pooya87 (OP)
Legendary

 Offline Offline
Activity: 3444
Merit: 10521

|
 |
September 11, 2023, 04:43:10 PM
Last edit: September 11, 2023, 05:04:34 PM by pooya87 |
|
This looks like a Dusting Attack[1] but in a slightly different and extremely weird way! The attacker seems to be searching the chain for funded addresses like [2] then uses a "brute force tool" similar to vanity address generators to find an address that looks similar to your address like [3] but they try to be sneaky and search for an address with matching beginning and end. Examples:
1LTaZWnFTAsTqBfkSEShSXEh5VTiWUKQh8 Someone's address holding 2.56BTC
1LTKTBLDQxxf5QvgRFMzuyPMnRUULCKQh8 Attacker's address
1GZ3EfTjHVxLqnKi7yhEGCoffdATJEKeR7 2.49BTC
1GZKQVjY21SAas1tjnibAHHHNF9B8nKeR7 dust
12XqeqZRVkBDgmPLVY4ZC6Y4ruUUEug8Fx 32,321BTC
12XgkRFEdE3oSvy4tzzp8jVtsdMATwg8Fx dust
1FZy7CPFA2UqqQJYUA1cG9KvdDFbSMBJYG 15,739BTC
1FZBQjXH1RhbfpYtA3LoVrzJKqiAWSBJYG dust
Then the attacker sends two dust amounts to these similar looking addresses in the same transaction (eg. 600 sat to you, 600 sat to their own address). Feel free to share your thoughts on why would someone do something weird like this but my guess is that they hope someone would see the incoming transaction, then try to spend that output and their own coins but copy the attacker's address that looks similar instead of their own and send all their coins there so that the attacker can steal it! But there are two weird parts involved in this "operation": 1. Usually in this type of attack they rely on the user's greed to rush them into making the mistake and send their coins to the attacker. For example one somewhat similar attack I've seen was to use some shittokens on Omni layer in an address empty of bitcoin and send the key to the user who would then get greedy and funds the key with bitcoin so they can spend the token but before they can do anything the attacker steals their bitcoins. But there are no tokens involved here as far as I can tell (not even the scamjunk called Ordinals) and the amount they send the user is dust! 2. They didn't even let the dust amount remain in user's wallet. As you can see now, the transaction is already double spent and none of the addresses I shared above (the ones with high balances like 2.56) have the dust any more while the scammer's address holds slightly higher than 2x the dust limit possibly wanting to repeat the attack once again but this time the sender address and the change address and your address all 3 would look similar. The only reason why I found this is because I received one of these transactions recently and was surprised when I saw the similar addresses in the output. The attacker seems to have given up on trying to scam the big whales though as the first couple of txs in the address are sent to those. [1] https://bitcoin.stackexchange.com/questions/81508/deanonymizing-dust-attack[2] https://blockchair.com/bitcoin/address/1LTaZWnFTAsTqBfkSEShSXEh5VTiWUKQh8[3] https://blockchair.com/bitcoin/address/1LTKTBLDQxxf5QvgRFMzuyPMnRUULCKQh8[4] bc1qfyftjfs2aufq566mlwldkzgl9v6rxqqg7ta75p |
.
.BLACKJACK ♠ FUN. | | | ███▄██████
██████████████▀
████████████
█████████████████
████████████████▄▄
░█████████████▀░▀▀
██████████████████
░██████████████
█████████████████▄
░██████████████▀
████████████
███████████████░██
██████████ | | CRYPTO CASINO &
SPORTS BETTING | | │ | | │ | ▄▄███████▄▄
▄███████████████▄
███████████████████
█████████████████████
███████████████████████
█████████████████████████
█████████████████████████
█████████████████████████
███████████████████████
█████████████████████
███████████████████
▀███████████████▀
███████████████████ | | .
|
|
|
|
|
|
|
|
|
|
|
"Bitcoin: the cutting edge of begging technology." -- Giraffe.BTC
|
|
|
Advertised sites are not endorsed by the Bitcoin Forum. They may be unsafe, untrustworthy, or illegal in your jurisdiction.
|
|
|
|
|
|
Faisal2202
|
 |
September 11, 2023, 04:55:39 PM |
|
This looks like a Dusting Attack[1] but in a slightly different and extremely weird way!
.................
Feel free to share your thoughts on why would someone do something weird like this but my guess is that they hope someone would see the incoming transaction, then try to spend that output and their own coins but copy the attacker's address that looks similar instead of their own and send all their coins there so that the attacker can steal it!
This is Address poisoning attack. Not something new. I get to know about this cam few months back and according to many studies these types of attacks has been useful for hackers/scammers because it helped them to scam hell lot of money and AFAIK, I started to see topic related to this issue back in few months but the hype of this issue started from December 2022. Scam with USDT TRC20 tokenWhat are Address Poisoning Scams?And you are 100% right about it, in such scams, victim only fall prey to these attacks once he used to copy address from the last transaction made to his/her account. The best practice is to compare the full address rather then just checking the initials and final words of your address. When I get to know about this address, I always compare the whole address even if I have to make a smaller transaction too. |
|
|
|
NeuroticFish
Legendary

