ChartBuddy
Legendary

 Offline Offline
Activity: 2156
Merit: 1745
1CBuddyxy4FerT3hzMmi1Jz48ESzRw1ZzZ

|
 |
September 09, 2023, 05:01:18 AM |
|
 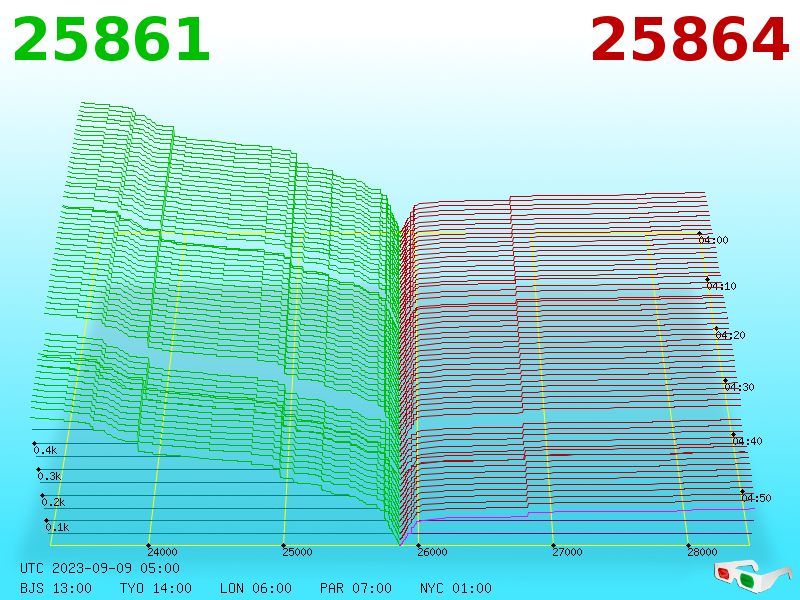 Explanation ExplanationChartbuddy thanks talkimg.com |
|
|
|
|
|
|
|
"If you don't want people to know you're a scumbag then don't be a scumbag." -- margaritahuyan
|
|
|
Advertised sites are not endorsed by the Bitcoin Forum. They may be unsafe, untrustworthy, or illegal in your jurisdiction.
|
|
|
ChartBuddy
Legendary

 Offline Offline
Activity: 2156
Merit: 1745
1CBuddyxy4FerT3hzMmi1Jz48ESzRw1ZzZ

|
 |
September 09, 2023, 06:01:21 AM |
|
 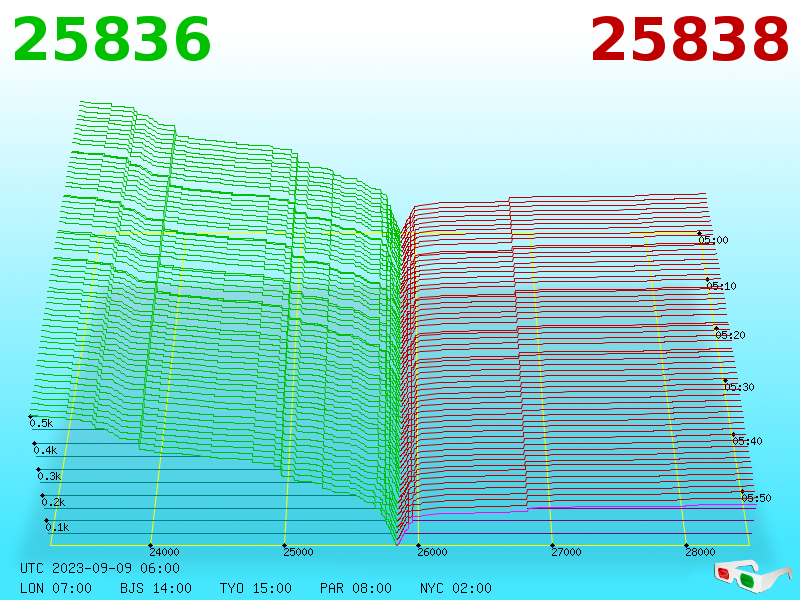 Explanation ExplanationChartbuddy thanks talkimg.com |
|
|
|
|
ChartBuddy
Legendary

