Timelord2067
Legendary

 Offline Offline
Activity: 3654
Merit: 2216
💲🏎️💨🚓

|
 |
October 13, 2020, 03:39:57 AM |
|
What are some of the wallet addresses that you have funds trapped in? Unless you're chasing the wind as others have suggested, there's no use searching for a way into a locked box unless you know there's something (other than a dead cat) inside... |
|
|
|
|
|
|
|
|
|
|
There are several different types of Bitcoin clients. The most secure are full nodes like Bitcoin Core, which will follow the rules of the network no matter what miners do. Even if every miner decided to create 1000 bitcoins per block, full nodes would stick to the rules and reject those blocks.
|
|
|
Advertised sites are not endorsed by the Bitcoin Forum. They may be unsafe, untrustworthy, or illegal in your jurisdiction.
|
bob123
Legendary

 Offline Offline
Activity: 1624
Merit: 2481


|
 |
October 13, 2020, 07:54:23 AM |
|
I am convinced that at the present stage of the development of computers, hacking a bitcoin wallet is an almost impracticable and difficult task.
It is impossible to bruteforce used private keys / seeds. But only if there is no flawed random number generator used and the implementation doesn't include any other vulnerability. Further, theft mostly doesn't occur through cracking/bruteforcing of seeds/private keys/brain wallets, but through bad user habits and compromised personal devices which itself is definitely possible and not as difficult as people may think. The largest vulnerability is the human sitting in front of the computer. And it is being successfully exploited to steal private data including private keys. |
|
|
|
BrewMaster
Legendary

 Offline Offline
Activity: 2114
Merit: 1292
There is trouble abrewing

|
 |
October 14, 2020, 04:15:52 PM |
|
It is impossible to bruteforce used private keys / seeds.
But only if there is no flawed random number generator used and the implementation doesn't include any other vulnerability.
that is only the case when there is a wallet and an actual private key in that wallet and a password that did really encrypt the whole thing. but all of these discussions (while true) become irrelevant when the wallet file is bought with the false promise of money inside. |
There is a FOMO brewing...
|
|
|
BASE16
Member
 
 Offline Offline
Activity: 180
Merit: 38

|
 |
October 15, 2020, 12:20:39 AM
Last edit: October 15, 2020, 12:31:42 AM by BASE16 |
|
It is impossible to bruteforce used private keys / seeds.
But only if there is no flawed random number generator used and the implementation doesn't include any other vulnerability.
Another member of the 'Impossible Squad' This is starting to get ridiculous now. I have to do something about this because all these lies might put people on the wrong track. It is very possible to bruteforce used private keys. In fact, I can prove you wrong in less then 10 seconds.Here is the used address you can look it up on the block explorer: 19ZewH8Kk1PDbSNdJ97FP4EiCjTRaZMZQA Here is the brute forced Private Key: http://www.youtube.com/watch?v=h5drF7wJgQgThis ends the discussion that it is impossible to brute force a used private key. I don't want to read or hear it anymore, it's not impossible, it is INEVITABLE.  |
|
|
|
|
HCP
Legendary

 Offline Offline
Activity: 2086
Merit: 4316
<insert witty quote here>

|
 |
October 15, 2020, 03:20:38 AM |
|
Not sure why you didn't just go with "1BgGZ9tcN4rm9KBzDn7KprQz87SZ26SAMH", you could have saved yourself 6 iterations and gone with key "1" instead of key "7"  You claim that it is "inevitable" and all it requires is "time". That's great... if you happen to have unlimited time. If you don't, then brute-forcing at least some of the search space is essentially "impossible" as you just don't have the "time" available to do it all before you either die, or earth gets hit by a planet-killer, or someone starts WW3 or the sun devours our solar system etc. The fact that some keys are able to be brute-forced, does not mean that all keys can be brute-forced. |
|
|
|
PrimeNumber7
Copper Member
Legendary

 Offline Offline
Activity: 1624
Merit: 1899
Amazon Prime Member #7

|
 |
October 15, 2020, 03:45:43 AM |
|
This will be possible if we use quantum computers, but this era has not yet arrived and no one knows when it will be. I think it's better to spend your time on something more useful in this life.  Even with quantum computer, you still need to obtain the bitcoin wallet file first. If someone is careless enough to get their bitcoin wallet file copied by someone else, it's likely that someone else could obtain the password/private key through another way such as using keylogger. Quantum computer is more likely to used against Bitcoin address where it's public key is known.My understanding is that Quantum technology will only be able to calculate the private keys from the public key. This means if you generate an address today, you will need to sign a message or transaction (and make either public) in order to expose your private key. |
|
|
|
|
BASE16
Member
 
