fillippone (OP)
Legendary

 Offline Offline
Activity: 2156
Merit: 15504
Fully fledged Merit Cycler - Golden Feather 22-23


|
 |
August 13, 2019, 06:03:48 PM
Last edit: January 03, 2021, 10:44:20 AM by fillippone Merited by Welsh (10), joniboini (6), suchmoon (4), El duderino_ (4), dbshck (4), vapourminer (2), o_solo_miner (2), DdmrDdmr (2), 1miau (2), PrivacyG (2), Hueristic (1), JayJuanGee (1), pooya87 (1), Quickseller (1), tranthidung (1), OcTradism (1), protrader786 (1) |
|
A few days ago I read this news, that got my attention: LITECOIN WALLETS HIT BY LARGE-SCALE DUSTING ATTACK, SO WHAT IS IT?Here you can find a couple of paragraph: Reports are emerging that Litecoin wallets have been hit by a new kind of cyber-attack called dusting. It has not affected LTC markets but is something that crypto traders and holders should be aware of. Binance Academy offered an explanation.
In short, a dusting attack is when scammers attempt to break the privacy of a cryptocurrency, Litecoin in this case, by sending tiny amounts of it to private wallets. The attackers then attempt to trace the transactional activity of these wallets in an attempt to discover the identity of the person that owns them.
The term ‘dust’ refers to the tiny fractions of crypto coins that most users ignore. A couple of hundred satoshis may be referred to as ‘dust’ as the sum is so tiny that most people would not even notice it. It is also prevalent on crypto exchanges as the remnants of transactions that remain in wallets and can no longer be used or transferred.
Dust therefore refers to those amounts of cryptocurrencies that cannot be transferred individually either or because their amount is less than the transaction fees of the blockchain, or because they are lower than the minimum transferable out of an exchange, thus remaining blocked in the portfolio of the account at a specific exchange. Here you can find an video from Binance Academy that explains what a Dust Attack is: What Is a Dusting Attack?This technique is also used on Bitcoin, so try to be careful when you receive Satoshi without knowing where they are coming from. Why is dust attack dangerous? What is the use of sending satoshi to trace transactions if the transactions are actually public? Well the explanations can be multiple: - The attacker sends satoshi to a used address, with a positive balance. A curious mechanism, in reality, the attacker does not get any advantage, given that the movements of the address could also be monitored previously. The only advantage could be to "accustom" the user to receive funds on an address, thus making it less prudent in the real dust attack.
- The attacker sends satoshi to a used but empty address. The receiver then aggregates those satoshis to a new address by making a payment. At that point, the old address and the new one are "linked" and the attacker can, with methods of chain analysis, try to trace your identity, having discovered, however, that you also have control of the old address.
- The attacker sets up a bitcoin faucet (or a bitcoin fork - do you remember United Bitcoin?), where it is possible to get some satoshi upon registration with an email. At that point, if you combine those satoshis with your main address, well, the attacker has extra starting data to identify you (an email, even if fake, provides a lot of information, for example, a connection IP).
- Extremizing: an exchange that offers you $ 30 to register, after KYC, is practically performing a dust attack. Except that in that case, using the chain analysis company you just bought, you can perform a very efficient tracking of your UTXOs. Do you think this is an impossible scenario? it already happened.
- Exaggerating 2: an exchange (the same as the previous point) offers you $ 80 in shitcoins by answering easy videos and questions, after KYC, is practically performing a dust attack. Except that in that case, using the chain analysis company you just bought, you can perform a very efficient tracking of your UTXOs. Do you think this is an impossible scenario? It is happening now.
So, what to do when you receive dust on your wallet? Two cases: - Attacker sent you on a positive balance address: there's nothing much you can do about that. The address is public, the balance is public, having dust on such address is not something you can control. Spending this dust does not pose any additional threat than moving your coins on that address. You can consolidate those coins and keep with your usual life.
- Attacker sent you on a zero balance address: this is a proper dust attack. The address is public, but it is not possible to link to your current address. Spending this together with your coins poses a privacy risk. The attacker doesn't know anything about your current address, if you spend the two UTXO together they are able to link them.
For this reason, you have to use Coin Control feature: clearly mark that dust UTXO as "do not spend" (many wallets allow for this, Wasabi being one of those) to that attacker cannot track you down.
Another example is the exchange airdrops made by our government-friendly exchange: Let's work an example out. They give you some Stellar Lumens, provided you see some videos. Of course, you don't care about XLM's, so once you get them you sell them immediately for BTC. Since you are an advanced BTC user, you know that "not your keys, not your Bitcoin", so you get your BTC and withdraw them in your private wallet. You forget for a few weeks. Two months later, taking advantage of the empty mempool, you decide to consolidate your addresses into one. You then put those few satoshis together with your 100 BTC you bought back in 2010. Well, now the shrewd chain analytics company is able to understand that even the 100 BTC are yours. The chain analytics company sells the information to the tax authorities, and you're screwed. Or sell it to a criminal organization, and you're even more screwed. How to defend yourself: Two tips immediately come to mind: - Keep the "KYC" and "anonymous" addresses absolutely separate, many wallets allow different UTXOs to be marked with different labels: use this option!
- If you really need to consolidate the addresses, before doing so, let them go through a coinjoin. However, having an anonymous set is not perfect, but at least you don't have an obvious link to your address.
As usual, I will try to update this thread by completing it with better information and examples as they become available. I look forward to your comments! EDIT: Other reads: Beware the Dusting Attack |
.
.HUGE. | | | | | | █▀▀▀▀
█
█
█
█
█
█
█
█
█
█
█
█▄▄▄▄ | ▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀
.
CASINO & SPORTSBOOK
▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ | ▀▀▀▀█
█
█
█
█
█
█
█
█
█
█
█
▄▄▄▄█ | | |
|
|
|
|
|
|
|
|
|
|
|
|
Every time a block is mined, a certain amount of BTC (called the
subsidy) is created out of thin air and given to the miner. The
subsidy halves every four years and will reach 0 in about 130 years.
|
|
|
Advertised sites are not endorsed by the Bitcoin Forum. They may be unsafe, untrustworthy, or illegal in your jurisdiction.
|
|
|
|
|
|
|
fillippone (OP)
Legendary

 Offline Offline
Activity: 2156
Merit: 15504
Fully fledged Merit Cycler - Golden Feather 22-23


|
 |
August 15, 2019, 10:12:38 PM |
|
An update on the Binance Dust Attack LTC Dusting Attack on Binance Affected Nearly 300,000 Addresses: ReportThe recent dusting attack against fourth-biggest altcoin Litecoin (LTC) on major cryptocurrency exchange Binance affected 294,582 addresses rather than the 50 Binance reported, according to a recent metrics report.
Blockchain data and metrics firm Glassnode revealed its latest findings in a tweet on Aug. 15, saying that the LTC dusting attack affected 294,582 addresses. The analysis ostensibly also indicated a similar scale attack in April.
 Of course the given explanation is pretty ridicule. |
.
.HUGE. | | | | | | █▀▀▀▀
█
█
█
█
█
█
█
█
█
█
█
█▄▄▄▄ | ▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀
.
CASINO & SPORTSBOOK
▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ | ▀▀▀▀█
█
█
█
█
█
█
█
█
█
█
█
▄▄▄▄█ | | |
|
|
|
hatshepsut93
Legendary

 Offline Offline
Activity: 2968
Merit: 2147

|
Maybe this dusting is more of a spam attack, it creates new unspent outputs that are more expensive to move than they are worth, so it can make people overpay fees when they don't keep track of what input they use. This raises a question - are wallets these days smart enough to recognize some inputs as dust that is inefficient to move at the current fee, or would they mindlessly include it in transactions?
|
|
|
|
DdmrDdmr
Legendary

 Offline Offline
Activity: 2310
Merit: 10759
There are lies, damned lies and statistics. MTwain


|
 |
August 16, 2019, 08:33:38 AM |
|
A person at Binance Academy now suggest that it was not a dusting attact per se in intent (although not discardable), but rather an attempt to promote a specific mining pool based in Russia: “The person behind the dusting attack owns a mining pool based out of Russia, EMCD[dot]io. They reached out to express that their intent was to advertise their mining pool to the users of Litecoin, however, it's unclear from our perspective or anyone else's as to whether there were alternative motives. The owner of the pool was not aware that he was subjecting all these users to a dusting attack and spreading fear among the Litecoin community.
“It's interesting to note, that even if this was not the intent of the mining pool owner, he provided a base for malicious actors to analyze. You see, the person responsible for conducting the dusting attack doesn't necessarily have to be the one collecting the data, they can just merely be providing a service so that someone else can collect all the information and analyze it at a later date.”
See: https://cointelegraph.com/news/understanding-litecoins-dusting-attack-what-happened-and-why |
|
|
|
|
fillippone (OP)
Legendary

 Offline Offline
Activity: 2156
Merit: 15504
Fully fledged Merit Cycler - Golden Feather 22-23


|
 |
August 16, 2019, 08:43:52 AM |
|
<SNIP>
Yes, that article expand what it was posted in the previous article I linked this morning. And still, this explanation (the guy promoting his own mining pool) seems ridicule to me. But I might be missing something here. |
.
.HUGE. | | | | | | █▀▀▀▀
█
█
█
█
█
█
█
█
█
█
█
█▄▄▄▄ | ▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀
.
CASINO & SPORTSBOOK
▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ | ▀▀▀▀█
█
█
█
█
█
█
█
█
█
█
█
▄▄▄▄█ | | |
|
|
|
DdmrDdmr
Legendary

 Offline Offline
Activity: 2310
Merit: 10759
There are lies, damned lies and statistics. MTwain


|
 |
August 16, 2019, 08:49:39 AM |
|
<…> And still, this explanation (the guy promoting his own mining pool) seems ridicule to me. <…>
Not really. A dusting attack is what it is, and that is what you’ve explained in this thread. The specific Litecoin recent alleged attack, as with many other news published, evolves overtime, and what media promptly affirm one day may have a different edge on the following. In any case, the article pointing to it being a promotion stunt cannot discard ulterior motives. |
|
|
|
|
fillippone (OP)
Legendary

 Offline Offline
Activity: 2156
Merit: 15504
Fully fledged Merit Cycler - Golden Feather 22-23


|
 |
August 16, 2019, 08:55:49 AM |
|
<…> And still, this explanation (the guy promoting his own mining pool) seems ridicule to me. <…>
Not really. A dusting attack is what it is, and that is what you’ve explained in this thread. The specific Litecoin recent alleged attack, as with many other news published, evolves overtime, and what media promptly affirm one day may have a different edge on the following. In any case, the article pointing to it being a promotion stunt cannot discard ulterior motives. My point is: as a promotion stunt, I see this move pretty lame: I would actually stay well away from someone putting user's privacy at risk with such a unrequested move. So I think there are other "reasoning" behind these actions. And also agreed this news evolved from the strict notion of "dust attack". |
.
.HUGE. | | | | | | █▀▀▀▀
█
█
█
█
█
█
█
█
█
█
█
█▄▄▄▄ | ▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀
.
CASINO & SPORTSBOOK
▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ | ▀▀▀▀█
█
█
█
█
█
█
█
█
█
█
█
▄▄▄▄█ | | |
|
|
|
bitmover
Legendary

 Online Online
Activity: 2296
Merit: 5942
bitcoindata.science


|
 |
August 16, 2019, 11:22:22 AM |
|
It is also prevalent on crypto exchanges as the remnants of transactions that remain in wallets and can no longer be user or transferred.
This statement makes no sense to me. Maybe am I missing something? The guy who sent the dust is watching. But the remaining balance he could be watching anyway, even if he didn't send any dust to the address. If you don't use the remaining balance with other addresses in the same transaction you are just fine imo. Any thoughts? |
.
.BLACKJACK ♠ FUN. | | | ███▄██████
██████████████▀
████████████
█████████████████
████████████████▄▄
░█████████████▀░▀▀
██████████████████
░██████████████
█████████████████▄
░██████████████▀
████████████
███████████████░██
██████████ | | CRYPTO CASINO &
SPORTS BETTING | | │ | | │ | ▄▄███████▄▄
▄███████████████▄
███████████████████
█████████████████████
███████████████████████
█████████████████████████
█████████████████████████
█████████████████████████
███████████████████████
█████████████████████
███████████████████
▀███████████████▀
███████████████████ | | .
|
|
|
|
fillippone (OP)
Legendary

 Offline Offline
Activity: 2156
Merit: 15504
Fully fledged Merit Cycler - Golden Feather 22-23


|
 |
August 16, 2019, 11:26:43 AM |
|
It is also prevalent on crypto exchanges as the remnants of transactions that remain in wallets and can no longer be user or transferred.
This statement makes no sense to me. Maybe am I missing something? This statement refers to the fact we call "dust" also the change you leave on the exchanges (offchain dust) after you change your shitcoin into bitcoin. When you convert your BPA (BitcoinPizza) into BTC and you are left with 0.432 BPA and the minimum fees to transfer it is 0.5 PBA, then your change is basically lost (now some exchange offer ways to clean that thou), and then referred as "dust" The guy who sent the dust is watching. But the remaining balance he could be watching anyway, even if he didn't send any dust to the address.
If you don't use the remaining balance with other addresses in the same transaction you are just fine imo. Any thoughts?
Exactly, this was more or less analysed in the OP message. |
.
.HUGE. | | | | | | █▀▀▀▀
█
█
█
█
█
█
█
█
█
█
█
█▄▄▄▄ | ▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀
.
CASINO & SPORTSBOOK
▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ | ▀▀▀▀█
█
█
█
█
█
█
█
█
█
█
█
▄▄▄▄█ | | |
|
|
|
Quickseller
Copper Member
Legendary

