WanderingPhilospher
Full Member
  
 Offline Offline
Activity: 1064
Merit: 219
Shooters Shoot...

|
 |
December 25, 2023, 07:23:03 AM |
|
Take your chances by deploying a bot to compete with the looter, otherwise you can kiss your coins good bye. Or just talk with a large pool beforehand, you could offer them $10,000 bonus and if they include the tx in their block, other pools won't dare to mine that block again just to take those extra coins.
So you are claiming that any Bitcoin transaction could be double-spended and therefore all Bitcoin transactions are insecure. Makes sense ? What do you think of a challenge? I transfer an amount of x coins, you only know the source address, which I will publish here. Then you siphon off the coins and transfer them to another address before I receive them just like you described the looter would. If the coins end up at your freely chosen address, you can keep them. If they end up with me, you have lost and made a fool of yourself. Deal ? I am pretty sure he's only talking about the low bit challenge/puzzles, like #66. |
|
|
|
|
|
|
|
|
|
|
|
|
|
Every time a block is mined, a certain amount of BTC (called the
subsidy) is created out of thin air and given to the miner. The
subsidy halves every four years and will reach 0 in about 130 years.
|
|
|
Advertised sites are not endorsed by the Bitcoin Forum. They may be unsafe, untrustworthy, or illegal in your jurisdiction.
|
|
|
|
citb0in
|
 |
December 25, 2023, 07:35:45 AM |
|
I forgot to mention that I will use a private within the 66bit key range, I edited my post above.
|
.
.HUGE. | | | | | | █▀▀▀▀
█
█
█
█
█
█
█
█
█
█
█
█▄▄▄▄ | ▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀
.
CASINO & SPORTSBOOK
▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ | ▀▀▀▀█
█
█
█
█
█
█
█
█
█
█
█
▄▄▄▄█ | | |
|
|
|
Venus Blue
Newbie

 Offline Offline
Activity: 3
Merit: 0

|
 |
December 25, 2023, 08:06:19 AM
Last edit: December 25, 2023, 08:26:33 AM by Venus Blue |
|
Take your chances by deploying a bot to compete with the looter, otherwise you can kiss your coins good bye. Or just talk with a large pool beforehand, you could offer them $10,000 bonus and if they include the tx in their block, other pools won't dare to mine that block again just to take those extra coins.
So you are claiming that any Bitcoin transaction could be double-spended and therefore all Bitcoin transactions are insecure. Makes sense ? What do you think of a challenge? I transfer an amount of x coins, you only know the source address, which I will publish here. Then you siphon off the coins and transfer them to another address before I receive them just like you described the looter would. If the coins end up at your freely chosen address, you can keep them. If they end up with me, you have lost and made a fool of yourself. Deal ? I am pretty sure he's only talking about the low bit challenge/puzzles, like #66. Yeah... #66, #67, #68 and so on can be cracked within seconds using Kangaroo. I'm pretty sure there are bots watching those addresses. As soon as those pubkeys go live people will be warned and they'll have at least a 5-10 minutes window to solve the key and RBF. Right now with the Ordinals situation that window could be greater, specially if the solver decides to cheap out with the fees... |
|
|
|
|
3dmlib
Newbie

 Offline Offline
Activity: 37
Merit: 0

|
 |
December 25, 2023, 08:17:50 AM |
|
#66, #67, #68 and so on can be cracked within seconds using Kangaroo. I'm pretty sure there are bots watching those addresses.
Is placing transaction (with transaction fee enough to be included in next block) in the last second before new block will be mined will help? |
|
|
|
|
Venus Blue
Newbie

 Offline Offline
Activity: 3
Merit: 0

|
 |
December 25, 2023, 08:23:14 AM |
|
#66, #67, #68 and so on can be cracked within seconds using Kangaroo. I'm pretty sure there are bots watching those addresses.
Is placing transaction (with transaction fee enough to be included in next block) in the last second before new block will be mined will help? I'm not sure, someone else with more knowledge than I will be able to better answer you. Although that's something I also thought of doing... |
|
|
|
|
AlanJohnson
Member
 
