Hello, I am an amateur developer and everything I think might be a problem I try to solve by programming. Last month a friend mentioned that ETH wallets have low security with a password. So I made a prototype of a system that makes the password difficult and it is always unique. I'll explain how it works and have the project practically done.
What is WhatPassword?It is a site or app that creates a 2Fa password to log into other sites or app.
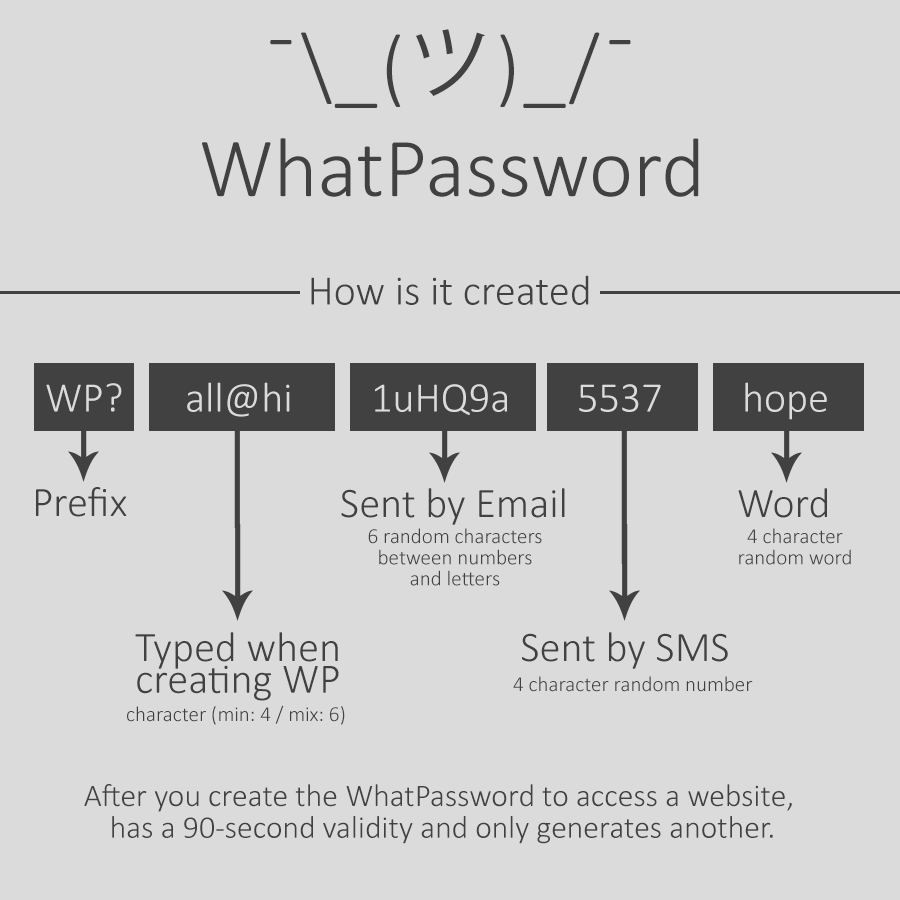
How are passwords created?The passwords are created in 5 different parts and the join makes the WhatPassword.
Part 1 - Prefix = WP?
Part 2 - Entered by the user = med2
Part 3 - Posted by E-mail = 1Los90
Part 4 - Sent by SMS = 3426
Part 5 - Word generated while creating password = love
WhatPassword = WP?med21Los903426love
Illustrative picture
OK, I know it seems too long the password and very complicated to type all this quickly. That's why each generated WP is only valid for 1 minute.
All passwords are sent or displayed to the user before going to the database and when it is saved in the database is already encrypted, this will not cause problems if the server is invaded.
I believe I can further decrease the password size and maintain the high security standard. Logic that the prefix will not be typed because it will be put on the form automatically.
Illustrative image of sending and access.
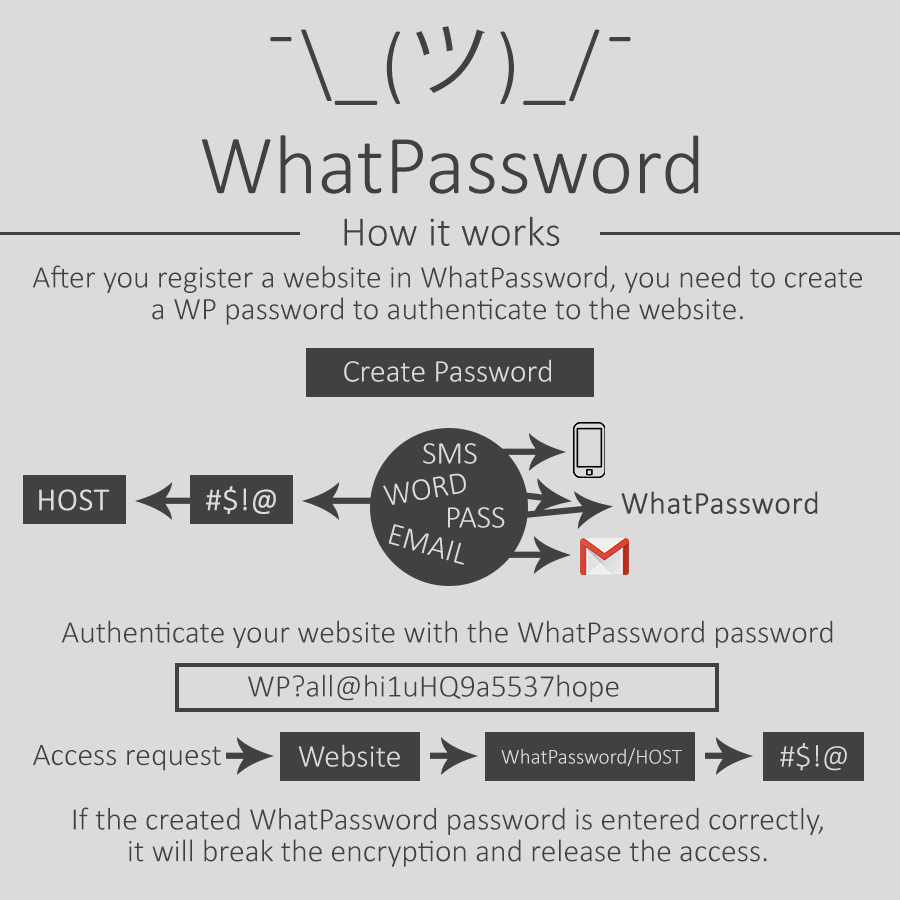
I would like to know your opinion about the prototype, of course it seems to have nothing to do with crypto-coins, but there is a lot to be. In addition you protect crypto-coin sites and you can also use the WhatPassword a paid tool. Because sending SMS has a high cost, in addition to this system I have explained is ready, I have other factors to add security that I will not divulge yet because the original idea is not completely copied.
edit
----
I remembered to mention a new idea I had about password security.
This idea may be more viable, create a token-like device that generates a password for the user, but the password is only generated if the user is going through 2 security parameters.
By holding the device in his hand, he would have to go through the biometric and facial reader at the same time to create a password.
This project is logically expensive, it would also be nice to put another heart attack on this device, if the person is assaulted and forced to create a password, this would be blocked unless it is very calm during a robbery kkk I find it difficult .
I have lots of ideas and few friends to share.