 Offline Offline
Activity: 2156
Merit: 1745
1CBuddyxy4FerT3hzMmi1Jz48ESzRw1ZzZ

|
 |
September 09, 2023, 07:01:18 AM |
|
  Explanation ExplanationChartbuddy thanks talkimg.com |
|
|
|
|
ChartBuddy
Legendary

 Offline Offline
Activity: 2156
Merit: 1745
1CBuddyxy4FerT3hzMmi1Jz48ESzRw1ZzZ

|
 |
September 09, 2023, 08:01:18 AM |
|
  Explanation ExplanationChartbuddy thanks talkimg.com |
|
|
|
|
DirtyKeyboard
Sr. Member
   
 Online Online
Activity: 252
Merit: 459
Fly free sweet Mango.

|
 |
September 09, 2023, 08:22:32 AM Merited by JayJuanGee (1) |
|
Thank you Lucius for all the Trezor information and links! Got some work to do this weekend. Regarding maker/taker fees. Does anyone have a favorite exchange to recommend? Looks like Kraken is the one? I've heard good things, but personally use Gemini and have had no problems. It looks like Coinbase for 30 day volume VOLUME TIER TAKER FEE MAKER FEE Up to $10k 0.60% 0.40% $10k - $50k 0.40% 0.25% $50k - $100k 0.25% 0.15% For Kraken $0 - $50,000 0.16% 0.26% $50k-100k 0.14% 0.24% For Gemini 0 0.40% 0.20% ≥ $10,000 0.30% 0.10% ≥ $50,000 0.25% 0.10% ≥ $100,000 0.20% 0.08% So, using the median exchange, I guess if you are buying $100 at market 0.4% one is only getting $99.60 worth of btc vs a limit buy at 0.2% for $99.80 worth. Not too much difference I suppose. links: https://pro.coinbase.com/feeshttps://www.kraken.com/features/fee-schedulehttps://www.gemini.com/fees/activetrader-fee-schedule#section-active-trader-fee-schedule |
|
|
|
|
|
_Hiloveua_
|
 |
September 09, 2023, 08:29:03 AM |
|
The first early #Bitcoin top of the cycle is now in 31.9k (yellow dot) according to my Halving cycles Theory. These tops come every cycle in green accumulation year (after green vertical line) +/- 21 days from the date of the second halving, July 9th. The first early top is typically the most aggressive, seeing pretty major decline in most cases. There will probably be some time to go before rally resumes. The second early top will take place +/- 21 days from July 9th, 2024. Now is the time to be patient for price to pivot and enjoy the accumulation prices of green year! https://twitter.com/CryptoCon_/status/1700136732820148687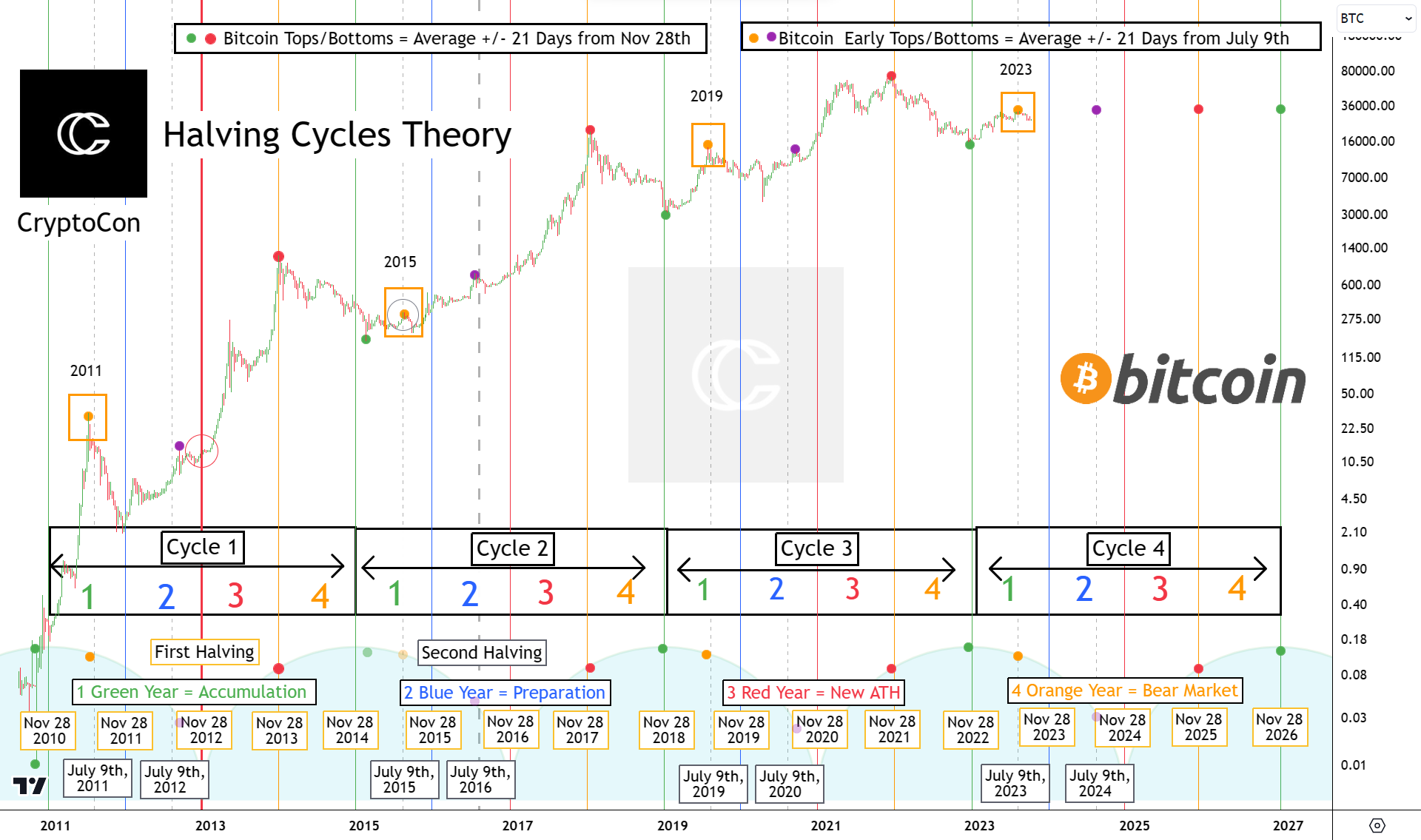 |
|
|
|
|
ChartBuddy
Legendary

