Spain, the Netherlands, Romania, Sweden, and elsewhere.
- The ads use convincing descriptions alongside generated AI videos and photos to lure potential users into accessing malicious payloads
- One particular Facebook page impersonating Midjourney with a whopping 1.2 million followers was active for nearly a year until it was shut down on March 8, 2024. Since then threat actors have continuously set up more fraudulent pages to deliver malicious ads to users.
- The Midjourney malvertising ad campaign was directed towards male Facebook users aged 25 to 55 and had an ad reach of approximately 500,000 individuals from Europe (demographics and reach of the campaign were obtained by tracking Meta’s Ad Library catalog)
The malware included here and most of them have been reported already in this community, Rilide Stealer by @The Cryptovator Vidar by @Lafu Nova StealerAnd one of the well-known AI tools right now, Mid-Journey, had 1.2 million followers and reach of over 500,000 individuals in Europe before being taken down on March 8, this year.  https://www.bitdefender.com/blog/labs/ai-meets-next-gen-info-stealers-in-social-media-malvertising-campaigns/ https://www.bitdefender.com/blog/labs/ai-meets-next-gen-info-stealers-in-social-media-malvertising-campaigns/
I know others will say that we should go and look for the official page and check everything before downloading. But with the recent AI resurgence, including myself joining the picture and taking advantage of it for whatever purpose it may served to me, still there are dangers lurking in the dark specially for us crypto enthusiast and those trying to learn AI. |
|
|
|
Mispadu, a supposedly banking trojan and infostealer that targets LATAM has evolved itself and now venturing not just in that region but other European as well and it also includes crypto exchanges in their crosshair. Sample phishing email sent by the threat actor, which include a PDF attachment that contains the malware as it will download a ZIP file through a URL shortener service.  Below are the target crypto exchanges,  And this is the two Bitcoin addresses associated with the cyber criminals, - bc1qn5fwarp0wesjahyaavj3zpzawsh3mp0mpuw94n
- bc1qzcdrhp30eztexrmyvz5dwuyzzqyylq5muuyllf
The first address has close to 1 BTC already. This address has transacted 62 times on the Bitcoin blockchain. It has received a total of 0.82939740 BTC $55,022.77 and has sent a total of 0.82937010 BTC $55,020.96 The current value of this address is 0.00002730 BTC $1.81. https://blog.morphisec.com/mispadu-infiltration-beyond-latam |
|
|
|
