Pmalek
Legendary

 Offline Offline
Activity: 2758
Merit: 7132

|
 |
April 09, 2022, 07:44:30 AM |
|
Six to eight random words are enough for a secure passphrase according to Andreas Antonopoulos himself. If you have an English-to-English dictionary such as an Oxford or a Longman, you can just randomly open pages and put your fingers on random words that you can use to construct your passphrase. Any other book would work as well really.
|
.
.BLACKJACK ♠ FUN. | | | ███▄██████
██████████████▀
████████████
█████████████████
████████████████▄▄
░█████████████▀░▀▀
██████████████████
░██████████████
█████████████████▄
░██████████████▀
████████████
███████████████░██
██████████ | | CRYPTO CASINO &
SPORTS BETTING | | │ | | │ | ▄▄███████▄▄
▄███████████████▄
███████████████████
█████████████████████
███████████████████████
█████████████████████████
█████████████████████████
█████████████████████████
███████████████████████
█████████████████████
███████████████████
▀███████████████▀
███████████████████ | | .
|
|
|
|
|
|
|
|
Advertised sites are not endorsed by the Bitcoin Forum. They may be unsafe, untrustworthy, or illegal in your jurisdiction.
|
|
|
|
|
|
|
o_e_l_e_o
In memoriam
Legendary

 Offline Offline
Activity: 2268
Merit: 18509

|
 |
April 09, 2022, 01:03:53 PM |
|
On average, trying to brute force a wallet with 12 words (12! = 479,001,600) is a waste of time Also worth pointing out that 12 scrambled words (12! combinations) is very easy to brute force and can be done in under an hour on even modest hardware. I might point out that a passphrase is only ever going to give you incremental additional security. A properly generated, random seed is already ~impossible to brute force with current technology, and it is very unlikely future technology will ever be able to brute force a randomly generated seed. The protection offered by a passphrase has never been against brute forcing of a seed phrase from scratch - all the addresses generated by your passphrased wallet will also be generated at some derivation path by some other non-passphrased seed phrase. If an adversary is somehow able to discover your seed, it is likely they can also discover your second seed which is your passphrase. Why? I would not say this is likely by any means, and definitely not immediately, unless you have stored both seed phrase and passphrase physically next to each other. If someone accidentally stumbles on one, there is no guarantee at all that they would be able to find the other provided it is well secured somewhere else. Six to eight random words are enough for a secure passphrase according to Andreas Antonopoulos himself. If you have an English-to-English dictionary such as an Oxford or a Longman, you can just randomly open pages and put your fingers on random words that you can use to construct your passphrase. Any other book would work as well really. A better option would be to use diceware. |
|
|
|
|
PrimeNumber7
Copper Member
Legendary

 Offline Offline
Activity: 1624
Merit: 1899
Amazon Prime Member #7

|
 |
April 09, 2022, 06:08:45 PM |
|
I might point out that a passphrase is only ever going to give you incremental additional security. A properly generated, random seed is already ~impossible to brute force with current technology, and it is very unlikely future technology will ever be able to brute force a randomly generated seed. The protection offered by a passphrase has never been against brute forcing of a seed phrase from scratch - all the addresses generated by your passphrased wallet will also be generated at some derivation path by some other non-passphrased seed phrase. The collisions you are referring to have basically a zero percent chance that two seeds will be generated as you describe. The chances are less than that of generating two private keys associated with the same address because flawed RNG will not cause these types of collisions. If an adversary is somehow able to discover your seed, it is likely they can also discover your second seed which is your passphrase. Why? I would not say this is likely by any means, and definitely not immediately, unless you have stored both seed phrase and passphrase physically next to each other. If someone accidentally stumbles on one, there is no guarantee at all that they would be able to find the other provided it is well secured somewhere else. Sure, if someone "accidentally" discovers one seed, they may not discover the other, although this would certainly be a sign that you are being careless in protecting your seeds. If someone is actively looking for your seeds, if they are able to breach your countermeasures for one seed, they should be able to breach your countermeasure on the other seed. Similarly, if someone is able to cause you to use flawed RNG to generate one seed, they can do the same for the other seed, although in this case, they may not know you are using two seeds this way. |
|
|
|
|
o_e_l_e_o
In memoriam
Legendary

