|
Frizz23 (OP)
|
 |
September 09, 2013, 08:54:33 PM |
|
"SHA-2 is a set of cryptographic hash functions (SHA-224, SHA-256, SHA-384, SHA-512) designed by the U.S. National Security Agency (NSA) ..." ( http://en.wikipedia.org/wiki/SHA-2) Every day we hear new news that the NSA is able to spy on us - and hack or bypass SSL, SSH, PGP, etc. Sometimes because they use backdoors that they have installed themselves. "Planted" weaknesses into systems. What's the probability that the NSA also designed some "flaws" into the SHA-2 algorithm? |
Ξtherization⚡️First P2E 2016⚡️🏰💎🌈 etherization.org
|
|
|
|
|
|
|
|
|
|
"Governments are good at cutting off the heads of a centrally
controlled
networks like Napster, but pure P2P networks like Gnutella and Tor seem
to be holding their own." -- Satoshi
|
|
|
Advertised sites are not endorsed by the Bitcoin Forum. They may be unsafe, untrustworthy, or illegal in your jurisdiction.
|
|
|
|
|
shadizzle
Newbie

 Offline Offline
Activity: 56
Merit: 0

|
 |
September 09, 2013, 09:03:07 PM |
|
Id say so, why not?
It's finally public they have cracked and have backdoors in EVERY mobile device, anything you click on the net. etc..
|
|
|
|
|
acoindr
Legendary

 Offline Offline
Activity: 1050
Merit: 1002

|
 |
September 09, 2013, 09:04:37 PM |
|
SHA-2 is an open algorithm and it uses as its constants the sequential prime cube roots as a form of "nothing up my sleeve numbers". For someone to find a weakness or backdoor in SHA would be the equivalent of the nobel prize in cryptography. Everyone who is anyone in the cryptography community has looked at SHA-2. Not just everyone with a higher degree in mathematics, computer science, or cryptography in the last 20 years but foreign intelligence agencies and major financial institutions. Nobody has found a flaw, not even an theoretical one (a faster than brute force solution which requires so much energy/time as to be have no real world value).
To believe the the NSA has broken SHA-2 would be to believe that the NSA found something the entire rest of the world combined hasn't found for twenty years. Also NIST still considers SHA-2 secure and prohibits the use of any other hashing algorithm (to include SHA-3 so far) in classified networks. So that would mean the NSA is keeping a flaw/exploit from NIST compromising US national security.
Anything is possible but occam's razor and all that.
|
|
|
|
|
will1982
Member
 
 Offline Offline
Activity: 122
Merit: 10

|
 |
September 09, 2013, 09:06:47 PM |
|
It seems likely at this point, but there's no proof that they have.
|
|
|
|
|
|
|
DeathAndTaxes
Donator
Legendary

 Offline Offline
Activity: 1218
Merit: 1079
Gerald Davis

|
 |
September 09, 2013, 10:03:31 PM |
|
It seems likely at this point, but there's no proof that they have.
I would say it seems unlikely at this point however you can never prove a flaw (intentional or otherwise) doesn't exist. |
|
|
|
|
marcus_of_augustus
Legendary

 Offline Offline
Activity: 3920
Merit: 2348
Eadem mutata resurgo

|
 |
September 09, 2013, 10:23:21 PM |
|
It seems likely at this point, but there's no proof that they have.
I would say it seems unlikely at this point however you can never prove a flaw (intentional or otherwise) doesn't exist. They intentionally produce shit cryptography and go to great lengths to deceive (social attacks) ... why trust them in any regard, least of all in an "open science" forum format when there is no requirement to? It should be quite clear now to dump any crypto that the NSA has come anywhere near, and trust no-one that has had anything to do with them. That maybe a massive undertaking given how ubiquitous their grasping tentacles have become but it is the only right thing to do, probably safest also. |
|
|
|
ElectricMucus
Legendary

 Offline Offline
Activity: 1666
Merit: 1057
Marketing manager - GO MP


|
 |
September 09, 2013, 10:25:50 PM |
|
Oh look it's this thread again.
|
|
|
|
|
El Extranjero
Member
 
 Offline Offline
Activity: 103
Merit: 10

|
 |
September 09, 2013, 10:45:27 PM |
|
It seems likely at this point, but there's no proof that they have.
I would say it seems unlikely at this point however you can never prove a flaw (intentional or otherwise) doesn't exist. They intentionally produce shit cryptography and go to great lengths to deceive (social attacks) ... why trust them in any regard, least of all in an "open science" forum format when there is no requirement to? It should be quite clear now to dump any crypto that the NSA has come anywhere near, and trust no-one that has had anything to do with them. That maybe a massive undertaking given how ubiquitous their grasping tentacles have become but it is the only right thing to do, probably safest also. 100% Agree! |
|
|
|
DeathAndTaxes
Donator
Legendary

 Offline Offline
Activity: 1218
Merit: 1079
Gerald Davis

|
 |
September 09, 2013, 11:07:24 PM |
|
It seems likely at this point, but there's no proof that they have.
I would say it seems unlikely at this point however you can never prove a flaw (intentional or otherwise) doesn't exist. They intentionally produce shit cryptography and go to great lengths to deceive (social attacks) ... why trust them in any regard, least of all in an "open science" forum format when there is no requirement to? I don't trust the NSA. I trust the fact that: a) the algorithm is open b) the constants are sequential prime cuberoots rather than "random" c) the entire world community hasn't found a flaw. Compare that to the EC RNG which was recommended by the NSA. A single cryptographer found the flaw in the span of a few months despite it being rather than rare algorithm with no widespread usage. However the entire world community can't find a backdoor/flaw in an one of the most widely used hashing algorithms in the world? |
|
|
|
|
marcus_of_augustus
Legendary

 Offline Offline
Activity: 3920
Merit: 2348
Eadem mutata resurgo

|
 |
September 09, 2013, 11:25:35 PM
Last edit: September 09, 2013, 11:36:12 PM by marcus_of_augustus |
|
The algorithm is open ... however it was produced by a politically motivated rogue government branch that seems to harbouring a cynical bunch of criminal bastards ... do your own due diligence, if you don't have to deal with them why bother? Compare that to the EC RNG which was recommended by the NSA. A single cryptographer found the flaw in the span of a few months despite it being rather than rare algorithm with no widespread usage. However the entire world community can't find a backdoor/flaw in an one of the most widely used hashing algorithms in the world?
Edit: oops, forgot to point out that the NSA algos flaws/backdoors will be tailored towards cracking by hardware capabilities that they , and maybe only them, possess. So saying it is secure because no-one else has found a flaw is redundant since no-one else knows or can replicate what they are capable of in terms of mining the exploit ... |
|
|
|
DeathAndTaxes
Donator
Legendary

 Offline Offline
Activity: 1218
Merit: 1079
Gerald Davis

|
 |
September 09, 2013, 11:27:11 PM |
|
The algorithm is open ... however it was produced by a politically motivated government branch that seems to harbouring a cynical bunch of criminal bastards ... do your own due diligence, if you don't have to deal with them why bother?
Well we do have to "deal with SHA-2" as a change to a different hashing algorithm would be a hard fork and that isn't going to happen. |
|
|
|
|
ageisp0lis
Newbie

 Offline Offline
Activity: 38
Merit: 0


|
 |
September 10, 2013, 12:27:07 AM
Last edit: September 12, 2013, 09:00:02 PM by ageisp0lis |
|
|
|
|
|
|
Littleshop
Legendary

 Offline Offline
Activity: 1386
Merit: 1003


|
 |
September 10, 2013, 01:07:18 AM |
|
The algorithm is open ... however it was produced by a politically motivated government branch that seems to harbouring a cynical bunch of criminal bastards ... do your own due diligence, if you don't have to deal with them why bother?
Well we do have to "deal with SHA-2" as a change to a different hashing algorithm would be a hard fork and that isn't going to happen. Actually I believe it could happen. And it should happen if SHA-2 was compromised, that was always the plan but right now SHA-2 is NOT compromised. The NSA may have some shortcuts and could exploit random number generator issues (including backdoors in those) but a clear get the private key from the public one is not possible at this time. Changing the algo was ALWAYS planned in Bitcoin if it was compromised. |
|
|
|
Come-from-Beyond
Legendary

