|
AYOBA (OP)
|
 |
September 26, 2023, 03:31:49 PM |
|
Hello, senior members of the forum. I have a question about a public key hash I discovered while doing research. I said I'd leave it here.
What is the significance of this public key hash?
According to my intuition, there may be a distinction between a public key and a public key hash.
I'd be delighted if the forum members could justify my deference.
Thank you so much; all of your responses will be greatly appreciated.
|
|
|
|
|
|
Advertised sites are not endorsed by the Bitcoin Forum. They may be unsafe, untrustworthy, or illegal in your jurisdiction.
|
|
|
|
|
|
Bitcoin Smith
|
 |
September 26, 2023, 03:38:22 PM |
|
there may be a distinction between a public key and a public key hash.
Public key hash is nothing but the shorter version of public key. In cryptocurrency we can call public key hash as crypto address which we usually send funds to whereas public key is a cryptographic key that is used for encrypting data and only the private key associated with that public key can be used to decrypt it. |
.
HUGE | | | | | | █▀▀▀▀
█
█
█
█
█
█
█
█
█
█
█
█▄▄▄▄ | ▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀
.
CASINO & SPORTSBOOK
▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ | ▀▀▀▀█
█
█
█
█
█
█
█
█
█
█
█
▄▄▄▄█ | | |
|
|
|
BitMaxz
Legendary

 Online Online
Activity: 3234
Merit: 2943
Block halving is coming.


|
 |
September 26, 2023, 04:05:57 PM |
|
The public key hash is our the wallet address. Bitcoin address is a hashed version of our public key derived from private key. There are different types of them one of them is P2PKH and P2SH read more here Bitcoin address types compared: P2PKH, P2SH, P2WPKH, and moreIf you want a better explanation about this I suggest read this " Public Key Hash Explained". |
|
|
|
|
Faisal2202
|
 |
September 26, 2023, 04:14:46 PM |
|
I would like to add my version, which is that the public key is used to encrypt data, and the other party will use the private key to decrypt the encrypted data. Public key hashes are the encrypted form of the public key, which is smaller in size and is the compact one.
This means that to secure the private keys, we use public keys, and to secure the public keys, we use public key hashes.
Let's say you have a public key:
044f40875d8b57f9d80e12b54677893997c7573bf176711680356e0336a8c7b29fa26599a933e92 c3f8399587f38818991759b7a2778c74c86a17f25b8e9a272b
Public key hash: 18d2e54761a9465a1943399808d63097c591451c
Encryption method of creating a hash key is different and it should be, and the key must be kept save otherwise your public key will be exposed.
|
|
|
|
|
albert0bsd
|
 |
September 26, 2023, 04:46:12 PM
Last edit: September 26, 2023, 06:11:33 PM by albert0bsd |
|
Always the same questions... Please read the next link: Chapter 4. Keys, Addresses, WalletsAlso you can found the full book on github and the pdf in some other pages. |
|
|
|
|
satscraper
|
 |
September 26, 2023, 06:10:47 PM
Last edit: September 26, 2023, 07:44:19 PM by satscraper |
|
The public key hash is our the wallet address. Bitcoin address is a hashed version of our public key derived from private key.
.
Not exactly. To create, for instance, the legacy address, we add to public key hash ( [Ripemd160[sha256(pubkey)]] the network type as a prefix (0x00 - if mainnet) and concatenate the checksum (which is equal to first four bytes of [sha256[sha256([Ripemd160[sha256(pubkey)]]) with the resulting string that should undergo a BASE58 conversion to get the target address. Thus, public key hash is used to create address but they are not exactly the same. The procedure in which it involves depends on type of address.
According to my intuition, there may be a distinction between a public key and a public key hash.
Public key hash, this concept is usually implies the digest of the blending hash function Ripemd160[sha256(pubkey) that takes pubkey as a message. |
.
.HUGE. | | | | | | █▀▀▀▀
█
█
█
█
█
█
█
█
█
█
█
█▄▄▄▄ | ▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀
.
CASINO & SPORTSBOOK
▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ | ▀▀▀▀█
█
█
█
█
█
█
█
█
█
█
█
▄▄▄▄█ | | |
|
|
|
o_e_l_e_o
In memoriam
Legendary