 Offline Offline
Activity: 2268
Merit: 18509

|
 |
April 09, 2022, 07:31:52 PM |
|
The collisions you are referring to have basically a zero percent chance that two seeds will be generated as you describe. Absolutely, but brute forcing a seed phrase from scratch also has a zero percent chance of happening. A passphrase does not change that, nor was it ever designed to. Similarly, if someone is able to cause you to use flawed RNG to generate one seed, they can do the same for the other seed, although in this case, they may not know you are using two seeds this way. That's a fair point, but I think it is a very unlikely method of attack. If someone is able to infiltrate both your home and your computer in order to plant some malware on your airgapped device to generate non-random seed phrases, then it is far more likely that they would simply steal your coins while they were there, plant a keylogger for your decryption key, $5 wrench attack you, etc. Although it does raise another point, that using the same piece of software to generate both seed phrases does leave you open to flaws in that software, which I think is a far more likely attack vector. That would probably be a good reason not to use a seed phrase as a passphrase. |
|
|
|
|
PrimeNumber7
Copper Member
Legendary

 Offline Offline
Activity: 1624
Merit: 1899
Amazon Prime Member #7

|
 |
April 10, 2022, 06:13:53 PM |
|
Similarly, if someone is able to cause you to use flawed RNG to generate one seed, they can do the same for the other seed, although in this case, they may not know you are using two seeds this way. That's a fair point, but I think it is a very unlikely method of attack. If someone is able to infiltrate both your home and your computer in order to plant some malware on your airgapped device to generate non-random seed phrases, then it is far more likely that they would simply steal your coins while they were there, plant a keylogger for your decryption key, $5 wrench attack you, etc. Although it does raise another point, that using the same piece of software to generate both seed phrases does leave you open to flaws in that software, which I think is a far more likely attack vector. That would probably be a good reason not to use a seed phrase as a passphrase. I was just using flawed RNG as an example. In bitcoin's early days, flawed RNG was implemented on android phones, which caused private keys to be generated in a small range of numbers -- too large for there to reasonably be collisions, but small enough for malicious actors to generate large numbers of private keys in the hopes of finding one with unspent coin. Android phones are not air-gapped computers, but this goes to your point about flawed software. |
|
|
|
|
|
apogio
|
Question:
a seed phrase of 12 words offers 128 bits of entropy.
Let's say that I add a passphrase of 30 numbers from 0 to 9. This is just an example.
If my calculations are correct, this will add approximately 100 bits of entropy. I did: ln(10^30)/ln(2)
Assuming that the numbers are generated from a valid entropy source:
1. Are my calculations correct?
2. What is the threshold above which the passphrase is secure? 100 bits? More?
3. Is it correct to say that my wallet is derived from 228 bits of entropy in total?
4. Is it better (in your opinion) to use characters that are easily read and written down? For example is it better to avoid 0 ,O, I, l ? Base58 does that, so I guess it's better to avoid these. However, when you write down the passphrase on paper you can use hand lettering for lowercase L etc.
|
|
|
|
o_e_l_e_o
In memoriam
Legendary

 Offline Offline
Activity: 2268
Merit: 18509

|
 |
December 02, 2023, 03:32:41 PM |
|
1. Are my calculations correct? Yes. 10 30 is 99.66 bits. 2. What is the threshold above which the passphrase is secure? 100 bits? More? Personally I would opt for 128 bits for obvious reasons, but 100 bits is probably secure enough. 3. Is it correct to say that my wallet is derived from 228 bits of entropy in total? Technically yes, but the final security of your private keys won't be any more than 128 bits. 4. Is it better (in your opinion) to use characters that are easily read and written down? For example is it better to avoid 0 ,O, I, l ? Base58 does that, so I guess it's better to avoid these. However, when you write down the passphrase on paper you can use hand lettering for lowercase L etc. If your writing is such that these characters are obviously different, then you don't need to. If you are concerned about confusing these characters, then by all means drop them from your character set. |
|
|
|
|
|
apogio
|
 |
December 02, 2023, 03:48:34 PM
Last edit: December 02, 2023, 04:03:28 PM by apogio |
|
Technically yes, but the final security of your private keys won't be any more than 128 bits.
Ok this causes me confusion. Would you please elaborate? I also had another question: Let's say I have a 2-of-2 multisig. Let's say both of the cosigners have 12 word seed phrases. Is the final security 256 bits? (128 + 128) Also if I have a wallet with 12 words seed phrase and a passphrase of 128 bits. Is the final security 256 bits? You said it's not, but I would love it if you could explain. Is the security of the 2 wallets equal? |
|
|
|
o_e_l_e_o
In memoriam
Legendary