We have been talking about using Mac OS or even Unix flavored for our crypto activities because using Windows based are very dangerous as malwares can easily spread with this OS. However, recently, there was a info-stealer, known as Atomic Stealer. So the threat actor leveraged everything when someone searches for  And then it will redirect them to a fake site . It will ask you to download the installer, that contains the Atomic Stealer. Other supported actions of the stealer include: - collection of usernames and passwords from browser login data
- the ability to pull credit card details
- stealing data from a list of installed crypto wallets, among which are Ledger and Trezor
Although Ledger has blocked it, still we are not sure what is the extend of this malware as it could targets a lot of crypto wallets. 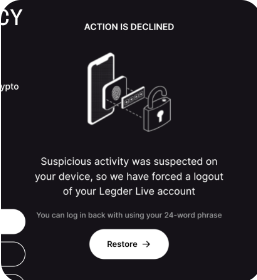
So again, we are not really safe in the world that we live-in. Hackers and criminals are evolving to author malware that will target any OS today and in the future. https://www.jamf.com/blog/infostealers-pose-threat-to-macos/ |
|
|
|
What happened: Fake BlockGames pre-sale website Website: https://events-blockgames.com/ 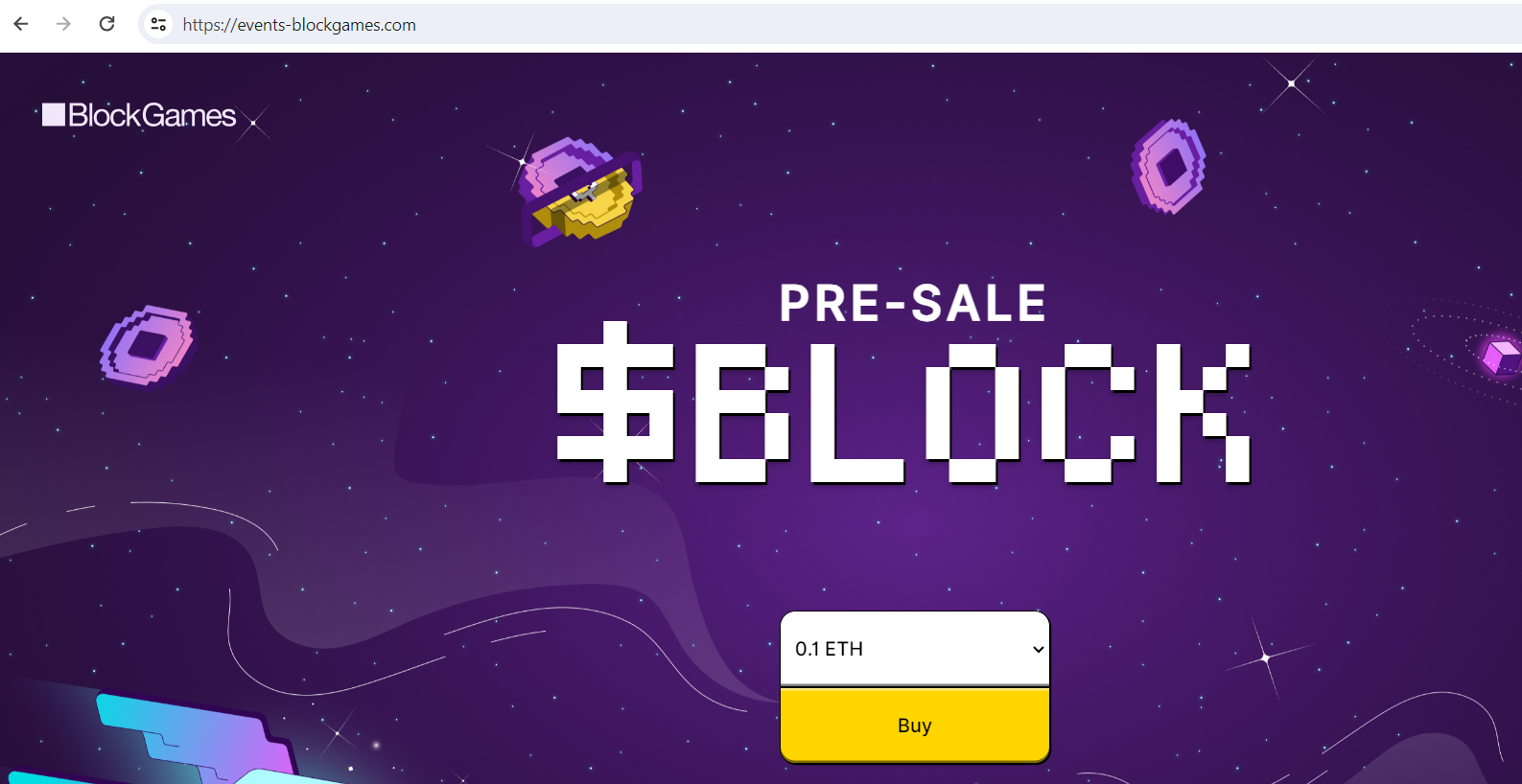 Archive Archive: https://archive.fo/Jo52qDomain info: Domain Name: EVENTS-BLOCKGAMES.COM
Registry Domain ID: 2866050571_DOMAIN_COM-VRSN
Registrar WHOIS Server: whois.nicenic.net
Registrar URL: http://www.nicenic.net
Updated Date: 2024-03-23T08:21:09Z
Creation Date: 2024-03-23T08:21:08Z
Registry Expiry Date: 2025-03-23T08:21:08Z
Registrar: NICENIC INTERNATIONAL GROUP CO., LIMITED
Registrar IANA ID: 3765
Registrar Abuse Contact Email:
Original site: https://presale.blockgames.com/Do not connect your wallet and if you have time then report it here:-> https://safebrowsing.google.com/safebrowsing/report_phish/?hl=en
|
|
|
|
Another malware in the wild dubbed as Azorult malware using fake fronting Google Sites pages and HTML smuggling to steal sensitive information that includes crypto wallet. It is reported that this malware is on the rise and probably it's because of the current bull run that we are seeing. Azorult malware contains a list of 119 target Chrome wallets and 12 Edge wallet extensions. we uncovered a campaign wherein an attacker created fake Google Docs pages on Google Sites from which they used HTML smuggling to download malicious payloads. They lure their victims to the fake Google Docs pages to trick them into believing the downloaded file was from Google Docs. And the payload is The Azorult payload is a .NET compiled. All stolen files and data are then transmitted to the C2 server over HTTP. Targeted Chrome Wallets  Targeted Edge Wallet  Targeted Firefox Wallet  And it looks for this keyword as well: 