 Offline Offline
Activity: 2268
Merit: 18507

|
 |
September 26, 2023, 07:45:14 PM |
|
Public key hash is nothing but the shorter version of public key. No, it isn't. It is a hashed version of the public key. Coins sent to a public key and coins sent to a public key hash have completely different unlocking scripts. There are different types of them one of them is P2PKH and P2SH P2SH (pay to script hash) addresses are hashes of a script, not necessarily hashes of a public key. Public key hashes are the encrypted form of the public key, which is smaller in size and is the compact one. Hashing is not the same as encryption. Pubkey hashes are not encrypted public keys. Let's say you have a public key:
044f40875d8b57f9d80e12b54677893997c7573bf176711680356e0336a8c7b29fa26599a933e92 c3f8399587f38818991759b7a2778c74c86a17f25b8e9a272b This is not a valid public key. |
|
|
|
|
HeRetiK
Legendary

 Offline Offline
Activity: 2912
Merit: 2084
Cashback 15%

|
 |
September 26, 2023, 08:05:24 PM |
|
Private keys sign transactions. Public keys verify transactions. Hashing a public key allows for keeping the public key secret until an outgoing transaction is made, which provides an additional layer of security, especially keeping the future possibility of quantum computing attacks in mind.
|
.
.HUGE. | | | | | | █▀▀▀▀
█
█
█
█
█
█
█
█
█
█
█
█▄▄▄▄ | ▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀
.
CASINO & SPORTSBOOK
▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ | ▀▀▀▀█
█
█
█
█
█
█
█
█
█
█
█
▄▄▄▄█ | | |
|
|
|
pooya87
Legendary

 Offline Offline
Activity: 3430
Merit: 10505

|
 |
September 27, 2023, 04:33:04 AM |
|
I would like to add my version, which is that the public key is used to encrypt data, and the other party will use the private key to decrypt the encrypted data. Public key hashes are the encrypted form of the public key, which is smaller in size and is the compact one.
I feel like you are confusing 3 different algorithms with each other. 1. EncryptionThis is a reversible operation where you create a "ciphertext" from a message using a password. The one with the password and the ciphertext can decrypt it to get the message. Combining encryption with public key cryptography will give us the hybrid systems such as ECIES where you can encrypt a message using the other party's public key so that they can decrypt it using their private key. 2. HashingThis is an irreversible operation where you compute a fixed size digest from an arbitrary size message. In bitcoin (addresses) we use hash functions to shorten the public key (or the arbitrary size script in pay to script addresses) and consequently the size of the address that needs to be copied. It's purpose is not to "hide" the public key since there is no security risk in revealing your public key in an asymmetric cryptography. If there were, the algorithm would have been obsolete. 3. Digital Signature AlgorithmTo put simply in the asymmetric cryptography algorithms you use a DSA to prove you own the private key to the revealed public key. For example in Bitcoin you sign a transaction with your private key (using ECDSA or ECSDSA) to satisfy the conditions in the smart contracts containing any of the OP_CHECK(MULTI)SIG(VERIFY) operations, so that you can spend the coins you have. |
.
.BLACKJACK ♠ FUN. | | | ███▄██████
██████████████▀
████████████
█████████████████
████████████████▄▄
░█████████████▀░▀▀
██████████████████
░██████████████
█████████████████▄
░██████████████▀
████████████
███████████████░██
██████████ | | CRYPTO CASINO &
SPORTS BETTING | | │ | | │ | ▄▄███████▄▄
▄███████████████▄
███████████████████
█████████████████████
███████████████████████
█████████████████████████
█████████████████████████
█████████████████████████
███████████████████████
█████████████████████
███████████████████
▀███████████████▀
███████████████████ | | .
|
|
|
|
|
WatChe
|
 |
September 27, 2023, 06:01:10 AM |
|
Private keys sign transactions. Public keys verify transactions. Hashing a public key allows for keeping the public key secret until an outgoing transaction is made, which provides an additional layer of security, especially keeping the future possibility of quantum computing attacks in mind.
Finally got someone who is taking Quantum computing serious, mostly people are not taking it serious for now. It may take 10 to 20 years (may be more or less no one is certain) for quantum computers to arrive but its good that we start preparing for it. There wont be any digital sector which wont be affected by the quantum computing. |
|
|
|
o_e_l_e_o
In memoriam
Legendary