 Offline Offline
Activity: 2870
Merit: 2301

|
 |
August 18, 2019, 05:32:54 AM |
|
A person at Binance Academy now suggest that it was not a dusting attact per se in intent (although not discardable), but rather an attempt to promote a specific mining pool based in Russia: “The person behind the dusting attack owns a mining pool based out of Russia, EMCD[dot]io. They reached out to express that their intent was to advertise their mining pool to the users of Litecoin, however, it's unclear from our perspective or anyone else's as to whether there were alternative motives. The owner of the pool was not aware that he was subjecting all these users to a dusting attack and spreading fear among the Litecoin community.
“It's interesting to note, that even if this was not the intent of the mining pool owner, he provided a base for malicious actors to analyze. You see, the person responsible for conducting the dusting attack doesn't necessarily have to be the one collecting the data, they can just merely be providing a service so that someone else can collect all the information and analyze it at a later date.”
See: https://cointelegraph.com/news/understanding-litecoins-dusting-attack-what-happened-and-whyThe intent of the person sending and funding the transactions doesn’t matter. Anyone looking after the fact can potentially break your privacy. It is also possible the stated reason is cover for his true intentions. |
|
|
|
|
DdmrDdmr
Legendary

 Offline Offline
Activity: 2310
Merit: 10759
There are lies, damned lies and statistics. MTwain


|
 |
August 18, 2019, 01:29:29 PM |
|
<…>
I know. That is the alleged reason, and the possibility of exploiting the action, regardless of the intention, is covered in the quoted text itself where it states: It's interesting to note, that even if this was not the intent of the mining pool owner, he provided a base for malicious actors to analyze.
|
|
|
|
|
Hueristic
Legendary

 Offline Offline
Activity: 3808
Merit: 4906
Doomed to see the future and unable to prevent it

|
 |
August 22, 2019, 12:59:26 AM |
|
So basically a dusting attack and then a "don't worry it was not an attack" response to lull the victims into not protecting themselves?
|
“Bad men need nothing more to compass their ends, than that good men should look on and do nothing.”
|
|
|
fillippone (OP)
Legendary

 Offline Offline
Activity: 2156
Merit: 15504
Fully fledged Merit Cycler - Golden Feather 22-23


|
 |
August 22, 2019, 04:09:55 PM |
|
So basically a dusting attack and then a "don't worry it was not an attack" response to lull the victims into not protecting themselves?
Social engineering is a good part of any attack. |
.
.HUGE. | | | | | | █▀▀▀▀
█
█
█
█
█
█
█
█
█
█
█
█▄▄▄▄ | ▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀
.
CASINO & SPORTSBOOK
▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ | ▀▀▀▀█
█
█
█
█
█
█
█
█
█
█
█
▄▄▄▄█ | | |
|
|
|
Hueristic
Legendary

 Offline Offline
Activity: 3808
Merit: 4906
Doomed to see the future and unable to prevent it

|
 |
August 22, 2019, 04:18:04 PM |
|
So basically a dusting attack and then a "don't worry it was not an attack" response to lull the victims into not protecting themselves?
Social engineering is a good part of any attack. True that, i had an idiot hand me a thumb drive to put something on for him that he found on the ground. Damn thats the oldest trick in the book. |
“Bad men need nothing more to compass their ends, than that good men should look on and do nothing.”
|
|
|
fillippone (OP)
Legendary

 Offline Offline
Activity: 2156
Merit: 15504
Fully fledged Merit Cycler - Golden Feather 22-23


|
 |
September 16, 2019, 11:52:17 AM |
|
So basically a dusting attack and then a "don't worry it was not an attack" response to lull the victims into not protecting themselves?
Social engineering is a good part of any attack. True that, i had an idiot hand me a thumb drive to put something on for him that he found on the ground. Damn thats the oldest trick in the book. Form an attacker point of view, the more a system is cryptographically secure, robust and offering minimum attack surface, the more concentrating on social engineering, human stupidity/complacency has an elevated payoff. |
.
.HUGE. | | | | | | █▀▀▀▀
█
█
█
█
█
█
█
█
█
█
█
█▄▄▄▄ | ▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀
.
CASINO & SPORTSBOOK
▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ | ▀▀▀▀█
█
█
█
█
█
█
█
█
█
█
█
▄▄▄▄█ | | |
|
|
|
Ann1989
Jr. Member

 Offline Offline
Activity: 38
Merit: 10

|
 |
December 05, 2019, 02:52:01 AM Merited by JayJuanGee (1) |
|
A few days agor I read this news, that got my attention: LITECOIN WALLETS HIT BY LARGE-SCALE DUSTING ATTACK, SO WHAT IS IT?Here you can find a couple of paragraph: Reports are emerging that Litecoin wallets have been hit by a new kind of cyber-attack called dusting. It has not affected LTC markets but is something that crypto traders and holders should be aware of. Binance Academy offered an explanation.
In short, a dusting attack is when scammers attempt to break the privacy of a cryptocurrency, Litecoin in this case, by sending tiny amounts of it to private wallets. The attackers then attempt to trace the transactional activity of these wallets in an attempt to discover the identity of the person that owns them.
The term ‘dust’ refers to the tiny fractions of crypto coins that most users ignore. A couple of hundred satoshis may be referred to as ‘dust’ as the sum is so tiny that most people would not even notice it. It is also prevalent on crypto exchanges as the remnants of transactions that remain in wallets and can no longer be user or transferred.
Dust therefore refers to those amounts of cryptocurrencies that cannot be transferred individually either or because their amount is less than the transaction fees of the blockchain, or because they are lower than the minimum transferable out of an exchange, thus remaining blocked in the portfolio of the account at a specific exchange. Here you can find an video from Binance Academy that explains what a Dust Attack is: What Is a Dusting Attack?This technique is also used on Bitcoin, so try to be careful when you receive Satoshi without knowing where they are coming from. Why is dust attack dangerous? What is the use of sending satoshi to trace transactions if the transactions are actually public? Well the explanations can be multiple: - The attacker sends satoshi to a used address, with a positive balance. Curious mechanism, in reality the attacker does not get any advantage, given that the movements of the address could also be monitored previously. The only advantage could be to "accustom" the user to receive funds on an address, thus making it less prudent in the real dust attack.
- The attacker sends satoshi to a used but empty address. The receiver then aggregates those satoshi to a new address by making a payment. At that point the old address and the new one are "linked" and the attacker can, with methods of chain analysis, try to trace your identity, having discovered, however, that you also have control of the old address.
- The attacker sets up a bitcoin faucet (or a bitcoin fork - do you remember United Bitcoin?), where it is possible to get some satoshi upon registration with an email. At that point, if you combine those satoshi with your main address, well, the attacker has extra starting data to identify you (an email, even if fake, provides a lot of information, for example a connection IP).
- Extremizing: an exchange that offers you $ 30 to register, after KYC, is practically performing a dust attack. Except that in that case, using the chain analysis company you just bought, you can perform a very efficient tracking of your UTXOs. Do you think this is an impossible scenario? it already happened.
- Exaggerating 2: an exchange (the same as the previous point) offers you $ 80 in shitcoins by answering easy videos and questions, after KYC, is practically performing a dust attack. Except that in that case, using the chain analysis company you just bought, you can perform a very efficient tracking of your UTXOs. Do you think this is an impossible scenario? It is happening now.
So, what to do when you receive dust on your wallet? Two cases: - Attacker sent you on a positive balance address: there's nothing much you can do about that. The address is public, the balance is public, having dust on such address is not something you can control. Spending this dust does not pose any additional threat than moving your coins on that address. You can consolidate those coins and keep with your usual life.
- Attacker sent you on a zero balance address: this is a proper dust attack. The address is public, built it is not possible to link to your current address. Spending this together with your coins poses a privacy risks. The attacker doesn't know anything about your current address, if you spend the two UTXO together they are able to link them.
For this reason you have to use Coin Control feature: clearly mark that dust UTXO as "do not spend" (many wallet allow for this, Wasabi being one of those) to that attacker cannot track you down.
Another example is the exchange airdop made by our government friendly exchange: Let's work an example out. They give you some Stellar Lumens, provided you see some videos. Of course you don't care about XLM's, so once you get them you sell them immediately for BTC. Since you are an advanced BTC user, you know that "not your keys not your Bitcoin", so you get your BTC and witdraw them in your private wallet. You froget it for a few weeks. Two months later, taking advantage of the empty mempool, you decide to consolidate your addresses into one. You then put those few satoshi together with your 100 BTC you bought back in 2010. Well, now the shrewd chain analytics company is able to understand that even the 100 BTC are yours. The chain analytics company sells the information to the tax authorities, and you're screwed. Or sell it to a criminal organization, and you're even more screwed. How to defend yourself: Two tips immediately come to mind: - Keep the "kyc" and "anonymous" addresses absolutely separate, many wallets allow different UTXOs to be marked with different labels: use this option!
- If you really need to consolidate the addresses, before doing so, let them go through a coinjoin. However, having an anonymous set is not perfect, but at least you don't have an obvious link to your address.
As usual I will try to update this thread by completing it with better information and examples as they become available. I look forward to your comments! This is nice. There's another article you could maybe use to add to this information - https://medium.com/cobo-vault/everything-you-need-to-know-about-the-dusting-attack-f0151f5a8843 |
|
|
|
|
pooya87
Legendary

 Offline Offline
Activity: 3444
Merit: 10558

|
 |
December 05, 2019, 05:40:02 AM |
|
The attacker sends satoshi to a used but empty address. The receiver then aggregates those satoshi to a new address by making a payment. At that point the old address and the new one are "linked" and the attacker can, with methods of chain analysis, try to trace your identity, having discovered, however, that you also have control of the old address.
this bold part is misleading because nobody can "trace your identity" this way, specially not by using blockchain analysis alone. all they can do is linking the different addresses if they weren't linked before only when the user consolidates the inputs in one transaction. and an address is not revealing the identity of the user on its own. |
.
.BLACKJACK ♠ FUN. | | | ███▄██████
██████████████▀
████████████
█████████████████
████████████████▄▄
░█████████████▀░▀▀
██████████████████
░██████████████
█████████████████▄
░██████████████▀
████████████
███████████████░██
██████████ | | CRYPTO CASINO &
SPORTS BETTING | | │ | | │ | ▄▄███████▄▄
▄███████████████▄
███████████████████
█████████████████████
███████████████████████
█████████████████████████
█████████████████████████
█████████████████████████
███████████████████████
█████████████████████
███████████████████
▀███████████████▀
███████████████████ | | .
|
|
|
|
fillippone (OP)
Legendary

 Offline Offline
Activity: 2156
Merit: 15504
Fully fledged Merit Cycler - Golden Feather 22-23


|
 |
December 05, 2019, 07:29:48 AM |
|
<...>
This is nice.
<...>
Please, learn to quote responsibly. It's not necessary to include the whole original text if you are replying to the thread without a specific quote reference. I might suggest you two threads to help you familiarize with such topics: The attacker sends satoshi to a used but empty address. The receiver then aggregates those satoshi to a new address by making a payment. At that point the old address and the new one are "linked" and the attacker can, with methods of chain analysis, try to trace your identity, having discovered, however, that you also have control of the old address.
this bold part is misleading because nobody can "trace your identity" this way, specially not by using blockchain analysis alone. all they can do is linking the different addresses if they weren't linked before only when the user consolidates the inputs in one transaction. and an address is not revealing the identity of the user on its own. Bitcoin it is not an anonymous protocol, but a pseudonymous. If an exchange gives you a few satoshi and you consolidate those with your bitcoin stash, they are perfectly able to link your KYC'd addresses to the pseudonymous one. Same thing if they send dust to an empty address and if you send to a KYC'd address (or an address "touched" with a KYC'd one). This is what the sentence ion bold meant. Please remember that this is not fantasy: Coinbase buying Neutrino (chain analysis company) AND giving out satoshis ( https://www.coinbase.com/earn) is the reality. |
.
.HUGE. | | | | | | █▀▀▀▀
█
█
█
█
█
█
█
█
█
█
█
█▄▄▄▄ | ▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀
.
CASINO & SPORTSBOOK
▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ | ▀▀▀▀█
█
█
█
█
█
█
█
█
█
█
█
▄▄▄▄█ | | |
|
|
|
pooya87
Legendary