 Offline Offline
Activity: 2142
Merit: 1009
Newbie

|
 |
September 10, 2013, 03:51:25 AM |
|
However the entire world community can't find a backdoor/flaw in an one of the most widely used hashing algorithms in the world?
NSA can afford to hire the best mathematicians. Nowadays when one of them devises something only a few people are able to understand the mathematical proof it's based on. A flaw could exist for decades/centuries before someone else find it by accident. |
|
|
|
|
|
MoneyMorpheus
|
 |
September 10, 2013, 06:08:52 AM |
|
The algorithm is open ... however it was produced by a politically motivated government branch that seems to harbouring a cynical bunch of criminal bastards ... do your own due diligence, if you don't have to deal with them why bother?
Well we do have to "deal with SHA-2" as a change to a different hashing algorithm would be a hard fork and that isn't going to happen. Actually I believe it could happen. And it should happen if SHA-2 was compromised, that was always the plan but right now SHA-2 is NOT compromised. The NSA may have some shortcuts and could exploit random number generator issues (including backdoors in those) but a clear get the private key from the public one is not possible at this time. Changing the algo was ALWAYS planned in Bitcoin if it was compromised. You do realize what a change in algo would mean? All the asics will become paperweights and the network will go back to gpu mining. Leaving the network less protected for the NSA or a third party to do a 51% attack. Not to mention all the asic manufacturers will bankrupt... It is possible, but the consequences will be huge... I think though that even if bitcoin is cracked by the nsa, they will not bring it down. They will exploit such crack in their benefit. Just remember governments don't destroy assets or money, they confiscate it. They will even try to make it look like they seized the btc by other means, making their backdoor last for as long as they can. Whats the point in investing millions on cracking a cryptocurrency in order to kill it and let the next one arise and start all over again? Greediness and power are two important factors in conspiracy theories. The NSA cracking btc to kill it lacks both... But then again that is just my theory... |
|
|
|
Dabs
Legendary

 Offline Offline
Activity: 3416
Merit: 1912
The Concierge of Crypto

|
 |
September 10, 2013, 06:18:53 AM |
|
Imagine, Satoshi has a million or two coins stashed on a bunch of private keys that have never moved since being mined. Those 50 BTC will be the target.
|
|
|
|
|
Frizz23 (OP)
|
 |
September 10, 2013, 08:00:20 AM |
|
Well we do have to "deal with SHA-2" as a change to a different hashing algorithm would be a hard fork and that isn't going to happen.
But it would kill two birds with one stone. 1) The ASIC madness would stop 2) The NSA algorithm would be gone. By the way: What might have been the reason that Mr. Nakamoto decided to use an NSA algorithm (SHA-256) for Bitcoin? |
Ξtherization⚡️First P2E 2016⚡️🏰💎🌈 etherization.org
|
|
|
dragonkid
Member
 
 Offline Offline
Activity: 84
Merit: 10

|
 |
September 10, 2013, 08:05:22 AM |
|
I don't trust the NSA. I trust the fact that:
a) the algorithm is open
b) the constants are sequential prime cuberoots rather than "random"
c) the entire world community hasn't found a flaw.
Compare that to the EC RNG which was recommended by the NSA. A single cryptographer found the flaw in the span of a few months despite it being rather than rare algorithm with no widespread usage. However the entire world community can't find a backdoor/flaw in an one of the most widely used hashing algorithms in the world?
That is why I only use Linux, and open source. |
|
|
|
|
operrajunk74
|
 |
September 10, 2013, 08:14:16 AM |
|
c) the entire world community hasn't found a flaw.
If another non US agency found a flaw, why would they publish it instead of use it for their advantage? |
|
|
|
|
ShadowOfHarbringer
Legendary

 Offline Offline
Activity: 1470
Merit: 1005
Bringing Legendary Har® to you since 1952

|
 |
September 10, 2013, 08:45:35 AM |
|
The algorithm is open ... however it was produced by a politically motivated rogue government branch that seems to harbouring a cynical bunch of criminal bastards ... do your own due diligence, if you don't have to deal with them why bother?
Don't forget that the Internet and TOR were also started by the US military. Just the fact that they did something does not mean that they still have control over it. Edit: oops, forgot to point out that the NSA algos flaws/backdoors will be tailored towards cracking by hardware capabilities that they , and maybe only them, possess. So saying it is secure because no-one else has found a flaw is redundant since no-one else knows or can replicate what they are capable of in terms of mining the exploit ...
Flaws in one of most widely used algos would be quickly found by NSA's/USA enemies - such as China and Russia (Russia/China have some of the world brightest mathematicans & cryptographers). Especially after the Prism scandal. Hiding something like this is simply not possible in after-Prism paranoia world. |
|
|
|
|
Jace
|
 |
September 10, 2013, 08:51:07 AM |
|
NSA can afford to hire the best mathematicians. Nowadays when one of them devises something only a few people are able to understand the mathematical proof it's based on. A flaw could exist for decades/centuries before someone else find it by accident. It could, yes, hypothetically. But it's extremely unlikely. Chances are slim to none. There is a much, MUCH larger group of extremely talented mathematicians out there than the NSA has employed. Oh, and in the VERY unlikely (and purely theoretical) scenario that the NSA does indeed have some sort of edge on SHA-256, we can still keep our peace of mind knowing that fortunately, Bitcoin uses double (nested) SHA-256. |
Feel free to send your life savings to 1JhrfA12dBMUhcgh85wYan6HL2uLQdB6z9
|
|
|
|
|
|
miztaziggy
|
 |
September 10, 2013, 11:20:20 AM |
|
Why is everyone so certain that the 'entire world community' has looked at this encryption and hasn't found a flaw? I don't understand the mathematics in this but: http://eprint.iacr.org/2008/270.pdfNow, this looks like it's been done by a university in India. My guess is that the NSA and other world intelligence agencies employ the very best of the best mathematicians. They will scour universities and pick up the top students early on. Their work won't be published like this was. It will be kept secret and the world will think that it's secure. Why would the NSA ever release a 'secure' algorithm? It's like shooting yourself in the foot, it would make their job so much harder. They would only ever release something that they could control. It's just the way the world works. |
*Image Removed*
|
|
|
|
Galahad
|
 |
September 10, 2013, 12:38:46 PM |
|
Why would the NSA ever release a 'secure' algorithm? It's like shooting yourself in the foot, it would make their job so much harder. They would only ever release something that they could control. It's just the way the world works.
Because it's public domain and the best experts in cryptography in the world have worked on it, tested it and found no flaw. Also, the NSA themselves rely on this encryption, do they want their secrets revealed? |
|
|
|
|
|
miztaziggy
|
 |
September 10, 2013, 12:56:59 PM |
|
Why would the NSA ever release a 'secure' algorithm? It's like shooting yourself in the foot, it would make their job so much harder. They would only ever release something that they could control. It's just the way the world works.
Because it's public domain and the best experts in cryptography in the world have worked on it, tested it and found no flaw. Also, the NSA themselves rely on this encryption, do they want their secrets revealed? Are you really that naive? |
*Image Removed*
|
|
|
|
Galahad
|
 |
September 10, 2013, 01:18:15 PM |
|
Are you really that naive?
Do you underestimate the brightest minds in the world? Do you believe that the minds in the NSA are somehow brighter than those outside of it? |
|
|
|
|
DeathAndTaxes
Donator
Legendary

 Offline Offline
Activity: 1218
Merit: 1079
Gerald Davis

|
 |
September 10, 2013, 01:31:10 PM |
|
By the way: What might have been the reason that Mr. Nakamoto decided to use an NSA algorithm (SHA-256) for Bitcoin?
The same reason that banks, the US government, foreign governments, millions of websites, the SSL protocol, PGP, and other secure systems use it. It is the most widely studied and analyzed algorithms in the last twenty years. It has held up to extensive public scrutiny and been shown to be a strong hashing function. |
|
|
|
|
DeathAndTaxes
Donator
Legendary