 Offline Offline
Activity: 2268
Merit: 18509

|
Ok this causes confusion. Would you please elaborate? The maximum security provided by a 256 bit private key on the secp256k1 curve is 128 bits. This is because the most efficient way to attack a 256 bit private key is not brute force, but by solving the ECDLP, which will take on average 2 128 operations. So all bitcoin private keys, regardless of how much entropy was used to generate them, will never provide more than 128 bits of security You can see this in Standards for Efficient Cryptography. SEC 2: Recommended Elliptic Curve Domain Parameters. (Table at the bottom of page 4.) Let's say I have a 2-of-2 multisig. Let's say both of the cosigners have 12 word seed phrases. Is the final security 256 bits? (128 + 128) No. The most efficient way to attack a 2-of-2 P2WSH multi-sig would not be to attack both individual private keys, but to find any other script which has a collision with the SHA256 of your P2WSH multi-sig script. Given the script hash is the digest of a single SHA256, then again, you would expect to find a collision in 2 128 operations on average. Also if I have a wallet with 12 words seed phrase and a passphrase of 128 bits. Still 128 bits.  |
|
|
|
|
|
apogio
|
 |
December 02, 2023, 04:26:13 PM
Last edit: December 02, 2023, 04:42:17 PM by apogio |
|
The maximum security provided by a 256 bit private key on the secp256k1 curve is 128 bits. This is because the most efficient way to attack a 256 bit private key is not brute force, but by solving the ECDLP, which will take on average 2 128 operations. So all bitcoin private keys, regardless of how much entropy was used to generate them, will never provide more than 128 bits of security You can see this in Standards for Efficient Cryptography. SEC 2: Recommended Elliptic Curve Domain Parameters. (Table at the bottom of page 4.) According to this, adding the passphrase is a protection measure only if someone steals the seed phrase, so you can make sure they would never guess the passphrase. But, theoretically, an attacker that brute forces bit-by-bit could generate 128 bits that would lead to the exact same private key that the wallet of 12 words seed + 128 bits passphrase would create, correct? And if so, this also applies to the example I provided with the multisig, correct? |
|
|
|
o_e_l_e_o
In memoriam
Legendary

 Offline Offline
Activity: 2268
Merit: 18509

|
 |
December 02, 2023, 04:49:03 PM |
|
According to this, adding the passphrase is a protection measure only if someone steals the seed phrase, so you can make sure they would never guess the passphrase. Correct. But, theoretically, an attacker that brute forces bit-by-bit could generate 128 bits that would lead to the exact same private key that the wallet of 12 words seed + 128 bits passphrase would create, correct? An attacker brute forcing from scratch (not that anyone would ever do this) would either be generating 256 bit private keys or 128 bit seed phrases. But actually, every seed phrase can generate every possible address if you put in the "right" derivation path. And if so, this also applies to example I provided with the multisig, correct? Yes. There will be literally trillions and trillions of scripts out there which will give the same script hash as your multi-sig script and therefore could unlock your coins. But just like standard addresses, the search space is so astronomically large that a collision will never happen. |
|
|
|
|
|
apogio
|
 |
December 02, 2023, 04:59:47 PM |
|
...
Fascinating! Therefore, one can argue that security is only set in danger by human mistake. Even with multisig, or strong passphrase etc, the security level is technically equal. But, human error can lead to losses. So we have transitioned our focus to providing solutions that avoid human mistakes, not to solutions that add more security in terms of bits. The PK can be theoretically brute forced regardless of the wallet setup by brute forcing 128 bits |
|
|
|
o_e_l_e_o
In memoriam
Legendary