 Offline Offline
Activity: 3654
Merit: 6371
Looking for campaign manager? Contact icopress!

|
 |
September 11, 2023, 05:02:32 PM |
|
The best practice is to compare the full address rather then just checking the initials and final words of your address That's the best approach every time one sends money. But in this very case an even better approach is to not reuse address. Nowadays all the modern wallets are HD. It's safer to pick a completely different address from the wallet. This way the new address will probably not be similar with the attacker address and avoiding reuse is a good practice anyway. |
.
.HUGE. | | | | | | █▀▀▀▀
█
█
█
█
█
█
█
█
█
█
█
█▄▄▄▄ | ▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀
.
CASINO & SPORTSBOOK
▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ | ▀▀▀▀█
█
█
█
█
█
█
█
█
█
█
█
▄▄▄▄█ | | |
|
|
|
pooya87 (OP)
Legendary

 Offline Offline
Activity: 3444
Merit: 10521

|
 |
September 11, 2023, 05:12:27 PM |
|
This is Address poisoning attack. Not something new.
I had completely forgotten about it, I guess seeing the dust double spent threw me off. There are so many things weird with this particular attacker. This type of attack looks to have a very low success rate as it is, which means decreasing that "window of opportunity" to scam makes no sense. For example I wouldn't have seen this transaction if I had checked my wallet a couple of hours later. |
.
.BLACKJACK ♠ FUN. | | | ███▄██████
██████████████▀
████████████
█████████████████
████████████████▄▄
░█████████████▀░▀▀
██████████████████
░██████████████
█████████████████▄
░██████████████▀
████████████
███████████████░██
██████████ | | CRYPTO CASINO &
SPORTS BETTING | | │ | | │ | ▄▄███████▄▄
▄███████████████▄
███████████████████
█████████████████████
███████████████████████
█████████████████████████
█████████████████████████
█████████████████████████
███████████████████████
█████████████████████
███████████████████
▀███████████████▀
███████████████████ | | .
|
|
|
|
DVlog
Full Member
  
 Offline Offline
Activity: 476
Merit: 212
Tontogether | Save Smart & Win Big

|
 |
September 11, 2023, 06:12:26 PM |
|
This is Address poisoning attack. Not something new.
I had completely forgotten about it, I guess seeing the dust double spent threw me off. There are so many things weird with this particular attacker. This type of attack looks to have a very low success rate as it is, which means decreasing that "window of opportunity" to scam makes no sense. For example I wouldn't have seen this transaction if I had checked my wallet a couple of hours later. By design double-spend attacks have a low success rate due to their complexity to execute. As you have mentioned you might have missed that transaction completely if you haven't checked your wallet within that specific timeframe. So the attacker needs to rely on their luck as well and a dust attack can put a red flag into the owner's mind that their wallet is targeted by a scammer. So they will be more cautious every time they do something with their wallet. |
|
|
|
buwaytress
Legendary

