ABCbits
Legendary

 Offline Offline
Activity: 2856
Merit: 7407
Crypto Swap Exchange

|
 |
August 08, 2022, 11:46:11 AM |
|
These two are not comparable though and BIP39 wasn't a replacement. It wasn't a replacement, but an even better proposal. Yes, you don't memorize seed phrases, but write them down. But: If you told me to choose between brain wallets and securing a wallet.dat file, which is how things worked before BIP39, I'd go with the former. Since you mention wallet.dat which usually associated with Bitcoin Core, i'd like to mention Bitcoin Core doesn't use BIP39. You still have to backup your wallet.dat or alternatively master private key from dumpwallet command/output descriptor. ... Then it doesn't make much sense to me to memorize it anymore and I could skip the whole brainwallet thing alltogether.
For most cases, i would agree. But i'd like to quote a page from Bitcoin Wiki. Brainwallets are not recommended to be used in general because of fallible human memory. But in special situations they could be very useful, for example when fleeing a country as a refugee with only the clothes on your back.
|
|
|
|
|
|
|
|
|
|
|
|
Advertised sites are not endorsed by the Bitcoin Forum. They may be unsafe, untrustworthy, or illegal in your jurisdiction.
|
|
|
d3bt3
Jr. Member

 Offline Offline
Activity: 51
Merit: 20


|
 |
August 08, 2022, 01:06:01 PM |
|
For most cases, i would agree. But i'd like to quote a page from Bitcoin Wiki. Brainwallets are not recommended to be used in general because of fallible human memory. But in special situations they could be very useful, for example when fleeing a country as a refugee with only the clothes on your back.
So for such case use https://brainwalletx.github.io/ ? |
https://altquick.com/exchange/market/BitcoinTestnet
|
|
|
itod
Legendary

 Offline Offline
Activity: 1974
Merit: 1076
^ Will code for Bitcoins

|
 |
August 08, 2022, 01:25:44 PM |
|
These two are not comparable though and BIP39 wasn't a replacement. It wasn't a replacement, but an even better proposal. Yes, you don't memorize seed phrases, but write them down. But: If you told me to choose between brain wallets and securing a wallet.dat file, which is how things worked before BIP39, I'd go with the former. Since you mention wallet.dat which usually associated with Bitcoin Core, i'd like to mention Bitcoin Core doesn't use BIP39. You still have to backup your wallet.dat or alternatively master private key from dumpwallet command/output descriptor. Backing up wallet.dat that is encrypted with decent passphrase is not a big issue, attacker first has to hack you to access your backup, and then has to attack the file's encryption passhprase. This is so complicated attack vector that all attackers rather choose to attack idiotic brainwallets. |
|
|
|
|
ABCbits
Legendary

 Offline Offline
Activity: 2856
Merit: 7407
Crypto Swap Exchange

|
For most cases, i would agree. But i'd like to quote a page from Bitcoin Wiki. Brainwallets are not recommended to be used in general because of fallible human memory. But in special situations they could be very useful, for example when fleeing a country as a refugee with only the clothes on your back.
So for such case use https://brainwalletx.github.io/ ? Tool you mentioned only use single SHA-256. Use WarpWallet[1] or rehashaddress (part of ecctools[2]) instead, which harder to brute force. [1] https://keybase.io/warp[2] https://github.com/albertobsd/ecctools#rehashaddress |
|
|
|
fxsniper
Member
 
 Offline Offline
Activity: 406
Merit: 45

|
 |
August 15, 2022, 09:47:18 AM |
|
rehashaddress it work by using privatekey to hash with sha-256 and use it again for next privatekey and loop right? |
|
|
|
|
fxsniper
Member
 
 Offline Offline
Activity: 406
Merit: 45

|
 |
August 15, 2022, 11:40:12 AM |
|
No, rehashaddress use user-chosen password/passphrase. It'll hash at least one time and perform additional rehash based on m parameter value. Here's snippet from the source code comment.
Thank you. I got it. |
|
|
|
|
PrimeNumber7
Copper Member
Legendary