 Offline Offline
Activity: 180
Merit: 38

|
 |
October 15, 2020, 08:52:29 AM |
|
The fact that some keys are able to be brute-forced, does not mean that all keys can be brute-forced.
So now we move from impossible to some keys can be brute forced. I must have started something because i can see some improvement in the claim. Let's step it up a notch. Here is the next step: If one key can be brute forced, then ALL keys can be brute forced. Your assumptions on how much time it will take according to the calculations including all known variables seems to be correct, but you have to calculate the time it will actually take in reality with all mod and methods applied. This is not possible if you do not know these methods yet, so it is understandable that you default to the known equations. Its a bad idea however, to present and defend them as facts. There are always the unknown methods, unknown factors and unknown parameters that when correctly applied, can smash your previous beliefs in an instant. A good example of this is the wright brothers vs all the people who claimed that a flying machine was impossible. We now have close to 10.000 airplanes in the sky at any given time. We also have the famous quote by Mark Twain, “They did not know it was impossible so they did it”. For example you could assume a 256 bits key strength, which takes n milliseconds to compute. But you have to realize that this only counts for YOU to get to YOUR public point. This is not so for an attacker, for an attacker ANY point will do. And the next point is not 256 Bits away. The next point is 1 Bit away. You can see that a private key has 255 intermediate public points that are normally just trashed inside of the calculation, but they are valid public points with valid addresses, for all you know you could have passed millions of BTC on some intermediate public point/address you landed on while on your way to bit 256 your own public point/address.... You will never know... Unless you deliberately looked for it.  |
|
|
|
|
AGD
Legendary

 Offline Offline
Activity: 2069
Merit: 1164
Keeper of the Private Key

|
 |
October 15, 2020, 09:30:06 AM |
|
I heard of an article about "hackers" trying to crack into a 70,000 BTC wallet, and was wondering if there's any tools out there on how to do it?
I already got a wallet that hasn't been used since 2017, and wanted to know if there are any good tutorials out there to successfully crack a wallet?
I do not know anything about the password of the wallet itself, and it is in the public domain (still has bitcoin on it), and I am aware that this isn't easy money, but it is worth a shot.
I decided to make a thread here because all the information that I've found is very vague on the subject.
If anyone has any suggestions or any help for me, go right ahead and reply to this thread, thanks.
Why don't you just dig holes somewhere in this world to find diamonds. At least it would be by far more possible to find one. |
|
|
|
|
bigvito19
|
 |
October 15, 2020, 09:40:41 AM |
|
It is impossible to bruteforce used private keys / seeds.
But only if there is no flawed random number generator used and the implementation doesn't include any other vulnerability.
Another member of the 'Impossible Squad' This is starting to get ridiculous now. I have to do something about this because all these lies might put people on the wrong track. It is very possible to bruteforce used private keys. In fact, I can prove you wrong in less then 10 seconds.Here is the used address you can look it up on the block explorer: 19ZewH8Kk1PDbSNdJ97FP4EiCjTRaZMZQA Here is the brute forced Private Key: http://www.youtube.com/watch?v=h5drF7wJgQgThis ends the discussion that it is impossible to brute force a used private key. I don't want to read or hear it anymore, it's not impossible, it is INEVITABLE.  Lol 'Impossible Squad', I like that. But how come you aren't searching for the 64 bit address, you must need the public key to use the program. |
|
|
|
|
HCP
Legendary