 Offline Offline
Activity: 1218
Merit: 1079
Gerald Davis

|
 |
September 10, 2013, 01:39:40 PM |
|
Why would the NSA ever release a 'secure' algorithm? It's like shooting yourself in the foot, it would make their job so much harder. They would only ever release something that they could control. It's just the way the world works.
Because you can never definitively prove a cryptographic system is secure. The only way to "know" a cipher is secure is to make it publicly available and let the best in the world take a crack at it. It is very easy to write a cryptographic system that you yourself can't break but that is next to useless. Secret cryptography usually is weak cryptography. History is littered with examples of failed "strong" systems. One classic one is WEP which is so unbelievably broken it is hard to believe cryptographers came up with it. Security through obscurity doesn't work. Had the specs for WEP been made publicly available in the design phase people would have found the flaws in a matter of weeks and saved everyone a ton of problems down the road. For every good cipher there are dozens and dozens of flawed ones. No matter how smart a single developer is the combined intellect of the planet is better, that is the entire rationale for open source. The NSA is not only responsible for finding the secrets of others they are responsible for ensuring others don't find the secrets of the United States. The US government uses SHA-2 in secure cryptographic systems including SIPERNet. I know this from personal experience. |
|
|
|
|
ShadowOfHarbringer
Legendary

 Offline Offline
Activity: 1470
Merit: 1005
Bringing Legendary Har® to you since 1952

|
 |
September 10, 2013, 01:51:35 PM |
|
Why would the NSA ever release a 'secure' algorithm? It's like shooting yourself in the foot, it would make their job so much harder. They would only ever release something that they could control. It's just the way the world works.
Because you can never definitively prove a cryptographic system is secure. The only way to "know" a cipher is secure is to make it publicly available and let the best in the world take a crack at it. It is very easy to write a cryptographic system that you yourself can't break but that is next to useless. Secret cryptography usually is weak cryptography. History is littered with examples of failed "strong" systems. One classic one is WEP which is so unbelievably broken it is hard to believe cryptographers came up with it. Security through obscurity doesn't work. Had the specs for WEP been made publicly available in the design phase people would have found the flaws in a matter of weeks and saved everyone a ton of problems down the road. For every good cipher there are dozens and dozens of flawed ones. No matter how smart a single developer is the combined intellect of the planet is better, that is the entire rationale for open source. The NSA is not only responsible for finding the secrets of others they are responsible for ensuring others don't find the secrets of the United States. This is probably the most wise & complete explanation of "why there is no backdoor in SHA-2" that we will come up with here. This topic could be now closed for all I care. |
|
|
|
|
miztaziggy
|
 |
September 10, 2013, 01:53:22 PM |
|
Are you really that naive?
Do you underestimate the brightest minds in the world? Do you believe that the minds in the NSA are somehow brighter than those outside of it? So what evidence do you have that the brightest minds in the world are not in these government agencies? A friend of mine's son has studied maths at Cambridge in the UK, he is now doing a PHD over in the US at MIT. She had her son's friend stay with her over the holiday, and told me that this girl was also studying for a PHD also. This girl is apparently ridiculously intelligent, to the point of being autistic, she has no social skills. She has already been approached by GCHQ and has done a summer placement there. She has been offered a place after completing her PHD. That's what happens in the real world, these ultra bright kids will be snapped up by places like GCHQ and NSA before they are 21, but, this forum is just like a hollow box where you all like to shout about the positives of bitcoin without ever considering the real world, so I guess none of this matters. |
*Image Removed*
|
|
|
|
Galahad
|
 |
September 10, 2013, 02:46:47 PM |
|
So what evidence do you have that the brightest minds in the world are not in these government agencies?
They will also be working in the open source community rather than exclusively in one place because they are passionate about the subject. Why would the NSA ever release a 'secure' algorithm? It's like shooting yourself in the foot, it would make their job so much harder. They would only ever release something that they could control. It's just the way the world works.
Because you can never definitively prove a cryptographic system is secure. The only way to "know" a cipher is secure is to make it publicly available and let the best in the world take a crack at it. It is very easy to write a cryptographic system that you yourself can't break but that is next to useless. Secret cryptography usually is weak cryptography. History is littered with examples of failed "strong" systems. One classic one is WEP which is so unbelievably broken it is hard to believe cryptographers came up with it. Security through obscurity doesn't work. Had the specs for WEP been made publicly available in the design phase people would have found the flaws in a matter of weeks and saved everyone a ton of problems down the road. For every good cipher there are dozens and dozens of flawed ones. No matter how smart a single developer is the combined intellect of the planet is better, that is the entire rationale for open source. The NSA is not only responsible for finding the secrets of others they are responsible for ensuring others don't find the secrets of the United States. This is probably the most wise & complete explanation of "why there is no backdoor in SHA-2" that we will come up with here. This topic could be now closed for all I care. Thank you. I couldn't properly express why he was wrong so I was waiting for more sane people to get here. Please close topic! |
|
|
|
|
cypherdoc
Legendary

 Offline Offline
Activity: 1764
Merit: 1002

|
 |
September 10, 2013, 02:47:04 PM |
|
Why would the NSA ever release a 'secure' algorithm? It's like shooting yourself in the foot, it would make their job so much harder. They would only ever release something that they could control. It's just the way the world works.
Because you can never definitively prove a cryptographic system is secure. The only way to "know" a cipher is secure is to make it publicly available and let the best in the world take a crack at it. It is very easy to write a cryptographic system that you yourself can't break but that is next to useless. Secret cryptography usually is weak cryptography. History is littered with examples of failed "strong" systems. One classic one is WEP which is so unbelievably broken it is hard to believe cryptographers came up with it. Security through obscurity doesn't work. Had the specs for WEP been made publicly available in the design phase people would have found the flaws in a matter of weeks and saved everyone a ton of problems down the road. For every good cipher there are dozens and dozens of flawed ones. No matter how smart a single developer is the combined intellect of the planet is better, that is the entire rationale for open source. The NSA is not only responsible for finding the secrets of others they are responsible for ensuring others don't find the secrets of the United States. The US government uses SHA-2 in secure cryptographic systems including SIPERNet. I know this from personal experience. i agree with this. |
|
|
|
|
|
miztaziggy
|
 |
September 10, 2013, 02:55:10 PM |
|
So what evidence do you have that the brightest minds in the world are not in these government agencies?
They will also be working in the open source community rather than exclusively in one place because they are passionate about the subject. Really? What world do you live in where employees of the NSA and GCHQ can moonlight in the open source community and spread state secrets around for the users of the bitcoin forum to read? And as for being passionate about the subject, I expect that when you're working on the inside of an agency like that and are in the know when it comes to the real threats in this world, you would probably be on the side of these agencies that do the work they do. |
*Image Removed*
|
|
|
cypherdoc
Legendary

 Offline Offline
Activity: 1764
Merit: 1002

|
 |
September 10, 2013, 02:57:52 PM |
|
The algorithm is open ... however it was produced by a politically motivated rogue government branch that seems to harbouring a cynical bunch of criminal bastards ... do your own due diligence, if you don't have to deal with them why bother?
Don't forget that the Internet and TOR were also started by the US military. Just the fact that they did something does not mean that they still have control over it. Edit: oops, forgot to point out that the NSA algos flaws/backdoors will be tailored towards cracking by hardware capabilities that they , and maybe only them, possess. So saying it is secure because no-one else has found a flaw is redundant since no-one else knows or can replicate what they are capable of in terms of mining the exploit ...
Flaws in one of most widely used algos would be quickly found by NSA's/USA enemies - such as China and Russia (Russia/China have some of the world brightest mathematicans & cryptographers). Especially after the Prism scandal. Hiding something like this is simply not possible in after-Prism paranoia world. and don't forget that the NSA relies on it's operatives going into harms way into foreign and hostile areas. you now have to imagine a scenario where they lie to them, and have the operatives allow themselves to be lied to, and say all their communications will continue to be safe and secure so continue doing what you're doing? either way, the NSA has suffered irreparable damage as a result of these so called revelations. i prefer the simplest explanation and that is to continue to believe that the Internet is ripping open age-old secrets and increasing the dissemination of the truth. to expect one US centric organization to be able to buck that trend over the long term is not viable, imo. |
|
|
|
|
cypherdoc
Legendary