 Offline Offline
Activity: 93
Merit: 11

|
 |
December 25, 2023, 08:40:02 AM |
|
I don't why out of sudden doublespend or replacemant is a problem with puzzle 66 but wasn't before with other puzzles ...
|
|
|
|
|
zahid888
Member
 
 Offline Offline
Activity: 260
Merit: 19
the right steps towerds the goal

|
 |
December 25, 2023, 09:18:36 AM |
|
Take your chances by deploying a bot to compete with the looter, otherwise you can kiss your coins good bye. Or just talk with a large pool beforehand, you could offer them $10,000 bonus and if they include the tx in their block, other pools won't dare to mine that block again just to take those extra coins.
So you are claiming that any Bitcoin transaction could be double-spended and therefore all Bitcoin transactions are insecure. Makes sense ? What do you think of a challenge? I transfer an amount of x coins, you only know the source address, which I will publish here. Its private key will be in the range of 66bit just like the mentioned puzzle. Then you siphon off the coins and transfer them to another address before I receive them just like you described the looter would. If the coins end up at your freely chosen address, you can keep them. If they end up with me, you have lost and made a fool of yourself. Deal ? He is speaking quite accurately. I have witnessed numerous instances where some private keys which have been compromised. Many individuals have set up auto-send bots with those compromised keys. If any funds accidentally land there, they are immediately transferred, and it waits for confirmation. Suddenly, a miner arrives and brings 1 confirmation with him. Before the individuals transaction is confirmed, it conflicts with the 1 confirmation, and the funds are transferred to the miner who broadcasts the tx_hash with The hellll   1 confirmation with his pocket  . I watch such cases about 4 or 5 times in a month. 1 ex: below 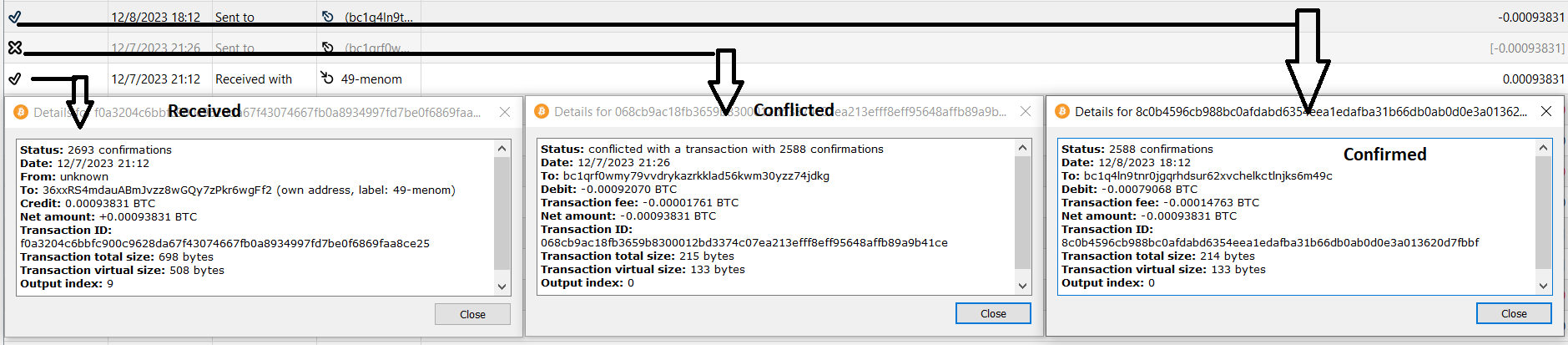
I urge Satoshi Nakamoto to promptly close this loophole. Only then will it be enjoyable to take on the challenge of this puzzle. Otherwise, it would be better for all of us to gracefully withdraw from this challenge. The one who has the private key and has signed the first transaction with sufficient fees, until that transaction is confirmed, no other tx_hash related to that address should be submitted in the mempool. Implementing this much is not a difficult task. |
1BGvwggxfCaHGykKrVXX7fk8GYaLQpeixA
|
|
|
nomachine
Member
 
 Offline Offline
Activity: 257
Merit: 12

|
 |
December 25, 2023, 10:32:37 AM |
|
I don't why out of sudden doublespend or replacemant is a problem with puzzle 66 but wasn't before with other puzzles ...
Or 67, 68, 69?  |
|
|
|
|
Kamoheapohea
Newbie