 Offline Offline
Activity: 2086
Merit: 4316
<insert witty quote here>

|
...
All great stuff.... in theory...  But saying there are <unknown things> that might, at <unknown point in the future> allow us to brute-force keys in a "reasonable" amount of time is not useful to people who need to brute-force keys NOW, is it?  You're arguing semantics, trying to look "cleverer" than everyone else in the room... but the fact of the matter is, if I give you "1JHxmgYtTADS7GpRPHbgzWdcDtkTHjj9eQ" which is an address which just received 0.23451412 BTC, the odds of you being able to brute-force the key for that address before <heat death of universe> (or even before the BTC are actually spent) are so close to zero that it may as well be zero. Which is the general meaning of "impossible" that everyone talks about when referring to brute-forcing keys. When these "unknown methods, unknown factors and unknown parameters" are made public... I'll happily admit that it is completely possible to brute-force all private keys. However, today, it is NOT possible... if it were, BTC would be worth zero as no coins would be safe. The entire system would be rendered useless. Feel free to maintain your "it's not impossible" stance, but until you can demonstrate the ability to brute-force the key for any given address in something resembling a standard human lifetime... well.... ¯\_(ツ)_/¯ |
|
|
|
BASE16
Member
 
 Offline Offline
Activity: 180
Merit: 38

|
 |
October 15, 2020, 12:53:05 PM |
|
All great stuff.... in theory...  ¯\_(ツ)_/¯ Not so fast.  Im not even trying to to look clever im just running the numbers and if you want to have a decent and meaningful discussion, then i think that you should do the same. These are not just theory and you can easily go and verify my notations. I gave you a very good and well put put together example, it's ok for you to ignore it but i can assure you that it will not go unnoticed among the community. Besides that we are not done yet, far from it, we are only just getting started. The reduction in key size it is not the only adjustment that you are going to have to face sooner or later. That oh so large or even 'astronomically large' <heat death of universe> space that you are currently defending, might just be a few hundred lightyears smaller then you had initially assumed. If you want, we can talk in exact numbers in stead of vague descriptions about how big something really is. Numbers don't lie unless the calculation is incomplete. When you look at randomness you can see that a bit had a 50% chance of becoming a 1 or a 0. Of course the generator can be adjusted in a way that it is biased to either side, but for all intense purposes let's assume a 50% distribution. In a fixed 50% distribution a private key will have 128 ones and 128 zeros. Because it's random, distribution will vary, but by how much exactly ? For example, if we generate 100 256 Bit private key's and analyze the distribution of ones and zeroes we can find something like this: 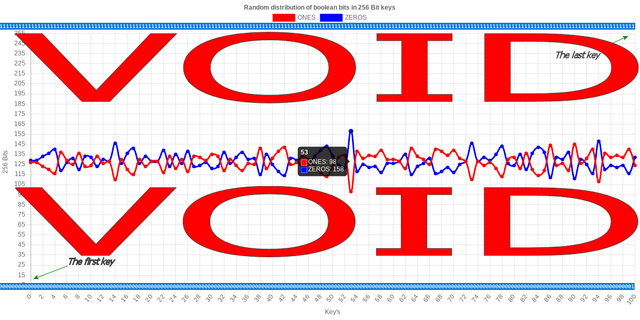 As you can see the number of ones versus zeros do not fluctuate all over the place, in fact most keys are contained within a remarkable small bandwidth. Most of the universe seems to be empty space.  |
|
|
|
|
|
bigvito19
|
 |
October 15, 2020, 04:53:11 PM |
|
The fact that some keys are able to be brute-forced, does not mean that all keys can be brute-forced.
So now we move from impossible to some keys can be brute forced. I must have started something because i can see some improvement in the claim. Let's step it up a notch. Here is the next step: If one key can be brute forced, then ALL keys can be brute forced. Your assumptions on how much time it will take according to the calculations including all known variables seems to be correct, but you have to calculate the time it will actually take in reality with all mod and methods applied. This is not possible if you do not know these methods yet, so it is understandable that you default to the known equations. Its a bad idea however, to present and defend them as facts. There are always the unknown methods, unknown factors and unknown parameters that when correctly applied, can smash your previous beliefs in an instant. A good example of this is the wright brothers vs all the people who claimed that a flying machine was impossible. We now have close to 10.000 airplanes in the sky at any given time. We also have the famous quote by Mark Twain, “They did not know it was impossible so they did it”. For example you could assume a 256 bits key strength, which takes n milliseconds to compute. But you have to realize that this only counts for YOU to get to YOUR public point. This is not so for an attacker, for an attacker ANY point will do. And the next point is not 256 Bits away. The next point is 1 Bit away. You can see that a private key has 255 intermediate public points that are normally just trashed inside of the calculation, but they are valid public points with valid addresses, for all you know you could have passed millions of BTC on some intermediate public point/address you landed on while on your way to bit 256 your own public point/address.... You will never know... Unless you deliberately looked for it.  Ok, you say all that but do you have a example(s) of what you just explain. |
|
|
|
|
BrewMaster
Legendary

