|
cozk (OP)
|
 |
February 16, 2015, 11:23:01 PM |
|
The U.S. National Security Agency has figured out how to hide spying software deep within hard drives made by Western Digital, Seagate, Toshiba and other top manufacturers, giving the agency the means to eavesdrop on the majority of the world's computers, according to cyber researchers and former operatives. STORY: http://www.cbc.ca/news/technology/nsa-hid-spying-software-in-hard-drive-firmware-report-says-1.2959252KASPERSKY super technical PDF REPORT: http://25zbkz3k00wn2tp5092n6di7b5k.wpengine.netdna-cdn.com/files/2015/02/Equation_group_questions_and_answers.pdf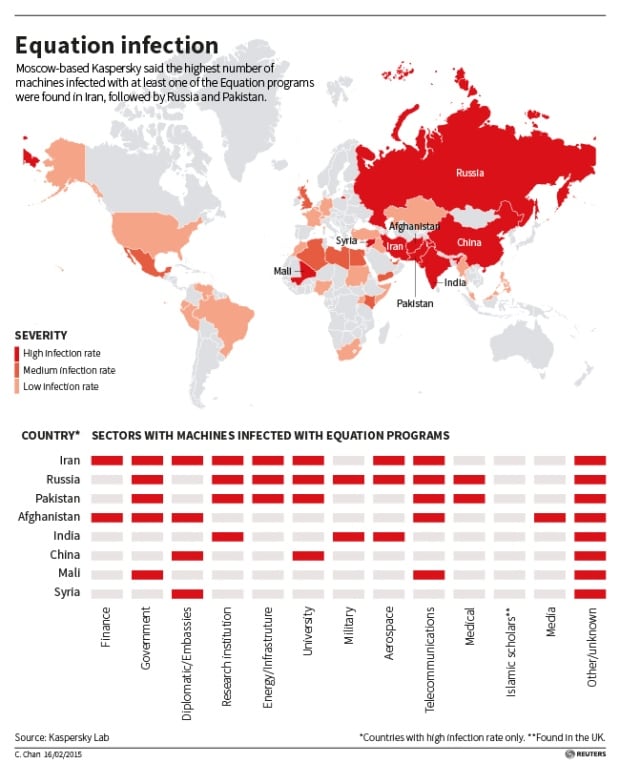 Kaspersky said it found personal computers in 30 countries infected with one or more of the spying programs, with the most infections seen in Iran, followed by Russia, Pakistan, Afghanistan, China, Mali, Syria, Yemen and Algeria. (Kaspersky Lab/Reuters) |
|
|
|
|
|
|
|
|
|
|
|
Be very wary of relying on JavaScript for security on crypto sites. The site can change the JavaScript at any time unless you take unusual precautions, and browsers are not generally known for their airtight security.
|
|
|
Advertised sites are not endorsed by the Bitcoin Forum. They may be unsafe, untrustworthy, or illegal in your jurisdiction.
|
|
|
|
|
Slark
Legendary

 Offline Offline
Activity: 1862
Merit: 1004

|
 |
February 16, 2015, 11:28:00 PM |
|
Moral of the story: if government wants to know what you are up to they will know - no matter what.Big brother is watching, with global social network, internet communicators spying is now easier than ever before.
|
|
|
|
|
|
Klestin
|
 |
February 16, 2015, 11:52:15 PM |
|
These two things do not go together:
1) Software was "completely undetectable" from the PC
2) Software executed on the PC
|
|
|
|
|
|
croato
|
 |
February 17, 2015, 12:26:53 AM |
|
I am not suprised, NSA is running USA and if they spy their alies like German goverment sure they spy regular ppl if nothing then to test their computing power lol.
|
|
|
|
|
|
ticoti
|
 |
February 17, 2015, 12:40:55 AM |
|
any way to know if our drive is one of that ?  |
|
|
|
|
|
Q7
|
 |
February 17, 2015, 12:49:22 AM |
|
Scary. But i wonder how this is possible since each hard disk manufacturer had their own proprietary hard drives' source code which mean they have to gain access one by one to insert the program.
|
|
|
|
|
cryptworld
|
 |
February 17, 2015, 12:58:01 AM |
|
this is creepy... we can't escape from the invasion of our privacy
|
|
|
|
|
|
orsotheysaid
|
 |
February 17, 2015, 01:17:45 AM |
|
Thats pretty fucking creepy.
|
|
|
|
|
|
calme
|
 |
February 17, 2015, 01:27:30 AM |
|
The U.S. government is out of control and does not represent or care about the U.S. American people.  |
|
|
|
|
rich93
Full Member
  
 Offline Offline
Activity: 595
Merit: 101
Chromia - Relational Blockchain


|
 |
February 17, 2015, 01:39:18 AM |
|
Is the KASPERSKY PDF available directly from KASPERSKY? Is there a KASPERSKY link to it?
|
|
|
|
|
BCwinning
|
 |
February 17, 2015, 01:42:32 AM |
|
One of the whistle blowers released this info a while back.
This is the first 3rd party source that I know of that has tied it all together so neatly.
|
The New World Order thanks you for your support of Bitcoin and encourages your continuing support so that they may track your expenditures easier.
|
|
|
|
croato
|
 |
February 17, 2015, 01:50:12 AM |
|
The U.S. government is out of control and does not represent or care about the U.S. American people.  That is true but not only U.S. govt, most goverments dont care about their ppl. |
|
|
|
|
bitkilo
Legendary

 Offline Offline
Activity: 1638
Merit: 1010
https://www.bitcoin.com/


|
 |
February 17, 2015, 01:55:27 AM |
|
Can't take a shit without the NSA or some government agency knowing what you ate last night anymore.
I didn't see Australia on the list so that's good but we have been in bed with the US for so long im sure there doing somthing similar here too.
|
Not a paid signature, just added to promote Bitcoin.com  |
|
|
|
Agestorzrxx
|
 |
February 17, 2015, 02:04:52 AM |
|
This is creazy, where is our privacy.
|
|
|
|
|
cakir
Legendary

