So I am looking into what would be required for a simple brain wallet passphrase generator that produced simple to remember passphrases, but ones that would not be able to be feasibly cracked within one's lifetime.
This comic was the starting point for me:
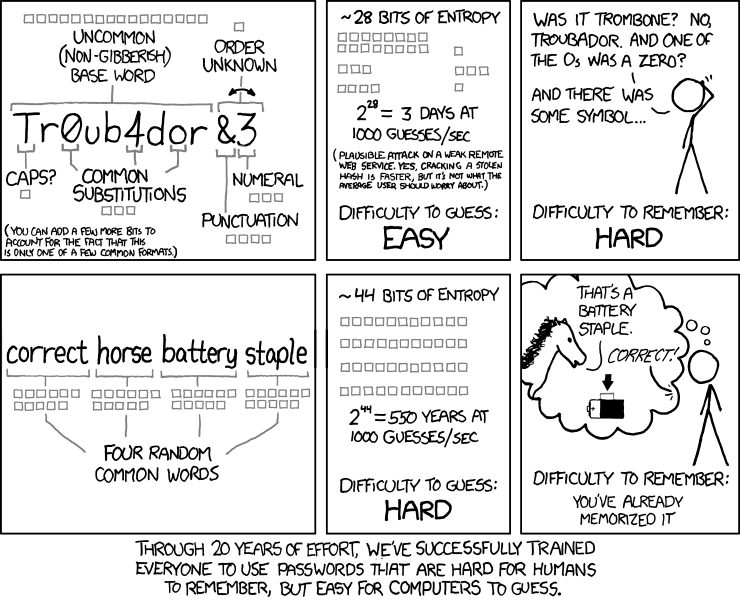
and someone created a generator here:
http://preshing.com/20110811/xkcd-password-generatorLooking at this thread:
https://bitcointalk.org/index.php?topic=68930.0it is considered that the number of possible bitcoin addresses is 2^96 or 8e28 (8x10^28).
This passphrase generator does 1949^4 = 1.4e13.
If a gigahash is 10^9 hashes per second, than 1 gigahash should be able to generate every possible hash of this in 1.4e4 seconds (or roughly 4 hours).
If I use something like this:
http://www.infochimps.com/datasets/word-list-100000-official-crossword-words-excel-readableit comes to about 3171 years for a machine producing 1 gigahash per second. (This would have 10^20 different 4 word combinations)
Assumptions made:
* Checking the blockchain for an address match takes no time (good indexing required to make this fast)
* The hashing hardware that is used to solve bitcoin blocks will generate priv/pub keypairs just as fast
(This second one I am very unsure of)
So to me it seems that using a really basic dictionary of about 2000 words does not produce the security required for this type of environment assuming a 4 word passphrase. A ~100000 word dictionary does produce the needed complexity using today's hardware.
Anyone with a better grasp of this stuff want to take a look and see if I am wildly off?