 Offline Offline
Activity: 2114
Merit: 1292
There is trouble abrewing

|
 |
October 15, 2020, 06:45:18 PM |
|
..
now you are just twisting the words and adding a lot of assumption into your claims to make them true by force. if the key is within a known range like between 1 and 10, if the RNG was broken and were creating non-random keys, if the RNG was broken and had bias, if, if, if,... then it becomes possible to find ways to compute the private key. otherwise 100% of the keys produced by good wallets that have experts reviewing them (eg. bitcoin core and a lot of others) have always been 100% safe and random and it is impossible to break them. |
There is a FOMO brewing...
|
|
|
HCP
Legendary

 Offline Offline
Activity: 2086
Merit: 4316
<insert witty quote here>

|
 |
October 16, 2020, 12:50:09 AM |
|
... As you can see the number of ones versus zeros do not fluctuate all over the place, in fact most keys are contained within a remarkable small bandwidth. Most of the universe seems to be empty space.  That graph is a very poor illustration of the search space. For one, you only have 100 keys out of the ("slightly" less than) 2^256 that are actually available as valid keys. The sample size is so small as to be essentially worthless. To then say that "Most of the universe seems to be empty space" is simply disingenuous, given that you have randomly picked 100 out of ((1.158 * 10 77) - 1) possible options. Of course your "universe" is going to appear to be "empty" if you simply ignore pretty much all of it contents   |
|
|
|
|
nullius
|
things you find on the internet telling you there is some money in it if you could do something (like finding a wallet file and being able to brute force it) are always fake and most of them contain malware to steal your coins instead. Actually all tools which promise to crack private keys or "wallets" are malware.
And i am quite sure that a lot of people download these from those low quality youtube videos showing how to "crack wallets". That sounds almost like an ethical scam: Stealing from wannabe wallet thieves! Maybe I am in the wrong business...
It is impossible to bruteforce used private keys / seeds.
But only if there is no flawed random number generator used and the implementation doesn't include any other vulnerability. Another member of the 'Impossible Squad' This is starting to get ridiculous now. I have to do something about this because all these lies might put people on the wrong track. No, you are ridiculous. And you are not even on the wrong track: You are off the tracks entirely.
When you look at randomness you can see that a bit had a 50% chance of becoming a 1 or a 0.
Of course the generator can be adjusted in a way that it is biased to either side, but for all intense purposes let's assume a 50% distribution.
In a fixed 50% distribution a private key will have 128 ones and 128 zeros. Wrong. In a uniform distribution of random bits, from 256 bits, you will see anywhere from 0 zeroes and 256 ones to 256 zeroes and 0 ones. Usually, of course, the count of bits will fall somewhere in between. But the expected number of 0s or 1s is not 128. It is a common fallacy of wannabe cryptographers (and of gamblers!) to expect that from n coin flips, you will get n/2 heads and n/2 tails. Actually, one of the worst and most common fallacies. I see the same arrant nonsense being spouted all over the Internet. Start here: https://en.wikipedia.org/wiki/Binomial_distributionFrom the other direction, before you cut yourself on any sharp edges trying to judge the quality of random number generators, you will want to understand this: https://en.wikipedia.org/wiki/R%C3%A9nyi_entropyThen, take a random walk; and don’t come back until you understand very thoroughly just why, if you flip a fair coin 256 times and take a step forwards for H and backwards for T, you are rather unlikely to wind up exactly back where you started. Because it's random, distribution will vary, but by how much exactly ? For example, if we generate 100 256 Bit private key's and analyze the distribution of ones and zeroes we can find something like this:  As you can see the number of ones versus zeros do not fluctuate all over the place, in fact most keys are contained within a remarkable small bandwidth. Most of the universe seems to be empty space.  Your sample size listed on your graph is absurdly small; and from the shape of that graph, you seem to have empirically discovered evidence that the Central Limit Theorem really works! Extra credit: Get acquainted with the Law of the Iterated Logarithm.
All of this stuff has been studied by actual mathematicians. Which I myself am not. When the “Impossible Squad” tells you that bruteforcing a private key is, for all practical purposes, impossible, that is based on rigorous knowledge of subjects that you are approaching with some erroneous intuition, a sprinkling of New Age omphaloskepsis about the universe being mostly empty space, and very common fallacies that you would not suffer if you had ever taken even an introductory-level class in statistics (which I myself have not—but I like to read, with my brain switched on). Now, don’t make me sic Kolmogorov on you. I hear that he is downright brutal. |
|
|
|
|
2chase
|
 |
October 31, 2020, 07:46:17 PM |
|
|
|
|
|
|
|
irukandji
|
 |
November 01, 2020, 06:56:41 AM |
|
The short version is: 1. extract "password hash" from wallet.dat using the "Bitcoin2John" script (refer here: https://github.com/openwall/john/blob/bleeding-jumbo/doc/README.bitcoin) 2. run some sort of bruteforce tool to generate passwords and test them against the extracted hash Most common tools used for Step 2. are: - Hashcat - John The Ripper There is also btcrecover, which will create an extract from the wallet.dat and test passwords against it: https://github.com/gurnec/btcrecover/blob/master/docs/Extract_Scripts.md#usage-for-bitcoin-unlimitedclassicxtcoreAnecdotally, the performance of hashcat seems to be the "best"... I do not know anything about the password of the wallet itself This is going to be the largest obstacle... without any sort of knowledge of the number of characters or the types of characters used (lowercase? UPPPERCASE? numb3r5? symbo!s? whole words? etc) then trying to create rules sets to generate passwords to test could be quite difficult... and the possible keyspace is so large, that the whole process will likely be regarded as "impossible". ... and it is in the public domain (still has bitcoin on it),
Not necessarily. While the addresses listed in the wallet might still have BTC assigned to them, it's quite possible the wallet was modified to insert those specific public keys to make it appear that the wallet contains a large amount of BTC, however the encrypted private keys in the wallet do not actually match these addresses. It's impossible to tell until the encryption key is known.  and I am aware that this isn't easy money, but it is worth a shot.
Honestly, it really isn't... you likely have more chance of winning a lottery than cracking one of these "70,000 BTC" type wallets floating around on the internet  I have an electrum wallet and cannot remember the password. I think I know the words i used though so can narrow it down. Could i use any of these things? |
|
|
|
|
PawGo
Legendary