 Offline Offline
Activity: 2268
Merit: 18507

|
It may take 10 to 20 years (may be more or less no one is certain) for quantum computers to arrive but its good that we start preparing for it. Using pubkey hashes provides little realistic security when it comes to quantum computers. Public keys are meant to be public. That's the whole point. No wallet, software, or service treats and handles public keys securely as it does with private keys. There are dozens of reasons your public keys will already be exposed, from transactions, signing messages, light wallets syncing with third parties, address reuse, multi-sig, taproot, use in BIP32, use in descriptors, and so on. And even if you personally keep your public keys completely secure on an airgapped machine and only use addresses in a watch only wallet, probably the majority of bitcoin out there is in addresses with public keys which have been revealed one way or another. Quantum resistance will come from forking to a quantum resistant algorithm and depreciating ECDLP altogether, not from using public key hashes. |
|
|
|
|
|
Bitcoin Smith
|
 |
September 27, 2023, 08:29:14 AM |
|
Public key hash is nothing but the shorter version of public key. No, it isn't. It is a hashed version of the public key. Coins sent to a public key and coins sent to a public key hash have completely different unlocking scripts. Thanks, I didn't know that but since I am not technically strong yet this is one more information I can learn today. |
.
HUGE | | | | | | █▀▀▀▀
█
█
█
█
█
█
█
█
█
█
█
█▄▄▄▄ | ▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀
.
CASINO & SPORTSBOOK
▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ | ▀▀▀▀█
█
█
█
█
█
█
█
█
█
█
█
▄▄▄▄█ | | |
|
|
|
o_e_l_e_o
In memoriam
Legendary

 Offline Offline
Activity: 2268
Merit: 18507

|
 |
September 27, 2023, 08:51:08 AM |
|
Thanks, I didn't know that but since I am not technically strong yet this is one more information I can learn today. No problem. Here is an example of transaction I just pulled from a recent block spending coins from a standard P2PKH (pay to pubkey hash) output - https://mempool.space/tx/ec8d6d318f0a73423782074cc1e73f8675af47b4f7fe574745c6cb1d2f95480d. If you click on "Details" and then look at the "Previous output script", you'll see the following: OP_DUP
OP_HASH160
OP_PUSHBYTES_20 0da3181e2da814fb4bf16ecd061c263847cbc5fb
OP_EQUALVERIFY
OP_CHECKSIG To spend such coins, your wallet will provide a signature for this address followed by the original unhashed public key. This set of instructions will first duplicate the public key (OP_DUP), then pass it through two hash functions (OP_HASH160). It will then verify that this hash value is equal to the hash value given above (OP_EQUALVERIFY). If it is, then it will check the signature you provided against the unhashed public key (OP_CHECKSIG). If the signature is valid, then the transaction can be broadcast and mined. Here is an example of transaction spending coins from a P2PK (pay to pubkey) output - https://mempool.space/tx/f4184fc596403b9d638783cf57adfe4c75c605f6356fbc91338530e9831e9e16. (This is actually the first bitcoin transaction from Satoshi to Hal Finney.) Again, if you click on "Details", you'll see the following: OP_PUSHBYTES_65 0411db93e1dcdb8a016b49840f8c53bc1eb68a382e97b1482ecad7b148a6909a5cb2e0eaddfb84ccf9744464f82e160bfa9b8b64f9d4c03f999b8643f656b412a3
OP_CHECKSIG To spend such coins, all you need to provide is a signature. The string in the locking script above is the public key, and so you do not need to provide the public key as you did with a P2PKH output. Just provide a signature and OP_CHECKSIG will check your signature against the public key which is already there. P2PK outputs are very rarely used these days, but there remains several million bitcoin on dormant on such outputs from the early days of bitcoin. But yes, public keys and public key hashes are different things which need to be unlocked with different scripts. |
|
|
|
|
HeRetiK
Legendary