 Offline Offline
Activity: 1274
Merit: 1000
★ BitClave ICO: 15/09/17 ★


|
 |
February 17, 2015, 02:06:14 AM |
|
They're gonna make me use my pc without a hdd... (Remove HDD and Boot a linux distro from usb / cd-rom)
|
|
|
|
|

|
|
,'#██+:
,█████████████'
+██████████████████
;██████████████████████
███████: .███████`
██████ ;█████'
`█████ #████#
████+ `████+
████: ████,
████: .# █ ████
;███+ ██ ███ ████
████ ███' ███. '███,
+███ #████ ,████ ████
████ █████ .+██████: █████+ `███.
,███ ███████████████████████ ████
████ ███████████████████████' :███
███: +████████████████████████ ███`
███ █████████████████████████` ███+
,███ ██████████████████████████ #███
'███ '██████████████████████████ ;███
#███ ███████████████████████████ ,███
████ ███████████████████████████. .███
████ ███████████████████████████' .███
+███ ███████████████████████████+ :███
:███ ███████████████████████████' +███
███ ███████████████████████████. ███#
███. #██████████████████████████ ███,
████ █████████████████████████+ `███
'███ '████████████████████████ ████
███; ███████████████████████ ███;
████ #████████████████████ ████
███# .██████████████████ `███+
████` ;██████████████ ████
████ '███████#. ████.
.████ █████
'████ █████
#████' █████
+█████` ██████
,██████: `███████
████████#;,..:+████████.
,███████████████████+
.███████████████;
`+███████#,
| |
|
|
|
rich93
Full Member
  
 Offline Offline
Activity: 595
Merit: 101
Chromia - Relational Blockchain


|
 |
February 17, 2015, 02:08:49 AM |
|
Thanks, its all over major news sites like Reuters, but I can't find a direct KASPERSKY link to it. |
|
|
|
manselr
Legendary

 Offline Offline
Activity: 868
Merit: 1004

|
 |
February 17, 2015, 02:19:19 AM |
|
It's clear now: we need open source hardware as well as internet decentralization.
|
|
|
|
|
Gleb Gamow
In memoriam
VIP
Legendary

 Offline Offline
Activity: 1428
Merit: 1145

|
 |
February 17, 2015, 02:26:00 AM |
|
http://bitcoin.stackexchange.com/questions/3736/is-wuala-lacie-the-largest-company-to-accept-bitcoinsIs Wuala (LaCie) the largest company to accept Bitcoins?
I just found out that you can pay for Wuala with Bitcoins. They are owned by LaCie, who have a revenue of €351.8 million according to Wikipedia. I think this makes them by far the largest company to accept Bitcoin for payment. Is that correct or are there other big players in the economy?
trade
shareimprove this question
asked May 20 '12 at 8:53
jl6
844312
Just to note that LaCie is now owned by Seagate (seagate.com/about/newsroom/press-releases/…) meaning that if Wuala is still accepting bitcoins (wuala.com/en/bitcoin) then this is probably by far the biggest company by market cap. accepting bitcoins in some form. – kirian Oct 10 '12 at 14:44
|
|
|
|
|
|
neurotypical
|
 |
February 17, 2015, 02:29:07 AM |
|
Is there an actual way to buy non NSA infected hardware or its a pipedream?
|
|
|
|
|
rich93
Full Member
  
 Offline Offline
Activity: 595
Merit: 101
Chromia - Relational Blockchain


|
 |
February 17, 2015, 02:36:27 AM |
|
Is there an actual way to buy non NSA infected hardware or its a pipedream?
If the story is right then they only targeted a limited amount of people's computers that held high value information. Most people were unaffected unless they worked high up in the government, or the military, or some other sensitive job. The hardware was sold uninfected but sometimes targeted with viruses that infected its firmware after purchase. |
|
|
|
ArticMine
Legendary

 Offline Offline
Activity: 2282
Merit: 1050
Monero Core Team

|
 |
February 17, 2015, 02:39:09 AM
Last edit: February 17, 2015, 03:02:48 AM by ArticMine |
|
I have read the .pdf and none of the malware works on GNU/Linux. It does work on Microsoft Windows, OS X and IOS. The simplest way to mitigate this risk is to: Ditch Microsoft, ditch Apple and run Free Software. Here is the relevant part of the .pdf. 22
13. �Have you seen any non-Windows
malware from the Equation group?
All the malware we have collected so far is designed to work on Microsoft’s
Windows operating system. However, there are signs that non-Windows malware
does exist. For instance, one of the sinkholed C&C domains is currently receiving
connections from a large pool of victims in China that appear to be Mac OS X
computers (based on the user-agent).
The malware callbacks are consistent with the DOUBLEFANTASY schema, which
normally injects into the system browser (for instance, Internet Explorer on
Windows).
The callbacks for the suspected Mac OS X versions have the following user
agents:
• Mozilla/5.0 (Macintosh; Intel Mac OS X 10_8_2) AppleWebKit/536.26.17
(KHTML, like Gecko) Version/6.0.2 Safari/536.26.17
• Mozilla/5.0 (Macintosh; Intel Mac OS X 10.8; rv:21.0) Gecko/20100101
Firefox/21.0
• Mozilla/5.0 (Macintosh; Intel Mac OS X 10_8_3) AppleWebKit/536.28.10
(KHTML, like Gecko) Version/6.0.3 Safari/536.28.10
This leads us to believe that a Mac OS X version of DOUBLEFANTASY also exists.
Additionally, we observed that one of the malicious forum injections, in the form
of a PHP script, takes special precautions to show a different type of HTML code to
Apple iPhone visitors. Unlike other cases, such as visitors from Jordan, which does
not get targeted, iPhone visitors are redirected to the exploit server, suggesting the
ability to infect iPhones as well. In order for the malware to get at the propriety hard disk firmware it needs Microsoft Windows or OS X. There is a reason why Edward Snowden uses GNU/Linux for his personal computing. Edit: Is there an actual way to buy non NSA infected hardware or its a pipedream?
It is way simpler to avoid NSA infected operating systems and the hardware will not get infected in the first place. Focusing on the hardware ignores the real risk which is operating systems which by their very nature are very friendly not just to the NSA but also to the PLA and FSB. |
|
|
|
wilth1
Member
 
 Offline Offline
Activity: 63
Merit: 10

|
 |
February 17, 2015, 03:25:23 AM |
|
Here's some relevant work: http://spritesmods.com/?art=hddhack&page=1It's not the exploits themselves that are surprising, but the sophisticated deployment often years prior to specimen disclosure or similar research. Docs indicate there are implants across the board that target free software OSes aplenty. |
|
|
|
|
ArticMine
Legendary