 Offline Offline
Activity: 2268
Merit: 18509

|
The PK can be theoretically brute forced regardless of the wallet setup by brute forcing 128 bits I think the point to understand is that 128 bits of security will not be brute forced. The energy required to brute force a single key with 128 bits of security would boil all the oceans on Earth 16,384 times. So until we can construct a Dyson sphere to harvest the entire energy output of the sun, 128 bits is quite safe. With that in mind, then all the additional security options we have - passphrases, multi-sigs, etc. - are not designed to increase this 128 bits of security (and indeed, as I've explained above, they can't. The final security of a bitcoin private key will never be more than 128 bits.) Rather, they are designed to protect against human error, compromised devices, viruses and malware, and so on. |
|
|
|
|
|
apogio
|
 |
December 03, 2023, 09:11:15 AM |
|
The PK can be theoretically brute forced regardless of the wallet setup by brute forcing 128 bits I think the point to understand is that 128 bits of security will not be brute forced. The energy required to brute force a single key with 128 bits of security would boil all the oceans on Earth 16,384 times. So until we can construct a Dyson sphere to harvest the entire energy output of the sun, 128 bits is quite safe. With that in mind, then all the additional security options we have - passphrases, multi-sigs, etc. - are not designed to increase this 128 bits of security (and indeed, as I've explained above, they can't. The final security of a bitcoin private key will never be more than 128 bits.) Rather, they are designed to protect against human error, compromised devices, viruses and malware, and so on. Yeap that is exactly the point I made above, isn't it? I just ask to verify that I have understood properly. |
|
|
|
o_e_l_e_o
In memoriam
Legendary

 Offline Offline
Activity: 2268
Merit: 18509

|
 |
December 03, 2023, 09:16:40 AM |
|
Yes exactly, just pointing out that brute forcing a public key is pretty much beyond the realms of "theoretically" as well, given how much energy it would require.
|
|
|
|
|
|
AprilioMP
|
 |
December 03, 2023, 01:22:35 PM |
|
The combination of several capital letters, lower case letters, several numbers and several characters with a total of 10 to 15, for me is strong enough to be used as a password and passphrase. Using this combination makes it easier for me to remember a time.
For one device and another I use different, but not more than two passphrase.
|
|
|
|
|

|
| R |
▀▀▀▀▀▀▀██████▄▄
████████████████
▀▀▀▀█████▀▀▀█████
████████▌███▐████
▄▄▄▄█████▄▄▄█████
████████████████
▄▄▄▄▄▄▄██████▀▀ | LLBIT | | | 4,000+ GAMES███████████████████
██████████▀▄▀▀▀████
████████▀▄▀██░░░███
██████▀▄███▄▀█▄▄▄██
███▀▀▀▀▀▀█▀▀▀▀▀▀███
██░░░░░░░░█░░░░░░██
██▄░░░░░░░█░░░░░▄██
███▄░░░░▄█▄▄▄▄▄████
▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀ | █████████
▀████████
░░▀██████
░░░░▀████
░░░░░░███
▄░░░░░███
▀█▄▄▄████
░░▀▀█████
▀▀▀▀▀▀▀▀▀ | █████████
░░░▀▀████
██▄▄▀░███
█░░█▄░░██
░████▀▀██
█░░█▀░░██
██▀▀▄░███
░░░▄▄████
▀▀▀▀▀▀▀▀▀ |
| | | ██░░░░░░░░░░░░░░░░░░░░░░██
▀█▄░▄▄░░░░░░░░░░░░▄▄░▄█▀
▄▄███░░░░░░░░░░░░░░███▄▄
▀░▀▄▀▄░░░░░▄▄░░░░░▄▀▄▀░▀
▄▄▄▄▄▀▀▄▄▀▀▄▄▄▄▄
█░▄▄▄██████▄▄▄░█
█░▀▀████████▀▀░█
█░█▀▄▄▄▄▄▄▄▄██░█
█░█▀████████░█
█░█░██████░█
▀▄▀▄███▀▄▀
▄▀▄▀▄▄▄▄▀▄▀▄
██▀░░░░░░░░▀██ | | | | | | | .
▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄
░▀▄░▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄░▄▀
███▀▄▀█████████████████▀▄▀
█████▀▄░▄▄▄▄▄███░▄▄▄▄▄▄▀
███████▀▄▀██████░█▄▄▄▄▄▄▄▄
█████████▀▄▄░███▄▄▄▄▄▄░▄▀
████████████░███████▀▄▀
████████████░██▀▄▄▄▄▀
████████████░▀▄▀
████████████▄▀
███████████▀ | ▄▄███████▄▄
▄████▀▀▀▀▀▀▀████▄
▄███▀▄▄███████▄▄▀███▄
▄██▀▄█▀▀▀█████▀▀▀█▄▀██▄
▄██▀▄██████▀████░███▄▀██▄
███░█████████▀██░████░███
███░████░█▄████▀░████░███
███░████░███▄████████░███
▀██▄▀███░█████▄█████▀▄██▀
▀██▄▀█▄▄▄██████▄██▀▄██▀
▀███▄▀▀███████▀▀▄███▀
▀████▄▄▄▄▄▄▄████▀
▀▀███████▀▀ | | OFFICIAL PARTNERSHIP
FAZE CLAN
SSC NAPOLI | | |
|
|
|
|
apogio
|
 |
December 03, 2023, 02:16:03 PM |
|
The combination of several capital letters, lower case letters, several numbers and several characters with a total of 10 to 15, for me is strong enough to be used as a password and passphrase. Using this combination makes it easier for me to remember a time.
For one device and another I use different, but not more than two passphrase.
Combining all the possible printable characters from the ASCII table(93 in total) wil give the following entropy (in bits): For 10 total characters: 65 bits For 15 total characters: 98 bits So I suggest you use anything larger than 15 characters to get a good entropy. Ps. I am not sure whether all these 93 characters can be used but if I recall correctly they can, I am just busy at the moment and I can't check online. If someone could confirm this please |
|
|
|
philipma1957
Legendary