 Offline Offline
Activity: 2800
Merit: 3443
Join the world-leading crypto sportsbook NOW!

|
 |
September 11, 2023, 06:20:27 PM |
|
Never seen this, now I know what it is called, but I figure you got the intent right. I've been guilty of double-triple-checking addresses only by checking with the first and last few characters, but it's rare for me anyway when sending to myself, to not mark the receiving address first from my own wallet.
I even make sure I choose an address in my list that I can easily recognise (usually a string of characters inside in my own language).
"Nice" to see people still haven't exhausted their creativity when it comes to trying to game Bitcoin... "not nice" that some people could very easily fall for that,
|
|
|
|
aoluain
Legendary

 Offline Offline
Activity: 2254
Merit: 1256

|
 |
September 11, 2023, 06:32:38 PM |
|
This is what the scammers are banking on, people checking starting and ending digits
to addresses. I think the majority of people verify their sending addresses like this, its convenient.
This type if attack seems complex and seems to rely as posted above on a deal of luck
but like a lot of scams they seem to work on the law of averages, somewhere and some
time someone will get tricked unfortunately
|
|
|
|
|

|
| R |
▀▀▀▀▀▀▀██████▄▄
████████████████
▀▀▀▀█████▀▀▀█████
████████▌███▐████
▄▄▄▄█████▄▄▄█████
████████████████
▄▄▄▄▄▄▄██████▀▀ | LLBIT | | | 4,000+ GAMES███████████████████
██████████▀▄▀▀▀████
████████▀▄▀██░░░███
██████▀▄███▄▀█▄▄▄██
███▀▀▀▀▀▀█▀▀▀▀▀▀███
██░░░░░░░░█░░░░░░██
██▄░░░░░░░█░░░░░▄██
███▄░░░░▄█▄▄▄▄▄████
▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀ | █████████
▀████████
░░▀██████
░░░░▀████
░░░░░░███
▄░░░░░███
▀█▄▄▄████
░░▀▀█████
▀▀▀▀▀▀▀▀▀ | █████████
░░░▀▀████
██▄▄▀░███
█░░█▄░░██
░████▀▀██
█░░█▀░░██
██▀▀▄░███
░░░▄▄████
▀▀▀▀▀▀▀▀▀ |
| | | ██░░░░░░░░░░░░░░░░░░░░░░██
▀█▄░▄▄░░░░░░░░░░░░▄▄░▄█▀
▄▄███░░░░░░░░░░░░░░███▄▄
▀░▀▄▀▄░░░░░▄▄░░░░░▄▀▄▀░▀
▄▄▄▄▄▀▀▄▄▀▀▄▄▄▄▄
█░▄▄▄██████▄▄▄░█
█░▀▀████████▀▀░█
█░█▀▄▄▄▄▄▄▄▄██░█
█░█▀████████░█
█░█░██████░█
▀▄▀▄███▀▄▀
▄▀▄▀▄▄▄▄▀▄▀▄
██▀░░░░░░░░▀██ | | | | | | | .
▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄
░▀▄░▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄░▄▀
███▀▄▀█████████████████▀▄▀
█████▀▄░▄▄▄▄▄███░▄▄▄▄▄▄▀
███████▀▄▀██████░█▄▄▄▄▄▄▄▄
█████████▀▄▄░███▄▄▄▄▄▄░▄▀
████████████░███████▀▄▀
████████████░██▀▄▄▄▄▀
████████████░▀▄▀
████████████▄▀
███████████▀ | ▄▄███████▄▄
▄████▀▀▀▀▀▀▀████▄
▄███▀▄▄███████▄▄▀███▄
▄██▀▄█▀▀▀█████▀▀▀█▄▀██▄
▄██▀▄██████▀████░███▄▀██▄
███░█████████▀██░████░███
███░████░█▄████▀░████░███
███░████░███▄████████░███
▀██▄▀███░█████▄█████▀▄██▀
▀██▄▀█▄▄▄██████▄██▀▄██▀
▀███▄▀▀███████▀▀▄███▀
▀████▄▄▄▄▄▄▄████▀
▀▀███████▀▀ | | OFFICIAL PARTNERSHIP
FAZE CLAN
SSC NAPOLI | | |
|
|
|
hugeblack
Legendary