 Offline Offline
Activity: 2282
Merit: 1050
Monero Core Team

|
 |
February 17, 2015, 04:06:47 AM
Last edit: February 17, 2015, 04:22:10 AM by ArticMine |
|
Here's some relevant work: http://spritesmods.com/?art=hddhack&page=1It's not the exploits themselves that are surprising, but the sophisticated deployment often years prior to specimen disclosure or similar research. Docs indicate there are implants across the board that target free software OSes aplenty. Very interesting site. It does add to the how of the NSA exploit. It also shows how this could also be used for another nefarious purpose namely DRM (preventing disk cloning). Yes this could be used to re install malware after the server was cleaned up, and this attack could work on a GNU/Linux system. The practical reality is that the attacker would need either root on the server / and or physical access to the hard drive. So it come down to the question how does the attacker get root in the first place? It is at this point where propriety operating systems provide a huge advantage to the attacker. Microsoft regularly provides access to the source code and advance knowledge of vulnerabilities to agencies such as the NSA, PLA and FSB. This creates a hugely uneven playing field since the attackers have access to the source code and vulnerabilities while the defenders do not. Stuxnet is a prime example of what can happen. In addition operating systems that support DRM must have hidden and obtuse parts to support the DRM. We must not forget that DRM and malware are in reality accomplishing the same thing. It is easy to spy on a user of say Windows, OS X or IOS when those operating systems by design treat that same user as an adversary not to be trusted. With GNU/Linux everyone has access to the source code creating a level playing field, and the operating system does not treat the user as an adversary not to be trusted. Big difference. |
|
|
|
TippingPoint
Legendary

 Offline Offline
Activity: 905
Merit: 1000

|
 |
February 17, 2015, 04:21:10 AM |
|
Raiu said the authors of the spying programs must have had access to the proprietary source code that directs the actions of the hard drives. That code can serve as a roadmap to vulnerabilities, allowing those who study it to launch attacks much more easily.
"There is zero chance that someone could rewrite the [hard drive] operating system using public information," Raiu said. They could get the hard drive firmware source code by approaching a key manager or employee directly, using traditional incentives of blackmail, extortion, bribery, sex, false flag, appeal to patriatism, etc. or by infiltration with a qualified agent. |
|
|
|
|
ArticMine
Legendary

 Offline Offline
Activity: 2282
Merit: 1050
Monero Core Team

|
 |
February 17, 2015, 05:20:16 AM |
|
Raiu said the authors of the spying programs must have had access to the proprietary source code that directs the actions of the hard drives. That code can serve as a roadmap to vulnerabilities, allowing those who study it to launch attacks much more easily.
"There is zero chance that someone could rewrite the [hard drive] operating system using public information," Raiu said. They could get the hard drive firmware source code by approaching a key manager or employee directly, using traditional incentives of blackmail, extortion, bribery, sex, false flag, appeal to patriatism, etc. or by infiltration with a qualified agent. ... or simply by making a deal with the manufacturer. No fancy spy techniques needed at all. |
|
|
|
Lauda
Legendary

 Offline Offline
Activity: 2674
Merit: 2965
Terminated.


|
 |
February 17, 2015, 05:37:43 AM |
|
Why does this surprise you? I was actually expecting something like this. The NSA just forces things like this on manufacturers.
You could prevent this from happening though, if you block the right outgoing traffic.
|
"The Times 03/Jan/2009 Chancellor on brink of second bailout for banks" 😼 Bitcoin Core ( onion) |
|
|
AGD
Legendary

 Offline Offline
Activity: 2069
Merit: 1164
Keeper of the Private Key

|
 |
February 17, 2015, 05:54:50 AM |
|
https://bitcointalk.org/index.php?topic=948636.msg10387510#msg10387510There is no big business without national interest. If you have a tech company and make millions, you are making part of national security already. Intel IS part of the national security since the 70s. You think Bill Gates would have sold his OS, if he refused the offer from the guys in the black suits back in the days?
Same with Seagate, IBM, WD, Samsung, Sony, GB, MSI and a lot more.
|
|
|
|
|
lunarboy
|
 |
February 17, 2015, 05:56:38 AM |
|
http://arstechnica.com/security/2015/02/how-omnipotent-hackers-tied-to-the-nsa-hid-for-14-years-and-were-found-at-last/A long list of almost superhuman technical feats illustrate Equation Group's extraordinary skill, painstaking work, and unlimited resources. They include:
The use of virtual file systems, a feature also found in the highly sophisticated Regin malware. Recently published documents provided by Ed Snowden indicate that the NSA used Regin to infect the partly state-owned Belgian firm Belgacom.
The stashing of malicious files in multiple branches of an infected computer's registry. By encrypting all malicious files and storing them in multiple branches of a computer's Windows registry, the infection was impossible to detect using antivirus software.
Redirects that sent iPhone users to unique exploit Web pages. In addition, infected machines reporting to Equation Group command servers identified themselves as Macs, an indication that the group successfully compromised both iOS and OS X devices.
The use of more than 300 Internet domains and 100 servers to host a sprawling command and control infrastructure.
USB stick-based reconnaissance malware to map air-gapped networks, which are so sensitive that they aren't connected to the Internet. Both Stuxnet and the related Flame malware platform also had the ability to bridge airgaps.
An unusual if not truly novel way of bypassing code-signing restrictions in modern versions of Windows, which require that all third-party software interfacing with the operating system kernel be digitally signed by a recognized certificate authority. To circumvent this restriction, Equation Group malware exploited a known vulnerability in an already signed driver for CloneCD to achieve kernel-level code execution.
Taken together, the accomplishments led Kaspersky researchers to conclude that Equation Group is probably the most sophisticated computer attack group in the world, with technical skill and resources that rival the groups that developed Stuxnet and the Flame espionage malware. The unfettered arrogance of these spies makes my skin creep. What happens next I wonder? Governments, agencies and hackers around the world have just received an advanced class in malware and will co-opt it to do as they please. The harm done by these intrusions will be 10 fold any advantage gained.
|
|
|
|
|
BitMos
Full Member
  
 Offline Offline
Activity: 182
Merit: 123
"PLEASE SCULPT YOUR SHIT BEFORE THROWING. Thank U"

|
 |
February 17, 2015, 12:33:11 PM |
|
The U.S. government is out of control and does not represent or care about the U.S. American people.  simply. It has been INCORPORATED. |
money is faster...
|
|
|
ajareselde
Legendary

