ThirdPrize2 (OP)
Jr. Member

 Offline Offline
Activity: 79
Merit: 1

|
 |
November 22, 2018, 03:28:52 PM |
|
I'm bored. How many different ways could there be to hack Bitcoin? I know it unlikely so don't bother telling me how unlikely it is. I want ideas.
1 - Start generating random pub/priv key pairs and their addresses. Keep a record and check them every now and again for transactions.
2 - Get a list of every word in the dictionary. You can generate keys using "phrases" as a seed. Try all the words and then all the combinations of words. Just like my Blockchain wallet.
3 - Take the output from point 1 and run it through some sort of neural net AI type thing. See if you can subconsciously train it to guess the keys for addresses.
4 - Like point 3 but with a quantum computer.
Any more?
|
|
|
|
|
|
|
|
The Bitcoin network protocol was designed to be extremely flexible. It can be used to create timed transactions, escrow transactions, multi-signature transactions, etc. The current features of the client only hint at what will be possible in the future.
|
|
|
Advertised sites are not endorsed by the Bitcoin Forum. They may be unsafe, untrustworthy, or illegal in your jurisdiction.
|
|
|
|
|
bob123
Legendary

 Offline Offline
Activity: 1624
Merit: 2481


|
None of your points really attacks bitcoin. And even less these are ways to 'hack' bitcoin.
What you are trying in point 1 and 2 is to attack math. That's something completely different. Senseless.
Point 3 and 4 don't make any sense either. You can't guess anything. That's not how it works. These are basically 'funny ideas' but not worth anything.
Also, people seem to believe that an AI is some kind of magic omniscient brain. That's not true. In the end, that's just IF-statements.
And quantum computer aren't magic machine either.
|
|
|
|
ThirdPrize2 (OP)
Jr. Member

 Offline Offline
Activity: 79
Merit: 1

|
 |
November 22, 2018, 03:39:43 PM |
|
None of your points really attacks bitcoin. And even less these are ways to 'hack' bitcoin.
What you are trying in point 1 and 2 is to attack math. That's something completely different. Senseless.
Point 3 and 4 don't make any sense either. You can't guess anything. That's not how it works. These are basically 'funny ideas' but not worth anything.
Also, people seem to believe that an AI is some kind of magic omniscient brain. That's not true. In the end, that's just IF-statements.
And quantum computer aren't magic machine either.
Optical recognition software will take a stream of 1s and 0s and can tell you if the picture they represent includes a face or a car (or whatever). You give it enough data and it can find patterns. |
|
|
|
|
ranochigo
Legendary

 Offline Offline
Activity: 2954
Merit: 4165

|
Optical recognition software will take a stream of 1s and 0s and can tell you if the picture they represent includes a face or a car (or whatever). You give it enough data and it can find patterns.
You can't find any pattern in Bitcoin (specifically address generation). The only reason why AI can figure out images is because they have a distinct pattern; human faces has specific features and cars has a standard look to it. Unfortunately, Bitcoin addresses is completely random so you can't use patterns to decipher anything. |
.
.HUGE. | | | | | | █▀▀▀▀
█
█
█
█
█
█
█
█
█
█
█
█▄▄▄▄ | ▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀
.
CASINO & SPORTSBOOK
▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ | ▀▀▀▀█
█
█
█
█
█
█
█
█
█
█
█
▄▄▄▄█ | | |
|
|
|
bones261
Legendary

 Offline Offline
Activity: 1806
Merit: 1826

|
 |
November 22, 2018, 03:45:47 PM |
|
2 - Get a list of every word in the dictionary. You can generate keys using "phrases" as a seed. Try all the words and then all the combinations of words. Just like my Blockchain wallet.
Actually, you don't need to list every word in a dictionary. With BIP39, there are only 2048 words to chose from. However, the longer the seed becomes, the more difficult it becomes to try and brute force it. Also, if a person decides to add a password on top of it, it becomes even more difficult. |
|
|
|
|
ABCbits
Legendary

 Offline Offline
Activity: 2856
Merit: 7407
Crypto Swap Exchange

|
 |
November 22, 2018, 04:38:51 PM |
|
If we're talking only about attacking Bitcoin in theory, there are plenty such as : 1. Looking for PRNG/CSPRNG flaw on open-source wallet. It already happens once with Google/Java's PRNG back in 2013 2. Brute-force brain wallet with common words in various language / popular terms 2. Hack multiple pools and perform 51% attack 3. Looking for bug on bitcoin protocol (signature, transaction/blockchain verification, etc.)  I'm sure it's slightly more likely than scenario you mentioned |
|
|
|
aliashraf
Legendary