 Offline Offline
Activity: 2156
Merit: 1745
1CBuddyxy4FerT3hzMmi1Jz48ESzRw1ZzZ

|
 |
September 09, 2023, 09:01:21 AM |
|
  Explanation ExplanationChartbuddy thanks talkimg.com |
|
|
|
|
nutildah
Legendary

 Offline Offline
Activity: 2968
Merit: 7952


|
 |
September 09, 2023, 09:55:12 AM |
|
Cmon bro you literally just copy pasted a tweet and are presenting it as original thought in an attempt to get merits. Its borderline plagiarism. Next time quote the text from the tweet. So lazy. |
|
|
|
|
ChartBuddy
Legendary

 Offline Offline
Activity: 2156
Merit: 1745
1CBuddyxy4FerT3hzMmi1Jz48ESzRw1ZzZ

|
 |
September 09, 2023, 10:01:19 AM |
|
  Explanation ExplanationChartbuddy thanks talkimg.com |
|
|
|
|
Lucius
Legendary

 Offline Offline
Activity: 3220
Merit: 5634
Blackjack.fun-Free Raffle-Join&Win $50🎲


|
 |
September 09, 2023, 10:47:39 AM |
|
I still have problems with the need for 37 random characters for the 25th word.. and let's say if someone just has 10-15 somewhat random characters, then how long is it going to take to break into the Trezor?
I think a lot of confusion has arisen about how strong a passphrase should be to protect someone's seed in case someone comes into physical possession and tries to extract the seed. What someone wanted to emphasize is that a passphrase of at least 37 random characters would provide the same level of protection as the seed itself (24 words) and is practically impossible to brute force, but that does not mean that 10+ characters are not resistant to brute force. We can always check how long it actually takes to brute force a password on sites like https://www.passwordmonster.comOnly 9 characters in this password makes it virtually impossible to brute force -> 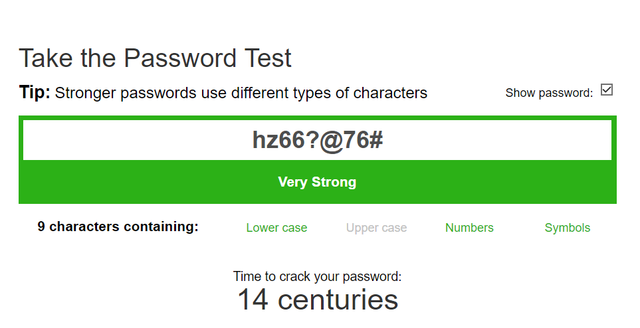 By the way, we have a long term member in these here parts that swears by that piece of crap, aka Ledger, and surely there are probably quite a few members who may or may not be in the closest about their use (and apparent belief) in the Ledger crap.