 Offline Offline
Activity: 1722
Merit: 1000
Satoshi is rolling in his grave. #bitcoin

|
 |
February 17, 2015, 03:37:07 PM |
|
Why does this surprise you? I was actually expecting something like this. The NSA just forces things like this on manufacturers.
You could prevent this from happening though, if you block the right outgoing traffic.
Block outgoing traffic? Well if were talking about dan hard drives that come with malware embedded, i wouldnt be surprised if the very software were using to defend us against such threats would be compromised to some extent also. Maybe thats why two antivirus programs recognize each other as infections :] cheers |
|
|
|
|
WEB slicer
Legendary

 Offline Offline
Activity: 1120
Merit: 1001
1NF4xXDDpMVmeazJxJDLrFxuJrCAT7CB1b

|
 |
February 17, 2015, 05:25:17 PM |
|
The U.S. government is out of control and does not represent or care about the U.S. American people.  +1 |
|
|
|
Wilikon
Legendary

 Offline Offline
Activity: 1176
Merit: 1001
minds.com/Wilikon

|
 |
February 17, 2015, 05:29:24 PM |
|
It's clear now: we need open source hardware as well as internet decentralization.
Yep... |
|
|
|
|
CIYAM
Legendary

 Offline Offline
Activity: 1890
Merit: 1078
Ian Knowles - CIYAM Lead Developer


|
 |
February 17, 2015, 05:37:41 PM |
|
And people thought I was being "too paranoid" when I created a QR code system for doing offline Bitcoin tx signing (whereas Armory still uses a USB stick).
|
|
|
|
ArticMine
Legendary

 Offline Offline
Activity: 2282
Merit: 1050
Monero Core Team

|
 |
February 17, 2015, 05:53:20 PM
Last edit: February 17, 2015, 06:19:37 PM by ArticMine |
|
Why does this surprise you? I was actually expecting something like this. The NSA just forces things like this on manufacturers.
You could prevent this from happening though, if you block the right outgoing traffic.
No the NSA does not force this on manufacturers. The manufactures do this because they believe they can get away with spying on their customers and selling the fruits of their spying for profit to marketers. Another very common motivation for manufactures to spy on their customers is DRM and "intellectual property protection". Agencies like the NSA come in much later. They realize the manufactures have valuable data and make a deal with the manufactures for access to that data. As for blocking the outgoing traffic yes on can do this but one must take over control of one's network and computing devices. The best way to do this is using Free Software. What actually happens is that one can build a Free Software jail around the propriety software "appliance". This can allow the owner to then use the appliance while blocking or controlling the malicious features in the appliance’s propriety software. It then becomes a battle for control between the owner and the appliance with each one trying to control the other. Edit1: This process is completely voluntary. The iSheep for example provide data to Apple on a voluntary (they clicked I agreee on Apple's EULA) basis. Apple also provides the data to the NSA on a voluntary basis to the NSA via the PRISM program. https://en.wikipedia.org/wiki/PRISM_%28surveillance_program%29. This is why many libertarians simply do not understand the real nature of the threat. Edit2: https://bitcointalk.org/index.php?topic=948636.msg10387510#msg10387510There is no big business without national interest. If you have a tech company and make millions, you are making part of national security already. Intel IS part of the national security since the 70s. You think Bill Gates would have sold his OS, if he refused the offer from the guys in the black suits back in the days?
Same with Seagate, IBM, WD, Samsung, Sony, GB, MSI and a lot more. Bill Gates did not just sell out to the United States. He also sold out to China and Russia among others. Ever wonder where all that Chinese hacking of Windows that has been traced back to the PLA came from? It is hardly surprising that Microsoft Windows has become such a cesspool of malware. |
|
|
|
BitMos
Full Member
  
 Offline Offline
Activity: 182
Merit: 123
"PLEASE SCULPT YOUR SHIT BEFORE THROWING. Thank U"

|
 |
February 17, 2015, 06:20:00 PM |
|
Why does this surprise you? I was actually expecting something like this. The NSA just forces things like this on manufacturers.
You could prevent this from happening though, if you block the right outgoing traffic.
No the NSA does not force this on manufacturers. The manufactures do this because they believe they can get away with spying on their customers and selling the fruits of their spying for profit to marketers. Another very common motivation for manufactures to spy on their customers is DRM and "intellectual property protection". Agencies like the NSA come in much later. They realize the manufactures have valuable data and make a deal with the manufactures for access to that data. As for blocking the outgoing traffic yes on can do this but one must take over control of one's network and computing devices. The best way to do this is using Free Software. What actually happens is that one can build a Free Software jail around the propriety software "appliance". This can allow the owner to then use the appliance while blocking or controlling the malicious features in the appliance’s propriety software. It then becomes a battle for control between the owner and the appliance with each one trying to control the other. Edit: This process is completely voluntary. The iSheep for example provide data to Apple on a voluntary (they clicked I agreee on Apple's EULA) basis. Apple also provides the data to the NSA on a voluntary basis to the NSA via the PRISM program. https://en.wikipedia.org/wiki/PRISM_%28surveillance_program%29. This is why many libertarians simply do not understand the real nature of the threat. Thank you for this interesting perspectives. It will sound ironic or naïve but I trust more the NSA than the marketers (1 THE NSA CAN "PRINT"). And here is why, the NSA can do infinitely more damages in all aspects to anyone than a "marketer" (because, who is really behind those buying), anyway, However, don't fool the NSA. Snowden, Binner... are few, don't forget they spoke against something that was against their own consciousness, however "exploiting" the nsa, that's another story, that ends more than often very silently... As such when a marketer "exploits" nsa people in their daily civilian lives, I believe it's the duty of those more versed in real combat operation (SF) after consultation with the "exploited" to take the lead and bring the Enemy (foreign or domestic) to his end. Naïve or stupid? Who cares  . I see a lot of possibility of exploits (zeroday real life attack, not very clever not to discuss it, it's called hiding) in those marketers... and contrary to nsa agents aren't really aware of what a betrayal (should) implies, once upon a time... |
money is faster...
|
|
|
TippingPoint
Legendary