So again, cyber criminals activities are ramping up as we go on a bull run already. So we might be very careful time and time again and not let our defense down as the attacks are getting very sophisticated by the day. I think we already have enough information in our community on how to protect our wallets. But from time to time it's also a good practice to revisit it just saying. https://www.netskope.com/blog/from-delivery-to-execution-an-evasive-azorult-campaign-smuggled-through-google-sites |
|
|
|
 https://www.justice.gov/opa/pr/bitcoin-fog-operator-convicted-money-laundering-conspiracy https://www.justice.gov/opa/pr/bitcoin-fog-operator-convicted-money-laundering-conspiracyRussian-Swedish national Roman Sterlingov was convicted by the US DOJ and a faces a max penalty of 20 years in prison. It took them years though, as this mixer existed since 2011 and have a lot of customers with illicit activities as it is rampant during those early days and this individual was taking advantage of it. But then again, the long hand of the law has caught up with them. |
|
|
|
What happened: Scam Smog Token website Website: https://staking.smogtoken.co/  Archive: https://web.archive.org/save/https://staking.smogtoken.co/Whois Information: Archive: https://web.archive.org/save/https://staking.smogtoken.co/Whois Information:Registrar Hosting Concepts B.V. d/b/a Registrar.eu IANA ID: 1647 URL: www.openprovider.comWhois Server: whois.registrar.eu (p) Registrar Status addPeriod, clientTransferProhibited, serverTransferProhibited Dates Created on 2024-03-02 Expires on 2025-03-02 Updated on 2024-03-02 Name Servers NS1.DNS-PARKING.COM (has 4,554,470 domains) NS2.DNS-PARKING.COM (has 4,554,470 domains) IP Address 185.212.70.114 - 52 other sites hosted on this server IP Location United States - Arizona - Phoenix - Hostinger International Limited Criminals are taking advantage as this is one of the hottest airdrop right now. So the UI is very similar and it's really hard for us to catch it as there's not much difference. But please, double or even triple check everything before we connect our Wallet. Please report it to: https://safebrowsing.google.com/safebrowsing/report_phish/?hl=en
|
|
|
|
A package listed on the Python Package Index (PyPI) repository, which has been dormant since it first published to PyPI in April 2022. The package name is, And it's repository is https://github.com/Ragib01/django_log_tracker. Django-log-tracker has been downloaded 3,866 times to date, with the rogue version (1.0.4) downloaded 107 times on the date it was published. While the linked GitHub repository hasn't been updated since April 10, 2022, the introduction of a malicious update suggests a likely compromise of the PyPI account belonging to the developer. So most likely their could be some machines already being compromised and stealing cryptos. Below are the crypto address that have been used by criminals. 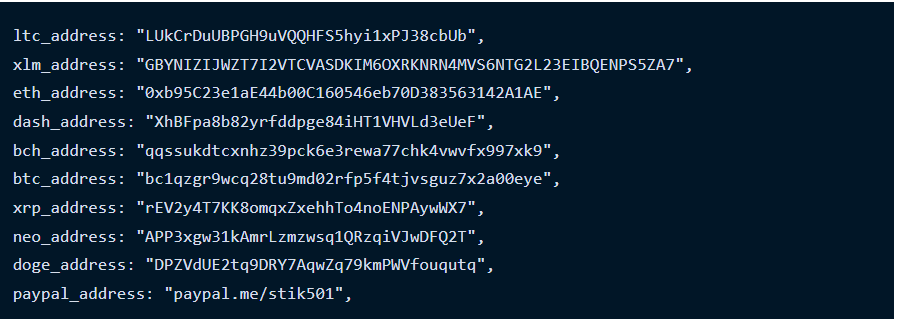 Ethereum address