 Offline Offline
Activity: 2912
Merit: 2084
Cashback 15%

|
 |
September 27, 2023, 11:33:21 AM |
|
It may take 10 to 20 years (may be more or less no one is certain) for quantum computers to arrive but its good that we start preparing for it. Using pubkey hashes provides little realistic security when it comes to quantum computers. Public keys are meant to be public. That's the whole point. No wallet, software, or service treats and handles public keys securely as it does with private keys. There are dozens of reasons your public keys will already be exposed, from transactions, signing messages, light wallets syncing with third parties, address reuse, multi-sig, taproot, use in BIP32, use in descriptors, and so on. And even if you personally keep your public keys completely secure on an airgapped machine and only use addresses in a watch only wallet, probably the majority of bitcoin out there is in addresses with public keys which have been revealed one way or another. Quantum resistance will come from forking to a quantum resistant algorithm and depreciating ECDLP altogether, not from using public key hashes. Yes and no. Yes, pubkey hashes are no long term solution, but they can still serve as stopgap as long as you avoid reusing addresses. That is to say, there will probably be a couple of years between the first quantum computer deriving a private key and the first quantum computer being fast enough to do the same while a transaction is still in transit. |
.
.HUGE. | | | | | | █▀▀▀▀
█
█
█
█
█
█
█
█
█
█
█
█▄▄▄▄ | ▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀
.
CASINO & SPORTSBOOK
▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ | ▀▀▀▀█
█
█
█
█
█
█
█
█
█
█
█
▄▄▄▄█ | | |
|
|
|
o_e_l_e_o
In memoriam
Legendary

 Offline Offline
Activity: 2268
Merit: 18507

|
 |
September 27, 2023, 12:25:06 PM |
|
That is to say, there will probably be a couple of years between the first quantum computer deriving a private key and the first quantum computer being fast enough to do the same while a transaction is still in transit. But still, public key hashes provide no real benefit. You are first assuming that a quantum computer capable of solving the ECDLP suddenly appears out of nowhere and we have no time to react. This is highly unlikely to happen, given we are all aware of quantum developments and discussions regarding quantum proof algorithms are already ongoing. What is far more likely is that we will transition to a quantum proof algorithm long before the first private key is attacked. And if a computer which can break ECDLP does pop up out of nowhere, then as I've explained above the majority of coins are in addresses with revealed public keys. Having your bitcoin secured behind a hash is little consolation if the network collapses because 10 million bitcoin have been stolen. If pubkey hashes actually provided any meaningful security, then we wouldn't be moving away from them with taproot addresses, which reveal the public key just from the address. |
|
|
|
|
|
apogio
|
 |
September 27, 2023, 12:54:28 PM |
|
I am following your conversation and without wanting to add something to what other users already said, I thought the following image could be helpful. 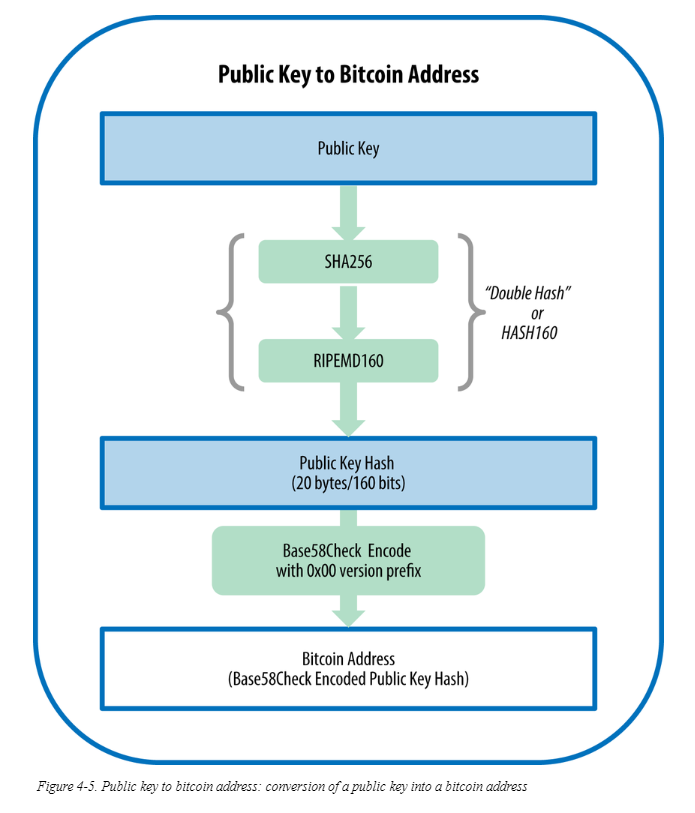 |
|
|
|
BlackHatCoiner
Legendary