 Offline Offline
Activity: 905
Merit: 1000

|
 |
February 17, 2015, 06:43:56 PM |
|
Raiu said the authors of the spying programs must have had access to the proprietary source code that directs the actions of the hard drives. That code can serve as a roadmap to vulnerabilities, allowing those who study it to launch attacks much more easily.
"There is zero chance that someone could rewrite the [hard drive] operating system using public information," Raiu said. They could get the hard drive firmware source code by approaching a key manager or employee directly, using traditional incentives of blackmail, extortion, bribery, sex, false flag, appeal to patriatism, etc. or by infiltration with a qualified agent. ... or simply by making a deal with the manufacturer. No fancy spy techniques needed at all. I doubt that agents would even attempt to make such a deal unless they already had leverage on someone. The consequences of alerting the target, and causing increased security measures would be too severe. Leverage could come from allegations or knowledge of corporate or individual income tax evasion, insider trading, or other human foibles such as infidelity. And agents would not want such an arrangement to be documented in writing. Alternatively, access to firmware code could be obtained as part of a large government purchase or certification of hardware, and compliance with MILSPECs. |
|
|
|
|
AGD
Legendary

 Offline Offline
Activity: 2069
Merit: 1164
Keeper of the Private Key

|
 |
February 17, 2015, 07:38:54 PM |
|
Why does this surprise you? I was actually expecting something like this. The NSA just forces things like this on manufacturers.
You could prevent this from happening though, if you block the right outgoing traffic.
No the NSA does not force this on manufacturers. The manufactures do this because they believe they can get away with spying on their customers and selling the fruits of their spying for profit to marketers. Another very common motivation for manufactures to spy on their customers is DRM and "intellectual property protection". Agencies like the NSA come in much later. They realize the manufactures have valuable data and make a deal with the manufactures for access to that data. As for blocking the outgoing traffic yes on can do this but one must take over control of one's network and computing devices. The best way to do this is using Free Software. What actually happens is that one can build a Free Software jail around the propriety software "appliance". This can allow the owner to then use the appliance while blocking or controlling the malicious features in the appliance’s propriety software. It then becomes a battle for control between the owner and the appliance with each one trying to control the other. Edit1: This process is completely voluntary. The iSheep for example provide data to Apple on a voluntary (they clicked I agreee on Apple's EULA) basis. Apple also provides the data to the NSA on a voluntary basis to the NSA via the PRISM program. https://en.wikipedia.org/wiki/PRISM_%28surveillance_program%29. This is why many libertarians simply do not understand the real nature of the threat. Edit2: https://bitcointalk.org/index.php?topic=948636.msg10387510#msg10387510There is no big business without national interest. If you have a tech company and make millions, you are making part of national security already. Intel IS part of the national security since the 70s. You think Bill Gates would have sold his OS, if he refused the offer from the guys in the black suits back in the days?
Same with Seagate, IBM, WD, Samsung, Sony, GB, MSI and a lot more. Bill Gates did not just sell out to the United States. He also sold out to China and Russia among others. Ever wonder where all that Chinese hacking of Windows that has been traced back to the PLA came from? It is hardly surprising that Microsoft Windows has become such a cesspool of malware. IF Bill sold out to others than the US, this would make part of the US foreign policy. Means, the NSA still would have the power to access every computer worldwide. |
|
|
|
|
croato
|
 |
February 17, 2015, 08:07:03 PM |
|
Looks like U.S. goverment lost controll and NSA is now in charge. I am not conspiracy theory fanatic but how to explain all that. Land of the free is becoming land of slaves and drones infecting whole world with their controll freak shit.
|
|
|
|
|
BitMos
Full Member
  
 Offline Offline
Activity: 182
Merit: 123
"PLEASE SCULPT YOUR SHIT BEFORE THROWING. Thank U"

|
 |
February 17, 2015, 08:33:52 PM
Last edit: February 17, 2015, 08:47:46 PM by BitMos |
|
Looks like U.S. goverment lost controll and NSA is now in charge. I am not conspiracy theory fanatic but how to explain all that. Land of the free is becoming land of slaves and drones infecting whole world with their controll freak shit.
the incorporation of the FED predates the Incorporation of the NSA, we can only hope for a take over of the FED and affiliates by the NSA and affiliates, for the better, don't forget that the NSA is just a part of the Military Industrial and Intelligence Complex, and as such has seen how systematic the horrors of wars are, stealth (ctrl+p) or plain visible. What ever darkness of man doings seems unstable in it's nature, furthermore exacerbates when the "adversaries" are on the Path.  interesting quotes : Questioning known liars makes you a "conspiracy theorist". ... The conspiracy theorist is the sheep in the middle trying to go in the opposite direction but constantly pushed by the 'normal' sheep into the slaughter chute. ... "conspiracy theorist" is a derogatory label coined by the media black arts (if they only knew  ) ) practitioners specifically for the purpose of unfairly maligning or smearing any person who challenges the official government/media/corporate narrative about anything. Because of this, the government media duo and the corporations they protect have a shield against all probing questions. As soon as you cause any static, you're a conspiracy theorist. add marketable digital profiles to use for " targeted ads attacks".   I don't understand why those holding the triggers, would serve against their interests known liars. Stupidity? A Master Plan, Who Knows  . But those who don't, and are on the "tricks" shall be aware, they know. ahaha. What sum of money can erase the blood, sweet and tears of a dying fallen? Guess, pen holders. But I agree the Mastery of the Arts of Wars aren't very "sexy"  . who cares, anyway. When the SWARM gravitates inwards, primitive parasitism is restored (on'a entropic lvl (Δ SBTC$,S)        ), some times, or all ways, who knows...  The civilian admin occupying the (R)ecless and white house buildins since a little too long is very not conducive for business, to come back to your first point...  |
money is faster...
|
|
|
TECSHARE
In memoriam
Legendary

 Offline Offline
Activity: 3318
Merit: 1958
First Exclusion Ever


|
 |
February 17, 2015, 09:22:34 PM |
|
Looks like U.S. goverment lost controll and NSA is now in charge. I am not conspiracy theory fanatic but how to explain all that. Land of the free is becoming land of slaves and drones infecting whole world with their controll freak shit.
Everyone seems to just gloss over the fact that the NSA is basically the biggest blackmail machine ever designed. They could easily subvert our government with it, or any other organization for that matter. Take out, discredit, or control those in key positions in any centralized organization, you own the whole. |
|
|
|
|
Cablez
Legendary

 Offline Offline
Activity: 1400
Merit: 1000
I owe my soul to the Bitcoin code...