 Offline Offline
Activity: 3444
Merit: 10558

|
 |
December 05, 2019, 01:50:37 PM |
|
this bold part is misleading because nobody can "trace your identity" this way, specially not by using blockchain analysis alone. all they can do is linking the different addresses if they weren't linked before only when the user consolidates the inputs in one transaction. and an address is not revealing the identity of the user on its own.
Bitcoin it is not an anonymous protocol, but a pseudonymous. If an exchange gives you a few satoshi and you consolidate those with your bitcoin stash, they are perfectly able to link your KYC'd addresses to the pseudonymous one. Same thing if they send dust to an empty address and if you send to a KYC'd address (or an address "touched" with a KYC'd one). This is what the sentence ion bold meant. exactly my point. they can not identify you by only using "dust attack" technique that you explained here. for example someone can have 2 addresses both not-linked to his identity. first one that is empty receives dust then he links it to the second one, there still is no way of linking these two to his identity. similarly the another person may have 2 addresses both linked to his identity, the empty one receives dust and he links it to the other one. no additional privacy was lost here. |
.
.BLACKJACK ♠ FUN. | | | ███▄██████
██████████████▀
████████████
█████████████████
████████████████▄▄
░█████████████▀░▀▀
██████████████████
░██████████████
█████████████████▄
░██████████████▀
████████████
███████████████░██
██████████ | | CRYPTO CASINO &
SPORTS BETTING | | │ | | │ | ▄▄███████▄▄
▄███████████████▄
███████████████████
█████████████████████
███████████████████████
█████████████████████████
█████████████████████████
█████████████████████████
███████████████████████
█████████████████████
███████████████████
▀███████████████▀
███████████████████ | | .
|
|
|
|
fillippone (OP)
Legendary

 Offline Offline
Activity: 2156
Merit: 15504
Fully fledged Merit Cycler - Golden Feather 22-23


|
 |
December 05, 2019, 02:05:44 PM
Last edit: December 05, 2019, 02:16:12 PM by fillippone |
|
exactly my point.
Ok. So we do agree. The misunderstanding comes from the fact that I define (as I think also all the link I surveyed) the dust attack as not only the sole act of sending dust to an address, but also the complex of following actions, that, if not properly monitored by the recipient of this attack, can lead to some loss of privacy. |
.
.HUGE. | | | | | | █▀▀▀▀
█
█
█
█
█
█
█
█
█
█
█
█▄▄▄▄ | ▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀
.
CASINO & SPORTSBOOK
▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ | ▀▀▀▀█
█
█
█
█
█
█
█
█
█
█
█
▄▄▄▄█ | | |
|
|
|
|
UserU
|
 |
December 05, 2019, 03:22:59 PM |
|
So I guess this can apply even on gambling and faucets?
Imagine faucet sites on FBC, then there's no way to find out if we've been dusted or not.
|
.
.500 CASINO.██ | ▄▀ |
▄
▄ | | .
THE HOTTEST CRYPTO
CASINO & SPORTSBOOK | | ▄▄▄████████████
▄▄▄███████████████████
▐█████████████████████
█████████████████████
▐███████████████████
▐███████████████████
███████████████████
██████▀█████▀██████
▐████████▀█████████
▐███████████████████
███████████████████
▐███████████████████
▀██████▀▀▀▀▀▀ ▀▀▀█ | ▄▄▄▀▀▀▀▀▀▀▄▄▄
▄▄▀▀▄ ▄ ▀ ▀ ▀ ▄ ▄▀▀▄▄
▄▀▄ ▀ ▀ ▄▀▄
█ ▄ ▄ █
█ ▄ █████ ▄███▄ ▄███▄ ▄ █
█ ▄ ██▄▄ ██ ██ ██ ██ ▄ █
█ ▄ ▀▀▀██ ██ ██ ██ ██ ▄ █
█ ▄ ▄▄ ██ ██ ██ ██ ██ ▄ █
█ ▄ ▀███▀ ▀███▀ ▀███▀ ▄ █
█ ▄ ▄ █
▀▄ ▀ ▄ ▄ ▀ ▄▀
▀▀▄▄ ▀ ▄ ▄ ▄ ▄ ▀ ▄▄▀▀
▀▀▀▄▄▄▄▄▄▄▀▀▀ |
█▄▄▄██████████▄▄▄
███████████▀██▀▀██▄▄
███████████████████▄
█████████████████████
████▄████▄███████▄███
█████████████████████
████▀████▀███████▀███
█████████████████████
███████████████████▀
███████████▄██▄▄██▀▀
▀▀▀██████████▀▀▀ | |
► ORIGINALS
► SLOTS | |
► LIVE GAMES
► SPORTSBOOK |
▄
▄
| ▀▄ | .
██..PLAY NOW.. |
|
|
|
fillippone (OP)
Legendary

 Offline Offline
Activity: 2156
Merit: 15504
Fully fledged Merit Cycler - Golden Feather 22-23


|
 |
December 05, 2019, 03:39:30 PM |
|
Exactely, faucets are another way of doing so.
The point is Faucets are rarely properly KYC'd, so it's difficult to link them to an identity.
|
.
.HUGE. | | | | | | █▀▀▀▀
█
█
█
█
█
█
█
█
█
█
█
█▄▄▄▄ | ▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀
.
CASINO & SPORTSBOOK
▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ | ▀▀▀▀█
█
█
█
█
█
█
█
█
█
█
█
▄▄▄▄█ | | |
|
|
|
|
naska21
|
 |
December 05, 2019, 06:14:55 PM |
|
snip
Last moth my empty and never used BTC address published on forum to authenticate my account has got 555 sat. Sure that was the dust attack but I wonder what for? who might have interest in me? |
|
|
|
|
fillippone (OP)
Legendary

 Offline Offline
Activity: 2156
Merit: 15504
Fully fledged Merit Cycler - Golden Feather 22-23


|
 |
December 05, 2019, 08:55:09 PM |
|
They shoot in the mass.
They are not targeting at you. Just shooting in the mass and hoping to fish something.
|
.
.HUGE. | | | | | | █▀▀▀▀
█
█
█
█
█
█
█
█
█
█
█
█▄▄▄▄ | ▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀
.
CASINO & SPORTSBOOK
▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ | ▀▀▀▀█
█
█
█
█
█
█
█
█
█
█
█
▄▄▄▄█ | | |
|
|
|
figmentofmyass
Legendary

 Offline Offline
Activity: 1652
Merit: 1483

|
 |
December 05, 2019, 10:19:38 PM Merited by fillippone (1) |
|
Bitcoin it is not an anonymous protocol, but a pseudonymous. If an exchange gives you a few satoshi and you consolidate those with your bitcoin stash, they are perfectly able to link your KYC'd addresses to the pseudonymous one. Same thing if they send dust to an empty address and if you send to a KYC'd address (or an address "touched" with a KYC'd one). This is what the sentence ion bold meant.
exactly my point. they can not identify you by only using "dust attack" technique that you explained here. for example someone can have 2 addresses both not-linked to his identity. first one that is empty receives dust then he links it to the second one, there still is no way of linking these two to his identity. similarly the another person may have 2 addresses both linked to his identity, the empty one receives dust and he links it to the other one. no additional privacy was lost here. all that says is that bitcoin is pseudonymous, which fillippone just stated. we already know that. all of bitcoin's privacy pitfalls require a link to real-life identity to be meaningful. how about the case where one address gets dusted, then linked to a second address (or cluster of addresses) which is already linked to your identity? |
|
|
|
Velkro
Legendary

 Offline Offline
Activity: 2296
Merit: 1014

|
 |
December 06, 2019, 12:01:52 AM |
|
Maybe this dusting is more of a spam attack, it creates new unspent outputs that are more expensive to move than they are worth, so it can make people overpay fees
This is a lot more likely than theory of topic author. I mean it have actual money reason to do that, and privacy concern? I didnt get it, and tried really hard of what topic author wrote. Its too far fetched for me, privacy is not affected here. |
|
|
|
|
|
naska21
|
 |
December 06, 2019, 06:05:01 PM |
|
They shoot in the mass.
They are not targeting at you. Just shooting in the mass and hoping to fish something.
Yeah, I know that but in my case by single trx they targeted around ten addresses , all of them are from bitcointalk and that surprised me. |
|
|
|
|
fillippone (OP)
Legendary

 Offline Offline
Activity: 2156
Merit: 15504
Fully fledged Merit Cycler - Golden Feather 22-23


|
 |
December 06, 2019, 06:50:41 PM |
|
Maybe this dusting is more of a spam attack, it creates new unspent outputs that are more expensive to move than they are worth, so it can make people overpay fees
This is a lot more likely than theory of topic author. I mean it have actual money reason to do that, and privacy concern? I didnt get it, and tried really hard of what topic author wrote. Its too far fetched for me, privacy is not affected here. Doing this kind of research and sell it to the government, or the IRS, is a is a fantastic business opportunity to gain from this kind of attack. Again this is not theory, but practice, done every day by chain analysis companies. Your privacy is at risk, and privacy is one of those goods that are vastly underappreciated until it’s lost. |
.
.HUGE. | | | | | | █▀▀▀▀
█
█
█
█
█
█
█
█
█
█
█
█▄▄▄▄ | ▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀
.
CASINO & SPORTSBOOK
▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ | ▀▀▀▀█
█
█
█
█
█
█
█
█
█
█
█
▄▄▄▄█ | | |
|
|
|
bitbro678
Jr. Member

 Offline Offline
Activity: 40
Merit: 1

|
 |
December 11, 2019, 06:05:43 AM Merited by JayJuanGee (1) |
|
this bold part is misleading because nobody can "trace your identity" this way, specially not by using blockchain analysis alone. all they can do is linking the different addresses if they weren't linked before only when the user consolidates the inputs in one transaction. and an address is not revealing the identity of the user on its own.
Bitcoin it is not an anonymous protocol, but a pseudonymous. If an exchange gives you a few satoshi and you consolidate those with your bitcoin stash, they are perfectly able to link your KYC'd addresses to the pseudonymous one. Same thing if they send dust to an empty address and if you send to a KYC'd address (or an address "touched" with a KYC'd one). This is what the sentence ion bold meant. exactly my point. they can not identify you by only using "dust attack" technique that you explained here. for example someone can have 2 addresses both not-linked to his identity. first one that is empty receives dust then he links it to the second one, there still is no way of linking these two to his identity. similarly the another person may have 2 addresses both linked to his identity, the empty one receives dust and he links it to the other one. no additional privacy was lost here. If someone wanted to identify you, I doubt if they would send dust to an empty address. Since everything is on the blockchain, they would send dust to addresses that have a fairly decent amount of crypto. If that address gets linked to another address that is linked to a person's identity, then they now know the person behind it. But then again, if you're really not bothered about privacy as such, a dust attack wouldn't affect you. |
|
|
|
|
Globb0
Legendary

 Offline Offline
Activity: 2674
Merit: 2053
Free spirit

|
 |
January 29, 2020, 09:23:22 PM |
|
SHUM +1
|
|
|
|
|
Kakmakr
Legendary

 Offline Offline
Activity: 3444
Merit: 1957
Leading Crypto Sports Betting & Casino Platform

|
 |
January 30, 2020, 12:12:19 PM Merited by fillippone (2) |
|
Why would you want to consolidate your "dust" transactions for a few Satoshi's? You would be burning more Satoshi's in miners fees to consolidate it, than gaining anything from it. They might have done this on LiteCoin, because the fees are lower than Bitcoin, but it will never work for Bitcoin, because the miners fees in Bitcoin is much higher. Also, consolidating "dust" into a single Bitcoin address would simply be a stupid idea. I have several coin spread out over a bunch of addresses, because I do not want someone to trace all my coins back to me. <This includes addresses from Paper wallets, desktop wallets, hardware wallets, exchanges and web wallets.> Proper coin management and the use of Mixer services will render this attack useless.  |
| ..Stake.com.. | | | ▄████████████████████████████████████▄
██ ▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄▄▄▄ ██ ▄████▄
██ ▀▀▀▀▀▀▀▀▀▀ ██████████ ▀▀▀▀▀▀▀▀▀▀ ██ ██████
██ ██████████ ██ ██ ██████████ ██ ▀██▀
██ ██ ██ ██████ ██ ██ ██ ██ ██
██ ██████ ██ █████ ███ ██████ ██ ████▄ ██
██ █████ ███ ████ ████ █████ ███ ████████
██ ████ ████ ██████████ ████ ████ ████▀
██ ██████████ ▄▄▄▄▄▄▄▄▄▄ ██████████ ██
██ ▀▀▀▀▀▀▀▀▀▀ ██
▀█████████▀ ▄████████████▄ ▀█████████▀
▄▄▄▄▄▄▄▄▄▄▄▄███ ██ ██ ███▄▄▄▄▄▄▄▄▄▄▄▄
██████████████████████████████████████████ | | | | | | ▄▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▄
█ ▄▀▄ █▀▀█▀▄▄
█ █▀█ █ ▐ ▐▌
█ ▄██▄ █ ▌ █
█ ▄██████▄ █ ▌ ▐▌
█ ██████████ █ ▐ █
█ ▐██████████▌ █ ▐ ▐▌
█ ▀▀██████▀▀ █ ▌ █
█ ▄▄▄██▄▄▄ █ ▌▐▌
█ █▐ █
█ █▐▐▌
█ █▐█
▀▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▀█ | | | | | | ▄▄█████████▄▄
▄██▀▀▀▀█████▀▀▀▀██▄
▄█▀ ▐█▌ ▀█▄
██ ▐█▌ ██
████▄ ▄█████▄ ▄████
████████▄███████████▄████████
███▀ █████████████ ▀███
██ ███████████ ██
▀█▄ █████████ ▄█▀
▀█▄ ▄██▀▀▀▀▀▀▀██▄ ▄▄▄█▀
▀███████ ███████▀
▀█████▄ ▄█████▀
▀▀▀███▄▄▄███▀▀▀ | | | ..PLAY NOW.. |
|
|
|
20kevin20
Legendary