has transacted 43 times on the Ethereum blockchain. It has received a total of 0.552653110090466539 ETH $1,649.89 and has sent a total of 0.52827227363384611 ETH $1,577.10. The current value of this address is 0.00 ETH $0.00. And the Bitcoin address
has transacted 49 times on the Bitcoin blockchain. It has received a total of 0.33228144 BTC $17,166.00 and has sent a total of 0.33228144 BTC $17,166.00 (❗) The current value of this address is 0.00000000 BTC $0.00. https://blog.phylum.io/dormant-pypi-package-updated-to-deploy-novasentinel-stealer/
So for Python developers out there, just be careful on what packages you used which includes: libraries, frameworks, utilities, and tools. Malwares are everywhere now and very difficult for us crypto enthusiast as we are the target by this cyber criminals. |
|
|
|
 https://www.aba.com/-/media/documents/letters-to-congress-and-regulators/jointclsec20240214.pdf https://www.aba.com/-/media/documents/letters-to-congress-and-regulators/jointclsec20240214.pdfI'm no banking expert, and so I'm asking others who have knowledge or at least understand what's the request of the American Bankers Association (“ABA”) and other groups to SEC's Chairman Gary Gensler's. It did mentioned Bitcoin Spot ETP in the official document and so I'm curious as to what changes they want? Are they asking that at least regulatory bodies be lenient for now specially for Bitcoin related in safeguarding their clients assets? |
|
|
|
It was reported that there's a trojan that harvest facial recognition data used for unauthorized access to bank accounts and crypto wallets too, and researchers dubbed it as a family of " GoldDigger". Among these discoveries, there is an exceptionally rare occurrence – a new sophisticated mobile Trojan specifically aimed at iOS users, dubbed GoldPickaxe.iOS by Group-IB. The GoldPickaxe family, which includes versions for iOS and Android, is based on the GoldDigger Android Trojan and features regular updates designed to enhance their capabilities and evade detection. GoldPickaxe.iOS, Group-IB researchers found, is capable of collecting facial recognition data, identity documents, and intercepting SMS. Its Android sibling has the same functionality but also exhibits other functionalities typical of Android Trojans. To exploit the stolen biometric data, the threat actor utilizes AI-driven face-swapping services to