 Offline Offline
Activity: 1610
Merit: 1899
Amazon Prime Member #7

|
 |
August 21, 2022, 09:48:56 PM |
|
How is someone supposed to remember the exact number of hashing rounds? I think in both the WarpWallet and your proposed ~1.2 million rounds of hashing implementations, you will need to either document the rounds of hashing, or rely on a third party to help calculate the private key, and I don't think this meets the definition of a brain wallet. With WarpWallet you can (and should!) keep your own offline copy. If you're going for a "weird" number of hashing rounds, I can think of many ways to remember the number. It could be your phone number or full date of birth. Or just something you remember. Worst-case, if you forget the exact number, you can still brute-force it yourself given that you know the pass phrase. You can keep your own copy of the software used to generate the private key, but if you are relying on a specific, non-standardized software implementation, you must have access to a copy of that software implementation to access your coin. This creates another layer of risk because now, without the software, you will not have access to your money. |
|
|
|
|
phrutis
Newbie

 Offline Offline
Activity: 8
Merit: 0

|
 |
August 21, 2022, 10:55:17 PM |
|
Here you have another toy to play with : https://github.com/phrutis/MiniKeys2This is the fastest public program to find old Serie1 minikeys (22 characters) in the world. |
|
|
|
|
almightyruler
Legendary

 Offline Offline
Activity: 2268
Merit: 1092

|
 |
September 18, 2022, 11:19:16 PM |
|
Link 404? Other repositories under that account seem to be cracking based, with executables only... so yeah, nah. |
|
|
|
|
|
n0nce
|
 |
September 18, 2022, 11:24:43 PM |
|
Link 404? Other repositories under that account seem to be cracking based, with executables only... so yeah, nah. No vouch or idea whether legit or not, but there is one result on GitHub: https://github.com/Yanmailde/Phrutis_MiniKeys2No source code either, just binaries; so proceed with extreme caution. Maybe it's possible to contact the repo's owner to clarify. |
|
|
|
ABCbits
Legendary

 Offline Offline
Activity: 2856
Merit: 7407
Crypto Swap Exchange

|
--snip--
No vouch or idea whether legit or not, but there is one result on GitHub: https://github.com/Yanmailde/Phrutis_MiniKeys2No source code either, just binaries; so proceed with extreme caution. Maybe it's possible to contact the repo's owner to clarify. After reading one of the FAQ and knowing the owner delete original repository, you could wasting your time. If I find the private key can I take all the coins for myself?
No, you will find the encrypted key.
Only the organizers can decrypt this key and pay you a 50%.
I'd recommend people to use different tool such as https://github.com/Coding-Enthusiast/FinderOuter to brute force mini private key. |
|
|
|
|
|
casinotester0001
Member
 
 Offline Offline
Activity: 194
Merit: 67
'Bitcoin signature chain' & '1 pixel inscriptions'

|
 |
September 23, 2022, 06:01:23 PM |
|
Maybe the miner inserted both transactions into the block and we never saw them in the mempool before being in the block. |
|
|
|
|
COBRAS
Member
 
 Offline Offline
Activity: 844
Merit: 20
$$P2P BTC BRUTE.JOIN NOW ! https://uclck.me/SQPJk

|
 |
September 25, 2022, 06:27:55 PM |
|
|
|
|
|
|
larry_vw_1955
|
 |
October 12, 2022, 11:18:27 PM |
|
how would someone make a mistake like that? it doesn't seem probable. |
|
|
|
|
|
n0nce
|
 |
October 13, 2022, 11:57:25 PM |
|
how would someone make a mistake like that? it doesn't seem probable. I guess it's always possible to use something like this for money laundering. I.e.: (1) Send 1BTC to address whose private key is publicly known. (2) Sweep the funds a few minutes later (depending on the amount of plausible deniability vs. risk you're willing to take). (3) Claim you mistakenly sent the funds and that they're gone, since it's an address whose private key is known. Then mix and be happy. Just an idea. |
|
|
|
PrivatePerson
Member
 
 Offline Offline
Activity: 173
Merit: 12

|
I guess it's always possible to use something like this for money laundering.
I.e.: (1) Send 1BTC to address whose private key is publicly known.
(2) See how your BTC was collected by someone else's bot. (3) Cry because you are a loser  |
|
|
|
|
LoyceV
Legendary