 Offline Offline
Activity: 1498
Merit: 7294
Farewell, Leo

|
What is the significance of this public key hash? Seems like nobody answered that. The significance of the public key hash is that it shortens the scriptPubKey, which in consequence shortens the transaction size. Compressed public keys are 33 bytes, whereas a RIPEMD-160 hash is 20.
Public key hashes provide no security whatsoever. Even if the attacker cannot work out the private key while the transaction is unconfirmed, the entire system is just so reliant on public keys that it'd be complete ignorance to even call it security. Signed messages, Taproot, lightning, billions of dollars worth of bitcoin with known public keys, SPV servers with master public keys stored etc. |
.
.HUGE. | | | | | | █▀▀▀▀
█
█
█
█
█
█
█
█
█
█
█
█▄▄▄▄ | ▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀
.
CASINO & SPORTSBOOK
▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ | ▀▀▀▀█
█
█
█
█
█
█
█
█
█
█
█
▄▄▄▄█ | | |
|
|
|
o_e_l_e_o
In memoriam
Legendary

 Offline Offline
Activity: 2268
Merit: 18507

|
Compressed public keys are 33 bytes, whereas a RIPEMD-160 hash is 20. Interestingly, pubkeyhash came before compressed public keys. While addresses and public key hashes are mentioned in Satoshi's initial v0.1 announcement email, it seems that Satoshi simply didn't know that public keys could be compressed in the way that we do now. The size difference between an uncompressed public key and an address is obviously much greater than the size difference between a compressed public key and an address. An uncompressed public key is 130 characters. If you want to encode that with Base58Check, then your resulting string is 95 characters. A compressed public key is 66 characters. If you encode that with Base58Check, then your resulting string is 51 characters. A standard legacy address is 33/34 characters. A reduction in size from 95 to 34 (61 characters) is much more meaningful than a reduction from 51 to 34 (17 characters). Would we even have P2PKH addresses at all had Satoshi known about compressed public keys? |
|
|
|
|
pooya87
Legendary

 Offline Offline
Activity: 3430
Merit: 10505

|
 |
September 28, 2023, 03:51:34 AM Merited by garlonicon (1) |
|
Seems like nobody answered that. The significance of the public key hash is that it shortens the scriptPubKey, which in consequence shortens the transaction size. Compressed public keys are 33 bytes, whereas a RIPEMD-160 hash is 20.
When you want to talk about size of transactions it is better to consider both transactions, the one creating the output and the one spending it. In this case the sum total size of the two transactions is larger when using the scripts that contain the pubkey hash instead of the public key itself (ie. P2PKH vs P2PK for example) because there is an additional hash size (20 bytes) and additional OP codes (each one byte) in the scripts. |
.
.BLACKJACK ♠ FUN. | | | ███▄██████
██████████████▀
████████████
█████████████████
████████████████▄▄
░█████████████▀░▀▀
██████████████████
░██████████████
█████████████████▄
░██████████████▀
████████████
███████████████░██
██████████ | | CRYPTO CASINO &
SPORTS BETTING | | │ | | │ | ▄▄███████▄▄
▄███████████████▄
███████████████████
█████████████████████
███████████████████████
█████████████████████████
█████████████████████████
█████████████████████████
███████████████████████
█████████████████████
███████████████████
▀███████████████▀
███████████████████ | | .
|
|
|
|
|
Faisal2202
|
 |
September 28, 2023, 04:41:32 PM |
|
Public key hashes are the encrypted form of the public key, which is smaller in size and is the compact one. Hashing is not the same as encryption. Pubkey hashes are not encrypted public keys. Really! I mean aren't they made by encrypting the public key? Let's say you have a public key:
044f40875d8b57f9d80e12b54677893997c7573bf176711680356e0336a8c7b29fa26599a933e92 c3f8399587f38818991759b7a2778c74c86a17f25b8e9a272b This is not a valid public key. This is just an example, to show the OP what it actually looks like. |
|
|
|
|