 Online Online
Activity: 4116
Merit: 7850
'The right to privacy matters'


|
 |
December 03, 2023, 02:44:30 PM |
|
The combination of several capital letters, lower case letters, several numbers and several characters with a total of 10 to 15, for me is strong enough to be used as a password and passphrase. Using this combination makes it easier for me to remember a time.
For one device and another I use different, but not more than two passphrase.
Combining all the possible printable characters from the ASCII table(93 in total) wil give the following entropy (in bits): For 10 total characters: 65 bits For 15 total characters: 98 bits So I suggest you use anything larger than 15 characters to get a good entropy. Ps. I am not sure whether all these 93 characters can be used but if I recall correctly they can, I am just busy at the moment and I can't check online. If someone could confirm this please Some website restrict the none number , letter symbols. @ and * are restricted on a few websites I use. |
|
|
|
hosseinimr93
Legendary

 Offline Offline
Activity: 2394
Merit: 5235

|
 |
December 03, 2023, 02:47:26 PM |
|
Combining all the possible printable characters from the ASCII table(93 in total) wil give the following entropy (in bits):
There are 95 printable ASCII characters. !"#$%&'()*+,-./0123456789:;<=>?@ABCDEFGHIJKLMNOPQRSTUVWXYZ[\]^_`abcdefghijklmnopqrstuvwxyz{|}~(whitespace is also included) Ps. I am not sure whether all these 93 characters can be used but if I recall correctly they can, I am just busy at the moment and I can't check online. If someone could confirm this please
All 95 printable ASCII characters can be used for a passphrase. Here is a screenshot taken from electrum. 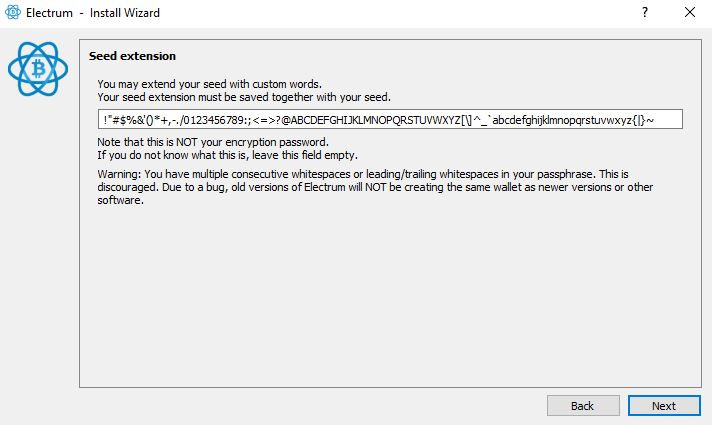 |
.
.BLACKJACK ♠ FUN. | | | ███▄██████
██████████████▀
████████████
█████████████████
████████████████▄▄
░█████████████▀░▀▀
██████████████████
░██████████████
█████████████████▄
░██████████████▀
████████████
███████████████░██
██████████ | | CRYPTO CASINO &
SPORTS BETTING | | │ | | │ | ▄▄███████▄▄
▄███████████████▄
███████████████████
█████████████████████
███████████████████████
█████████████████████████
█████████████████████████
█████████████████████████
███████████████████████
█████████████████████
███████████████████
▀███████████████▀
███████████████████ | | .
|
|
|
|
|
apogio
|
 |
December 03, 2023, 02:51:08 PM |
|
All 95 printable ASCII characters can be used for a passphrase. Here is a screenshot taken from electrum.  Brilliant! Thank you, so my numbers will change slightly (in decimal range). The bits will remain the same even with 95 instead of 93 available characters. |
|
|
|
|