 Offline Offline
Activity: 29
Merit: 9

|
 |
December 25, 2023, 06:08:34 PM
Last edit: December 25, 2023, 06:25:43 PM by Kamoheapohea |
|
The solution is "exclusive mining".
As a "proof of solution" you create a hash of the privatekey (or publickey), your username and bitcoin address and post the hash here and/or other services where you have a (more or less) trusted timestamp.
This is your evidence that you solved the key before any other person.
You create your transaction locally and pick one of the big (and trusted) miningpools and send your transaction directly to the pool (contact them via E-Mail or maybe they have a preferred way of contacting). This way the public-key will never get into the mempool.
|
|
|
|
|
modma
Newbie

 Offline Offline
Activity: 10
Merit: 0

|
 |
December 25, 2023, 06:26:08 PM |
|
But couldn't disabling rbf and banning the use of wallets for change solve this problem?
|
|
|
|
|
tmar777
Newbie

 Offline Offline
Activity: 7
Merit: 0

|
 |
December 25, 2023, 10:15:55 PM |
|
Hi guys,
I am not sure if here is the correct place to ask but I need your help.
I need a secure, checked and efficient script that gets binaries (256bit) and returns:
1) private key (c)
2) private key (u)
3) public address in hex
4) public address
5) balance
or at least some of the above. As for the 5, i know that i need a connection to the API, so i prefer to suggest me of two different scripts because i want to run the 1-4 offline locally for speed.
If you have anything in mind TESTED and SECURE please let me know where to look.
Thanks
|
|
|
|
|
AlanJohnson
Member
 
 Offline Offline
Activity: 93
Merit: 11

|
 |
December 26, 2023, 08:06:59 AM |
|
You should use Bitcrack > https://bitcointalk.org/index.php?topic=4453897.0There is no need to check balance via API, you just place all funded addresses in a text file and set it as target, then the tool will grind through the range and if there is a match, it will save it to a file. I've done that already. Waste of time for lower bit ranges and for higher it takes too long. I can tell you one thing everything that can be stolen on bitcoin blockchain is already stolen  |
|
|
|
|
pseudospace
Newbie

 Offline Offline
Activity: 7
Merit: 0

|
 |
December 26, 2023, 03:40:42 PM |
|
Hello, sorry if this is a dumb question or has already been answered in a place I'm failing to find, I'm wondering if there is there any knowledge (or speculation!) of the methodology which was used in the creation of the transaction?
Many thanks
pseudospace.
|
|
|
|
|
nomachine
Member
 
 Offline Offline
Activity: 257
Merit: 12

|
 |
December 27, 2023, 09:35:55 AM |
|
I'm wondering if there is there any knowledge (or speculation!) of the methodology which was used in the creation of the transaction?
A few words about the puzzle. There is no pattern. It is just consecutive keys from a deterministic wallet (masked with leading 000...0001 to set difficulty). |
|
|
|
|
kalos15btc
Jr. Member

 Offline Offline
Activity: 50
Merit: 1

|
 |
December 27, 2023, 12:08:40 PM |
|
Some rocket science, some dice, a few weeks of calm and quiet, a few cups of coffee and finally an HD wallet to generate 256 keys and then masking each key with 0s to place each key in a certain bit range. Like : 9845224217be692ed430097d85a368999c01f3d14e5cf30c3b0ce72921e9d0cf Replace the strike through characters with 0s and good to go.
I managed to take a snapshot of the situation when #66 is solved. some mod ban this user please  his always reply with nothing to say about the puzzle, this is not a forum for memes, where are your new accounts ? we didint see your self reply to yourself anymore, stay away from this thread we are trying to solve a puzzle here, P66 is in 20-2F range not in 30-3F. |
|
|
|
|
AlanJohnson
Member
 