 Offline Offline
Activity: 3290
Merit: 16558
Thick-Skinned Gang Leader and Golden Feather 2021


|
 |
October 14, 2022, 09:28:05 AM |
|
I guess it's always possible to use something like this for money laundering.
~
(3) Claim you mistakenly sent the funds and that they're gone, since it's an address whose private key is known. That's not money laundering. It sounds more like a "boating accident". Then mix and be happy. Just an idea. Now you have money you don't officially have, and can't officially spend. Great for buying drugs, terrible for buying a car. |
|
|
|
|
n0nce
|
 |
October 14, 2022, 10:43:03 PM
Last edit: October 14, 2022, 10:57:27 PM by n0nce |
|
I guess it's always possible to use something like this for money laundering.
I.e.: (1) Send 1BTC to address whose private key is publicly known.
(2) See how your BTC was collected by someone else's bot. (3) Cry because you are a loser  I actually addressed your criticism: 'a few minutes later (depending on the amount of plausible deniability vs. risk you're willing to take)'. Never claimed that this was a risk-free method.  As we saw above, it took a whole 10 minutes for (maybe) a bot to sweep the funds. I guess it's always possible to use something like this for money laundering.
I.e.: (1) Send 1BTC to address whose private key is publicly known.
(2) Sweep the funds a few minutes later (depending on the amount of plausible deniability vs. risk you're willing to take).
(3) Claim you mistakenly sent the funds and that they're gone, since it's an address whose private key is known.
Alternatively, generate private key with relative weak (but not publicly known) string before executing your idea. After some time you could make an account on social media/forum and claim you found another weak Brainwallets which already emptied. P.S. This is informative post, i'm not taking any responsibility if you weaken your privacy or lose your money  . That's much better actually!  All hypothetical of course.  I guess it's always possible to use something like this for money laundering.
~
(3) Claim you mistakenly sent the funds and that they're gone, since it's an address whose private key is known. That's not money laundering. It sounds more like a "boating accident". Then mix and be happy. Just an idea. Now you have money you don't officially have, and can't officially spend. Great for buying drugs, terrible for buying a car. Very true. Similar to mixing and buying on decentralized exchange, I guess. Except you can keep / export Bisq trade records and mixing receipts. Would you recommend this? |
|
|
|
LoyceV
Legendary

 Offline Offline
Activity: 3290
Merit: 16558
Thick-Skinned Gang Leader and Golden Feather 2021


|
 |
October 15, 2022, 09:12:41 AM |
|
I actually addressed your criticism: 'a few minutes later (depending on the amount of plausible deniability vs. risk you're willing to take)'. Never claimed that this was a risk-free method.  As we saw above, it took a whole 10 minutes for (maybe) a bot to sweep the funds. It's rare, but I think you missed the point completely. It doesn't take 10 minutes to sweep the funds (and you shouldn't trust Blockchain.com on this). This is what Blockchair.com shows: 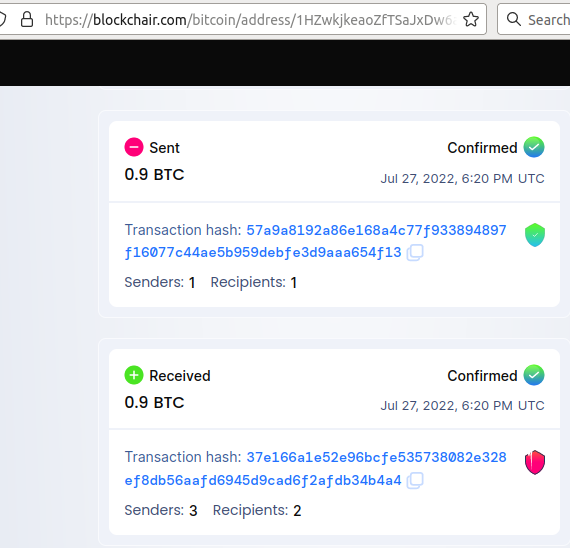 I give it half a second between the moment you broadcast the transaction, and the moment you see it disappear from the compromised address. Many bots are competing to steel those funds, and the fastest wins. You won't have minutes, you won't have seconds. Your money is instantly gone. Now you have money you don't officially have, and can't officially spend. Great for buying drugs, terrible for buying a car. Very true. Similar to mixing and buying on decentralized exchange, I guess. Except you can keep / export Bisq trade records and mixing receipts. Would you recommend this? It depends: your drug dealer won't care about receipts, your tax man will. |
|
|
|
|