|
 |
February 17, 2015, 10:04:37 PM |
|
Isn't that similar to J Edgar Hoover and the FBI of yore? They supposedly had dirt on everyone of consequence back then. Real easy to turn the power tables.
|
Tired of substandard power distribution in your ASIC setup??? Chris' Custom Cablez will get you sorted out right! No job too hard so PM me for a quote
Check my products or ask a question here: https://bitcointalk.org/index.php?topic=74397.0
|
|
|
freedomno1
Legendary

 Offline Offline
Activity: 1806
Merit: 1090
Learning the troll avoidance button :)

|
 |
February 18, 2015, 01:07:15 AM |
|
This is very orwellian
Scares the heck out of you when police and spy agencies can target individuals
When non violent peaceful activities get monitored by default that is a threat to all people especially if its in key storage infrastructure.
Recommend the Core Devs get checked as they were on the toplist
• Companies developing cryptographic technologies
|
Believing in Bitcoins and it's ability to change the world
|
|
|
BitMos
Full Member
  
 Offline Offline
Activity: 182
Merit: 123
"PLEASE SCULPT YOUR SHIT BEFORE THROWING. Thank U"

|
 |
February 18, 2015, 06:47:53 AM |
|
This is very orwellian
Scares the heck out of you when police and spy agencies can target individuals
When non violent peaceful activities get monitored by default that is a threat to all people especially if its in key storage infrastructure.
Recommend the Core Devs get checked as they were on the toplist
• Companies developing cryptographic technologies
then I don't understand why the "billionaires" of America are allowed to do what they want, they are just tools, probes, or test of exploits ?... nothing to be afraid of? Or have gain a domination over the nsa and are using them like their slaves for their needs? Never be scared, who is the Greatest? Who can you Trust? don't get fooled again. It's normal to die. Would you have trusted all along or just before the End? What's your relation with your coming crossing to the other side? Do you know yourself? Do you know your fears? Did you took the time to overcome them? |
money is faster...
|
|
|
AGD
Legendary

 Offline Offline
Activity: 2069
Merit: 1164
Keeper of the Private Key

|
 |
February 18, 2015, 07:49:14 AM |
|
Looks like U.S. goverment lost controll and NSA is now in charge. I am not conspiracy theory fanatic but how to explain all that. Land of the free is becoming land of slaves and drones infecting whole world with their controll freak shit.
US gov + US industry loves the NSA! They have gained huge advantages over the worldwide competitors due to the work of the NSA. |
|
|
|
phelix
Legendary

 Offline Offline
Activity: 1708
Merit: 1020

|
 |
February 18, 2015, 10:10:52 AM |
|
Looks like U.S. goverment lost controll and NSA is now in charge. I am not conspiracy theory fanatic but how to explain all that. Land of the free is becoming land of slaves and drones infecting whole world with their controll freak shit.
this Plenty of people will become pathologically paranoid from all this. I already curse the NSA when one of my systems runs slow   |
|
|
|
|
uki
Legendary

 Offline Offline
Activity: 1358
Merit: 1000
cryptojunk bag holder

|
 |
February 18, 2015, 10:40:20 AM |
|
This is when you start thinking 1984 was a mere fairytale.
|
this space is intentionally left blank
|
|
|
GreekBitcoin
Legendary

 Offline Offline
Activity: 1428
Merit: 1001
getmonero.org


|
 |
February 18, 2015, 10:44:04 AM |
|
 Stasi is bad! China is spying our companies. North Korea is spying their people. Iran censorships the web. etc... West democracy is the only way! oh wait.... |
|
|
|
|
GreekBitcoin
Legendary

 Offline Offline
Activity: 1428
Merit: 1001
getmonero.org


|
 |
February 18, 2015, 10:52:21 AM |
|
 So by giving CIA, NSA etc ultimate powers at least now the world is a safer place right? No terrorists, no wars, no threats, economic stability... I wonder who is going to save us from them. |
|
|
|
|
BitMos
Full Member
  
 Offline Offline
Activity: 182
Merit: 123
"PLEASE SCULPT YOUR SHIT BEFORE THROWING. Thank U"

|
 |
February 18, 2015, 11:03:12 AM |
|
 So by giving CIA, NSA etc ultimate powers at least now the world is a safer place right? No terrorists, no wars, no threats, economic stability... I wonder who is going to save us from them. that's my fav part, forget everything you saw, it's THE SHOW OF THE SWARM (). |
money is faster...
|
|
|
|
tss
|
 |
February 18, 2015, 12:49:11 PM |
|
CRAP! they got me! that's pretty slick though, hardware built in rats, glad it's public now.
how do i check if my drives are affected?
|
|
|
|
|
|
|
TippingPoint
Legendary

 Offline Offline
Activity: 905
Merit: 1000

|
 |
February 18, 2015, 03:59:40 PM |
|
It might be worth mentioning that the story, at least at this point, is that the altered hard drive firmware is not being installed on drives before they leave the factory. The story is that the altered firmware is later installed on targeted computers, sometimes by individually-prepared installation CDs, and sometimes by NSAs Office of Tailored Access Operations. During the middle part of the last decade, the special unit (TAO) succeeded in gaining access to 258 targets in 89 countries -- nearly everywhere in the world. In 2010, it conducted 279 operations worldwide. According to details in Washington's current budget plan for the US intelligence services, around 85,000 computers worldwide are projected to be infiltrated by the NSA specialists by the end of this year. By far the majority of these "implants" are conducted by TAO teams via the Internet. http://www.spiegel.de/international/world/the-nsa-uses-powerful-toolbox-in-effort-to-spy-on-global-networks-a-940969-druck.html |
|
|
|
|
uki
Legendary

 Offline Offline
Activity: 1358
Merit: 1000
cryptojunk bag holder

|
 |
February 18, 2015, 04:27:57 PM |
|
It might be worth mentioning that the story, at least at this point, is that the altered hard drive firmware is not being installed on drives before they leave the factory. The story is that the altered firmware is later installed on targeted computers, sometimes by individually-prepared installation CDs, and sometimes by NSAs Office of Tailored Access Operations. During the middle part of the last decade, the special unit (TAO) succeeded in gaining access to 258 targets in 89 countries -- nearly everywhere in the world. In 2010, it conducted 279 operations worldwide. According to details in Washington's current budget plan for the US intelligence services, around 85,000 computers worldwide are projected to be infiltrated by the NSA specialists by the end of this year. By far the majority of these "implants" are conducted by TAO teams via the Internet. http://www.spiegel.de/international/world/the-nsa-uses-powerful-toolbox-in-effort-to-spy-on-global-networks-a-940969-druck.htmlThat changes the scale of the whole story quite drastically. Media love to alarm people as they will gladly read such stories. There is of course an immediate question popping up: what if someone used that kind of weapon against the 'average Joe' and for what reason? |
this space is intentionally left blank
|
|
|
BitMos
Full Member
  