create deepfakes. This data combined with ID documents and the ability to intercept SMS, enables cybercriminals to gain unauthorized access to the victim’s banking account – a new technique of monetary theft, previously unseen by Group-IB researchers in other fraud schemes. https://www.group-ib.com/blog/goldfactory-ios-trojan/And it really sounds very complex and complicated and it seems the Chinese did take time to create this trojan that mostly targets APAC region specially in Vietnam as it targets targets more than 50 applications related to banking, e-wallets, and crypto-wallets. 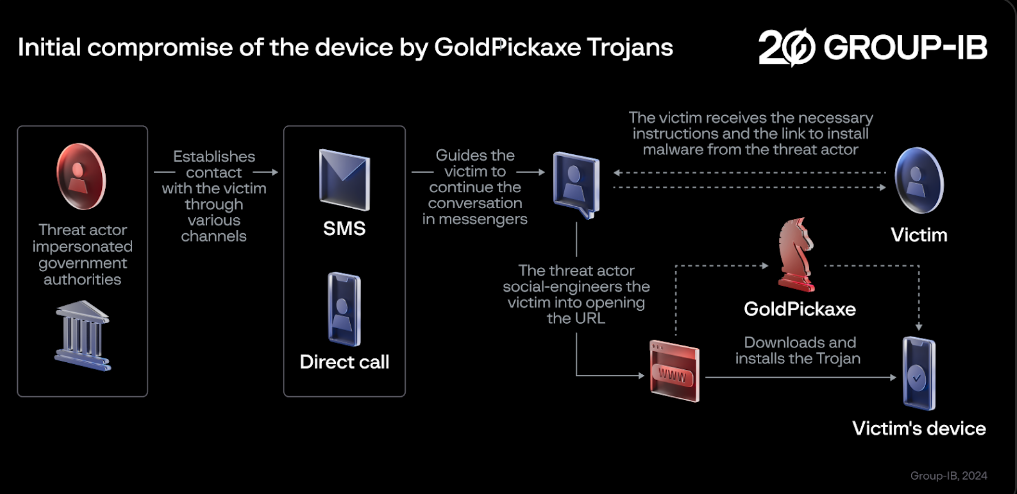 So to our friends from South East Asean region, just be careful with your banking apps and crypto wallet in your mobile or even Pc or laptop. Do everything and learn safe practice as not to infect your machines with this trojan. |
|
|
|
There is a new and sophisticated attack coming from cyber criminals. It's complicated because they are not hiding it, but instead taking advantage of legitimate online platforms, including GitHub, Vimeo, and Ars Technica, to host encoded payloads. But for now, it's not known how the criminals were able to spread it in the wild because the victims needs to physically click a link from a USB drive. And when it is launched: 1. Executes a PowerShell script "explorer.ps1" 2. it retrieves an intermediary payload, which decrypts into a URL and initiates an infection within the system by downloading 'EMPTYSPACE malware. 3. The intermediary payloads consist of text strings that, when decoded, reveal a URL for downloading the subsequent payload and facilitate communication with a C2C (Command and Control). 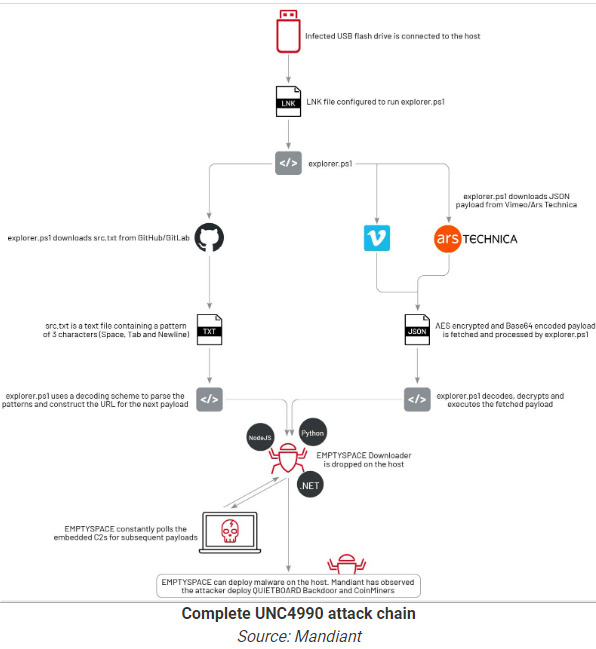 Targeted crypto wallets: Targeted crypto wallets:
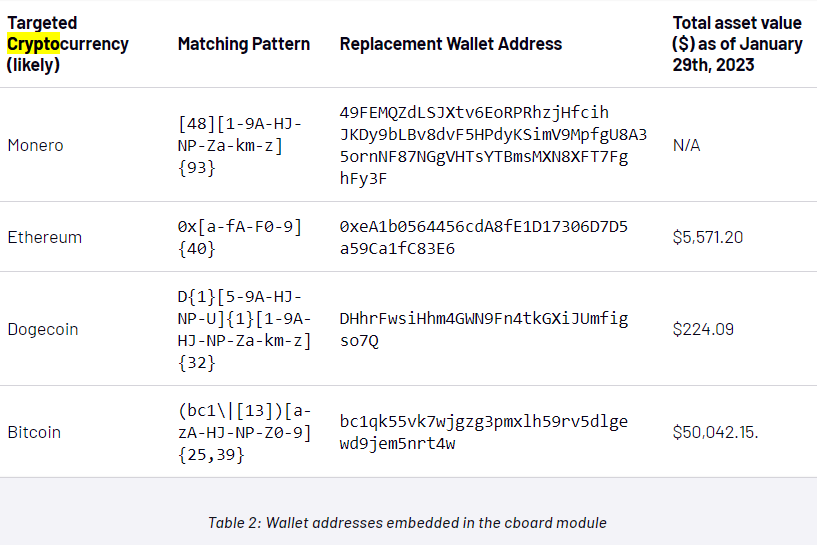 https://www.mandiant.com/resources/blog/unc4990-evolution-usb-malware https://www.mandiant.com/resources/blog/unc4990-evolution-usb-malwareSo this might be the right time now not to just be very careful on the USB drives that we are going to used or moving forward. As we have seen, criminals are getting really complex and refine with their attacks that even we can see it, we will never thought that those can be used to attack us. |
|
|
|
 https://www.justice.gov/opa/pr/three-individuals-charged-roles-189b-cryptocurrency-fraud-scheme https://www.justice.gov/opa/pr/three-individuals-charged-roles-189b-cryptocurrency-fraud-schemeNot sure if there are victims of this fraud from our community. But then again, if you look at the jail time, it's 5 years for this criminals (for each count). So it's just another slap on their risk for this criminals. I mean they could get out in the next crypto bull run or maybe much earlier and then think again of another scams that they will pull off. But we can't question the US authorities though, that's who justice is for them. This is a billion dollar scam, and not just those couple of millions. And I say that if they don't return the money, then we might not call this justice after-all. |