Ledger does not have the problems that Trezor has, but if we take into account that a few years ago almost the entire database of users with all the data was hacked, and that a few months ago they announced the revolutionary "seed recovery" service, they shot themselves in the knee by giving the possibility at all to one such device shares the user's seed with as many as three different companies. Of course, the service is optional and you pay $9.99 per month, but when someone does something completely contrary to what they have been advocating for years, I wonder how to trust such a company. Oh I see that the 39+ pin is different from the extra word...and that 39 character pin would resolve the other issue regarding a hacker getting ahold of the physical device and breaking into it.. so that still leaves the issue of the 13th or 25th word actually not needing to be very complicated, and a 8-15 character passphrase may well make it quite difficult to get at the wallet because they would first need to know (or suspect) that such a wallet (or extra portal to a wallet) actually exists in connection with the 12 or 24 word seed that was extracted from the device.
As I already wrote, I think that the passphrase I mentioned above is more than enough if we take into account today's computers and the time it would take for someone to brute force such a password. Of course, the whole thing doesn't matter at all if someone who knows what he's doing doesn't get hold of our hardware wallet. Speaking of how to take care of our hardware devices, I always remember an interesting film on that very topic - it's worth watching if you haven't seen it already. https://www.youtube.com/watch?v=hf97ofTlZhk (Schloss Bitcoin (2020) - deutscher Kurzfilm - Crime Black Comedy Subtitles in English, French & more) |
|
|
|
|
ChartBuddy
Legendary

 Offline Offline
Activity: 2156
Merit: 1745
1CBuddyxy4FerT3hzMmi1Jz48ESzRw1ZzZ

|
 |
September 09, 2023, 11:01:19 AM |
|
  Explanation ExplanationChartbuddy thanks talkimg.com |
|
|
|
|
shahzadafzal
Copper Member
Legendary

 Offline Offline
Activity: 1526
Merit: 2890

|
 |
September 09, 2023, 11:39:46 AM |
|
Technically he’s HODLing  |
|
|
|
|
ChartBuddy
Legendary

 Offline Offline
Activity: 2156
Merit: 1745
1CBuddyxy4FerT3hzMmi1Jz48ESzRw1ZzZ

|
 |
September 09, 2023, 12:01:22 PM |
|
 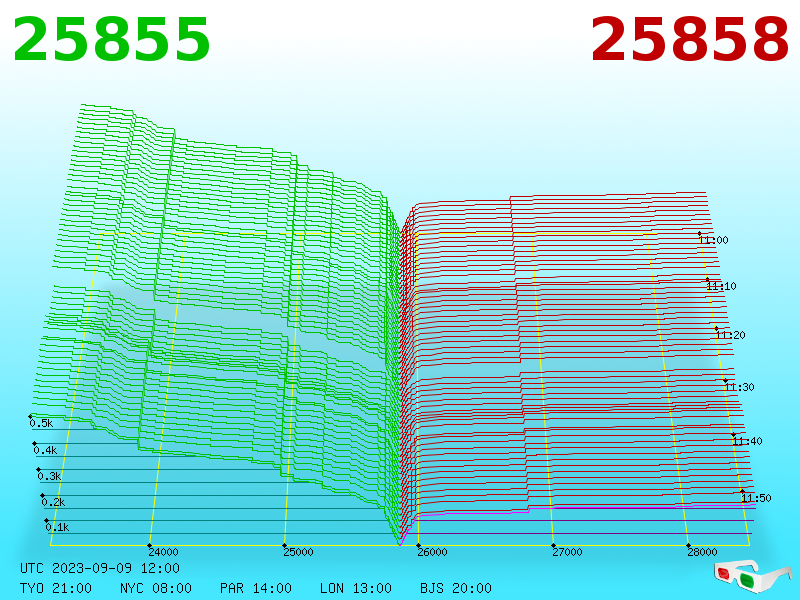 Explanation ExplanationChartbuddy thanks talkimg.com |
|
|
|
|
AlcoHoDL
Legendary