 Offline Offline
Activity: 182
Merit: 123
"PLEASE SCULPT YOUR SHIT BEFORE THROWING. Thank U"

|
 |
February 18, 2015, 04:33:53 PM |
|
It might be worth mentioning that the story, at least at this point, is that the altered hard drive firmware is not being installed on drives before they leave the factory. The story is that the altered firmware is later installed on targeted computers, sometimes by individually-prepared installation CDs, and sometimes by NSAs Office of Tailored Access Operations. During the middle part of the last decade, the special unit (TAO) succeeded in gaining access to 258 targets in 89 countries -- nearly everywhere in the world. In 2010, it conducted 279 operations worldwide. According to details in Washington's current budget plan for the US intelligence services, around 85,000 computers worldwide are projected to be infiltrated by the NSA specialists by the end of this year. By far the majority of these "implants" are conducted by TAO teams via the Internet. http://www.spiegel.de/international/world/the-nsa-uses-powerful-toolbox-in-effort-to-spy-on-global-networks-a-940969-druck.htmlThat changes the scale of the whole story quite drastically. Media love to alarm people as they will gladly read such stories. There is of course an immediate question popping up: what if someone used that kind of weapon against the 'average Joe' and for what reason? ukie boy they fucking don't care of average joe, they want his wife and his daughter... the rest is pure BS, they are primates. |
money is faster...
|
|
|
uki
Legendary

 Offline Offline
Activity: 1358
Merit: 1000
cryptojunk bag holder

|
 |
February 18, 2015, 04:40:33 PM |
|
That changes the scale of the whole story quite drastically. Media love to alarm people as they will gladly read such stories. There is of course an immediate question popping up: what if someone used that kind of weapon against the 'average Joe' and for what reason?
ukie boy they fucking don't care of average joe, they want his wife and his daughter... the rest is pure BS, they are primates. BitMos, just read my post again. I wrote that such story sells very well in the media, as people tend to think 'what if they used it against my computer?' Of course they don't care about the average Joe like you or me (as of today), but who knows if one day you become important guy, you may want to check your hard drive. |
this space is intentionally left blank
|
|
|
BitMos
Full Member
  
 Offline Offline
Activity: 182
Merit: 123
"PLEASE SCULPT YOUR SHIT BEFORE THROWING. Thank U"

|
 |
February 18, 2015, 04:55:18 PM |
|
That changes the scale of the whole story quite drastically. Media love to alarm people as they will gladly read such stories. There is of course an immediate question popping up: what if someone used that kind of weapon against the 'average Joe' and for what reason?
ukie boy they fucking don't care of average joe, they want his wife and his daughter... the rest is pure BS, they are primates. BitMos, just read my post again. I wrote that such story sells very well in the media, as people tend to think 'what if they used it against my computer?' Of course they don't care about the average Joe like you or me (as of today), but who knows if one day you become important guy, you may want to check your hard drive. that's why PLAoC and Russia have no others choices... I know that for American controllers every girls born on earth is a future hole they will fuck (they are worth it remember, they are the chosen ones)... And what do you think the Germans think about a foreign nations having access to all the data of their Nation? ahaha... amerikis, betrayal&deceit incorporated. |
money is faster...
|
|
|
Balthazar
Legendary

 Offline Offline
Activity: 3108
Merit: 1358

|
 |
February 18, 2015, 05:01:33 PM
Last edit: February 18, 2015, 09:18:25 PM by Balthazar |
|
The U.S. National Security Agency has figured out how to hide spying software deep within hard drives made by Western Digital, Seagate, Toshiba and other top manufacturers, giving the agency the means to eavesdrop on the majority of the world's computers, according to cyber researchers and former operatives. STORY: http://www.cbc.ca/news/technology/nsa-hid-spying-software-in-hard-drive-firmware-report-says-1.2959252KASPERSKY super technical PDF REPORT: http://25zbkz3k00wn2tp5092n6di7b5k.wpengine.netdna-cdn.com/files/2015/02/Equation_group_questions_and_answers.pdf Kaspersky said it found personal computers in 30 countries infected with one or more of the spying programs, with the most infections seen in Iran, followed by Russia, Pakistan, Afghanistan, China, Mali, Syria, Yemen and Algeria. (Kaspersky Lab/Reuters) This feature will be helpful only if it's targeted against the regular user, because any government has a special policy for ssecret/private information. If we're talking about Russia then there are serious requirements to hardware and software if you wish to work with sensitive data, such as secret documentation. Here are some of those requirements: - FSB approved SATA/SAS controller with runtime encryption and separate flash memory for the boot loader, kernel image and device drivers. 1;
- Approved operation system2;
- All system modules should be digitally signed, it's prohibited to execute any unsigned software;
- Isolated network or no networking at all;
- Mandatory access control (MAC) for file system and database records.
If somebody would work with secret data while his system doesn't match those requirements, he'll get few years in the jail for simply doing that.  1. I.e. so-called APMDZ aka "hardware-software module for trusted boot", our company provides Maxim-M1 for that purpose. 1. I.e. so-called APMDZ aka "hardware-software module for trusted boot", our company provides Maxim-M1 for that purpose.
2. Current preference is our debian-based Linux distro, AstraLinux SE. It's currently used by the most of government institutions to work with sensitive data. |
|
|
|
|
BitMos
Full Member
  