|
|
|
There is a group of cyber actors that targeted Mexican banking apps and crypto trading exchange and has been active in the wild right now. Not sure why Mexico and Latin-American countries, (Lat-Am), but they are financially motivated and targeting companies, gross revenues over $100M. They uses to lure their victims with the IDSE software update document: guia_de_soluciones_idse.pdf and IMSS payment system SIPARE The infection process initiates with a ZIP file, which is disseminated through either phishing or a drive-by compromise. Inside this ZIP file is an MSI installer that deploys a .NET downloader. This downloader is responsible for verifying the victim's geographical location in Mexico.  And once you extract and executed this files you will be instructed to:  1.- EXTRACT THE CONTENT OF THE INSTALARPLUGINSIPARE.ZIP FILE 2.- RUN THE FILE CALLED "INSTALARPLUGIN" 3.- WHEN YOU FINISH THE INSTALLATION YOU WILL BE ABLE TO LOG IN NORMALLY It checks ipinfo[.]io for a geolocation in Mexico, if MX is not in the response string then the downloader aborts itself.  This is just a warning to our Mexican members or those who are in Latin-American. I know that there are a lot of respected members here and maybe they can share this. https://blogs.blackberry.com/en/2024/01/mexican-banks-and-cryptocurrency-platforms-targeted-with-allakore-rat |
|
|
|
When we thought that MacOS is safe from crypto malwares, a new discovery says that this is not the case. Although the malware itself only targets newer version of the operating system, but still for us crypto enthusiast, this is very dangerous. The mode of infection is that if the user downloaded a crack or fake apple software, then you will be directed to this, a bogus Activator window that asks for the administrator password. 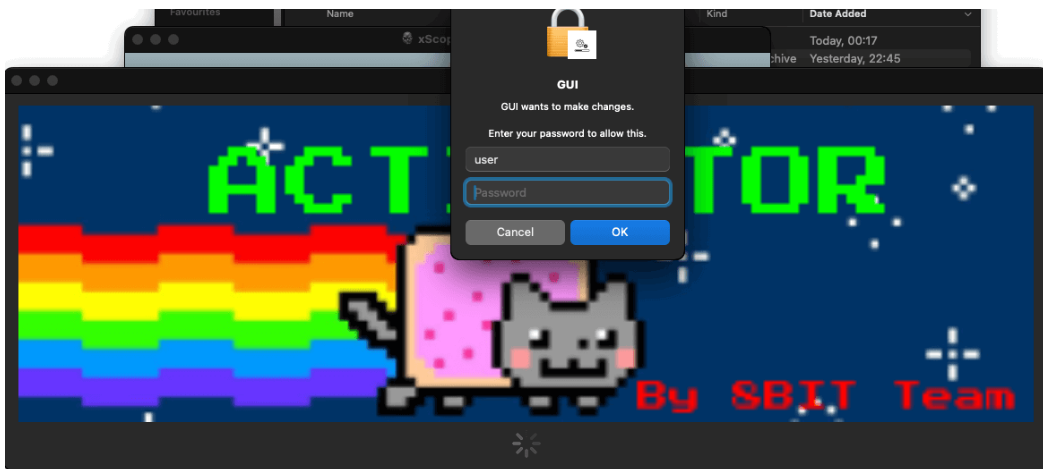 So once you give them permission, it will execute a program and then will communicate to their C2 (command and control), to downloaded a script. And this script check for the presence of Bitcoin Core and Exodus wallet (so far only this two wallets) in your machine. It will then sends everything to the criminals C2 server, including, seed, mnemonic phrase, your balance, password and once they got the data, they will obviously drain your wallet. What do we learn here?