 Offline Offline
Activity: 1134
Merit: 1597

|
 |
January 30, 2020, 12:25:08 PM |
|
I know this topic is old and has been revived yesterday by someone, but I just found it and I can relate to it. My XRP, LTC, BTC, BCH, ETH and DASH addresses have all received dust transactions from an unknown address. I've never done KYC anywhere, nor are my addresses linked to my real identity in any way. Is there anything I must do? Some of them MIGHT be empty, but I'm not entirely sure.
Now, after reading the last part of the thread posted by the OP, I have another theory: governments may be conducting this process of blockchain analyzing in order to find the identity of a person for money laundering and tax evasion purposes.
I'm using Ledger by the way.
|
|
|
|
|
fillippone (OP)
Legendary

 Offline Offline
Activity: 2156
Merit: 15504
Fully fledged Merit Cycler - Golden Feather 22-23


|
 |
January 30, 2020, 01:28:25 PM |
|
I know this topic is old and has been revived yesterday by someone, but I just found it and I can relate to it. My XRP, LTC, BTC, BCH, ETH and DASH addresses have all received dust transactions from an unknown address. I've never done KYC anywhere, nor are my addresses linked to my real identity in any way. Is there anything I must do? Some of them MIGHT be empty, but I'm not entirely sure.
Now, after reading the last part of the thread posted by the OP, I have another theory: governments may be conducting this process of blockchain analyzing in order to find the identity of a person for money laundering and tax evasion purposes.
I'm using Ledger by the way.
Many modern wallet (for bicoin for sure, I don't know anything about shitcoins) have a "do not spend" feature you can tag given UTXO with. So tagging in this way your dust prevents you doing stupid things with that. |
.
.HUGE. | | | | | | █▀▀▀▀
█
█
█
█
█
█
█
█
█
█
█
█▄▄▄▄ | ▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀
.
CASINO & SPORTSBOOK
▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ | ▀▀▀▀█
█
█
█
█
█
█
█
█
█
█
█
▄▄▄▄█ | | |
|
|
|
hatshepsut93
Legendary

 Offline Offline
Activity: 2968
Merit: 2147

|
 |
January 30, 2020, 02:25:15 PM Merited by JayJuanGee (1) |
|
I know this topic is old and has been revived yesterday by someone, but I just found it and I can relate to it. My XRP, LTC, BTC, BCH, ETH and DASH addresses have all received dust transactions from an unknown address. I've never done KYC anywhere, nor are my addresses linked to my real identity in any way. Is there anything I must do? Some of them MIGHT be empty, but I'm not entirely sure.
Now, after reading the last part of the thread posted by the OP, I have another theory: governments may be conducting this process of blockchain analyzing in order to find the identity of a person for money laundering and tax evasion purposes.
I'm using Ledger by the way.
Can you analyze to what sort of addresses did you receive that dust? Was that the addresses that you used to withdraw from some exchanges? If so, can you tell from which exchanges? Or was it some other services? Or maybe addresses that were never used (but how it can even possibly happen?)? Maybe we can get some idea who is behind this dusting if we try to start tracking them. |
|
|
|
20kevin20
Legendary

 Offline Offline
Activity: 1134
Merit: 1597

|
 |
January 30, 2020, 03:42:44 PM Merited by JayJuanGee (1) |
|
Can you analyze to what sort of addresses did you receive that dust? Was that the addresses that you used to withdraw from some exchanges? If so, can you tell from which exchanges? Or was it some other services? Or maybe addresses that were never used (but how it can even possibly happen?)? Maybe we can get some idea who is behind this dusting if we try to start tracking them.
I'll try analizing them ASAP, although I will not share them due to privacy reasons. They are not addresses that I used on exchanges. In fact, I do not remember using any of my addresses on exchanges and I believe I have not used them for services either. Will try tracking the dust addresses down but I don't know if I'll get to any results. Many modern wallet (for bicoin for sure, I don't know anything about shitcoins) have a "do not spend" feature you can tag given UTXO with.
So tagging in this way your dust prevents you doing stupid things with that.
I will have to look into that, I've never seen this option on my Ledger though. Thanks for the suggestion, although I think I've even spent some of the UTXOs already..   |
|
|
|
|
fillippone (OP)
Legendary

 Offline Offline
Activity: 2156
Merit: 15504
Fully fledged Merit Cycler - Golden Feather 22-23


|
 |
January 30, 2020, 03:47:21 PM |
|
Many modern wallet (for bicoin for sure, I don't know anything about shitcoins) have a "do not spend" feature you can tag given UTXO with.
So tagging in this way your dust prevents you doing stupid things with that.
I will have to look into that, I've never seen this option on my Ledger though. Thanks for the suggestion, although I think I've even spent some of the UTXOs already..   IF you use your Ledger togheter with Electrum you can use the "freeze Coin" option: What does it mean to “freeze” an address in Electrum?
When you freeze an address, the funds in that address will not be used for sending bitcoins. You cannot send bitcoins if you don’t have enough funds in the non-frozen addresses.
https://electrum.readthedocs.io/en/latest/faq.html#what-does-it-mean-to-freeze-an-address-in-electrum |
.
.HUGE. | | | | | | █▀▀▀▀
█
█
█
█
█
█
█
█
█
█
█
█▄▄▄▄ | ▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀
.
CASINO & SPORTSBOOK
▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ | ▀▀▀▀█
█
█
█
█
█
█
█
█
█
█
█
▄▄▄▄█ | | |
|
|
|
20kevin20
Legendary

 Offline Offline
Activity: 1134
Merit: 1597

|
 |
January 30, 2020, 06:20:18 PM |
|
Thanks. I don't use it with Electrum, unfortunately. Anyway, I thought there might've been some risk if I'd spend my BTC balance with the dust from it too, but as soon as it hasn't been connected in any way to my identity ever since I started using Bitcoin, I think I'm fine. I don't plan to share my ID with anyone in the near future either. I've browsed a little through my transactions and apparently I cannot find the Bitcoin dust txid. Might have been a paper wallet or my mobile one. I've found two of the dust transactions I had through alts though, I'm going off-topic but I'll leave the information here in case anyone is interested to research them. First, the most recent dust tx, we have a Ripple transaction with a memo (description) attached to it: "NETWORK ANNOUNCEMENT: Ripple unlocks 50% stake in XRP, indicates massive airdrop www.*hidden fraud domain*". Seems like someone tried to scam by sending dust XRP with links in memos. I looked the memo up on Google and found this wallet: https://bithomp.com/explorer/rpWhspQz4DX5N5NoPDpvFtkcpyZiNa9Uv1, which confirms my doubts. A second dust sent to my wallet was through a LTC tx: https://live.blockcypher.com/ltc/tx/c0ad0412027347d137f5f8c18ad0b61064d7051a8b57f97d09101bceabfd8c07/. The user apparently sent this to 2000+ different wallets. |
|
|
|
|
fillippone (OP)
Legendary

 Offline Offline
Activity: 2156
Merit: 15504
Fully fledged Merit Cycler - Golden Feather 22-23


|
 |
June 19, 2020, 01:16:14 PM |
|
A nice read about dust attacks I found recently, even if the article itself is quite old: Bitcoin Data Science (Pt. 3): Dust & ThermodynamicsIt contains, for the most technical experts, a good technical analyis of dust, how it is created, and how it is sort of "natural" in bitcoin system. What it is not natural is the malicious use you can do with dust. We examine the history and future of dust: containers (UTXOs) of bitcoin that cost more to spend in fees than they hold.
The amount of dust in the blockchain is determined by the current UTXO set and transaction fee market. At peak fees (~December 2017), between 25–50% of the UTXOs in the Bitcoin blockchain could have been called dust! At the same time, the amount of BTC contained in these dusty UTXOs was small: only a few tens of millions of dollars. So, depending on how you measure it, dust is either a huge problem or a trivial one. Either way, we discuss possible solutions for minimizing new dust and cleaning up existing dust.
Proof-of-work strongly anchors bitcoin in the physical world and makes it subject to the laws of thermodynamics. Energy expended by miners secures the blockchain, but this useful work is accompanied by an increase in entropy and the production of waste heat. If the Bitcoin blockchain were an engine, dusty UTXOs would be a part of the waste heat it exhausts. As no engine is perfectly efficient, Bitcoin will never stop making dust.
|
.
.HUGE. | | | | | | █▀▀▀▀
█
█
█
█
█
█
█
█
█
█
█
█▄▄▄▄ | ▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀
.
CASINO & SPORTSBOOK
▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ | ▀▀▀▀█
█
█
█
█
█
█
█
█
█
█
█
▄▄▄▄█ | | |
|
|
|
fillippone (OP)
Legendary

 Offline Offline
Activity: 2156
Merit: 15504
Fully fledged Merit Cycler - Golden Feather 22-23


|
 |
August 19, 2020, 11:51:46 AM |
|
Dust Attack hitting the news again on Coindesk: Dust Attacks Make a Mess in Bitcoin Wallets, but There Could Be a FixWhen dust settles in your home, you wipe it up. But what about when unwanted dust makes its way into your bitcoin wallet? Well, cleaning it up may not be so simple Nothing new, or nothing already written in this thread. Two passages need a special comment, in my opinion: CoinDesk reached out to Chainalysis and CipherTrace to ask if they use dust in their analytics. Both companies denied using this technique, though Chainalysis Manager of Investigation Justin Maile added that dusting is “more often [used] by investigators” to trace illicit funds. Maile continued that exchanges may use dusting to trace stolen funds following a hack. LOL! Of course they don't do that! But other do that! Facepalm. Broken Logic. Hypocrisy. Chain analysis firm are bad. Bonus Read: A treatise on privacyAlso this one: “When the dust is consolidated with the user’s other funds, it helps with chain analytics by making it easier to cluster addresses,” Sergej Kotliar, the CEO of Bitrefill, told CoinDesk. If users don’t consolidate the unspent transactions (UTXOs), then they don’t need to worry about their anonymity. However, most wallets automatically consolidate UTXOs when a user creates a transaction, so this can be tough to navigate around unless you are choosing which UTXOs to spend manually. This is exactly the point: they send you the dust hoping you do stupid things with that (like consolidating with your existent UTXO). Please note that consolidating doesn't mean aggregate the outputs, something that might require your intervention, but also aggregating those UTXO's as a transaction input. Something a wallet could do, if you don't take the necessary precautions. |
.
.HUGE. | | | | | | █▀▀▀▀
█
█
█
█
█
█
█
█
█
█
█
█▄▄▄▄ | ▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀
.
CASINO & SPORTSBOOK
▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ | ▀▀▀▀█
█
█
█
█
█
█
█
█
█
█
█
▄▄▄▄█ | | |
|
|
|
|
|
|
CryptocurencyKing
|
 |
September 11, 2020, 01:22:14 AM Merited by fillippone (2) |
|
Sure, that's practically so true and possible. Especially amongst people who participate in multiple bounty campagnes and with the public nature of the wallet address. Your wallet is just everywhere by that singular act of always publicizing your wallet address also as seen on some forum users profile. But then, that is not a bad thing at all as, it allows coins come in and not go out without due authorization.
Hence, dusting comes to play with the idea of accumulation which then pays the price. Having your identity in the wrong hands especially criminals as that could be such a bad thing when you've got something of worth. Play safe people, question yourself over any unexpected coin you get and apply caution.
|
|
|
|
|
fillippone (OP)
Legendary

 Offline Offline
Activity: 2156
Merit: 15504
Fully fledged Merit Cycler - Golden Feather 22-23


|
 |
September 11, 2020, 06:30:36 AM |
|
Sure, that's practically so true and possible. Especially amongst people who participate in multiple bounty campagnes and with the public nature of the wallet address. Your wallet is just everywhere by that singular act of always publicizing your wallet address also as seen on some forum users profile. But then, that is not a bad thing at all as, it allows coins come in and not go out without due authorization.
Hence, dusting comes to play with the idea of accumulation which then pays the price. Having your identity in the wrong hands especially criminals as that could be such a bad thing when you've got something of worth. Play safe people, question yourself over any unexpected coin you get and apply caution.
Agree. Safety is important: know your public addresses and track them: know where every stats comes from. Do not do stupid things with unknown coins, like consolidating with your own sats, using them in a payment, for example. |
.
.HUGE. | | | | | | █▀▀▀▀
█
█
█
█
█
█
█
█
█
█
█
█▄▄▄▄ | ▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀
.
CASINO & SPORTSBOOK
▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ | ▀▀▀▀█
█
█
█
█
█
█
█
█
█
█
█
▄▄▄▄█ | | |
|
|
|
Globb0
Legendary