 Offline Offline
Activity: 1456
Merit: 1174
Always remember the cause!


|
 |
November 22, 2018, 04:58:02 PM
Last edit: November 22, 2018, 07:00:11 PM by aliashraf Merited by ABCbits (1), pebwindkraft (1) |
|
OP! It is not even about bitcoin, not to mention hacking it.
Actually, hack is the last label one ever could find appropriate for brute forcing hashed public keys. A lot of literature out there showing how dumb it would be attempting such an attack. And it is brute force, clueless naive brute force, forget about AI and QC, neither of the two would be of little help in this context.
Bitcoin RIPEMD-160 addresses, are immune to both AI or any hypothetical analytical or heuristic function and Quantum Computing has nothing to do with the whole story. Decades(/centuries?) later once QC could become both commercially available and developed enough, their only cracking application against bitcoin would be breaking exposed public keys in their transient state, which will be mitigated before we are even close, I suppose.
So, you are left with an exhaustive brute force attack against an astronomical search space which is impractical as you are already aware. Aren't you?
|
|
|
|
|
ThirdPrize2 (OP)
Jr. Member

 Offline Offline
Activity: 79
Merit: 1

|
 |
November 22, 2018, 09:59:06 PM |
|
Actually, hack is the last label one ever could find appropriate for brute forcing hashed public keys. A lot of literature out there showing how dumb it would be attempting such an attack. And it is brute force, clueless naive brute force, forget about AI and QC, neither of the two would be of little help in this context.
I prefer the first two methods. Keep generating as many key pairs as you can and wait. As much chance of getting lucky as solo mining.  |
|
|
|
|
HeRetiK
Legendary

 Offline Offline
Activity: 2912
Merit: 2084
Cashback 15%

|
 |
November 23, 2018, 12:51:08 AM |
|
Actually, hack is the last label one ever could find appropriate for brute forcing hashed public keys. A lot of literature out there showing how dumb it would be attempting such an attack. And it is brute force, clueless naive brute force, forget about AI and QC, neither of the two would be of little help in this context.
I prefer the first two methods. Keep generating as many key pairs as you can and wait. As much chance of getting lucky as solo mining.  If you solo mine with a single Antminer S9 (ie. 14.5 TH/s) your chance of finding a block within a year is approx 1.9053% (assuming an average total network hashrate of 40,000,000 TH/s [1]). 14.5 TH/s of 40,000,000 TH/s = 0.00003625% 144 blocks/day * 365 = 52,560 blocks/year 52,560 blocks/year * 0.00003625% = 1.9053% If you bruteforce Bitcoin's key space using all computational power currently available to the Large Bitcoin Collider at roughly 365 Mkeys/s [2] your chance of finding an active private key within a year is approx 0.000000000000000000000000055% (assuming 550,000 used addresses [3]). 365 Mkey/s = 31.5 Tkey/day = 1.14975 * 10^16 keys/year 10^16 scanned keys * 550,000 used addresses of 10^48 (ie. 2^160 of 2^256 due to RIPEMD-160) = 5.5% * 10^-25 TLDR; You're approx 10^25 times less likely to find a private key with balance using hundreds of machines than you are to successfully mine a block using a single miner. That's the likeliness of getting hit by lightning during the same timeframe -- four times [4]. So not quite the same chance as getting lucky solo mining  [1] https://www.blockchain.com/en/charts/hash-rate[2] https://lbc.cryptoguru.org/stats[3] https://www.blockchain.com/charts/n-unique-addresses[4] https://www.cbs17.com/news/odds-of-winning-powerball-jackpot-less-than-being-hit-by-lightning-twice/1082701256 |
.
.HUGE. | | | | | | █▀▀▀▀
█
█
█
█
█
█
█
█
█
█
█
█▄▄▄▄ | ▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀
.
CASINO & SPORTSBOOK
▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ | ▀▀▀▀█
█
█
█
█
█
█
█
█
█
█
█
▄▄▄▄█ | | |
|
|
|
seoincorporation
Legendary