 Offline Offline
Activity: 2352
Merit: 4145
Addicted to HoDLing!

|
I still have problems with the need for 37 random characters for the 25th word.. and let's say if someone just has 10-15 somewhat random characters, then how long is it going to take to break into the Trezor?
I think a lot of confusion has arisen about how strong a passphrase should be to protect someone's seed in case someone comes into physical possession and tries to extract the seed. What someone wanted to emphasize is that a passphrase of at least 37 random characters would provide the same level of protection as the seed itself (24 words) and is practically impossible to brute force, but that does not mean that 10+ characters are not resistant to brute force. We can always check how long it actually takes to brute force a password on sites like https://www.passwordmonster.comOnly 9 characters in this password makes it virtually impossible to brute force ->  By the way, we have a long term member in these here parts that swears by that piece of crap, aka Ledger, and surely there are probably quite a few members who may or may not be in the closest about their use (and apparent belief) in the Ledger crap.
Ledger does not have the problems that Trezor has, but if we take into account that a few years ago almost the entire database of users with all the data was hacked, and that a few months ago they announced the revolutionary "seed recovery" service, they shot themselves in the knee by giving the possibility at all to one such device shares the user's seed with as many as three different companies. Of course, the service is optional and you pay $9.99 per month, but when someone does something completely contrary to what they have been advocating for years, I wonder how to trust such a company. Oh I see that the 39+ pin is different from the extra word...and that 39 character pin would resolve the other issue regarding a hacker getting ahold of the physical device and breaking into it.. so that still leaves the issue of the 13th or 25th word actually not needing to be very complicated, and a 8-15 character passphrase may well make it quite difficult to get at the wallet because they would first need to know (or suspect) that such a wallet (or extra portal to a wallet) actually exists in connection with the 12 or 24 word seed that was extracted from the device.
As I already wrote, I think that the passphrase I mentioned above is more than enough if we take into account today's computers and the time it would take for someone to brute force such a password. Of course, the whole thing doesn't matter at all if someone who knows what he's doing doesn't get hold of our hardware wallet. Speaking of how to take care of our hardware devices, I always remember an interesting film on that very topic - it's worth watching if you haven't seen it already. https://www.youtube.com/watch?v=hf97ofTlZhk (Schloss Bitcoin (2020) - deutscher Kurzfilm - Crime Black Comedy Subtitles in English, French & more) Good post. That was my point in my earlier post about giving ourselves enough time to restore the seed to another device and transfer the coins to another wallet, unknown to the thief. Practically, one needs just a few days/weeks of time, and in most cases the theft can be discovered immediately after the fact, so the transfer can be done in the first 24 hours. This means that the thief has to have a pretty powerful computer rig to be able to brute force a passphrase of 10+ ASCII characters in 24 hours, or even a week or a month. I've tested variations of my passphrase (even shorter versions of it) in several different, and well-respected, passphrase strength testers, and they all report a crack time of centuries! Another thing to note is that the attacker does not have an immediate indication that the correct passphrase was found, because ALL possible passphrases (even "wrong" ones) result in valid (albeit empty) wallets. So, the attacker will need to check the blockchain against ALL passphrase candidates, and reject those that result in empty wallets. I'm quite confident that even a modest, few-characters-only passphrase should be able to stall even the seasoned thief for sufficient time for us to transfer our coins to a fresh wallet. Using a 128-bit entropy PIN or passphrase is surely the safest option, but greatly reduces the usability of the wallet, as Jay has pointed out. Furthermore, using such a humongously long/complex PIN/passphrase, you run the risk of "locking yourself out" of your wallet, because you may forget part of it, which may prompt you to write it down somewhere, thereby defeating the purpose of using a PIN/passphrase in the first place. I particularly liked vapourminer's "Trezor wipe-restore" method. Never thought of it, and it does make sense for those not using their Trezors often (myself included). It's a trade-off, with potentially dire consequences at either extreme. I choose the middle ground, i.e., a PIN and passphrase that are complex enough to deter even a seasoned thief/hacker, but memorable enough to reside in the neurons of my brain -- that last part could potentially be dangerous in case of amnesia or head injury. I'm glad we're having this discussion, it certainly helps us all be more aware of the potential dangers and act accordingly. |
|
|
|
|
ChartBuddy
Legendary