 Offline Offline
Activity: 2506
Merit: 3625
Buy/Sell crypto at BestChange


|
 |
September 11, 2023, 07:09:52 PM |
|
I used to see such attacks on the Ethereum blockchain, where they exploit a loophole that allows sending zero transactions from your wallet, but such attacks can be solved at the level of explorer or the wallet, either by hiding dust transactions or preventing spending from them, although I suspected that these attacks would be random to this degree due to the need for extra resources in brute force.
Moving this topic to Beginners & Help would be better.
|
|
|
|
|
Z-tight
|
 |
September 11, 2023, 08:29:49 PM |
|
a dust attack can put a red flag into the owner's mind that their wallet is targeted by a scammer. So they will be more cautious every time they do something with their wallet.
Because you can't stop someone from sending you BTC's, any user with a BTC address can be attacked with a dust transaction, and it doesn't mean they are exactly targeted by scammers. Nevertheless it is easy to avoid dust attacks if you know what you are doing, addresses should never be selected from your transaction history and you should fully crosscheck all the characters in your address and not only the first and last characters. This type if attack seems complex and seems to rely as posted above on a deal of luck
Just like most scams, you have to be lucky that you get victims who don't know what they are doing. |
.
.BLACKJACK ♠ FUN. | | | ███▄██████
██████████████▀
████████████
█████████████████
████████████████▄▄
░█████████████▀░▀▀
██████████████████
░██████████████
█████████████████▄
░██████████████▀
████████████
███████████████░██
██████████ | | CRYPTO CASINO &
SPORTS BETTING | | │ | | │ | ▄▄███████▄▄
▄███████████████▄
███████████████████
█████████████████████
███████████████████████
█████████████████████████
█████████████████████████
█████████████████████████
███████████████████████
█████████████████████
███████████████████
▀███████████████▀
███████████████████ | | .
|
|
|
|
Volgastallion
Sr. Member
   
 Offline Offline
Activity: 476
Merit: 263
CONTEST ORGANIZER

|
 |
September 11, 2023, 08:48:15 PM |
|
Hi thanks you for sharing this cases and this information very valuable for us.
First of all one thing, i also do the check only with the start and the finish part of the adress, but when i heard about this kind of attack i do something to prevent my to fall into this trap.
I have my adress linked on a favorite page in the browser, for example in blockchair or whatever, also in ninjastatic , if you put an adress here in the forum can work. So i only copy paste the adress from there.
Its ok to do this simple trick to avoid this attack? Or im making a shit movement?
|
|
|
|
DVlog
Full Member
  
 Offline Offline
Activity: 476
Merit: 212
Tontogether | Save Smart & Win Big

|
 |
September 11, 2023, 08:56:48 PM |
|
a dust attack can put a red flag into the owner's mind that their wallet is targeted by a scammer. So they will be more cautious every time they do something with their wallet.
Because you can't stop someone from sending you BTC's, any user with a BTC address can be attacked with a dust transaction, and it doesn't mean they are exactly targeted by scammers. Nevertheless it is easy to avoid dust attacks if you know what you are doing, addresses should never be selected from your transaction history and you should fully crosscheck all the characters in your address and not only the first and last characters. People selected their address from the transaction history! Why Someone would do that when they could select their address from the receive button. Such careless people are the victims in most of the cases, I think. It is pretty annoying to cross-check every character, so I think name service is the most convenient way for a user. I am not sure if there is any for making transactions with bitcoin or not, but it is pretty popular in EVM-based blockchain. |
|
|
|
DaveF
Legendary