 Offline Offline
Activity: 182
Merit: 123
"PLEASE SCULPT YOUR SHIT BEFORE THROWING. Thank U"

|
 |
February 18, 2015, 05:08:05 PM |
|
If somebody would work with secret data while his system doesn't match those requirements, he'll get few years in the jail for simply doing that.  I hope so, otherwise it would allow a plausible deniability way for the traitors... and who does want to see the Motherland fall in the Hands of the controllers of America (biden, his son, or the worst they hide under praise and glory). |
money is faster...
|
|
|
|
98problems
|
 |
February 18, 2015, 11:19:45 PM |
|
It might be worth mentioning that the story, at least at this point, is that the altered hard drive firmware is not being installed on drives before they leave the factory. The story is that the altered firmware is later installed on targeted computers, sometimes by individually-prepared installation CDs, and sometimes by NSAs Office of Tailored Access Operations. During the middle part of the last decade, the special unit (TAO) succeeded in gaining access to 258 targets in 89 countries -- nearly everywhere in the world. In 2010, it conducted 279 operations worldwide. According to details in Washington's current budget plan for the US intelligence services, around 85,000 computers worldwide are projected to be infiltrated by the NSA specialists by the end of this year. By far the majority of these "implants" are conducted by TAO teams via the Internet. http://www.spiegel.de/international/world/the-nsa-uses-powerful-toolbox-in-effort-to-spy-on-global-networks-a-940969-druck.htmlThat changes the scale of the whole story quite drastically. Media love to alarm people as they will gladly read such stories. There is of course an immediate question popping up: what if someone used that kind of weapon against the 'average Joe' and for what reason? I wouldn't be surprised if the 'average person' were targeted by some program similar to this. They already are targeted by a number of other NSA spying programs so I don't see why this would be any different |
|
|
|
|
jt byte
|
 |
February 19, 2015, 02:36:53 AM |
|
The US has control of the internet, communications satellites, and everything else we use to communicate electronically
|
|
|
|
|
Souldream
Legendary

 Offline Offline
Activity: 1110
Merit: 1000

|
 |
February 19, 2015, 06:30:33 AM |
|
Scary. But i wonder how this is possible since each hard disk manufacturer had their own proprietary hard drives' source code which mean they have to gain access one by one to insert the program.
They dump, reverse analyse and patch it , NSA have the so far the best reverse/hacker, they do not need source ! |
|
|
|
|
AGD
Legendary

 Offline Offline
Activity: 2069
Merit: 1164
Keeper of the Private Key

|
 |
February 19, 2015, 07:31:42 AM |
|
The US has control of the internet, communications satellites, and everything else we use to communicate electronically
Even more: most, if not all of the high end technology and cryptography, hard- and software is controlled by the US. Not because the US scientists are inventing more than ones from other countries, but because for centuries they were smart in detecting new promising technology and inventions worldwide. They took things serious, when all the other countries were sleeping. Who visited Gavin Andresen, because they wanted to know about this "Bitcoins"? Russians? Chinese? Germany? No! It was the US. If there is something new, they will want to know about it. If it is either helpful or a thread for the national security, they will take it over with the necessary force. |
|
|
|
BitMos
Full Member
  
 Offline Offline
Activity: 182
Merit: 123
"PLEASE SCULPT YOUR SHIT BEFORE THROWING. Thank U"

|
 |
February 19, 2015, 09:08:25 AM |
|
Scary. But i wonder how this is possible since each hard disk manufacturer had their own proprietary hard drives' source code which mean they have to gain access one by one to insert the program.
They dump, reverse analyse and patch it , NSA have the so far the best reverse/hacker, they do not need source ! bahh bahh... nice words... not paid? |
money is faster...
|
|
|
bryant.coleman
Legendary

 Offline Offline
Activity: 3668
Merit: 1217

|
 |
February 19, 2015, 09:10:09 AM |
|
lol... soon we can expect new sanctions on Kaspersky Lab from both the United States and the European Union. Most probably, they will put Eugene Kaspersky in the blacklist as well.  |
|
|
|
|
BitMos
Full Member
  
 Offline Offline
Activity: 182
Merit: 123
"PLEASE SCULPT YOUR SHIT BEFORE THROWING. Thank U"

|
 |
February 19, 2015, 10:11:56 AM |
|
lol... soon we can expect new sanctions on Kaspersky Lab from both the United States and the European Union. Most probably, they will put Eugene Kaspersky in the blacklist as well.  I like your sense of humors  , but if mr Kaspersky shares is daughter it will be good as it never happened  . |
money is faster...
|
|
|
Balthazar
Legendary

 Offline Offline
Activity: 3108
Merit: 1358

|
 |
February 19, 2015, 10:28:34 AM |
|
Scary. But i wonder how this is possible since each hard disk manufacturer had their own proprietary hard drives' source code which mean they have to gain access one by one to insert the program.
They dump, reverse analyse and patch it , NSA have the so far the best reverse/hacker, they do not need source ! Ahaha, it was expectable that real maidummie should be a lamer as well. You'll be surprised but I don't need a source to add new section into executable module. Nobody needs that. Now you're free to continue coal transportation... C'mon, is there any limit for your dumbness? I've lost count of absurd statements which you did.   |
|
|
|
|
Nemo1024
Legendary

 Offline Offline
Activity: 1680
Merit: 1014


|
 |
February 21, 2015, 05:30:19 PM |
|
|
“Dark times lie ahead of us and there will be a time when we must choose between what is easy and what is right.”
“We are only as strong as we are united, as weak as we are divided.”
“It is important to fight and fight again, and keep fighting, for only then can evil be kept at bay, though never quite eradicated.”
|
|
|
BitMos
Full Member
  
 Offline Offline
Activity: 182
Merit: 123
"PLEASE SCULPT YOUR SHIT BEFORE THROWING. Thank U"

|
 |
February 21, 2015, 05:31:56 PM
Last edit: February 21, 2015, 07:48:11 PM by BitMos |
|
we all know that all the us media serve the actual admin, as such this admin as attacked repeatedly the nsa, q: in which camp is the NSA? that would be insane China+Japan+Russia+NSA vs the rest... lol. I love asymmetrical warfare  . but it would a pleasure be to see the nsa stay in the other camp, as I told what ever, any ways. edit: my sincere apologize to all the Russian Services assuring the protection of eddy the rogue. the nsa is fully in bed with the masson to enslave the world. they haven't show me a single proof of their will to work for a more peaceful world. let's hash them. one day their algos, when they will reach consciousness will kill them all anyway. traitors, like the rest of the usmiic. fuck you all. never have helped, only enslaved, or faked it to try to manipulate, but against the path it was futile since the beginning. Long live those that assure a secure Russian Federation against those subhumans, be aware, they are as vicious as it can be made by humans, ie nothing dangerous for the FALLEN ONES, our toy boys, sold souls so easy to play with. |
money is faster...
|
|
|
|
matrix zion
|
 |
February 22, 2015, 03:45:08 AM |
|
how to wipe it out of the firmware ?
|
|
|
|
|
|