 Offline Offline
Activity: 93
Merit: 11

|
 |
December 27, 2023, 04:36:09 PM |
|
P66 is in 20-2F range not in 30-3F.
How do you know that ? |
|
|
|
|
|
citb0in
|
 |
December 27, 2023, 04:36:58 PM |
|
P66 is in 20-2F range not in 30-3F.
How do you know that ? he cannot, just ignore. |
.
.HUGE. | | | | | | █▀▀▀▀
█
█
█
█
█
█
█
█
█
█
█
█▄▄▄▄ | ▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀
.
CASINO & SPORTSBOOK
▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ | ▀▀▀▀█
█
█
█
█
█
█
█
█
█
█
█
▄▄▄▄█ | | |
|
|
|
|
citb0in
|
 |
December 27, 2023, 06:18:54 PM
Last edit: December 27, 2023, 07:27:07 PM by citb0in |
|
Take your chances by deploying a bot to compete with the looter, otherwise you can kiss your coins good bye. Or just talk with a large pool beforehand, you could offer them $10,000 bonus and if they include the tx in their block, other pools won't dare to mine that block again just to take those extra coins.
So you are claiming that any Bitcoin transaction could be double-spended and therefore all Bitcoin transactions are insecure. Makes sense ? What do you think of a challenge? I transfer an amount of x coins, you only know the source address, which I will publish here. Its private key will be in the range of 66bit just like the mentioned puzzle. Then you siphon off the coins and transfer them to another address before I receive them just like you described the looter would. If the coins end up at your freely chosen address, you can keep them. If they end up with me, you have lost and made a fool of yourself. Deal ? @Legends_Never_Die So what's about the RBF-challenge, deal or no deal?I generate an address with a 66bit private key and send a few coins to it. Then I create a transaction to send the entire contents of this wallet address to any other address. I will explicitly set 1 sat/vB as the fee so that the transaction can stay in the blockchain forever. Now you (or someone else if you like) try to cancel this outgoing transaction and thus simulate a mallory sucker that wants to withdraw the coins. As the transaction has the minimum fee you have all the time that you need. As the fees are currently very high, I am unfortunately unable to send coins to the RBF-challenge address. If anyone is interested in this RBF-challenge and would like to sponsor some minimum amount of satoshis, here is the wallet address: 1C8uD9G4AGQas5sG15869p5B1mrF3RELY3I own the private key of this address, here's the signature: Message: This address was exclusively generated for the RBF-challenge <https://bitcointalk.org/index.php?topic=1306983.msg63398077#msg63398077> and I have the private key of this address. citb0in, 2023-12-27
Address: 1C8uD9G4AGQas5sG15869p5B1mrF3RELY3
Signature: IAMmKuX5C2Z97eCSjYjfAN49hApXTk2LcMLzHWUp/vYYTxmKsHGaUdc7KQRFilTHUyqiEGt0B3NFqanjcgWl/Fg=The sha256 of the privkey is: 6297b7a9a38985d967e9d5603ba5e4f133b0e8a998219f29c4029aa03601110b As soon as this address has been funded with a few satoshis by a generous supporter, I could prepare the outgoing transaction as explained. Any funder appreciated Let me know if anyone's interested in that challenge. |
.
.HUGE. | | | | | | █▀▀▀▀
█
█
█
█
█
█
█
█
█
█
█
█▄▄▄▄ | ▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀
.
CASINO & SPORTSBOOK
▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ | ▀▀▀▀█
█
█
█
█
█
█
█
█
█
█
█
▄▄▄▄█ | | |
|
|
|
_Counselor
Member
 
 Offline Offline
Activity: 107
Merit: 61

|
 |
December 28, 2023, 06:35:19 AM |
|
It seems as though nobody is knowledgeable enough to figure out as to why generator points of 2 curves secp and secq256k1 both when divided by 2 generate the same coordinates. Either the so called "experts" and "cryptographers" are clueless as well or they refuse to reveal the secret. Asking questions on other platforms seems to produce the same scripted answers.
It's just because both generators were created by doubling the same point. |
|
|
|
|
Kamoheapohea
Newbie

 Offline Offline
Activity: 29
Merit: 9

|
 |
December 28, 2023, 07:13:33 AM |
|
...
As the fees are currently very high, I am unfortunately unable to send coins to the RBF-challenge address...
Let me know if anyone's interested in that challenge.
Please fund your challenges or don't have a challenge. Miners decide which transaction to include in blocks and any serious miner will chose those with the highest fees. So I don't see why we need such challenge. |
|
|
|
|
|