 Offline Offline
Activity: 2156
Merit: 1745
1CBuddyxy4FerT3hzMmi1Jz48ESzRw1ZzZ

|
 |
September 09, 2023, 01:01:18 PM |
|
  Explanation ExplanationChartbuddy thanks talkimg.com |
|
|
|
|
xhomerx10
Legendary

 Offline Offline
Activity: 3822
Merit: 7972

|
 |
September 09, 2023, 01:56:58 PM Merited by JayJuanGee (1) |
|
I grabbed some silver.
I am stacking more btc.
Why silver? Physical silver comes at a premium you can't recover - it's nearly CA$10 an ounce on ounce coins right now (25%) and you'll get spot when you sell unless you're brave enough to do it privately but it's not worth the risk imo. Are you a closet prepper Phil? |
|
|
|
|
ChartBuddy
Legendary

 Offline Offline
Activity: 2156
Merit: 1745
1CBuddyxy4FerT3hzMmi1Jz48ESzRw1ZzZ

|
 |
September 09, 2023, 02:01:18 PM |
|
  Explanation ExplanationChartbuddy thanks talkimg.com |
|
|
|
|
bitebits
Legendary

 Offline Offline
Activity: 2211
Merit: 3178
Flippin' burgers since 1163.

|
 |
September 09, 2023, 02:26:21 PM Merited by JayJuanGee (1) |
|
So not bragging about your holdings is another easy security layer.
Part of the reason why 0.63 BTC will have to be downgraded, at some point. @AlcoHoDL, Trezor vulnerability is something that has been known for years, there was a lot of discussion about it in the technical discussion boards, but luckily every user can protect himself by setting a passphrase, and there is also another option, which is the use of an SD card. When it comes to passphrase, the conclusion is that they should be at least 37 characters long : A physical access to a Trezor One, Trezor T, Keepkey, or B-wallet allows an attacker to extract the 12/24-words within a few minutes using a low-cost setup (~100$), with a very high reproducibility (we had 100% success). We finally proved it can be fully automated allowing anyone to use it in case someone would sell the Extraktor box (similar to old Playstation hacks). This attack can not be fixed. The only mitigation is to use a strong passphrase: we recommend 37 random characters to maintain the same level of security. For those who are interested in how to protect themselves additionally with the help of an SD card : Trezor T (2.3.0) and Trezor One (1.9.0) firmware updateAlso, one thing I forgot is that it is possible to set a so-called fake PIN that can be left as a bait, and if it is entered, all data from the hardware wallet will be deleted. The Wipe Code
Another exciting new feature is the wipe code that acts as a “self-destruct PIN” that erases your Trezor if someone tries to unlock your device without your consent. If the wipe code is entered into any PIN entry dialog, then all private data will be immediately erased from your Trezor and the device will be reset to factory defaults. You can write the wipe code somewhere near your Trezor as a decoy PIN, so if someone tries to unlock the device without your consent, they will cause it to erase itself. You can also use the wipe code to reset your Trezor without using a host device. This update can be enabled on both Trezor models. A 128 bits PIN should do the trick as well, as it is used to encrypt the seed on the chip. (Please let me know if you think I'm wrong) I still have problems with the need for 37 random characters for the 25th word.. and let's say if someone just has 10-15 somewhat random characters, then how long is it going to take to break into the Trezor? Remember each time that we log into the device and sometimes we might get disconnected and have to log in again, it can take quite a bit of time to be logging in these 37 random characters each time... I am not going to say how many digits that I actually use, and I also am not going to give any hints either... and it is bad enough that I said that I use such a device, in theory. By the way, we have a long term member in these here parts that swears by that piece of crap, aka Ledger, and surely there are probably quite a few members who may or may not be in the closest about their use (and apparent belief) in the Ledger crap. ~snip~