 Offline Offline
Activity: 3458
Merit: 6258
Crypto Swap Exchange


|
 |
September 11, 2023, 09:07:35 PM |
|
This is Address poisoning attack. Not something new....
But with GPUs getting more and more powerful it's starting to show up more since what would have used to be days or weeks of trying to get an address is now seconds. You can import one of many lists of addresses with balances and then get 6 or 7 characters in just about no time. I'm 100% sure there is some hack of vanitysearch out there that would do it. Heck VS might actually do it, I didn't look. -Dave |
|
|
|
|
EL MOHA
|
People selected their address from the transaction history! Why Someone would do that when they could select their address from the receive button. Such careless people are the victims in most of the cases, I think. It is pretty annoying to cross-check every character, so I think name service is the most convenient way for a user. I am not sure if there is any for making transactions with bitcoin or not, but it is pretty popular in EVM-based blockchain.
Name service is definitely a bad idea because it requires a some certain extensions or plugins to save them and generate a name to this alphanumerics. This kind of service is even more dangerous or easy to attack than randomly copying the address. Just like the copy and paste address is prone to keyboard malware’s this also is too. It is more dangerous again because you definitely need to expose your address to the internet, an attacker can also temper with such sites and change the address without you knowing through malware. |
|
|
|
|
albert0bsd
|
 |
September 11, 2023, 10:12:15 PM |
|
Thank you for sharing your post, as this kind of awareness is vital for ensuring the security of our satoshis. Yes they expect that some less experienced users fall for it. Some recomendations for new users will be: -Never be too quick to spend funds you've received, especially if it's a small and strange transaction. -Always make sure the FULL destination address matches where you want your money to go. -Using a good wallet that lets you block incoming dust transactions is a smart move. -You've gotta be careful, and don't rush into sending money without double-checking everything. It's kind of frustrating that those scammers always try always shady tactics, but by sharing info and educating others i think that we are doing it good  Regads! |
|
|
|
|
Text
|
 |
September 11, 2023, 10:18:38 PM |
|
This scenario is indeed unusual and suspicious, possibly indicating an attempted scam or a variant of a 'dusting attack' with a unique approach. The attacker's precise motive is misdirection: they aim to confuse users into sending their funds to the wrong address by generating addresses that closely resemble the legitimate ones. The attacker will succeed if the user accidentally copies the attacker's address instead of their own during a transaction.
This is new information to me, and I'm thankful I came across this thread to learn about it. Now that I'm aware of this type of trick, I'll be more cautious and double-check addresses to ensure they are identical when conducting Bitcoin transactions.
|
| | | | | | | ███▄▀██▄▄
░░▄████▄▀████ ▄▄▄
░░████▄▄▄▄░░█▀▀
███ ██████▄▄▀█▌
░▄░░███▀████
░▐█░░███░██▄▄
░░▄▀░████▄▄▄▀█
░█░▄███▀████ ▐█
▀▄▄███▀▄██▄
░░▄██▌░░██▀
░▐█▀████ ▀██
░░█▌██████ ▀▀██▄
░░▀███ | | ▄▄██▀▄███
▄▄▄████▀▄████▄░░
▀▀█░░▄▄▄▄████░░
▐█▀▄▄█████████
████▀███░░▄░
▄▄██░███░░█▌░
█▀▄▄▄████░▀▄░░
█▌████▀███▄░█░
▄██▄▀███▄▄▀
▀██░░▐██▄░░
██▀████▀█▌░
▄██▀▀██████▐█░░
███▀░░ | | | | |
|
|
|
|
Z-tight
|
I have my adress linked on a favorite page in the browser, for example in blockchair or whatever, also in ninjastatic , if you put an adress here in the forum can work. So i only copy paste the adress from there.
These are not recommended places to copy your wallets address if you want to avoid this kind of attack. Copy your wallet address only from your wallets addresses tab, or you select or generate new addresses from your wallets receive tab so you wouldn't reuse addresses, which is both bad for privacy and vulnerable to this attack. -Never be too quick to spend funds you've received, especially if it's a small and strange transaction.
You can spend dust tx's and it is not risky to do so if you know what you are doing, sometimes dust attack is an attack on your privacy and a way an attacker can link your utxo's if you spend the dust utxo with the others in your wallet, using coin control is one way of spending dust tx's without losing your privacy. -Using a good wallet that lets you block incoming dust transactions is a smart move.
You cannot block incoming tx's into your wallet, in other words you can't stop someone from sending you BTC's. |
.
.BLACKJACK ♠ FUN. | | | ███▄██████
██████████████▀
████████████
█████████████████
████████████████▄▄
░█████████████▀░▀▀
██████████████████
░██████████████
█████████████████▄
░██████████████▀
████████████
███████████████░██
██████████ | | CRYPTO CASINO &
SPORTS BETTING | | │ | | │ | ▄▄███████▄▄
▄███████████████▄
███████████████████
█████████████████████
███████████████████████
█████████████████████████
█████████████████████████
█████████████████████████
███████████████████████
█████████████████████
███████████████████
▀███████████████▀
███████████████████ | | .
|
|
|
|
_BlackStar
Legendary