 Offline Offline
Activity: 1764
Merit: 1002

|
 |
September 10, 2013, 03:10:41 PM |
|
if open source is so insecure, why are all these gov't agencies using it including the NSA itself via SELinux? i think the same can be said of SHA 1&2: http://en.wikipedia.org/wiki/List_of_Linux_adoptersGovernment As local governments come under pressure from institutions such as the World Trade Organization and the International Intellectual Property Alliance, some have turned to Linux and other Free Software as an affordable, legal alternative to both pirated software and expensive proprietary computer products from Microsoft, Apple and other commercial companies. The spread of Linux affords some leverage for these countries when companies from the developed world bid for government contracts (since a low-cost option exists), while furnishing an alternative path to development for countries like India and Pakistan that have many citizens skilled in computer applications but cannot afford technological investment at "First World" prices. In July 2001[1] the White House started moving their computers to a Linux platform based on Red Hat Linux and Apache HTTP Server.[2] The installation was completed in February 2009.[3][4] In October 2009 the White House servers adopted Drupal, an open source content management system software distribution.[5][6] Brazil uses PC Conectado, a program utilizing Linux. The City government of Munich chose in 2003 to start to migrate its 14,000 desktops to Debian-based LiMux.[7] Even though more than 80% of workstations used OpenOffice and 100% used Firefox/Thunderbird five years later (November 2008),[8] an adoption rate of Linux itself of only 20.0% (June 2010) was achieved.[9][10] The effort was later reorganized, focusing on smaller deployments and winning over staff to the value of the program. By the end of 2011 the program had exceeded its goal and changed over 9000 desktops to Linux.[11] The city of Munich reported at the end of 2012 that the migration to Linux was highly successful and has already saved the city over €11 million (US$14 million).[12] The United States Department of Defense uses Linux - "the U.S. Army is “the” single largest install base for Red Hat Linux"[13] and the US Navy nuclear submarine fleet runs on Linux.[14] The city of Vienna has chosen to start migrating its desktop PCs to Debian-based Wienux.[15] However, the idea was largely abandoned, because the necessary software was incompatible with Linux.[16] Spain was noted as the furthest along the road to Linux adoption in 2003,[17] for example with Linux distribution LinEx State owned Industrial and Commercial Bank of China (ICBC) is installing Linux in all of its 20,000 retail branches as the basis for its web server and a new terminal platform. (2005) [18] In April 2006, the US Federal Aviation Administration announced that it had completed a migration to Red Hat Enterprise Linux in one third of the scheduled time and saved 15 million dollars.[19][dead link] The Government of Pakistan established a Technology Resource Mobilization Unit in 2002 to enable groups of professionals to exchange views and coordinate activities in their sectors and to educate users about free software alternatives. Linux is an option for poor countries which have little revenue for public investment; Pakistan is using open source software in public schools and colleges, and hopes to run all government services on Linux eventually. The French Parliament has switched to using Ubuntu on desktop PCs.[20][21] The Federal Employment Office of Germany (Bundesagentur für Arbeit) has migrated 13,000 public workstations from Windows NT to OpenSuse.[22] Czech Post migrated 4000 servers and 12,000 clients to Novell Linux in 2005[23][24] Cuba - Students from the Cuban University of Information Science launched its own distribution of Linux called Nova to promote the replace of Microsoft Windows on civilian and government computers, a project that is now supported by the Cuban Government. By early 2011 the Universidad de Ciencias Informáticas announced that they would migrate more than 8000 PCs to this new operating system.[25][26][27] The Canton of Solothurn in Switzerland decided in 2001 to migrate its computers to Linux, but in 2010 the Swiss authority has made a U-turn by deciding to use Windows 7 for desktop clients.[28] France's national police force, the National Gendarmerie started moving their 90,000 desktops from Windows XP to Ubuntu in 2007 over concerns about the additional training costs of moving to Windows Vista, and following the success of OpenOffice.org roll-outs. The migration should be completed by 2015. The force has saved about €50 million on software licensing between 2004 and 2008.[29][30][31] France's Ministry of Agriculture uses Mandriva Linux.[31] Macedonia's Ministry of Education and Science deployed more than 180,000 Ubuntu based classroom desktops, and has encouraged every student in the Republic of Macedonia to use Ubuntu computer workstations.[32] The People's Republic of China exclusively uses Linux as the operating system for its Loongson processor family, with the aim of technology independence.[33] The US National Nuclear Security Administration operates the world's tenth fastest supercomputer, the IBM Roadrunner, which uses Red Hat Enterprise Linux along with Fedora as its operating systems.[34] The regional Andalusian Autonomous Government of Andalucía in Spain developed its own Linux distribution, called Guadalinex in 2004.[35] The South African Social Security Agency (SASSA) deployed Multi-station Linux Desktops to address budget and infrastructure constraints in 50 rural sites.[36] In 2003, the Turkish government decided to create its own Linux distribution, Pardus, developed by UEKAE (National Research Institute of Electronics and Cryptology). The first version, Pardus 1.0, was officially announced in 27 December 2005.[37] In 2010 The Philippines fielded an Ubuntu-powered national voting system.[38] In July 2010 Malaysia had switched 703 of the state's 724 agencies to Free and Open Source software with a Linux based operating system used.[39] The Chief Secretary to the Government cited, "(the) general acceptance of its promise of better quality, higher reliability, more flexibility and lower cost".[40] In late 2010 Vladimir Putin signed a plan to move the Russian Federation government towards free software including Linux in the second quarter of 2012.[41][42] The city government of Largo, Florida, USA uses Linux and has won international recognition for their implementation, indicating that it provides "extensive savings over more traditional alternatives in city-wide applications."[43] Iceland has announced in March 2012 that it wishes to migrate to open source software in public institutions. Schools have already migrated from Windows to Ubuntu Linux.[44] In June 2012 the US Navy signed a US$27,883,883 contract with Raytheon to install Linux ground control software for its fleet of vertical take-off and landing (VTOL) Northrup-Grumman MQ8B Fire Scout drones. The contract involves Naval Air Station Patuxent River, Maryland, which has already spent $5,175,075 in preparation for the Linux systems.[45] In 2004 Venezuela's government approved the 3390 decree,[46] to give preference to using free software in public administration. One result of this policy is the development of Canaima, a Deban-based Linux distribution. |
|
|
|
|
Zangelbert Bingledack
Legendary

 Offline Offline
Activity: 1036
Merit: 1000

|
 |
September 10, 2013, 03:16:03 PM |
|
I have a sneaking suspicion that the NSA's alleged superpowers are overrated. Maybe they once were way ahead of the curve back when crypto was a nerd curiosity. But now? In 2013, when the whole world understands the importance of crypto and scads of people are interested in it, including hackers who stand to become fabulously wealthy if they could find a flaw? I just don't buy it. More likely the government just wants people to think there's no point in using cryptography.
|
|
|
|
|
|
Galahad
|
 |
September 10, 2013, 03:28:20 PM |
|
I won't be following this topic now as I want to avoid an irrational troll. The only thing which could add to this discussion now for me would be an explanation of what they have cracked.
|
|
|
|
|
|
Xiaoma
|
 |
September 10, 2013, 03:56:05 PM |
|
By the way: What might have been the reason that Mr. Nakamoto decided to use an NSA algorithm (SHA-256) for Bitcoin?
There are more than a few hints that Mr Nakamoto himself (themselves) may be linked to NSA. just saying... |
|
|
|
|
DeathAndTaxes
Donator
Legendary

 Offline Offline
Activity: 1218
Merit: 1079
Gerald Davis

|
 |
September 10, 2013, 04:19:51 PM |
|
By the way: What might have been the reason that Mr. Nakamoto decided to use an NSA algorithm (SHA-256) for Bitcoin?
There are more than a few hints that Mr Nakamoto himself (themselves) may be linked to NSA. just saying... A cite? The only comments I remember is when Gavin went to CIA for a presentation on Bitcoin, Satoshi wasn't interested. |
|
|
|
|
cypherdoc
Legendary