 Offline Offline
Activity: 3136
Merit: 2908
Top Crypto Casino

|
 |
November 23, 2018, 05:18:06 PM |
|
The main vulnerability of Bitcoin or any system are the users. But is really different to attack bitcoin and to attack users to get their bitcoins, if you want to attack bitcoin, then what you can do is to send 100,000 transactions every minute for 24h, and that way you will fuck up the network, no one says it would be easy or it would be cheap, but is the way to fuck it, if I'm not wrong they call it the network spam attack.
Now if the goal is to hack bitcoin users, then i can think in 2 ways, the first one is with trojans and keyloggers you know... the old school way. I have seen users who get hacked trying to play Mario for bitcoin, lol. And the other way i would recommend is the MITM attack, of course, you need to do this attack in the same network of the victim, but if you go to a bitcoin conference and poison the network, every guy there will be vulned.
|
|
|
|
HeRetiK
Legendary

 Offline Offline
Activity: 2912
Merit: 2084
Cashback 15%

|
 |
November 23, 2018, 07:13:23 PM |
|
The main vulnerability of Bitcoin or any system are the users. [...]
Now if the goal is to hack bitcoin users, then i can think in 2 ways, the first one is with trojans and keyloggers you know... the old school way. I have seen users who get hacked trying to play Mario for bitcoin, lol. And the
other way i would recommend is the MITM attack, of course, you need to do this attack in the same network of the victim, but if you go to a bitcoin conference and poison the network, every guy there will be vulned.
Good point. I guess social engineering is more effective than any direct attack on Bitcoin can ever be, so I'd probably add: 1) Create a shitcoin or shitfork for pump-and-dumping (disclaimer: I don't believe all alts are bad) 2) Create an ICO and spend years "developing" your "project" (disclaimer: I'm not so sure about ICOs though) 3) Run a HYIP 4) Offer cloud mining (essentially a HYIP without the H) (using a rather loose definition of social engineering, that is) |
.
.HUGE. | | | | | | █▀▀▀▀
█
█
█
█
█
█
█
█
█
█
█
█▄▄▄▄ | ▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀
.
CASINO & SPORTSBOOK
▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ | ▀▀▀▀█
█
█
█
█
█
█
█
█
█
█
█
▄▄▄▄█ | | |
|
|
|
mixoftix
Full Member
  
 Offline Offline
Activity: 131
Merit: 178
..