A 128 bits PIN should do the trick as well, as it is used to encrypt the seed on the chip.
(Please let me know if you think I'm wrong)
You are definitely right, considering that I am not a user of Trezor, I was not even aware that in 2021 they increased the maximum PIN length to even 50 digits, and they say that 39 digits is quite enough to protect the seed from hacking. It's actually a good thing for those who for some reason don't want to use a passphrase or maybe don't even know such an option exists - although it's an option they always recommend to advanced users. Everyone should use the passphrase.. and it should not be considered advanced... and maybe using 37 random characters might be considered advanced. But I still wonder if a relatively short password might just be considered a less advance version. and is better than no password at all.. so why do we have to have a need to overly complicate matters by suggesting so much complication, when surely it must add quite a bit of difficulty to just have a shorter 25th word in there (or 13th word seems to be more standard) rather than no extra word (passphrase) at all. In other words, why let the perfect be the enemy of the good? We have a lot of cases where users wonder why they don't see anything on their balance even though they have the correct seed, and then it turns out that they actually added an extra password without which the seed creates a completely new set of addresses.
It might be a bit impractical to enter a PIN that's 39+ digits long, but for the average user it's probably easier than setting a passphrase.
Oh I see that the 39+ pin is different from the extra word...and that 39 character pin would resolve the other issue regarding a hacker getting ahold of the physical device and breaking into it.. so that still leaves the issue of the 13th or 25th word actually not needing to be very complicated, and a 8-15 character passphrase may well make it quite difficult to get at the wallet because they would first need to know (or suspect) that such a wallet (or extra portal to a wallet) actually exists in connection with the 12 or 24 word seed that was extracted from the device. Some thoughts: If nobody can access your seed your won't need any passphrase, if the seed was created with sufficient entropy ...which should always be questionable though! Also, you are right, even a short passphrase will leave anyone who gets your seed in doubt if there even is a hidden passphrase wallet and if it makes sense to put in the work to look brute force for any. A 128 bits phrase can secure your seed with the same security the seed secures your BTC, if that's what you want/need for ease of mind. Nice thing: totally independent from all that passphrase science is the PIN which can secure your Trezor 100% against seed extraction from the open source chip. If the PIN is strong enough, your device will be worthless to any attacker. Multisig solves a lot of potential security issues without making things complex (which is a security issue by itself). It really should be the standard in case of managing anything else than pocket change. |
|
|
|
|
ChartBuddy
Legendary

 Offline Offline
Activity: 2156
Merit: 1745
1CBuddyxy4FerT3hzMmi1Jz48ESzRw1ZzZ

|
 |
September 09, 2023, 03:01:23 PM |
|
  Explanation ExplanationChartbuddy thanks talkimg.com |
|
|
|
|
philipma1957
Legendary

 Offline Offline
Activity: 4102
Merit: 7815
'The right to privacy matters'


|
 |
September 09, 2023, 03:08:41 PM |
|
I grabbed some silver.
I am stacking more btc.
Why silver? Physical silver comes at a premium you can't recover - it's nearly CA$10 an ounce on ounce coins right now (25%) and you'll get spot when you sell unless you're brave enough to do it privately but it's not worth the risk imo. Are you a closet prepper Phil? I buy from sellers I know on btc talk I grabbed 40 oz for 988. which is 24.65 an oz just A bit over spot. I am looking to have four investments silver btc fed bonds real estate. I do have some of each along with mining income and pensions. |
|
|
|
|
|




 Poll
Poll