 Offline Offline
Activity: 1764
Merit: 1002

|
 |
September 10, 2013, 04:50:59 PM |
|
|
|
|
|
|
TippingPoint
Legendary

 Offline Offline
Activity: 905
Merit: 1000

|
 |
September 10, 2013, 05:46:44 PM |
|
By the way: What might have been the reason that Mr. Nakamoto decided to use an NSA algorithm (SHA-256) for Bitcoin?
There are more than a few hints that Mr Nakamoto himself (themselves) may be linked to NSA. just saying... A cite? The only comments I remember is when Gavin went to CIA for a presentation on Bitcoin, Satoshi wasn't interested. This is quoted from the defunct Bruce Wagner Bitcoin podcast:
Bruce Wagner : When was the last time you chatted to satoshi <laugh>
Gavin Andresen: Um... I haven't had email from satoshi in a couple months actually. The last email I sent him I actually told him I was going to talk at the CIA. So it's possible , that.... that may have um had something to with his deciding
Link to source/timestamp? I'd love to hear this part, but not enough to listen through Bruce Wagner's podcast. It should be around 17:53. First episode. |
|
|
|
|
Come-from-Beyond
Legendary

 Offline Offline
Activity: 2142
Merit: 1009
Newbie

|
 |
September 10, 2013, 06:35:02 PM |
|
The US government uses SHA-2 in secure cryptographic systems including SIPERNet. I know this from personal experience.
Quoted for future references when I prove that 1. D&T = Satoshi2. Bitcoin was created by NSAHehe |
|
|
|
|
marcus_of_augustus
Legendary

 Offline Offline
Activity: 3920
Merit: 2348
Eadem mutata resurgo

|
 |
September 10, 2013, 09:46:13 PM |
|
Are you really that naive?
Do you underestimate the brightest minds in the world? Do you believe that the minds in the NSA are somehow brighter than those outside of it? It is not who is brighter or has the most talent ... it is about an asymmetry of knowledge (as it has always been, the designer of the lock is the guy who knows where it is vulnerable.) NSA designed the SHA256 algorithm, you don't think they had an eye on what their hardware is capable of whilst doing so? |
|
|
|
marcus_of_augustus
Legendary

 Offline Offline
Activity: 3920
Merit: 2348
Eadem mutata resurgo

|
 |
September 10, 2013, 09:48:14 PM |
|
Why would the NSA ever release a 'secure' algorithm? It's like shooting yourself in the foot, it would make their job so much harder. They would only ever release something that they could control. It's just the way the world works.
Because you can never definitively prove a cryptographic system is secure. The only way to "know" a cipher is secure is to make it publicly available and let the best in the world take a crack at it. It is very easy to write a cryptographic system that you yourself can't break but that is next to useless. Secret cryptography usually is weak cryptography. History is littered with examples of failed "strong" systems. One classic one is WEP which is so unbelievably broken it is hard to believe cryptographers came up with it. Security through obscurity doesn't work. Had the specs for WEP been made publicly available in the design phase people would have found the flaws in a matter of weeks and saved everyone a ton of problems down the road. For every good cipher there are dozens and dozens of flawed ones. No matter how smart a single developer is the combined intellect of the planet is better, that is the entire rationale for open source. The NSA is not only responsible for finding the secrets of others they are responsible for ensuring others don't find the secrets of the United States. The US government uses SHA-2 in secure cryptographic systems including SIPERNet. I know this from personal experience. Hmmm, you are sounding more and more like a spook or ex-spook ... doth protest too much? |
|
|
|
Dabs
Legendary

 Offline Offline
Activity: 3416
Merit: 1912
The Concierge of Crypto

|
 |
September 11, 2013, 12:49:09 AM |
|
Well, SHA-512 was also designed by the NSA right? And HMAC-SHA-512 uses the same hash function. Does anyone think they can crack that better than brute-force?
|
|
|
|
|
|
drawingthesun
Legendary

 Offline Offline
Activity: 1176
Merit: 1015

|
 |
September 11, 2013, 05:44:16 AM |
|
I have a sneaking suspicion that the NSA's alleged superpowers are overrated. Maybe they once were way ahead of the curve back when crypto was a nerd curiosity. But now? In 2013, when the whole world understands the importance of crypto and scads of people are interested in it, including hackers who stand to become fabulously wealthy if they could find a flaw? I just don't buy it. More likely the government just wants people to think there's no point in using cryptography.
And we have a winner! Ding ding ding! After Prism we started to hear lots of stories coming from two sides. Side 1) We need to start using crypto in everything now! Secure all the things! (This is us, the geeks) Side 2) Oh fudge if people start securing everything the future is going to be very dark indeed. Very dark because our capturing data centers will be redundant. (This is the NSA) If the NSA had really broken core cryptographic functions they would be neutral on people using encryption as it wouldn't matter. They would stay in the dark like they always do. Just watching us. However instead we started to get FUD all over the place about encryption. I remember reading that the government recommended people not to use encryption because it would mean the NSA would keep your data forever, and when that didn't work they started to give hints that all this encryption is useless anyway. This is what they want people to think, that its all broken so why waste your time? Just go back to using closed source please. If there is something they have done, that is they are "cheating" in that they are compromising many communication lines, certificates and closed source software. NSA most likely have access to gmail, skype, perhaps even windows backdoors. This is a campaign of FUD from the government. EDIT: I think SSL is compromised because they rely on certificates which is trivial for the NSA to acquire. |
|
|
|
|
domob
Legendary

 Offline Offline
Activity: 1135
Merit: 1161


|
 |
September 11, 2013, 06:29:18 AM |
|
I have a sneaking suspicion that the NSA's alleged superpowers are overrated. Maybe they once were way ahead of the curve back when crypto was a nerd curiosity. But now? In 2013, when the whole world understands the importance of crypto and scads of people are interested in it, including hackers who stand to become fabulously wealthy if they could find a flaw? I just don't buy it. More likely the government just wants people to think there's no point in using cryptography.
And we have a winner! Ding ding ding! After Prism we started to hear lots of stories coming from two sides. Side 1) We need to start using crypto in everything now! Secure all the things! (This is us, the geeks) Side 2) Oh fudge if people start securing everything the future is going to be very dark indeed. Very dark because our capturing data centers will be redundant. (This is the NSA) If the NSA had really broken core cryptographic functions they would be neutral on people using encryption as it wouldn't matter. They would stay in the dark like they always do. Just watching us. However instead we started to get FUD all over the place about encryption. I remember reading that the government recommended people not to use encryption because it would mean the NSA would keep your data forever, and when that didn't work they started to give hints that all this encryption is useless anyway. Very good points! I also believe that they are very far from actually breaking the algorithms themselves. (Except possibly if they managed to build a quantum computer, which I see as faint possibility.) EDIT: I think SSL is compromised because they rely on certificates which is trivial for the NSA to acquire.
Very true. SSL/TLS may be secure by itself, but the CA infrastructure is not. In fact, not only the NSA but a lot of other governments also directly or indirectly "own" a CA which is trusted by all major browsers/systems. |
Use your Namecoin identity as OpenID: https://nameid.org/Donations: 1 domobKsPZ5cWk2kXssD8p8ES1qffGUCm | NMC: NC domobcmcmVdxC5yxMitojQ4tvAtv99pY BM-GtQnWM3vcdorfqpKXsmfHQ4rVYPG5pKS | GPG 0xA7330737 |
|
|
Dabs
Legendary

 Offline Offline
Activity: 3416
Merit: 1912
The Concierge of Crypto

|
 |
September 11, 2013, 06:45:52 AM |
|
I use gmail. But I also use GPG with 4096 bit RSA keys. They can store my encrypted message and keep it for all eternity, but they'll never read it.
|
|
|
|
domob
Legendary

 Offline Offline
Activity: 1135
Merit: 1161


|
 |
September 11, 2013, 06:58:24 AM |
|
I use gmail. But I also use GPG with 4096 bit RSA keys. They can store my encrypted message and keep it for all eternity, but they'll never read it.
I wouldn't be so sure that RSA with 4096 bits will really never be cracked. Especially asymmetric algorithms seem quite vulnerable, given enough time for new methods and hardware to develop. (Nevertheless I also consider my GPG mails with this setting to be reasonable secure.) |
Use your Namecoin identity as OpenID: https://nameid.org/Donations: 1 domobKsPZ5cWk2kXssD8p8ES1qffGUCm | NMC: NC domobcmcmVdxC5yxMitojQ4tvAtv99pY BM-GtQnWM3vcdorfqpKXsmfHQ4rVYPG5pKS | GPG 0xA7330737 |
|
|
Come-from-Beyond
Legendary