|
 |
November 23, 2018, 10:42:46 PM
Last edit: November 24, 2018, 05:39:11 AM by mixoftix Merited by ABCbits (1), aliashraf (1) |
|
3 - Take the output from point 1 and run it through some sort of neural net AI type thing. See if you can subconsciously train it to guess the keys for addresses.
sometimes this happens to tech guys who learn about AI / Unsupervised Learning Methods - just because unsupervised learning identifies commonalities in the data and reacts based on the presence or absence of such commonalities in each new piece of data - and you need to know that an encrypted message in not a normal data. there is a big misunderstanding here, because an encrypted message is the output of an Incorrect Algorithm. in definition of correct/incorrect algorithm we have: "An algorithm is said to be correct if, for every input instance, it halts with the correct ouput. We say that a correct algorithm solves the given computational problem. An incorrect algorithm might not halt at all on some input instances, or it might halt with an answer other than the desired one. Contrary to what one might expect, incorrect algorithms can sometimes be useful, if their error rate can be controlled." so we use incorrect algorithms in cryptography (to protect the plain data) and you can not find anything valuable in encrypted messages, because they are the output of incorrect algorithms. existing uncontrolled error rates in an incorrect algorithm means, encryption algorithms that build based on them are not standard or broken (perhaps most of unpublished encryption algorithms belong to this club). the bitcoin uses published encryption algorithm which been under accurate analysis of scientists for years - so don't waste your time in this part. |
Development of "Azim Blockchain" is in progress..
|
|
|
|
btc-room101
|
 |
November 29, 2018, 06:39:46 AM |
|
3 - Take the output from point 1 and run it through some sort of neural net AI type thing. See if you can subconsciously train it to guess the keys for addresses.
sometimes this happens to tech guys who learn about AI / Unsupervised Learning Methods - just because unsupervised learning identifies commonalities in the data and reacts based on the presence or absence of such commonalities in each new piece of data - and you need to know that an encrypted message in not a normal data. there is a big misunderstanding here, because an encrypted message is the output of an Incorrect Algorithm. in definition of correct/incorrect algorithm we have: "An algorithm is said to be correct if, for every input instance, it halts with the correct ouput. We say that a correct algorithm solves the given computational problem. An incorrect algorithm might not halt at all on some input instances, or it might halt with an answer other than the desired one. Contrary to what one might expect, incorrect algorithms can sometimes be useful, if their error rate can be controlled." so we use incorrect algorithms in cryptography (to protect the plain data) and you can not find anything valuable in encrypted messages, because they are the output of incorrect algorithms. existing uncontrolled error rates in an incorrect algorithm means, encryption algorithms that build based on them are not standard or broken (perhaps most of unpublished encryption algorithms belong to this club). the bitcoin uses published encryption algorithm which been under accurate analysis of scientists for years - so don't waste your time in this part. 'DONT DO THIS, YOU WILL SHOOT YOUR EYE OUT' What is it with all this, none of the people here have ever even tried to do this stuff, they just jump in and say "This isn't possible", how do you know if you haven't tried it? Take RNN-LSTM, you know you can train ML to do math, right? Ok, using Msieve and Sage, start small with simple ECDSA and work you way up to SECp256k1, learn to train, learn to train your machine to take simple public-addresses and generate the private-keys, then once you have the simple case working, move up to large prime-fields, always start small. Another thing is I mention Msieve, this lets you do a prime-decomposition, on the 'P' prime for Secp256k1, once you have the prime-factored, you can use ML to learn factoring, and again starting small you can train your ML to factor larger problems, like DLP for bitcoin. Baby-step/giant-step is the third case, there are many algo's for cracking ECDSA, this is just another learn to work with simple cases, and then turn your GPU loose on the big cases, The deal here is to understand the problem FIRST with the simple cases, and really understand discrete-modular arithmetic, and the DLP problem associated with BITCOIN. Me thinks that not a single person here really has ever done any of the above I concur the brute-force method is just plain dumb, that's why its called the NAIVE-METHOD to hack bitcoin. BITCOIN can be hacked, but its clear that if you talk real on this forum you get banned, blocked, ... there is a vested interest with BITCOIN old-boy community to just keep chugging along, and act like everything is fine. I suspect long after BITCOIN is hacked on a regular basis the people on this forum will still be in denial, and until their own coin goes missing will they pull their head out of the sand. |
|
|
|
|
|
btc-room101
|
 |
November 29, 2018, 06:56:15 AM |
|
OP! It is not even about bitcoin, not to mention hacking it.
Actually, hack is the last label one ever could find appropriate for brute forcing hashed public keys. A lot of literature out there showing how dumb it would be attempting such an attack. And it is brute force, clueless naive brute force, forget about AI and QC, neither of the two would be of little help in this context.
Bitcoin RIPEMD-160 addresses, are immune to both AI or any hypothetical analytical or heuristic function and Quantum Computing has nothing to do with the whole story. Decades(/centuries?) later once QC could become both commercially available and developed enough, their only cracking application against bitcoin would be breaking exposed public keys in their transient state, which will be mitigated before we are even close, I suppose.
So, you are left with an exhaustive brute force attack against an astronomical search space which is impractical as you are already aware. Aren't you?
HASHING doesn't have anything to do with BITCOIN hacking, the hash is just used to condense the public-key to an public address that is short, HASH is sha-256 on btc, ECDSA is the means that private/public keys are encrypted, k=d*P, where P is the prime for sec256k1, and d is the private key, k is the public key, which is hashed into hex(base16), and then into wif (base16), to be short It's clear that people who tell people here that something can't be done, don't even know what they're talking about. Hacking BTC means to try and find 'd' from k the public key, its irrelevant what hashing is as its a one-way operation When we're hacking we're running predictive private key space, and we convert that to a public-key, and hash and then compare with bloom filters if that 'hashed address' has value in the bloom. The means to which generate private-keys is done in blocks, the problem is k=d*P, but its in log form ( k=d+P) and we're solving for 'd', so d=k-P in log form, Sometimes we do know the public-key, because early on bitcoin had the public-keys public in the block-chain, but now they're all 'hashed' that's ok, because we can hash our 'guess' to the public-key when we have a candidate for its private-key If your 'hacking' and prefer to work with public-keys, then you work with the old legacy-satoshi coin, that's ok, because that is the GOOD STUFF anyhow If your hacking on the post 2013 block-chain about when they removed the public-keys, that's ok, because you can run though predictive private-keys, and get their public-keys and look to see if that address has 'value' One of the things with ML or SVM that is powerful is you can 'train' your ML to learn about associations of public-key with private-key, then you can use the prediction for a public-address to check for a region that the private-key may reside, You can also use FFT to look for periodicity in the training of your machine when learning the association of public-address ( hashed ) with private-keys, there is cyclic redundancy, there always is, just keep it simple in the early learning, so you can see the patterns. |
|
|
|
|
bob123
Legendary