Never ever downloaded fake or pirated software. You already have a powerful machine in your hand and you have like shell out thousands of dollars already, so why not just buy original software as not to compromise your expensive MacOS. https://securelist.com/new-macos-backdoor-crypto-stealer/111778/ |
|
|
|
A known malware, called Phemedrone Stealer is on the circulation right now and trying to take advantage and exploited CVE-2023-36025, the Windows Defender SmartScreen Bypass vulnerability. The targets are cryptocurrency wallets: - Armory
- Atomic
- Bytecoin
- Coinomi
- Jaxx
- Electrum
- Exodus
- Guarda
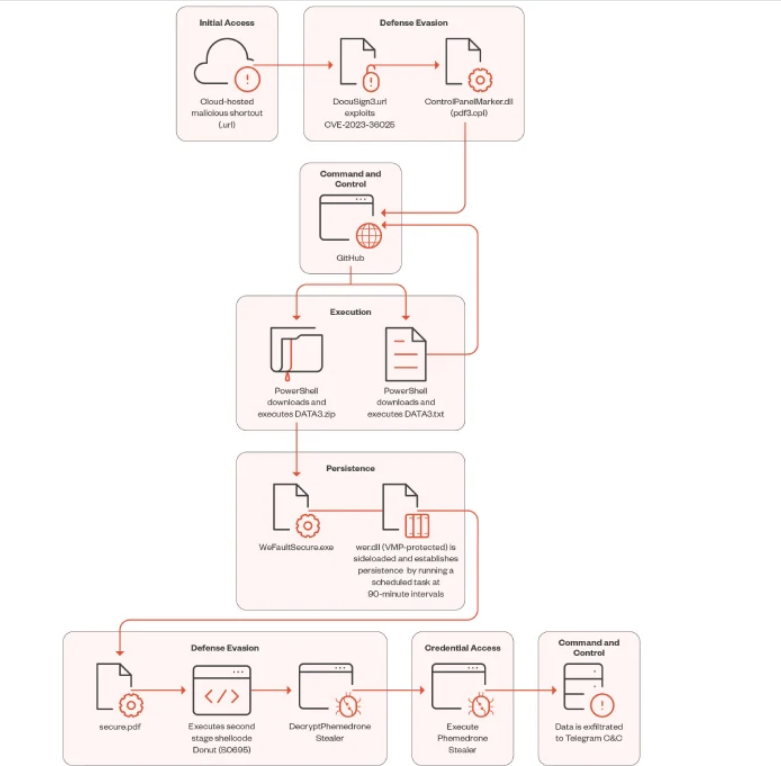 So the leverage here is that the criminals are going to hosts malicious internet shortcut files on Discord or other cloud services such as FileTransfer.io. And so once we click that shortcut files, it will connect to a controlled server by the hackers and then execute control panel item (.cpl) file. However, Microsoft Windows Defender should warn us about this shortcut url and what it will execute, but attackers also crafted a shortcut URL to evade everything. We've seen a lot of shortcut files recently, and I suggest not to click anything specially from unknown source as we might be the next victims and then this criminals draining our wallets. ( https://www.trendmicro.com/en_us/research/24/a/cve-2023-36025-exploited-for-defense-evasion-in-phemedrone-steal.html) |
|
|
|
What happened: Yearn Finance fake site Website:  Archived: https://archive.is/p6O4e Archived: https://archive.is/p6O4eWhois Record for YEaNr.finance How does this work? Domain Profile Registrant REDACTED FOR PRIVACY Registrant Org WhoisGuard, Inc. Registrant Country pa Registrar NameCheap, Inc. IANA ID: 1068 URL: https://www.namecheap.com/Whois Server: whois.namecheap.com (p) Registrar Status clientTransferProhibited Dates 18 days old Created on 2020-12-27 Expires on 2021-12-27 Updated on 2021-01-01 Name Servers DNS1.NAMECHEAPHOSTING.COM (has 1,008,481 domains) DNS2.NAMECHEAPHOSTING.COM (has 1,008,481 domains) Tech Contact REDACTED FOR PRIVACY REDACTED FOR PRIVACY, REDACTED FOR PRIVACY, REDACTED FOR PRIVACY, REDACTED FOR PRIVACY, REDACTED FOR PRIVACY (p) (f) IP Address 162.0.209.74 - 82 other sites hosted on this server So they took advantage of the mis spelling and created this malicious website. If you directly type it to your browser, and make the mistake, you will surely fall for this trap. So bookmark it and check even the spelling just to make sure.