 Offline Offline
Activity: 2142
Merit: 1009
Newbie

|
 |
September 11, 2013, 07:16:25 AM |
|
I use gmail. But I also use GPG with 4096 bit RSA keys. They can store my encrypted message and keep it for all eternity, but they'll never read it.
Even with their quantum computer? |
|
|
|
|
dave111223
Legendary

 Offline Offline
Activity: 1190
Merit: 1001


|
 |
September 11, 2013, 08:09:54 AM |
|
A friend of mine's son has studied maths at Cambridge in the UK, he is now doing a PHD over in the US at MIT. She had her son's friend stay with her over the holiday, and told me that this girl was also studying for a PHD also. This girl is apparently ridiculously intelligent, to the point of being autistic, she has no social skills. She has already been approached by GCHQ and has done a summer placement there. She has been offered a place after completing her PHD.
It's true...the NSA drives around on campus' in black vans looking for people with bad haircuts and mismatching orange and pink socks. They then throw a bunch of matches out the car window, if the target starts frantically counting the matches and repeating the total sum they put a brown bag over their head and bring them to area 51 for some super secret smart ass shit. |
|
|
|
|
manfred
Legendary

 Offline Offline
Activity: 966
Merit: 1001
Energy is Wealth

|
 |
September 11, 2013, 11:53:18 AM |
|
They would be dump as hell if there is no chance in at all to access it if there is a need to do so. As it stands there is no need to blow the cover and sacrifice years of work and huge amounts of money spend. In the big picture S.R. is laughable and Bitcoin is endorsed by the system at the moment (growing economy: hardware sales, exchanges, new products...).
Any rough element or country could simply send encrypted messages back and forth using a few satoshis and they would be totally defenceless defending themselves and country using a tool they created. If u believe this, well Santa Clause is coming to town too. If they see the need to switch the switch then they will.
|
|
|
|
|
Dabs
Legendary

 Offline Offline
Activity: 3416
Merit: 1912
The Concierge of Crypto

|
 |
September 11, 2013, 12:50:48 PM |
|
I use gmail. But I also use GPG with 4096 bit RSA keys. They can store my encrypted message and keep it for all eternity, but they'll never read it.
Even with their quantum computer? Even with their quantum computer. If you live long enough to read my email, you are effectively immortal. That, or someone stole my private key. |
|
|
|
DeathAndTaxes
Donator
Legendary

 Offline Offline
Activity: 1218
Merit: 1079
Gerald Davis

|
 |
September 11, 2013, 01:00:03 PM |
|
I use gmail. But I also use GPG with 4096 bit RSA keys. They can store my encrypted message and keep it for all eternity, but they'll never read it.
I wouldn't be so sure that RSA with 4096 bits will really never be cracked. Especially asymmetric algorithms seem quite vulnerable, given enough time for new methods and hardware to develop. (Nevertheless I also consider my GPG mails with this setting to be reasonable secure.) This. There is a high probability that 4096 bit asymmetric encryption will eventually be broken (by classical computing). Various agencies estimate a high probability that 4096 bit will no longer be secure after 2030-2060. That being said 4096 bit RSA provides reasonable security for the intermediate future however "never" is a long time. If it must be longer than your lifespan you should be looking at something like 15,360 bit RSA or 512 bit ECC. |
|
|
|
|
Dabs
Legendary

 Offline Offline
Activity: 3416
Merit: 1912
The Concierge of Crypto

|
 |
September 11, 2013, 01:26:03 PM |
|
Ok. I stand corrected. The word "never" was used as hyperbole. 2030 to 2060 is just about right, and maybe even sooner. Obligatory cartoon here: http://xkcd.com/538/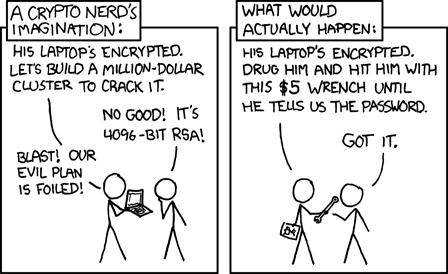 However, those same studies find 256 bit symmetric keys and hashes going far beyond the year 2080. We can already start using 512 bit hash functions. |
|
|
|
DeathAndTaxes
Donator
Legendary

 Offline Offline
Activity: 1218
Merit: 1079
Gerald Davis

|
 |
September 11, 2013, 02:00:54 PM |
|
Ok. I stand corrected. The word "never" was used as hyperbole. 2030 to 2060 is just about right, and maybe even sooner. Obligatory cartoon here:
No problem I personally use 4096 bit keys for PGP and don't worry. I does what its name says it does "pretty good privacy". I also agree even if 4096 bit can be broken someday it is more likely someone is going to beat me with a wrench instead.  Someone uninformed however might reach the wrong conclusion. I guess it all depends on how secret your secrets are or maybe more importantly how long they need to remain a secret. However, those same studies find 256 bit symmetric keys and hashes going far beyond the year 2080. We can already start using 512 bit hash functions.
Symmetric cryptography and hashing functions (assuming the algorithm itself is secure) don't have the same attack vectors that public key cryptography does. They also aren't vulnerable to Shor's algorithm. It is very like we will never need larger than 256 bit symmetric encryption or 512 bit hashes due to thermodynamics*. Public key is always going to be trickier to keep secure as they all rely on assumptions, and that will lead to a never ending "arms race". BTW I like that cartoon I have a signed print on my wall. Good reminder to see the forest from the trees when dealing with security. * Brute forcing a 256 bit key is a "never" scenario (more energy than available in our star system). https://www.schneier.com/blog/archives/2009/09/the_doghouse_cr.html |
|
|
|
|
gmaxwell
Staff
Legendary

 Offline Offline
Activity: 4158
Merit: 8382


|
 |
September 11, 2013, 02:20:58 PM
Last edit: September 11, 2013, 02:32:15 PM by gmaxwell |
|
Public key is always going to be trickier to keep secure as they all rely on assumptions, and that will lead to a never ending "arms race".
Well, careful, symmetric ciphers depend on the existence of one way functions. If P happened to practically equal NP, then one way functions couldn't exist and I could solve for the symmetric keys that turns your ciphertext into ascii (there is probably only one). NOT. BLOODLY. LIKELY. (kinda sadly, there would be a lot of other befits to such a world) It's possible to construct public key signature systems that depend only on the existence of one way functions. (Lamport!) The soundness assumptions in error correcting code crypto-systems are also generally pretty solid (well, we keep breaking them trying to make their overheads tolerable…) (solving for random linear codes is NP-HARD ... the only question is can the attacker turn your public key back into an easy linear code) Considering that for encrypted messages overhead is mostly immaterial I'm surprised that no one has created a stone soup protocol that just takes "one from each column": NIST-521 bit ECDH, just in case the NSA made it stronger 1024 bit ECDH with parameters selected the best known public art techniques (e.g. like the brainpool curves) Supersingular isogenies key agreement Wrapped up inside an error correcting code public key encryption And that encrypted with a symmetric key which is from the recipient, a starter one is in the public key.. though thats not very useful. Feed it to a pair of orthogonal strong KDFs which then feed separate passes of multiple standard ciphers (unrelated keys) in some long block modes. Then inside the encrypted messages you send symmetric keys generated using H(random, data_thats_part_of_your_private_key) which your receiver will save and use as an additional key in your KDFs in messages they send to you in the future (perhaps up to N of them with octave spacing, so a spy that can break the public key stuff will get locked out with high probability if they miss any of your messages). Perhaps then the whole message gets thrown through a gnarly unkeyed cryptographic permutation and coded up with a RS code and you replace it with the non-systematic outputs and, at your option send, the message in as many parts as you like over different communications channels... so an attacker who can't snoop all of them learns almost nothing about the whole message. Care would need to be taken to avoid interactions that hurt security.. but for encrypted messages.. who gives a crap if there is 50K of overhead and it takes a half second to decrypt? There are plenty of applications where thats totally unacceptable, like Bitcoin... but also plenty where it is. ... wait. what board is this?? woah .. way offtopic. |
|
|
|
|
hashman
Legendary