 Offline Offline
Activity: 1064
Merit: 1228

|
 |
September 11, 2023, 10:39:51 PM |
|
I'm not sure how many users are fooled by these strange attacks - but I think it's true that the success rate of these attacks is very low. In fact I'm sure some of the destination addresses are addresses that were never actually used and those dust transactions were the only transactions available in history. For example, for this address: https://blockchair.com/bitcoin/address/1GZKQVjY21SAas1tjnibAHHHNF9B8nKeR71GZ3EfTjHVxLqnKi7yhEGCoffdATJEKeR7 2.49BTC
1GZKQVjY21SAas1tjnibAHHHNF9B8nKeR7 dust 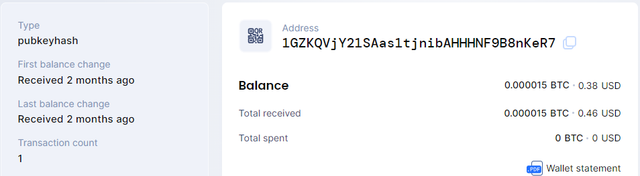 |
|
|
|
|
albert0bsd
|
 |
September 11, 2023, 10:40:31 PM |
|
You cannot block incoming tx's into your wallet, in other words you can't stop someone from sending you BTC's.
Yes you are right we can't block those input TX. What i mean it was hidden it or at least to have a way block the UTXO preventing to be spend it to another of our own address. 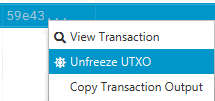 And yes just like you said we can spend it with out problem to another address as payment to someone else, we can said, thanks for pay our fees  |
|
|
|
|
nelson4lov
|
 |
September 11, 2023, 10:48:53 PM |
|
People selected their address from the transaction history! Why Someone would do that when they could select their address from the receive button. Such careless people are the victims in most of the cases, I think. It is pretty annoying to cross-check every character, so I think name service is the most convenient way for a user. I am not sure if there is any for making transactions with bitcoin or not, but it is pretty popular in EVM-based blockchain.
Name services are cool but they're not well integrated to platforms that support EVM-based services and I haven't heard about any for Bitcoin. I'm not surprised that some users still fall victim to these kind of attacks and there's the clipboard hack as well that allows a user copy their address but when it's time to paste, it pastes a similar address like the ones posted in OP that has almost or the same first and last few characters.
Only way is for users to take full responsibility and be super careful whenever they want to spend BTC. |
|
|
|
sheenshane
Legendary

 Offline Offline
Activity: 2394
Merit: 1215
Cashback 15%


|
 |
September 11, 2023, 10:57:20 PM |
|
I'm confused about where they get those thousands of addresses for dust attacks.
Technically, I don't know how this works further with them but I think this wasting of time since we know most people will always double-check transactions before sending or transferring to another address.
I remember last year one of my Bitcoin addresses was part of a dust attack but I successfully withdrew it and nothing happened.
By the way OP, thanks for sharing this.
|
.
.HUGE. | | | | | | █▀▀▀▀
█
█
█
█
█
█
█
█
█
█
█
█▄▄▄▄ | ▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀
.
CASINO & SPORTSBOOK
▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ | ▀▀▀▀█
█
█
█
█
█
█
█
█
█
█
█
▄▄▄▄█ | | |
|
|
|
|