 Offline Offline
Activity: 1624
Merit: 2481


|
 |
November 29, 2018, 07:17:11 AM |
|
[...]
BITCOIN can be hacked, but its clear that if you talk real on this forum you get banned, blocked,
[...]
You are probably the most intelligent person on the world. I wonder why noone has successively 'hacked' (just using this word brings discredit on you) bitcoin yet  Maybe because the whole world consists of retarded idiots (besides of you of course) ? ECDSA is safe if used correctly. The highest risks of 'hacking' (better: cracking) those keys come from a bad implementation (e.g. trough faulty implementation; side-channel attacks). We are talking about 256 bit curves here.. It is defined over prime fields and has no known vulnerability. The currently 'best attack' is Pollard's rho. |
|
|
|
mixoftix
Full Member
  
 Offline Offline
Activity: 131
Merit: 178
..


|
 |
November 29, 2018, 09:40:23 AM |
|
Take RNN-LSTM, you know you can train ML to do math, right?
hello btc-room. you know, I never underestimate anything new in this area, and I follow your post in url bellow about your called RNN-LSTM: https://bitcointalk.org/index.php?topic=5075651.0and before get in, I need you take a look at this post too, where we have discussed the way it could happen to predict "narrow-input" values for RNG that may influence the whole key-pair generation process: "Quantum Computing and Bitcoin" https://bitcointalk.org/index.php?topic=5075137.0and as bob123 said above, most of the time security-break happens during implementation steps, not in the math. for example you could also take a look at a post to IETF that talks about using multiple keys with multiple certificate authorities in a TLS session - in the case one authority compromised: https://www.ietf.org/mail-archive/web/tls/current/msg15293.html============== now you are talking about breaking ECDSA in its narrow-input level. I need to know: 1- if the problem that you are talking about is a backdoor in the field of "Kleptography"? in other words, the main math is correct but in some implementations (ECDSA) there is a backdoor in the algorithm? however this is again another problem in implementation, but if it is widely in use, then we could take it serious. 2- while this is a good idea to train your machine and then provide a web page that accepts some addresses and generates their private-keys for users, why don't you do that? then we could generate our addresses in pack of comma separated e.g. 10 addresses/pack and see how your codes works in practice. the result that we get from your online solution (with an existing trained machine - not a pure code) will make us read more and follow it.. |
Development of "Azim Blockchain" is in progress..
|
|
|
|
btc-room101
|
 |
November 30, 2018, 07:55:37 AM |
|
Take RNN-LSTM, you know you can train ML to do math, right?
hello btc-room. you know, I never underestimate anything new in this area, and I follow your post in url bellow about your called RNN-LSTM: https://bitcointalk.org/index.php?topic=5075651.0and before get in, I need you take a look at this post too, where we have discussed the way it could happen to predict "narrow-input" values for RNG that may influence the whole key-pair generation process: "Quantum Computing and Bitcoin" https://bitcointalk.org/index.php?topic=5075137.0and as bob123 said above, most of the time security-break happens during implementation steps, not in the math. for example you could also take a look at a post to IETF that talks about using multiple keys with multiple certificate authorities in a TLS session - in the case one authority compromised: https://www.ietf.org/mail-archive/web/tls/current/msg15293.html============== now you are talking about breaking ECDSA in its narrow-input level. I need to know: 1- if the problem that you are talking about is a backdoor in the field of "Kleptography"? in other words, the main math is correct but in some implementations (ECDSA) there is a backdoor in the algorithm? however this is again another problem in implementation, but if it is widely in use, then we could take it serious. 2- while this is a good idea to train your machine and then provide a web page that accepts some addresses and generates their private-keys for users, why don't you do that? then we could generate our addresses in pack of comma separated e.g. 10 addresses/pack and see how your codes works in practice. the result that we get from your online solution (with an existing trained machine - not a pure code) will make us read more and follow it.. 1.) Study ECDSA, and study Secp256k1 ( NSA curve factor that was created and used for bitcoin keys & sigs ), all the 'curves' of ESCDA have unique properties, unless one deeply study's Secp256k1, you don't really understand, you can experiment with SAGE & MSIEVE and learn a lot about curves and how they work, 2.) I think I already said that the ML, SVM, FFT can be used to feed DLP algo's base points for finding keys. Study baby-step/giant-step, google 'dlp algo's' there are a ton on wikipedia Another thing that can be done post 2013, as public-keys were no longer available, is there is a lot of non-noise high quality data in the digital-signatures posted in the block chain. There are endless ways to hack bitcoin Brainflayer can be re-deployed to find private-keys based on public-keys, and no-noise data, rather than simply hashing strings and using that as a priv-key compare Vanity-Gen can be re-deployed with bloom-filters and used to search for all used addresses for all clones&bitcoin at once,using optimized private-key blocks using DLP algo's |
|
|
|
|
HeRetiK
Legendary