 Offline Offline
Activity: 2674
Merit: 2053
Free spirit

|
 |
September 11, 2020, 07:25:51 AM
Last edit: September 11, 2020, 08:10:04 AM by Globb0 |
|
Any opinions here:
an unknown person has sent 547 Satoshis to our escrow address:
This transaction happened 2 days ago and just now someone sent again 547 Sats to our escrow address:
Free money, I need to join up to more public facing bitcoin competitions. If they are spreading marking transaction about, who cares. In fact dust the addresses! you can make a fake competition and a long list of your own addresses and wait for them to send you money. Just don't use your own address. An hope one doesn't land in your super secret wallet I guess. But hey, bitcoin is transparent and verifiable anyway whats the problem? |
|
|
|
|
nc50lc
Legendary

 Offline Offline
Activity: 2408
Merit: 5601
Self-proclaimed Genius

|
 |
September 11, 2020, 07:59:48 AM
Last edit: September 11, 2020, 08:16:36 AM by nc50lc Merited by 1miau (4), fillippone (2) |
|
My first impression was a dust attack but it makes no sense because our escrow address is public and contains funds anyway... -snip-Does anyone have an explanation?  The attacker might be using a software that follows those specific UTXO, not the addresses themselves nor their previous outputs. If he's sending more than once to some addresses, he might be trying to increase the transaction fee when the victim tries to consolidate or " spend-all" by adding additional inputs. Or just trolling/advertising a fork ( together with the previous reasons) since the first five addresses are proof-of-burn addresses with vague meaning. BTW, It doesn't end there, the change was spent by another 608 output transaction series ( until it's empty? I didn't checked until the last). And it wasn't even the start of that series of 20,000vB transactions, those transactions are somewhere in the middle so this must be a large scale dust attack. -edit-It pointed me to this page ( based from those first five addresses): https://memo.sv/topic/hmwydaYou can easily spot it, These are the first five addresses: 1Lets1xxxx1use1xxxxxxxxxxxy2EaMkJ
1fuLL1xxxx1power1xxxxxxxxxxzatvCK
1of1xxxxx1anonymity1xxxxxxxz9JzFN
1See1xxxx1memo1xxxxxxxxxxxxxBuhPF
1dot1xxxxx1sv1xxxxxxxxxxxxxwYqEEt
1topic1xxx1hmwyda1xxxxxxxxxvo8wMn
1xxxxxxxxxxxxxxxxxxxxxxxxxy1kmdGr And it looks like the trolling/attack is not not exclusive to Bitcoin's chain.
But hey, bitcoin is transparent and verifiable anyway whats the problem?
But others wont be able to tell which ones belong to an ID/person unless for example: he publicly displays that address or used to withdraw/deposit from/to an Exchange or service with KYC. That what these kind of attacks are uncovering: linking a public/identified address(es) to another or to undisclosed ones. |
|
|
|
btcduster
Jr. Member

 Offline Offline
Activity: 46
Merit: 66
#WeAreAllHodlonaut


|
 |
September 11, 2020, 08:26:46 AM |
|
This is a very interesting read. I've heard of these attacks before, but I never understood how a person could be threatened. - Extremizing: an exchange that offers you $ 30 to register, after KYC, is practically performing a dust attack. Except that in that case, using the chain analysis company you just bought, you can perform a very efficient tracking of your UTXOs. Do you think this is an impossible scenario? it already happened.
it already happened. Do you have any references for this information? It would be interesting to read a little about this IRL attack. Looking at it, this is a threat only to people who have a lot of accumulated coins. Another scenario, If I am attacked this way, and then I decide to buy something with these satoshis, and if the buyer eventually puts the coins in their savings address, no one can prove that these coins are mine. N.B. Quoting a part of a list is awful. |
Learning about Bitcoin.
|
|
|
fillippone (OP)
Legendary

 Offline Offline
Activity: 2156
Merit: 15504
Fully fledged Merit Cycler - Golden Feather 22-23


|
 |
September 11, 2020, 10:40:13 AM |
|
This is a very interesting read. I've heard of these attacks before, but I never understood how a person could be threatened. - Extremizing: an exchange that offers you $ 30 to register, after KYC, is practically performing a dust attack. Except that in that case, using the chain analysis company you just bought, you can perform a very efficient tracking of your UTXOs. Do you think this is an impossible scenario? it already happened.
it already happened. Do you have any references for this information? It would be interesting to read a little about this IRL attack. Looking at it, this is a threat only to people who have a lot of accumulated coins. I was referring to Coinbase. Coinbase offered Wlecome Bonus to make sure you wanted to grab 30$ worth of Bitcoin, and do stupid things with those. They also had the EARN proram, where they give you some obscure shitcoin for watching a few videos and then hope, again, you do stupid things with those coins. Just remember: Coinbase the most anti-Bitcoin organisation. Make #DeleteCoinbase great again |
.
.HUGE. | | | | | | █▀▀▀▀
█
█
█
█
█
█
█
█
█
█
█
█▄▄▄▄ | ▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀
.
CASINO & SPORTSBOOK
▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ | ▀▀▀▀█
█
█
█
█
█
█
█
█
█
█
█
▄▄▄▄█ | | |
|
|
|
1miau
Legendary

 Offline Offline
Activity: 2142
Merit: 6791
Currently not much available - see my websitelink


|
 |
September 12, 2020, 01:22:02 AM |
|
In fact dust the addresses! you can make a fake competition and a long list of your own addresses and wait for them to send you money.
Yes, but 547 Sats are not much. At least right now. 
The attacker might be using a software that follows those specific UTXO, not the addresses themselves nor their previous outputs.
If he's sending more than once to some addresses, he might be trying to increase the transaction fee when the victim tries to consolidate or "spend-all" by adding additional inputs.
Important point. Since our escrow isn't using SegWit here, that might get a bigger issue.  We'll watch it carefully. |
|
|
|
nc50lc
Legendary

 Offline Offline
Activity: 2408
Merit: 5601
Self-proclaimed Genius

|
Important point. Since our escrow isn't using SegWit here, that might get a bigger issue.  We'll watch it carefully. Since there were already two dust UTXOs, you can now send them to a black-hole/dust-donation address using " coin-control" to get rid of them. As long as the transaction doesn't reach 547B or above with 1sat/B fee rate, it will be valid with 547sat output. Or use coin control when sending the price money. Electrum has a useful " freeze coin/address" feature that will make this easy, as well as coin-control. |
|
|
|
Hueristic
Legendary

 Offline Offline
Activity: 3808
Merit: 4906
Doomed to see the future and unable to prevent it

|
 |
September 12, 2020, 04:11:11 AM |
|
Pretty scary for Cryptocurrency enthusiast when they want privacy and scumbags dox this people, pretty crazy in regards to things that they do not get anything from it. Doxing is pretty scary especially if you are a private person.
SHUM |
“Bad men need nothing more to compass their ends, than that good men should look on and do nothing.”
|
|
|
Globb0
Legendary

 Offline Offline
Activity: 2674
Merit: 2053
Free spirit

|
 |
September 12, 2020, 08:32:58 AM |
|
In fact dust the addresses! you can make a fake competition and a long list of your own addresses and wait for them to send you money.
Yes, but 547 Sats are not much. At least right now.  but if your fake "potential criminals list" competition in a suspicious area of the net contained a thousand addresses That's over 5 bitcoin right? Reading this thread, I expect they do it to targeted and then associated addresses. But hey if they are lifting things from the forum, as in the football pool example? it might work. (I suppose there was a google docs? as there usualy is? with all the addresses? maybe another place they are targeting |
|
|
|
|
1miau
Legendary

 Offline Offline
Activity: 2142
Merit: 6791
Currently not much available - see my websitelink


|
Important point. Since our escrow isn't using SegWit here, that might get a bigger issue.  We'll watch it carefully. Since there were already two dust UTXOs, you can now send them to a black-hole/dust-donation address using " coin-control" to get rid of them. As long as the transaction doesn't reach 547B or above with 1sat/B fee rate, it will be valid with 547sat output. Or use coin control when sending the price money. Electrum has a useful " freeze coin/address" feature that will make this easy, as well as coin-control. Ok, I will suggest this as a solution. Many thanks for your help!
In fact dust the addresses! you can make a fake competition and a long list of your own addresses and wait for them to send you money.
Yes, but 547 Sats are not much. At least right now.  but if your fake "potential criminals list" competition in a suspicious area of the net contained a thousand addresses That's over 5 bitcoin right? 5 BTC? That would be nice but I think it's 1000 x 0.00000547 = 0.00547 BTC ? Or how did you calculate 5 BTC? 
Reading this thread, I expect they do it to targeted and then associated addresses. But hey if they are lifting things from the forum, as in the football pool example? it might work. (I suppose there was a google docs? as there usualy is? with all the addresses? maybe another place they are targeting
It is an escrow address from willi9974 who is escrowing our funds. I don't know where he has used this address additionally.  |
|
|
|
fillippone (OP)
Legendary

 Offline Offline
Activity: 2156
Merit: 15504
Fully fledged Merit Cycler - Golden Feather 22-23


|
 |
September 13, 2020, 11:54:10 AM |
|
Important point. Since our escrow isn't using SegWit here, that might get a bigger issue.  We'll watch it carefully. Since there were already two dust UTXOs, you can now send them to a black-hole/dust-donation address using " coin-control" to get rid of them. As long as the transaction doesn't reach 547B or above with 1sat/B fee rate, it will be valid with 547sat output. Or use coin control when sending the price money. Electrum has a useful " freeze coin/address" feature that will make this easy, as well as coin-control. Ok, I will suggest this as a solution. Many thanks for your help! Coin control is the key, when dealing with dust attack. I thought I made clear in the OP, but apparently it didn’t catch your attention. I will edit OP to detail exactly how to do this in at least a couple of Wallet (Electrum and Wasabi, just to start). |
.
.HUGE. | | | | | | █▀▀▀▀
█
█
█
█
█
█
█
█
█
█
█
█▄▄▄▄ | ▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀
.
CASINO & SPORTSBOOK
▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ | ▀▀▀▀█
█
█
█
█
█
█
█
█
█
█
█
▄▄▄▄█ | | |
|
|
|
fillippone (OP)
Legendary

 Offline Offline
Activity: 2156
Merit: 15504
Fully fledged Merit Cycler - Golden Feather 22-23