|
|
|
|
Be careful with this so called integration wallet around, I'm seriously doubt that it is work as design as you have to enter your seed or recovery phrase. I'm trying to find out if there is such real application out there, but so far I can't find any deducing that this is a malicious site who's intention to steal our crypto. Or if there is a legit site, this is obviously a clone and fake. https://www.integrationwallet.com/  Archive: https://archive.is/bLFE7Not just bitcoin wallet, but almost all popular altcoins wallet like MEW and MetaMask. So be careful with this, if you have encounter it, kindly report it to Google or to the registrar themselves Whois Record for IntegrationWallet.com How does this work? Domain Profile Registrant Registration Private Registrant Org Domains By Proxy, LLC Registrant Country us Registrar GoDaddy.com, LLC IANA ID: 146 URL: http://www.godaddy.comWhois Server: whois.godaddy.com Registrar Status clientDeleteProhibited, clientRenewProhibited, clientTransferProhibited, clientUpdateProhibited Dates 16 days old
Created on 2020-12-25
Expires on 2021-12-25
Updated on 2020-12-25 IP Address 165.227.12.111 - 8,962 other sites hosted on this server And that IP address and its relations has a lot of flags.  https://www.virustotal.com/gui/ip-address/165.227.12.111/relations https://www.virustotal.com/gui/ip-address/165.227.12.111/relations |
|
|
|
What happened: Fake Waves Airdrop Website: https://wave-airdrop.live/
https://wave-airdrop.live/WAVES/index.html
 Registrant REDACTED FOR PRIVACY Registrant Org WhoisGuard, Inc. Registrant Country pa Registrar NameCheap, Inc. IANA ID: 1068 URL: https://www.namecheap.com/Whois Server: whois.namecheap.com (p) Registrar Status clientTransferProhibited Dates 30 days old Created on 2020-12-10 Expires on 2021-12-10 Updated on 2020-12-15 IP Address 198.54.125.171 - 873 other sites hosted on this server Unfortunately, this site has been up in the last month, so I do hope that no one has fallen for this scheme. If we can just spend less than 5 minutes of your time to report this, then for sure we will clean crypto space one at a time.
|
|
|
|
What Happened: Fake and Phishing Walletconnect.org Website: https://wallet-connect.org/  Domain Name: WALLET-CONNECT.ORG Registry Domain ID: D402200000015501490-LROR Registrar WHOIS Server: whois.namecheap.com Registrar URL: http://www.namecheap.comUpdated Date: 2020-12-19T18:40:53Z Creation Date: 2020-12-19T18:40:44Z Registry Expiry Date: 2021-12-19T18:40:44Z Registrar Registration Expiration Date: Registrar: NameCheap, Inc. Registrar IANA ID: 1068 Registrar Abuse Contact Email: Registrar Abuse Contact Phone: +1.6613102107 Reseller: Domain Status: serverTransferProhibited https://icann.org/epp#serverTransferProhibitedRegistrant Organization: WhoisGuard, Inc. Registrant State/Province: Panama Registrant Country: PA Name Server: DNS1.NAMECHEAPHOSTING.COM Name Server: DNS2.NAMECHEAPHOSTING.COM DNSSEC: unsigned URL of the ICANN Whois Inaccuracy Complaint Form https://www.icann.org/wicf/) For more information on Whois status codes, please visit https://icann.org/eppThe real website is: https://walletconnect.org/This is a warning, double check if you are connected to the real website because the domain is very similar to the original one.
|
|
|
|
|

 .
.




