 Offline Offline
Activity: 2912
Merit: 2084
Cashback 15%

|
 |
November 30, 2018, 05:46:33 PM |
|
[...]
Another thing that can be done post 2013, as public-keys were no longer available, is there is a lot of non-noise high quality data in the digital-signatures posted in the block chain. There are endless ways to hack bitcoin
Brainflayer can be re-deployed to find private-keys based on public-keys, and no-noise data, rather than simply hashing strings and using that as a priv-key compare
Vanity-Gen can be re-deployed with bloom-filters and used to search for all used addresses for all clones&bitcoin at once,using optimized private-key blocks using DLP algo's
What's preventing a would-be attacker from deploying any of these methods? What are the challenges they are facing? Serious question. At least to me the above sentences read pretty much like bullshit and a random assembly of technical terms but maybe it simply requires a more precise description of said techniques. As described they sound neither theoretically plausible nor practically feasible. |
.
.HUGE. | | | | | | █▀▀▀▀
█
█
█
█
█
█
█
█
█
█
█
█▄▄▄▄ | ▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀
.
CASINO & SPORTSBOOK
▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ | ▀▀▀▀█
█
█
█
█
█
█
█
█
█
█
█
▄▄▄▄█ | | |
|
|
|
|
|
|
rifiuti
|
 |
December 02, 2018, 09:14:01 AM |
|
Someone here either can't use search engines or doing this on purpose to get more activity to his account; 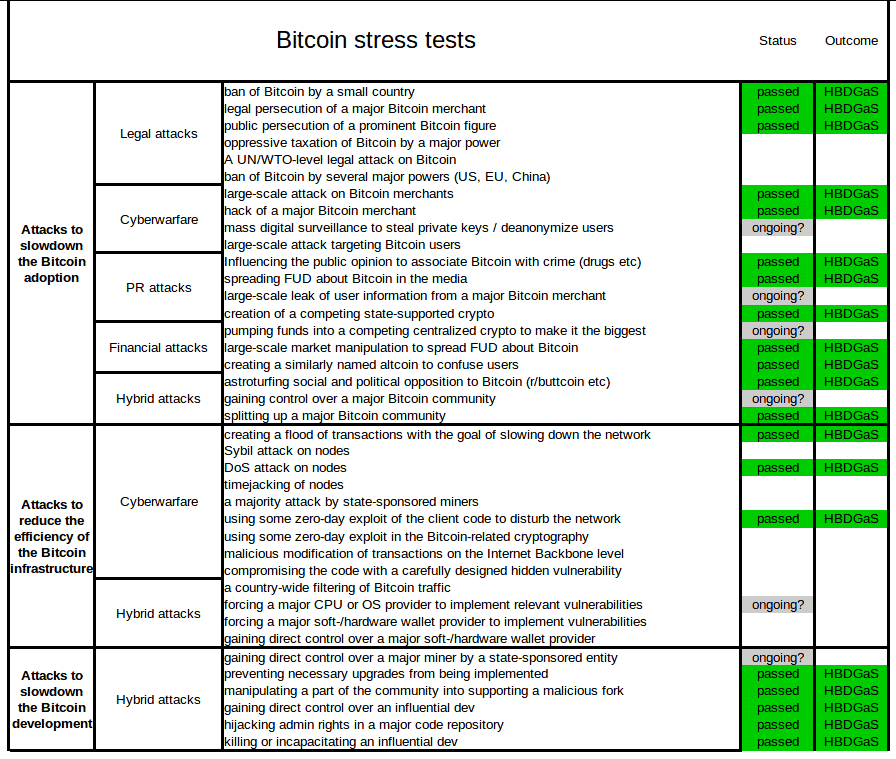 |
|
|
|
|
|