|
In order to make the things more clear, I will detail how to mark some address as freezed so that the dusted coins do not mark other clean coins: There are two separate possible case: - If a dust attack hits an empty address, you can actually damage your privacy, if you are not aware of this attack. If you spend from that address, you are probably going to use the dusted UTXO with your other UTXO's, effectively linking a "past" address of yours with your current transaction. This is very dangerous.
- If a dust attack hits an address with a positive balance it is no major damage, I think: the dust comes together in the address with some other UTXO's, so it would have been trivial to follow those coins without the dust in the first place. Dust acts as a not-so-cheap marker of your public UTXO's. You know you are being tracked anyway on the blockchain, so you act consciously.
The action to be taken are then different: - If the dusted address is empty: "Freeze address", this will prevent using the address in any future operation in the wallet
- If the dusted address is not empty: "Freeze Coin", this will freeze only the dusted UTXO (you can think as UTXO and Coins as synonymous, while the address will be able to spend the UTXO as usual.
ELECTRUM I will show you the coin Control feature in Electrum, one of the most used wallet to offer such a feature. If you are using another wallet and you get dusted, my suggestion is to import your wallet in Electrum and do the following steps. To avoid privacy concerns I created a test wallet, dusted it and censored some relevant information. This is the dusted Wallet. 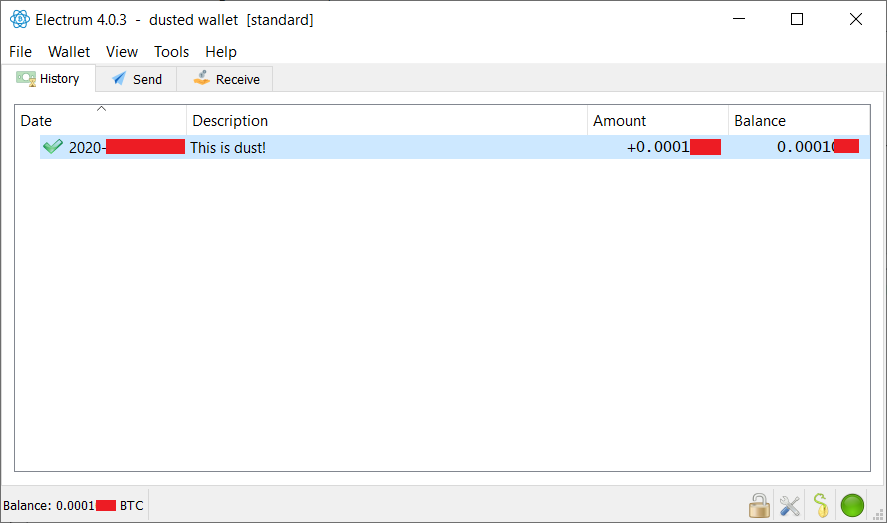 I am assuming the dust hits an empty address, maybe one I used in the past and is now empty after a spend.
Freeze AddressSince the address is empty, and the only associated UTXO is dusted, I decide to block the whole address. This will make this address unable to spend any coin. 1.Make Electrum show all your Addresses.Click on "View" menù, select "Show Addresses"  2. Locate the address where you received the dust. 2. Locate the address where you received the dust. You might want to label it. In this case it is easy, as it is the only one address with a positive balance. In your case you might have many positive addresses. 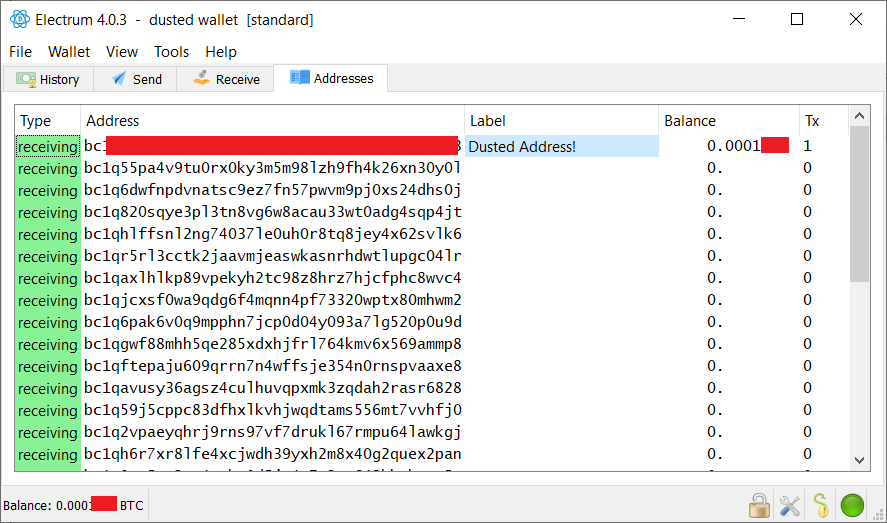 3. Freeze the dusted address. 3. Freeze the dusted address.
Right Click on the dusted address, select "Freeze" 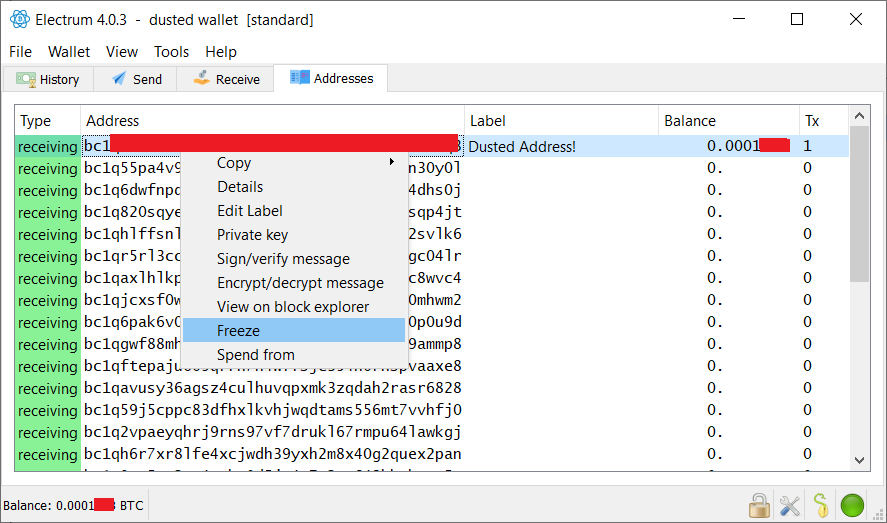 4. The Address is now Freezed. 4. The Address is now Freezed.The address is highlighted in dark Blue 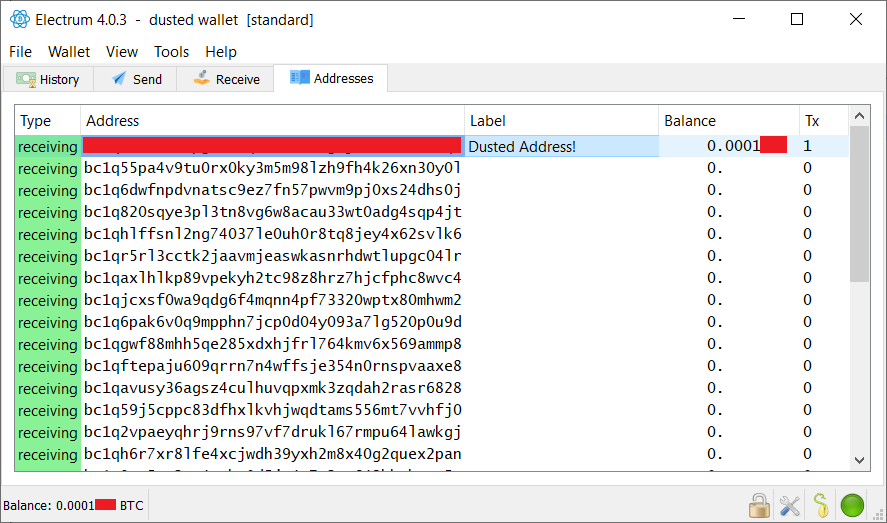 From now on, all the UTXO pertaining that address won't be used until the address is Freezed. Those UTXO won't mix with other "clean" UTXO then, defending us from the Dusting Attack.
Freeze CoinIn case you receive the dust on an address with some other coins, you might not lose such coins. Then you can freeze the dust UTXO only. 1.Make Electrum show all your Coins.Click on "View" menù, select "Show Coins"  2. Locate the UTXO that are the Dust. 2. Locate the UTXO that are the Dust. You might want to label it. In this case it is easy, as it is the only one UTXO. In your case you might have many UTXO's. 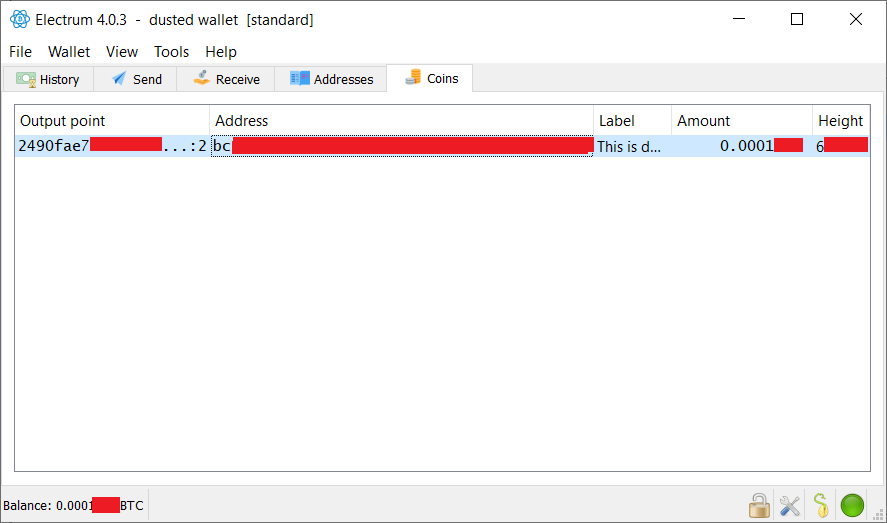 3. Freeze the Coins. 3. Freeze the Coins.
Right Click on the dusted address, select "Freeze" 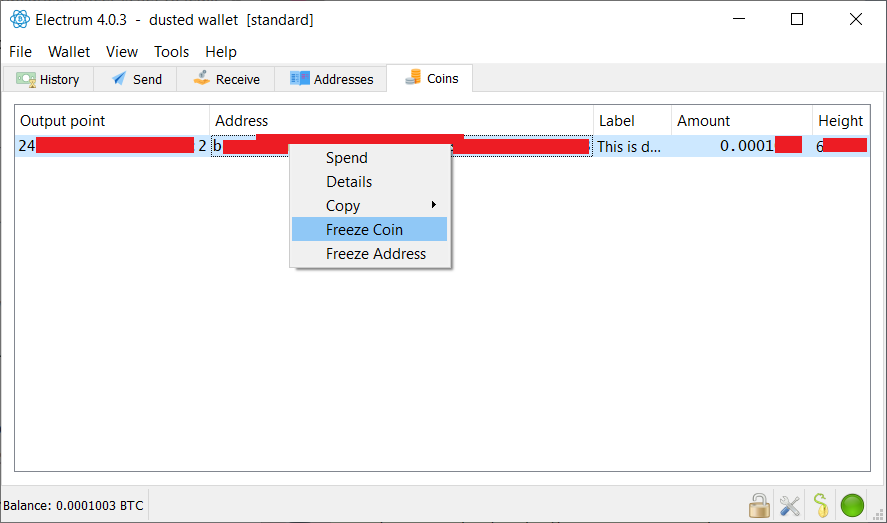 4. The Coin is now Freezed. 4. The Coin is now Freezed.The coin is highlighted in dark Blue, and won't be spent in future transactions. 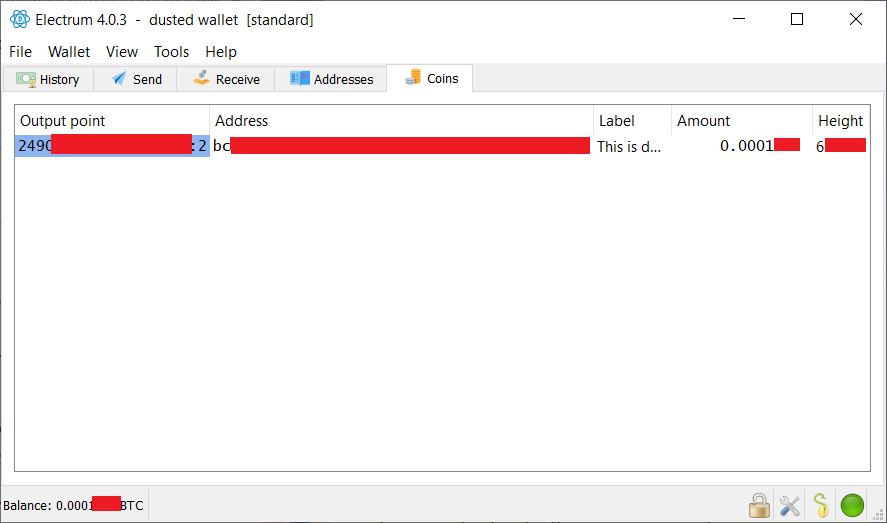 |
.
.HUGE. | | | | | | █▀▀▀▀
█
█
█
█
█
█
█
█
█
█
█
█▄▄▄▄ | ▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀
.
CASINO & SPORTSBOOK
▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ | ▀▀▀▀█
█
█
█
█
█
█
█
█
█
█
█
▄▄▄▄█ | | |
|
|
|
|
OcTradism
|
 |
October 13, 2020, 01:03:20 PM Merited by fillippone (2) |
|
I use Electrum wallet but I did not pay my attention on Freeze option. I did not know Freeze is used to avoid Dust Attack. Beyond Dust Attack, any other use cases for the Freeze option in Electrum wallet, can you share more? I feel worry what will happen after use Freeze and with search my fear is cleaned away. Frozen address can be unfrozen and it is simple to do. If misclick to Freeze one address, people can do backward Unfreeze that address later. Frozen coins: In the same vein as frozen addresses you can also freeze individual unspent outputs which are also known as utxos or coins in the jargon. Frozen utxos show up with a coloured background on the coins tab. If the coins tab is not visible go to view menu > show coins to make it appear. To unfreeze a specific utxo just right click it and choose to unfreeze from the context menu that appears.
https://bitcoinelectrum.com/frequently-asked-questions/ |
| | | .
.Duelbits. | | | █▀▀▀▀▀
█
█
█
█
█
█
█
█
█
█
█
█▄▄▄▄▄ | TRY OUR
NEW UNIQUE
GAMES! | | .
..DICE... | ███████████████████████████████
███▀▀ ▀▀███
███ ▄▄▄▄ ▄▄▄▄ ███
███ ██████ ██████ ███
███ ▀████▀ ▀████▀ ███
███ ███
███ ███
███ ███
███ ▄████▄ ▄████▄ ███
███ ██████ ██████ ███
███ ▀▀▀▀ ▀▀▀▀ ███
███▄▄ ▄▄███
███████████████████████████████ | .
.MINES. | ███████████████████████████████
████████████████████████▄▀▄████
██████████████▀▄▄▄▀█████▄▀▄████
████████████▀ █████▄▀████ █████
██████████ █████▄▀▀▄██████
███████▀ ▀████████████
█████▀ ▀██████████
█████ ██████████
████▌ ▐█████████
█████ ██████████
██████▄ ▄███████████
████████▄▄ ▄▄█████████████
███████████████████████████████ | .
.PLINKO. | ███████████████████████████████
█████████▀▀▀ ▀▀▀█████████
██████▀ ▄▄███ ███ ▀██████
█████ ▄▀▀ █████
████ ▀ ████
███ ███
███ ███
███ ███
████ ████
█████ █████
██████▄ ▄██████
█████████▄▄▄ ▄▄▄█████████
███████████████████████████████ | 10,000x
MULTIPLIER | │ | NEARLY UP TO
.50%. REWARDS | | | ▀▀▀▀▀█
█
█
█
█
█
█
█
█
█
█
█
▄▄▄▄▄█ |
|
|
|
nc50lc
Legendary

