Hi everyone!
In this post I’d like to discuss a very strange situation that happened on July 12 this year with my (and it seems not only mine) bitcoin wallet.
Some input about my setupSince 2018, I've been using a Bitcoin Core wallet (full node, but slightly cut down with a log block limit of about 30 GB + headers, etc.) on my own server (Ubuntu 16.04). The wallet was used not only to store BTC, but also periodically to deposit and withdraw BTC. Interacted with the node locally on my server.
The mnemonic for the current wallet was generated in 2020 using this library:
bitcore-mnemonic +
bitcore-lib . The mnemonic was stored on the server, and also in my encrypted file with keys (strongbox), I did not decrypt it and did not use it in open form from the moment it was generated and placed in the wallet, because there was no need for it. Several backups of wallet.dat also resided on the server and never left it.
Only I exclusively had access to the server via SSL, it was done from reliable places and with all precautions, and no extraneous activity on the server was recorded before, during or after the situation.
I have used the following wallet versions in chronological order:
#ENV BITCOIN_VERSION 0.16.0
#ENV BITCOIN_VERSION 0.16.3
#ENV BITCOIN_VERSION 0.18.0
#ENV BITCOIN_VERSION 0.20.0 — was used at the time of the leak
ENV BITCOIN_VERSION 0.25.0 — the current version, which I rolled out right after
Also, I somehow used the following libraries on this server:
- bip39
- bitcoin-core
- bitcoinjs-lib
- bitcoin-ops
- pushdata-bitcoin
- varuint-bitcoin
About the situation that occurred on July 12Nothing out of the ordinary has happened to date. On the afternoon of July 12, precisely at 12:38 (UTC), without my knowledge from my wallet was carried out a transaction to withdraw 0.25211065 BTC to an unknown address —
3D2mKf28exn26v7BCVe9AXrrg4BY7qvYcvThe transaction itself is very interesting, so let's take a closer look, here is its hash:
a22b33a9a4ca0de2f56ef166298c186c5d71e56b944a255c2ecc52748f8f774bThis transaction performed a withdrawal
from 1207 (!) ADDRESSES for a total amount of 14.846758BTC (
of which 4 addresses are mine with 0.25211065 BTC of belongings), apparently to the attacker's wallet, which is indicated above.
I found out that my address had less BTC (surprisingly, after an unauthorized withdrawal 1.05328237 BTC remained in the wallet) only in the evening, and at first I thought that maybe those bitcoins were stuck somewhere on the address for change, which had not yet been pulled up by the wallet. I decided to download Bitcoin core to my work PC and import wallet.dat in there (it only left the server for the first time after I discovered my diminished balance) to check everything again. Furthermore, I also resynchronized cli-wallet on the server, but the balance did not visually change and the missing 0.25 BTC did not appear. After Bitcoin core synced on my PC, I saw a transaction with a withdrawal of 0.25 BTC dated July 12, see the screenshots below.
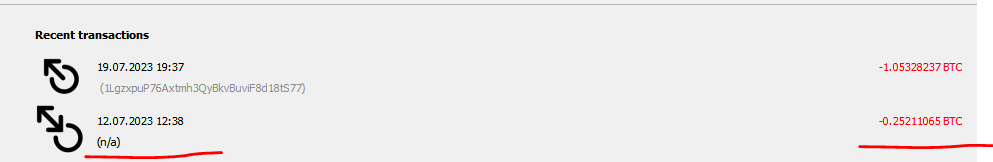
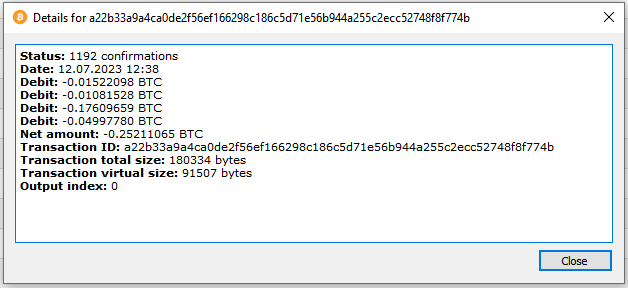
Withdrawal transaction data:
Status: 1193 confirmations
Date: 12.07.2023 12:38
Debit: -0.01522098 BTC
Debit: -0.01081528 BTC
Debit: -0.17609659 BTC
Debit: -0.04997780 BTC
Net amount: -0.25211065 BTC
Transaction ID: a22b33a9a4ca0de2f56ef166298c186c5d71e56b944a255c2ecc52748f8f774b
Transaction total size: 180334 bytes
Transaction virtual size: 91507 bytes
Output index: 0
At that moment, I finally realized that BTC wasn’t stuck anywhere, but was withdrawn (stolen) by someone to an address unknown to me, and therefore I decided to withdraw the remaining 1.05 BTC from my wallet to another safe address, assuming that my wallet could be compromised. Please note:
I withdrew 1.05 BTC to a secure address only on July 19 - a week after the event, but the BTC from the allegedly compromised wallet was waiting for me in there all this time - don't you find this strange?I personally find it very strange that the attacker withdrew only a part of bitcoins from my wallet, not all of them. Upon closer examination, I found that all bitcoins were withdrawn from bech32(segwit) addresses, which were automatically created by the wallet as addresses for receiving change after the outgoing transactions I made (addresses created on June 30, 2023, May 29, 2022, June 15, 2023, June 30, 2023, respectively). At the same time, all the addresses that I created as part of using the wallet remained untouched.In addition, the fact that this withdrawal affected
more than 1200 addresses within one transaction (!) led me to the assumption that this was some kind of a planned event, which may be the result of a vulnerability in some library, or even a bakcdoor that was used by an attacker to carry out this theft.
I would very much like to discuss this situation with the members of the forum in order to understand the details and exactly where and how my wallet was compromised (along with a large number of others), and, importantly, how to avoid this in the future. Ready to answer your questions.
I consider the version with obtaining unauthorized access to the server untenable, because there were also nodes with other crypto on the server, but fortunately they remained untouched. I also very much doubt that the mnemonics could leak from my key holder, because there were many more interesting things for a thief, but nothing like this happened anywhere else.
P.S. It may be that you or your friends own one of 1200+ addresses that have also been hacked - in this case, do not hesitate to share your version of what happened, so we can get to the truth as quickly as possible.
P.S.2 for some unknown reason, my similar post on reddit was deleted by moderators
Thanks for your attention.