 Offline Offline
Activity: 952
Merit: 1367

|
 |
November 01, 2020, 06:53:36 PM |
|
I have an electrum wallet and cannot remember the password. I think I know the words i used though so can narrow it down. Could i use any of these things?
Do you know the seed? If yes - create a new wallet with the known seed. If not: the procedure is identical like with wallet.dat files from Bitcoin Core. If you suspect you know what could be the password - you may try to do it yourself. (be careful with sites like https://www.onlinehashcrack.com/tools-electrum-hash-extractor.php) Try to extract hash of password using the script from John the Ripper project: https://github.com/openwall/john/blob/bleeding-jumbo/run/electrum2john.pyYou should receive something like "$electrum$4*123456abcd...". then you may use this hash with hashcat. If in doubt - the best service seems to be https://www.walletrecoveryservices.com/ Email Dave, he will tell you what to do next. |
|
|
|
|
HCP
Legendary

 Offline Offline
Activity: 2086
Merit: 4316
<insert witty quote here>

|
 |
November 04, 2020, 09:44:41 PM |
|
I have an electrum wallet and cannot remember the password. I think I know the words i used though so can narrow it down. Could i use any of these things?
As PawGo suggested, recovering from the wallet seed mnemonic would be the preferable way, as you do not need to know the wallet file encryption password if you have the 12 word seed mnemonic. You can just restore using the "I already have a seed" option and it will recreate your wallet and allow you to set a new password. In addition to using JohnTheRipper and hashcat, you can also try btcrecover, but I'm not sure if that is working with Electrum wallets used with newer versions of Electrum (ie. version 3 or 4). |
|
|
|
COBRAS
Member
 
 Offline Offline
Activity: 846
Merit: 22
$$P2P BTC BRUTE.JOIN NOW ! https://uclck.me/SQPJk

|
 |
November 08, 2020, 02:52:55 AM |
|
|
|
|
|
|