 Offline Offline
Activity: 2408
Merit: 5601
Self-proclaimed Genius

|
 |
October 14, 2020, 02:27:29 AM |
|
I use Electrum wallet but I did not pay my attention on Freeze option. I did not know Freeze is used to avoid Dust Attack. Beyond Dust Attack, any other use cases for the Freeze option in Electrum wallet, can you share more?
-snip-
It's also for " coin control" when there're more inputs to spend than the to-be-excluded. It's easier to freeze the unwanted UTXO(s) ( coins tab) than selecting multiple inputs, specially when there are hundreds of them. I feel worry what will happen after use Freeze and with search my fear is cleaned away. Frozen address can be unfrozen and it is simple to do. If misclick to Freeze one address, people can do backward Unfreeze that address later. Frozen coins: In the same vein as frozen addresses you can also freeze individual unspent outputs which are also known as utxos or coins in the jargon. Frozen utxos show up with a coloured background on the coins tab. If the coins tab is not visible go to view menu > show coins to make it appear. To unfreeze a specific utxo just right click it and choose to unfreeze from the context menu that appears.
That's because it's a local wallet feature that won't affect the blockchain. All it does is exclude those frozen addresses/coins whenever the wallet needs to automatically select inputs for your transactions. BTW, that quoted message ( freeze in the coins tab) is better than freezing addresses when it comes with " Dust Attacks" since the usual targets are those frequently used, have been reusing and publicly displayed addresses. If the user has frozen that address, he wont be able to spend his legitimate balance that was received through it. |
|
|
|
fillippone (OP)
Legendary

 Offline Offline
Activity: 2156
Merit: 15504
Fully fledged Merit Cycler - Golden Feather 22-23


|
 |
October 14, 2020, 07:45:30 AM
Last edit: October 14, 2020, 09:08:30 AM by fillippone |
|
<....>
BTW, that quoted message (freeze in the coins tab) is better than freezing addresses when it comes with "Dust Attacks"
since the usual targets are those frequently used, have been reusing and publicly displayed addresses.
If the user has frozen that address, he wont be able to spend his legitimate balance that was received through it.
I had a thought about choosing if freezing coins (UTXO) or address. I chose to show the "freeze address" methodology because I supposed the dust attack would affect empty addresses. If a dust attack hits an address with a positive balance it is no major damage, I think: the dust comes together in the address with some other UTXO's, so it would have been trivial to follow those coins without the dust in the first place. Dust acts as a not-so-cheap marker of your public UTXO's. You know you are bein tracked anyway on the blockchain, so you act consciously. If a dust attack hits an empty address, you can actually damage your privacy, if you are not aware of this attack. If you spend from that address, you are probably going to use the dusted UTXO with your other UTXO's, effectively linking a "past" address of yours with your current transaction. This is very dangerous. This is why I chose to select the "freeze address" procedure: I want to freeze dust on "empty" addresses only, because I think dust in addresses with UTXO's is not so dangerous, after all. Please let me know if you dissent from this, so I can elaborate more in the guide. EDIT: I completely forgot about that message of yours here: <...>
The attacker might be using a software that follows those specific UTXO, not the addresses themselves nor their previous outputs.
If he's sending more than once to some addresses, he might be trying to increase the transaction fee when the victim tries to consolidate or "spend-all" by adding additional inputs.
Or just trolling/advertising a fork (together with the previous reasons) since the first five addresses are proof-of-burn addresses with vague meaning.
Yes, it could be the case, but it looks highly un effective tactic. I really don get it why an user should do that. If I had received those transactions, the last thing I would have done would have been, if I ever had realised the presence of such an "hidden message", it would have been to go and check that website. If the objective would have been a "spam attack" to increase the network fees, well there would have been other, more efficient ways to do so. |
.
.HUGE. | | | | | | █▀▀▀▀
█
█
█
█
█
█
█
█
█
█
█
█▄▄▄▄ | ▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀
.
CASINO & SPORTSBOOK
▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ | ▀▀▀▀█
█
█
█
█
█
█
█
█
█
█
█
▄▄▄▄█ | | |
|
|
|
Karartma1
Legendary

 Offline Offline
Activity: 2310
Merit: 1422

|
 |
October 14, 2020, 08:12:03 AM Merited by vapourminer (1) |
|
Why don't you consider UTXO's with dust txs dangerous?
I am lucky enough to have had only one previous UTXO with quite a large amount under a spam/dust attack. When I saw that I marked that specific dust UTXO as do not spend.
Ok, we can't avoid being tagged by dust as we speak but I'd rather prefer freezing them as soon as I realize it.
Better to take one hit and leave a scar, than to fight the battle and possibly losing a war in the long run. Put it differently, to me tagging received dust is like eliminating damage sources which are not under my control (who knows one day that leaving the dust behind can completely nullify my opsec?).
|
|
|
|
|
nc50lc
Legendary

 Offline Offline
Activity: 2408
Merit: 5601
Self-proclaimed Genius

|
-snip-
-snip-This is why I chose to select the "freeze address" procedure: I want to freeze dust on "empty" addresses only, because I think dust in addresses with UTXO's is not so dangerous, after all. Please let me know if you dissent from this, so I can elaborate more in the guide. That's reasonable for used empty addresses, users shouldn't be reusing addresses anyways. But it's best not to include those dust from loaded addresses to avoid unnecessary additional fee and cut the link from the source in case they came from illicit sources. Perhaps you should add some use-cases like if you've received dust to an empty used address, freeze that address; if with unspent outputs, freeze the coin. Because it depends on the situation whether it's best to freeze coins or addresses. |
|
|
|
fillippone (OP)
Legendary

 Offline Offline
Activity: 2156
Merit: 15504
Fully fledged Merit Cycler - Golden Feather 22-23


|
 |
October 14, 2020, 02:19:09 PM |
|
<...>
Perhaps you should add some use-cases like if you've received dust to an empty used address, freeze that address; if with unspent outputs, freeze the coin.
Because it depends on the situation whether it's best to freeze coins or addresses.
Thanks for the suggestion, I have just done that. Hope you like the guide! Any other idea is more than welcome. |
.
.HUGE. | | | | | | █▀▀▀▀
█
█
█
█
█
█
█
█
█
█
█
█▄▄▄▄ | ▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀
.
CASINO & SPORTSBOOK
▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ | ▀▀▀▀█
█
█
█
█
█
█
█
█
█
█
█
▄▄▄▄█ | | |
|
|
|
OgNasty
Donator
Legendary

 Offline Offline
Activity: 4732
Merit: 4253
Leading Crypto Sports Betting & Casino Platform


|
 |
October 15, 2020, 12:00:10 PM |
|
In short... Learn to manage your coins and ignore dust. Getting dusted in itself is no reason for fear. Not understanding how to properly manage your coins is the danger, and that is something that can lead to loss of privacy whether you’ve been dusted or not.
|
| ..Stake.com.. | | | ▄████████████████████████████████████▄
██ ▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄▄▄▄ ██ ▄████▄
██ ▀▀▀▀▀▀▀▀▀▀ ██████████ ▀▀▀▀▀▀▀▀▀▀ ██ ██████
██ ██████████ ██ ██ ██████████ ██ ▀██▀
██ ██ ██ ██████ ██ ██ ██ ██ ██
██ ██████ ██ █████ ███ ██████ ██ ████▄ ██
██ █████ ███ ████ ████ █████ ███ ████████
██ ████ ████ ██████████ ████ ████ ████▀
██ ██████████ ▄▄▄▄▄▄▄▄▄▄ ██████████ ██
██ ▀▀▀▀▀▀▀▀▀▀ ██
▀█████████▀ ▄████████████▄ ▀█████████▀
▄▄▄▄▄▄▄▄▄▄▄▄███ ██ ██ ███▄▄▄▄▄▄▄▄▄▄▄▄
██████████████████████████████████████████ | | | | | | ▄▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▄
█ ▄▀▄ █▀▀█▀▄▄
█ █▀█ █ ▐ ▐▌
█ ▄██▄ █ ▌ █
█ ▄██████▄ █ ▌ ▐▌
█ ██████████ █ ▐ █
█ ▐██████████▌ █ ▐ ▐▌
█ ▀▀██████▀▀ █ ▌ █
█ ▄▄▄██▄▄▄ █ ▌▐▌
█ █▐ █
█ █▐▐▌
█ █▐█
▀▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▀█ | | | | | | ▄▄█████████▄▄
▄██▀▀▀▀█████▀▀▀▀██▄
▄█▀ ▐█▌ ▀█▄
██ ▐█▌ ██
████▄ ▄█████▄ ▄████
████████▄███████████▄████████
███▀ █████████████ ▀███
██ ███████████ ██
▀█▄ █████████ ▄█▀
▀█▄ ▄██▀▀▀▀▀▀▀██▄ ▄▄▄█▀
▀███████ ███████▀
▀█████▄ ▄█████▀
▀▀▀███▄▄▄███▀▀▀ | | | ..PLAY NOW.. |
|
|
|
hatshepsut93
Legendary

 Offline Offline
Activity: 2968
Merit: 2147

|
 |
December 30, 2020, 03:26:34 PM Merited by fillippone (2) |
|
Here's a real world example of dust attack - in late 2019 someone sent 937 satoshis each to multiple addresses. I didn't check the rest, but one of them is mine - the address from my profile on this forum, which is also the address that I stacked in the thread in Meta. I think the purpose of this dust transaction is clear - someone hoped to link the address that I stacked with other addresses that I might own. I also noticed that some address that received 937 satoshis in that same transaction has sent these satoshis to the Bitcoin eater address. I'm not going to bother, I practice coin control in all my transactions anyway. |
|
|
|
fillippone (OP)
Legendary

 Offline Offline
Activity: 2156
Merit: 15504
Fully fledged Merit Cycler - Golden Feather 22-23


|
 |
December 31, 2020, 10:17:50 AM |
|
Here's a real world example of dust attack - in late 2019 someone sent 937 satoshis each to multiple addresses. I didn't check the rest, but one of them is mine - the address from my profile on this forum, which is also the address that I stacked in the thread in Meta. I think the purpose of this dust transaction is clear - someone hoped to link the address that I stacked with other addresses that I might own. I also noticed that some address that received 937 satoshis in that same transaction has sent these satoshis to the Bitcoin eater address. I'm not going to bother, I practice coin control in all my transactions anyway. And you did the right thing: I see many of those sats have been spent. I would like to think they were sent to a coinjoin, but I instead am afraid they for spent together with other UTXO they shouldn't have mixed with. Nice reference in the OP_Return of the transaction: "Saints: I have seen a lot of deaths but when I come here the dying is different". Is he referring to the users' privacy? |
.
.HUGE. | | | | | | █▀▀▀▀
█
█
█
█
█
█
█
█
█
█
█
█▄▄▄▄ | ▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀
.
CASINO & SPORTSBOOK
▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ | ▀▀▀▀█
█
█
█
█
█
█
█
█
█
█
█
▄▄▄▄█ | | |
|
|
|
Globb0
Legendary

 Offline Offline
Activity: 2674
Merit: 2053
Free spirit

|
 |
December 31, 2020, 11:16:42 AM |
|
Nice reference in the OP_Return of the transaction: "Saints: I have seen a lot of deaths but when I come here the dying is different". Is he referring to the users' privacy?
It sounds quite heavy. I looked it up, def religious stuff. Maybe originates here? reused a few times http://dailyrosaryfamily.com/read-the-powerful-dying-words-of-these-six-saints/ |
|
|
|
|
fillippone (OP)
Legendary

 Offline Offline
Activity: 2156
Merit: 15504
Fully fledged Merit Cycler - Golden Feather 22-23


|
 |
December 31, 2020, 11:25:29 AM |
|
Yes, I found a similar reference for that same sentence, and also a different web address pointing to the same page! I don't know what the intentions of the dust senders were, but it adds a twist of mystery to me. Going further in the details of the transactions, @hatshepsut93 did you bother noting if other involved addresses were also stacked on the same thread? It was basically an attack targeted at bitcointalk users? Also, I found the bitcoin eater address you mentioned in the earlier post: 1BitcoinEaterAddressDontSendf59kuEAgree coin control is a far better alternative, as sending to a bitcoin address implies the owner of the address still monitors and has control of such addresses. Doing nothing you don't even give this information to the attacker. |
.
.HUGE. | | | | | | █▀▀▀▀
█
█
█
█
█
█
█
█
█
█
█
█▄▄▄▄ | ▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀
.
CASINO & SPORTSBOOK
▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ | ▀▀▀▀█
█
█
█
█
█
█
█
█
█
█
█
▄▄▄▄█ | | |
|
|
|
hatshepsut93
Legendary