 Offline Offline
Activity: 1264
Merit: 1008

|
 |
September 11, 2013, 04:55:09 PM |
|
I use gmail. But I also use GPG with 4096 bit RSA keys. They can store my encrypted message and keep it for all eternity, but they'll never read it.
Even with their quantum computer? Even with their quantum computer. If you live long enough to read my email, you are effectively immortal. That, or someone stole my private key. Or, they were reading the email as you typed it using 1) Rootkit 2) Tempest 3) Robotic mosquito flying behind your head |
|
|
|
|
manfred
Legendary

 Offline Offline
Activity: 966
Merit: 1001
Energy is Wealth

|
 |
September 11, 2013, 05:08:03 PM |
|
|
|
|
|
|
ElectricMucus
Legendary

 Offline Offline
Activity: 1666
Merit: 1057
Marketing manager - GO MP


|
 |
September 11, 2013, 08:13:32 PM |
|
3) Robotic mosquito flying behind your head
I'm living under constant fear that this happens day in and day out, how do I keep going? |
|
|
|
|
|
MoneyMorpheus
|
 |
September 11, 2013, 09:05:45 PM |
|
3) Robotic mosquito flying behind your head
I'm living under constant fear that this happens day in and day out, how do I keep going? Kill all the mosquitoes at sight and you should be safe  |
|
|
|
Dabs
Legendary

 Offline Offline
Activity: 3416
Merit: 1912
The Concierge of Crypto

|
 |
September 11, 2013, 11:45:23 PM |
|
Or, they were reading the email as you typed it using
1) Rootkit
2) Tempest
3) Robotic mosquito flying behind your head
1. Not likely. Email composed and encrypted offline. Also got tools for this, GMER, etc. 2. Not likely. Faraday cage and all that. 3. Not likely. All insects don't get past the door and air filters. Of course, it's still possible. Just not likely. @gmaxwell, nice post. I almost understood everything. hehehe. |
|
|
|
Dabs
Legendary

 Offline Offline
Activity: 3416
Merit: 1912
The Concierge of Crypto

|
 |
September 11, 2013, 11:51:43 PM |
|
all their needs could be handled on 10 year old XP machines or even just a couple of smartphones. I know several companies that still work with 10 year old XP (SP3) machines. Get's the job done and still runs everything new out there, just a little bit slower. |
|
|
|
|
illpoet
|
 |
September 12, 2013, 04:06:38 AM |
|
Are you really that naive?
Do you underestimate the brightest minds in the world? Do you believe that the minds in the NSA are somehow brighter than those outside of it? So what evidence do you have that the brightest minds in the world are not in these government agencies? A friend of mine's son has studied maths at Cambridge in the UK, he is now doing a PHD over in the US at MIT. She had her son's friend stay with her over the holiday, and told me that this girl was also studying for a PHD also. This girl is apparently ridiculously intelligent, to the point of being autistic, she has no social skills. She has already been approached by GCHQ and has done a summer placement there. She has been offered a place after completing her PHD. That's what happens in the real world, these ultra bright kids will be snapped up by places like GCHQ and NSA before they are 21, but, this forum is just like a hollow box where you all like to shout about the positives of bitcoin without ever considering the real world, so I guess none of this matters. The real world has no relevance on the internet. |
Tym's Get Rich Slow scheme: plse send .00001 to
btc: 1DKRaNUnMQkeby6Dk1d8e6fRczSrTEhd8p ltc: LV4Udu7x9aLs28MoMCzsvVGKJbSmrHESnt
thank you.
|
|
|
AndrewWilliams
Full Member
  
 Offline Offline
Activity: 182
Merit: 100
Fourth richest fictional character

|
 |
September 12, 2013, 08:53:00 PM |
|
If you have to ask, you already know the answer.
|
|
|
|
|
hashman
Legendary

 Offline Offline
Activity: 1264
Merit: 1008

|
 |
September 13, 2013, 01:49:05 PM |
|
If you have to ask, you already know the answer.
More like, if you have to ask, you are trying to divert us from looking at secp256k1. |
|
|
|
|
marcus_of_augustus
Legendary

 Offline Offline
Activity: 3920
Merit: 2348
Eadem mutata resurgo

|
 |
September 14, 2013, 03:50:38 AM |
|
If you have to ask, you already know the answer.
More like, if you have to ask, you are trying to divert us from looking at secp256k1. hehe |
|
|
|
hashman
Legendary

 Offline Offline
Activity: 1264
Merit: 1008

|
 |
September 14, 2013, 09:19:37 AM |
|
Or, they were reading the email as you typed it using
1) Rootkit
2) Tempest
3) Robotic mosquito flying behind your head
1. Not likely. Email composed and encrypted offline. Also got tools for this, GMER, etc. 2. Not likely. Faraday cage and all that. 3. Not likely. All insects don't get past the door and air filters. Of course, it's still possible. Just not likely. @gmaxwell, nice post. I almost understood everything. hehehe. You seem to have your systems quite in order sir  Do you mind while we stray somewhat off topic if I ask, how you authenticate your recipients public key? |
|
|
|
|
Abdussamad
Legendary

 Offline Offline
Activity: 3598
Merit: 1560

|
 |
September 14, 2013, 10:32:48 AM |
|
Bitcoin is one big worry after another.  |
|
|
|
|
AndrewWilliams
Full Member
  
 Offline Offline
Activity: 182
Merit: 100
Fourth richest fictional character

|
 |
September 14, 2013, 05:40:15 PM |
|
Bitcoin Pakistan... holy $hit.
Something tells me NSA's computers just went off the charts, LOL
|
|
|
|
|
Abdussamad
Legendary

 Offline Offline
Activity: 3598
Merit: 1560

|
 |
September 14, 2013, 05:42:47 PM |
|
Bitcoin Pakistan... holy $hit.
Something tells me NSA's computers just went off the charts, LOL
Why just? I've been a member of this forum for months and my site has been up for most of that time. Also there's a dedicated thread for Pakistan in the other forum. |
|
|
|
|
Maidak
Legendary

 Offline Offline
Activity: 1876
Merit: 1058
The OGz Club

|
 |
September 14, 2013, 05:51:33 PM |
|
What if satoshi nakamoto works at nsa  |
|
|
|
|
FTWbitcoinFTW
|
 |
September 14, 2013, 07:12:39 PM |
|
What if satoshi nakamoto works at nsa  Then the USA and a small group of shadow people would take control over the next standard currency by holding 1M BTCWait...! What ? |
Lost coins only make everyone else's coins worth slightly more. Think of it as a donation to everyone. it has lots of buttery taste.. |
|
|
becoin
Legendary

 Offline Offline
Activity: 3431
Merit: 1233

|
 |
September 14, 2013, 07:43:02 PM |
|
Also, the NSA themselves rely on this encryption, do they want their secrets revealed? How can you know that NSA use SHA-256 in their own communication channels? |
|
|
|
|
Dabs
Legendary

 Offline Offline
Activity: 3416
Merit: 1912
The Concierge of Crypto

|
 |
September 15, 2013, 07:44:24 AM |
|
You seem to have your systems quite in order sir  Do you mind while we stray somewhat off topic if I ask, how you authenticate your recipients public key? I'm supposed to get their GPG fingerprint from a more secure channel, such as voice or telephone (including SMS or text messages). But these days you can do VOIP, and some chats, some video conferencing, skype, yahoo with webcam, etc. The best method, of course, is in person. Also depends on how much you should trust the other party, if it's just casual conversation or he's trying to buy something from me, I don't even bother, I just accept his public key and check later (from somewhere else, another physical internet connection from another physical location) if I got the same public key. I try to check if it's from a keyserver or his own private web page or something. Would be very hard for some bad guy to compromise all of those unless the poor guy has already been a national security level target for some time and he's been replaced by a clone or something. I can probably accept the public keys of most of the bitcoin devs, for example, and use those to communicate with them and/or verify the latest bitcoin-qt releases. |
|
|
|
GoldSilverBitcoin
Member
 
 Offline Offline
Activity: 80
Merit: 10
Gold Silver Bitcoin: It's your choice


|
 |
September 15, 2013, 10:16:13 AM |
|
It is, after all, the "world wide web"
|
|
|
|
|
marketorder
|
 |
September 15, 2013, 10:25:27 AM |
|
Sh*t I thought SHA-256 was designed by aliens!
|
|
|
|
|
dragonkid
Member
 