 Offline Offline
Activity: 2968
Merit: 2147

|
 |
December 31, 2020, 02:26:05 PM Merited by fillippone (2) |
|
Going further in the details of the transactions, @hatshepsut93 did you bother noting if other involved addresses were also stacked on the same thread? It was basically an attack targeted at bitcointalk users?
Yes, I checked it, all the addresses are linked to this forum - stacked addresses, addresses in profiles, mentioned addresses. Also, seems like all the accounts are high-rank accounts, so they might have not been selected randomly. I wonder who is behind this - my guess would be some chainanalysis company, they are well known for going beyond simply looking at blockchain, they do things like runnings electrum servers and full nodes to collect IP addresses and other data. |
|
|
|
exstasie
Legendary

 Offline Offline
Activity: 1806
Merit: 1521

|
 |
January 01, 2021, 08:14:59 AM |
|
Here's a real world example of dust attack - in late 2019 someone sent 937 satoshis each to multiple addresses. I didn't check the rest, but one of them is mine - the address from my profile on this forum, which is also the address that I stacked in the thread in Meta. I think the purpose of this dust transaction is clear - someone hoped to link the address that I stacked with other addresses that I might own. Someone included me in a dust attack last year too. My address was linked to this forum so I assumed it was an attack on Bitcointalk users, but I couldn't find any common links just from Googling a few random addresses. There were almost 3K outputs: https://blockstream.info/nojs/tx/3f807962c02583dbed82cd8787668f049daa71ba88147544f57486b3d24bc400I also noticed that some address that received 937 satoshis in that same transaction has sent these satoshis to the Bitcoin eater address. I'm not going to bother, I practice coin control in all my transactions anyway.
Same, but after I noticed this attack last year I started freezing all used addresses (in Electrum) as an additional check against accidental spending. |
|
|
|
odolvlobo
Legendary

 Offline Offline
Activity: 4312
Merit: 3214

|
 |
January 07, 2021, 10:46:10 AM Merited by fillippone (2) |
|
Here is a guide showing how to dump the dust if you use Electrum: https://gist.github.com/ncstdc/90fe6209a0b3ae815a6eaa2aef53524c |
Join an anti-signature campaign: Click ignore on the members of signature campaigns.
PGP Fingerprint: 6B6BC26599EC24EF7E29A405EAF050539D0B2925 Signing address: 13GAVJo8YaAuenj6keiEykwxWUZ7jMoSLt
|
|
|
fillippone (OP)
Legendary

 Offline Offline
Activity: 2156
Merit: 15504
Fully fledged Merit Cycler - Golden Feather 22-23


|
 |
January 07, 2021, 12:31:52 PM
Last edit: January 07, 2021, 10:43:54 PM by fillippone |
|
Thanks for the guide. However, I don't get how it is different from sending the dust to 1BitcoinEaterAddressDontSendf59kuE setting maximum fees. Of course, a 1 sat/byte fee on a legacy transaction is 192, so this is not viable for lower amounts, but still... In addition to that, spending that dust confirms to the attacker you still in control of the dusted address(es). Jut be aware of this. |
.
.HUGE. | | | | | | █▀▀▀▀
█
█
█
█
█
█
█
█
█
█
█
█▄▄▄▄ | ▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀
.
CASINO & SPORTSBOOK
▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ | ▀▀▀▀█
█
█
█
█
█
█
█
█
█
█
█
▄▄▄▄█ | | |
|
|
|
odolvlobo
Legendary

 Offline Offline
Activity: 4312
Merit: 3214

|
 |
January 08, 2021, 12:52:55 AM Merited by fillippone (2) |
|
Thanks for the guide. However, I don't get how it is different from sending the dust to 1BitcoinEaterAddressDontSendf59kuE setting maximum fees. Of course, a 1 sat/byte fee on a legacy transaction is 192, so this is not viable for lower amounts, but still... In addition to that, spending that dust confirms to the attacker you still in control of the dusted address(es). Jut be aware of this. The difference is the OP_RETURN prevents the transaction from being kept in the UTXO set forever. Though I guess if you can get the output amount to exactly 0, it might have the same effect. |
Join an anti-signature campaign: Click ignore on the members of signature campaigns.
PGP Fingerprint: 6B6BC26599EC24EF7E29A405EAF050539D0B2925 Signing address: 13GAVJo8YaAuenj6keiEykwxWUZ7jMoSLt
|
|
|
fillippone (OP)
Legendary

 Offline Offline
Activity: 2156
Merit: 15504
Fully fledged Merit Cycler - Golden Feather 22-23


|
 |
March 14, 2021, 12:35:23 PM
Last edit: January 17, 2023, 12:55:16 AM by fillippone Merited by JayJuanGee (1) |
|
A very well written blog post by Jameson Lopp on Dust attacks and a few misconceptions. A History of Bitcoin Transaction Dust & Spam Storms A well known feature of Bitcoin is that if you want to send money, no one can stop you from creating a valid transaction and broadcasting it onto the network. The flip side of this feature is that you can't stop anyone from sending money to you.
You may be wondering "why wouldn't I want someone to send me money?" Due to the scarcity of block space and fees related to this scarcity it can actually become an economic burden that costs more to spend than the value you received; naturally this is quite annoying to manage.
Recommend read, even if he seems to downplay the dust risk a little bit. |
.
.HUGE. | | | | | | █▀▀▀▀
█
█
█
█
█
█
█
█
█
█
█
█▄▄▄▄ | ▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀
.
CASINO & SPORTSBOOK
▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ | ▀▀▀▀█
█
█
█
█
█
█
█
█
█
█
█
▄▄▄▄█ | | |
|
|
|
|
nullius
|
I clicked on this thread so that I could post that. :-)Absent better evidence, I suspect that dust attacks are probably an urban legend (except in case of high-value targets). Blockchain spam is a real problem; and it used to be worse when transactions were cheaper. However, I doubt that blockchain spies are blasting out free money to significant numbers of people. It just doesn’t make sense. The cost is high, and the gain for them is low when blockchain privacy is already so bad.
Thanks for the guide. However, I don't get how it is different from sending the dust to 1BitcoinEaterAddressDontSendf59kuE setting maximum fees. Of course, a 1 sat/byte fee on a legacy transaction is 192, so this is not viable for lower amounts, but still... In addition to that, spending that dust confirms to the attacker you still in control of the dusted address(es). Jut be aware of this. The difference is the OP_RETURN prevents the transaction from being kept in the UTXO set forever. Though I guess if you can get the output amount to exactly 0, it might have the same effect. Yes. Thank you. If you want to destroy bitcoins, please use OP_RETURN instead of a burn address! The use of burn addresses permanently spams the UTXO set, forever imposing a burden on every full node (including pruned nodes!). It is harmful and irresponsible. Burn addresses should never be used for any reason. However, the linked gist is wrong. Why does it spam the blockchain with 32 bytes of random data in the OP_RETURN? That smells like cargo-culting from an application that uses a 32-byte push. An OP_RETURN (0x6a) can be followed by a push of 1–40 bytes. (I just tried some other opcodes to cut it below a 1-byte push, and Core’s decoderawtransaction barfed.) OP_RETURN spam is not nearly as bad as UTXO set spam; but putting random data in OP_RETURNs for no reason is spam, and it is bad for Bitcoin. Don’t do it! OP_RETURN should only be used for data that you really want to force every non-pruned node in the world to store on disk forever— e.g., for OpenTimestamps, or as seen in the puzzle with magical txid 000000000fdf0c619cd8e0d512c7e2c0da5a5808e60f12f1e0d01522d2986a51. (I should scan to see if that’s the first cat emoji ever embedded in the blockchain.) OP_RETURN has another use: The amount placed in an OP_RETURN output is irrevocably destroyed, thus permanently reducing Bitcoin’s monetary supply. That is a consensus rule: The coins no longer exist (unlike coins at burn addresses, which still exist). The script in the gist isn’t doing that. It is a completely wrong use of OP_RETURN. The gist’s author evidently does not know the purpose of OP_RETURN. The script is not using either of its functions (storing useful data, and/or destroying coins). If your objective is to donate a spam coin to miners, then... <snip>
I started here to write a helpful explanation of how better to do this, with a script for getting it done. I wanted to demonstrate on testnet, and link to that on a testnet explorer. I have some testnet coins; but I use them for things that I don’t want blockchain analysts to link to nullius. Of course, that is also a concern on testnet! And the testnet faucet situation is fouled up. It seems that due to abuse, testnet faucets are requiring Javascript and CAPTCHAs; and some are blocking Tor. I rarely do Javascript, and I never do CAPTCHAs nowadays. I am sure as heck not dealing with that to obtain some worthless test coins so that I can provide free advice on a forum! If someone would please be so kind as to send testnet dust to tb1qywy48q0yfj8pjffrav39fvwkmm0kpcj6ntmgqw, then I will show how to get rid of it. N.b. that the same privacy concerns may apply to you. Transparent blockchains are a problem. :-(Thanks. |
|
|
|
Quickseller
Copper Member
Legendary

 Offline Offline
Activity: 2870
Merit: 2301

|
 |
March 26, 2021, 07:45:54 PM |
|
I would not necessarily do that. The dust from these transactions may someday have real value. If you want to destroy bitcoins, please use OP_RETURN instead of a burn address! The use of burn addresses permanently spams the UTXO set, forever imposing a burden on every full node (including pruned nodes!). It is harmful and irresponsible. Burn addresses should never be used for any reason. However, the linked gist is wrong. Why does it spam the blockchain with 32 bytes of random data in the OP_RETURN? That smells like cargo-culting from an application that uses a 32-byte push. An OP_RETURN (0x6a) can be followed by a push of 1–40 bytes. (I just tried some other opcodes to cut it below a 1-byte push, and Core’s decoderawtransaction barfed.) I suspect the rational behind this is to prevent two of your transactions being linked together. If you send 10 transactions with the same 1 byte of data, whoever is behind the dust attack might be able to conclude those 10 transactions were made by the same person, after reviewing other "crumbs" that you have left in your other transactions. |
|
|
|
|
fillippone (OP)
Legendary

 Offline Offline
Activity: 2156
Merit: 15504
Fully fledged Merit Cycler - Golden Feather 22-23


|
 |
January 17, 2023, 12:48:18 AM
Last edit: May 15, 2023, 10:47:49 AM by fillippone |
|
My Fellow friend xhomerx10 noticed I fell for a dust attack: While doing a tiny bit of wallet maintenance today I discovered something strange I did a little digging and some searching and I found that disgraced user naim027 had a short stint running a lending service; the repayment address was: 18HfvLNNsZdMZeXmyKg59AfG7n4d1ibKRU (as posted here) which on 9/14/2022 @ 12:24:14 transferred a small amount of bitcoin to this address: bc1qw0qsvzuxgmyqvc6mcaqw77v3sd9jt0lppcxkn6 which on 9/23/2022 @ 24:14:25 transferred most of that amount to this adress: bc1qy4ta9wtwufm3d56tqrys3wh50q7fmd7p0g0z6n which on 9/23/2022 @ 24:28:50 dispersed ~0.00005 BTC to each of the following users at their publicly posted addresses - fillippone: bc1qd7rqlrw5h4q3g2x45xacd72zshcm2dht2ztclh
Chartbuddy: 1CBuddyxy4FerT3hzMmi1Jz48ESzRw1ZzZ
Gachapin: 1L1KknC9sGqr6CUuZzEME3V8YPSfLqLRoM
Ivonm: 38s6Ku7BMThahWcSQQLwnM9K1U5GWF5Rkk
JayJuanGee: 35EVP8EePt8dyvKHaB7bXaRmKLm22YgRCA
OutOfMemory: bc1qhy8gjn9klgmtlx08a2cpruq9dkv0tvqhv5x5lk
OgNasty: 168WXhArv7Fasqvi2xm5MQMfLhG18jifMe
Richy_T: 1RichyTrEwPYjZSeAYxeiFBNnKC9UjC5k
El duderino_: 19X5vZE8KGZ6YgtSkJmZEryDgX24tg6amR
xhomerx10: 1RoMaNiAjSGeGsYJzPjsLUGogbDEsK4TZ I'm not sure what naim027 is up to nor would I trust any answer from him but I did not request his dust. This dust can be used to track future transactions and potentially deanonymize you. It's probably a good idea to freeze the UTXO associated with this tx to make sure it never gets spent. Hopefully the rest of you either caught it already or have not yet transacted using that UTXO. At the times, I already noticed the transaction, labelled it, and froze the UTXO as unspendable.  Not that he could have don some major damage, as the address wasn't even empty. But better to be sure. |
.
.HUGE. | | | | | | █▀▀▀▀
█
█
█
█
█
█
█
█
█
█
█
█▄▄▄▄ | ▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀
.
CASINO & SPORTSBOOK
▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ | ▀▀▀▀█
█
█
█
█
█
█
█
█
█
█
█
▄▄▄▄█ | | |
|
|
|
|