 Offline Offline
Activity: 84
Merit: 10

|
 |
September 15, 2013, 04:54:35 PM |
|
You seem to have your systems quite in order sir  Do you mind while we stray somewhat off topic if I ask, how you authenticate your recipients public key? I'm supposed to get their GPG fingerprint from a more secure channel, such as voice or telephone (including SMS or text messages). But these days you can do VOIP, and some chats, some video conferencing, skype, yahoo with webcam, etc. The best method, of course, is in person. Also depends on how much you should trust the other party, if it's just casual conversation or he's trying to buy something from me, I don't even bother, I just accept his public key and check later (from somewhere else, another physical internet connection from another physical location) if I got the same public key. I try to check if it's from a keyserver or his own private web page or something. Would be very hard for some bad guy to compromise all of those unless the poor guy has already been a national security level target for some time and he's been replaced by a clone or something. I can probably accept the public keys of most of the bitcoin devs, for example, and use those to communicate with them and/or verify the latest bitcoin-qt releases. Boy you know your stuff. I got a Master Degree in Information Security and Advance Cryptography. I can confirm you are spot on.  |
|
|
|
Dabs
Legendary

 Offline Offline
Activity: 3416
Merit: 1912
The Concierge of Crypto

|
 |
September 16, 2013, 03:05:36 AM |
|
Boy you know your stuff. I got a Master Degree in Information Security and Advance Cryptography. I can confirm you are spot on.  I can't tell if you are sarcastic or trolling or what, but just in case you are serious: Where did you get your Masters Degree? I am genuinely curious. I don't see those kinds of courses offered in any school in my country. The closest I can see is a Masters in National Security Administration, which I've been eyeing for a few years now. I just need to find the time (one year of going to school.) They don't seem to talk about Cryptography though, it's more like a Strategic Warfare school. (It's a military college.) |
|
|
|
|
Honeypot
|
 |
December 20, 2013, 11:58:11 PM |
|
"In God we trust. Everyone else, we monitor".
Sounds like a good policy. As if anyone else would be 'better' if they were in that position.
Check yourselves before criticizing the 'government' please...
|
|
|
|
|
marcus_of_augustus
Legendary

 Offline Offline
Activity: 3920
Merit: 2348
Eadem mutata resurgo

|
 |
December 21, 2013, 12:02:09 AM |
|
"In God we trust. Everyone else, we monitor".
Sounds like a good policy. As if anyone else would be 'better' if they were in that position.
Check yourselves before criticizing the 'government' please...
Except they use the full force of secrecy laws and corrupt judges (and who knows what other nefarious means) and the Iron Fist of the State to specifically avoid all monitoring ... check yourself before defending corruption please ... |
|
|
|
|
Honeypot
|
 |
December 21, 2013, 12:07:58 AM |
|
"In God we trust. Everyone else, we monitor".
Sounds like a good policy. As if anyone else would be 'better' if they were in that position.
Check yourselves before criticizing the 'government' please...
Except they use the full force of secrecy laws and corrupt judges (and who knows what other nefarious means) and the Iron Fist of the State to specifically avoid all monitoring ... check yourself before defending corruption please ... Fool check yourself before bitching about 'corruption' in a developed first world nation/ 'nefarious', 'iron fist' LOL Do you think you can even post like this if you were under REAL tyranny? Mouthing off like no tomorrow. Jesus Christ you naive fuck. |
|
|
|
|
marcus_of_augustus
Legendary

 Offline Offline
Activity: 3920
Merit: 2348
Eadem mutata resurgo

|
 |
December 21, 2013, 12:12:26 AM |
|
"In God we trust. Everyone else, we monitor".
Sounds like a good policy. As if anyone else would be 'better' if they were in that position.
Check yourselves before criticizing the 'government' please...
Except they use the full force of secrecy laws and corrupt judges (and who knows what other nefarious means) and the Iron Fist of the State to specifically avoid all monitoring ... check yourself before defending corruption please ... Fool check yourself before bitching about 'corruption' in a developed first world nation/ 'nefarious', 'iron fist' LOL Do you think you can even post like this if you were under REAL tyranny? Mouthing off like no tomorrow. Jesus Christ you naive fuck. Typical Statist apologist ... all class defending the indefensible. The NSA are a soft tyranny, you have no clue. Have a nice day sweetie.  |
|
|
|
|
Honeypot
|
 |
December 21, 2013, 12:18:05 AM |
|
"In God we trust. Everyone else, we monitor".
Sounds like a good policy. As if anyone else would be 'better' if they were in that position.
Check yourselves before criticizing the 'government' please...
Except they use the full force of secrecy laws and corrupt judges (and who knows what other nefarious means) and the Iron Fist of the State to specifically avoid all monitoring ... check yourself before defending corruption please ... Fool check yourself before bitching about 'corruption' in a developed first world nation/ 'nefarious', 'iron fist' LOL Do you think you can even post like this if you were under REAL tyranny? Mouthing off like no tomorrow. Jesus Christ you naive fuck. Typical Statist apologist ... all class defending the indefensible. The NSA are a soft tyranny, you have no clue. Have a nice day sweetie.  LOL typical soft fuck from 1st world that thinks they know something about 'tyranny'. The only difference, but a big one, between tyranny and politics is the end result. Let me know when they bust in your door in the middle of the night and drag off your family mafia style into the deepest darkest alley to be raped and killed as you watch. No one gives a shit about some pampered fools bitching about 'tyranny' and can't even tell the difference between a real talk and 'state apologist' Really, it's sad how naive some of you are. You even deluded yourself you know better than others  |
|
|
|
|
marcus_of_augustus
Legendary

 Offline Offline
Activity: 3920
Merit: 2348
Eadem mutata resurgo

|
 |
December 21, 2013, 12:26:22 AM |
|
Yeah, because some tyrannies are better than others ...  With logic like that, winning is not an option chump. |
|
|
|
|
Honeypot
|
 |
December 21, 2013, 12:27:09 AM |
|
Yeah, because some tyrannies are better than others ...  With logic like that, winning is not an option chump. And that's why you lose  |
|
|
|
|
DeepCryptoanalist3
Member
 
 Offline Offline
Activity: 81
Merit: 10

|
 |
December 21, 2013, 12:39:45 AM |
|
Wo wo wow! NSA have a backdoor in SHA? Srsly? All cryptanalytics worldwide are NSA undercover agents. This thoughts made me wet
|
|
|
|
|
|
evoked22
|
 |
December 21, 2013, 03:26:19 AM |
|
|
SnZN5o2ePUgtr9roQyavBC3r41vz7p63ne
|
|
|
|
FTWbitcoinFTW
|
 |
December 21, 2013, 05:03:00 AM |
|
Within a year, major questions were raised about Dual Elliptic Curve.
Cryptography authority Bruce Schneier wrote that the weaknesses in the formula "can only be described as a back door".
After reports of the back door in September, RSA urged its customers to stop using the Dual Elliptic Curve number generator.
But unlike the Clipper Chip fight two decades ago, the company is saying little in public, and it declined to discuss how the NSA
entanglements have affected its relationships with customers. http://www.theguardian.com/world/2013/dec/20/nsa-internet-security-rsa-secret-10m-encryptionECC is use for Bitcoin right ? |
Lost coins only make everyone else's coins worth slightly more. Think of it as a donation to everyone. it has lots of buttery taste.. |
|
|
marcus_of_augustus
Legendary

 Offline Offline
Activity: 3920
Merit: 2348
Eadem mutata resurgo

|
 |
December 21, 2013, 05:19:01 AM |
|
Wo wo wow! NSA have a backdoor in SHA? Srsly? All cryptanalytics worldwide are NSA undercover agents. This thoughts made me wet
I guess two sock-puppets is always better than one in dumb govt. drone way of thinking ... bigger budgets, less accountability. |
|
|
|
|
Trance
|
 |
December 21, 2013, 08:17:50 AM |
|
If the NSA did make Bitcoin, the would be able to find A LOT of people money laundering, operating out of China and so forth perhaps?! Speculation is fun  |
Some people are so poor ALL they have is money
|
|
|
|
|
BullCreek
Newbie

 Offline Offline
Activity: 26
Merit: 0

|
 |
June 08, 2017, 06:14:27 AM |
|
REALITY WINNER
|
|
|
|
|
|



