|
albert0bsd
|
 |
March 28, 2024, 06:16:41 PM |
|
Im using this command :
.\keyhunt.exe -m bsgs -f keys.txt -b 130 -t 4 -s 10 -k 256 -S
should i change something or this is my power and i cant do anything more ?
Your problem is the .exe and windows stuff Don use it on windows, compile it your self in a WSL environment or native linux The lastest version is Version 0.2.230519 Satoshi Quest it provide an increment of speed X2 compared with previous version |
|
|
|
|
|
|
|
|
|
|
I HATE TABLES I HATE TABLES I HA(╯°□°)╯︵ ┻━┻ TABLES I HATE TABLES I HATE TABLES
|
|
|
Advertised sites are not endorsed by the Bitcoin Forum. They may be unsafe, untrustworthy, or illegal in your jurisdiction.
|
|
|
AliBah
Newbie

 Offline Offline
Activity: 24
Merit: 0

|
 |
March 28, 2024, 06:26:37 PM |
|
Im using this command :
.\keyhunt.exe -m bsgs -f keys.txt -b 130 -t 4 -s 10 -k 256 -S
should i change something or this is my power and i cant do anything more ?
Your problem is the .exe and windows stuff Don use it on windows, compile it your self in a WSL environment or native linux The lastest version is Version 0.2.230519 Satoshi Quest it provide an increment of speed X2 compared with previous version thank you, i will try |
|
|
|
|
nomachine
Member
 
 Offline Offline
Activity: 243
Merit: 12

|
 |
March 28, 2024, 07:22:02 PM
Last edit: March 28, 2024, 07:47:45 PM by nomachine |
|
# ./keyhunt -m bsgs -f 65.txt -t 12 -k 4096 -l compress -b 65 -S -q -S -e - Version 0.2.230519 Satoshi Quest, developed by AlbertoBSD
- Threads : 12
- K factor 4096
- Search compress only
- Quiet thread output
- Endomorphism enabled
- Mode BSGS sequential
- Opening file 65.txt
- Added 1 points from file
- Bit Range 65
- -- from : 0x10000000000000000
- -- to : 0x20000000000000000
- N = 0x100000000000
- Bloom filter for 17179869184 elements : 58890.60 MB
- Bloom filter for 536870912 elements : 1840.33 MB
- Bloom filter for 16777216 elements : 57.51 MB
- Allocating 256.00 MB for 16777216 bP Points
- Reading bloom filter from file keyhunt_bsgs_4_17179869184.blm .... Done!
- Reading bloom filter from file keyhunt_bsgs_6_536870912.blm .... Done!
- Reading bP Table from file keyhunt_bsgs_2_16777216.tbl .... Done!
- Reading bloom filter from file keyhunt_bsgs_7_16777216.blm .... Done!
- Thread Key found privkey 1a838b13505b26867
- Publickey 0230210c23b1a047bc9bdbb13448e67deddc108946de6de639bcc75d47c0216b1b
All points were found It takes about 10 seconds to find after the files are loaded. AMD Ryzen 5 3600 / 64GB RAM *It even depends on how it is compiled for which platform - for example: gcc -Q -march=native --help=target | grep -E '^\s+-.*(sse|march)' -march= znver2 -mfpmath= sse -mno-sse4 [disabled] -msse4.2 [enabled] -msse4a [enabled] -msse5 -mavx -msseregparm [disabled] -mssse3 [enabled] Makefile g++ -m64 -march=native -mtune=native -msse4.2 ...etc... |
|
|
|
|
AliBah
Newbie

 Offline Offline
Activity: 24
Merit: 0

|
 |
March 28, 2024, 07:44:44 PM |
|
Im using this command :
.\keyhunt.exe -m bsgs -f keys.txt -b 130 -t 4 -s 10 -k 256 -S
should i change something or this is my power and i cant do anything more ?
Your problem is the .exe and windows stuff Don use it on windows, compile it your self in a WSL environment or native linux The lastest version is Version 0.2.230519 Satoshi Quest it provide an increment of speed X2 compared with previous version Thank you for your advise , now im in WSL and i did everything exactly from your github, but after 10 min the processing is sill in 0 ali@DESKTOP-HVET2KH:~/keyhunt$ ./keyhunt -m bsgs -f key.txt -b 130 -t 4 -s 5 -k 256 -S - Version 0.2.230519 Satoshi Quest, developed by AlbertoBSD
- Threads : 4
- Stats output every 5 seconds
- K factor 256
- Mode BSGS sequential
- Opening file key.txt
- Added 1 points from file
- Bit Range 130
- -- from : 0x200000000000000000000000000000000
- -- to : 0x400000000000000000000000000000000
- N = 0x100000000000
- Bloom filter for 1073741824 elements : 3680.66 MB
- Bloom filter for 33554432 elements : 115.02 MB
- Bloom filter for 1048576 elements : 3.59 MB
- Allocating 16.00 MB for 1048576 bP Points
- processing 0/1073741824 bP points : 0%
whats the problem now? |
|
|
|
|
|
|
hellishgoblin234
Newbie

 Offline Offline
Activity: 4
Merit: 0

|
 |
March 29, 2024, 06:54:42 AM |
|
Hi
What if someone found the key and spent the btc to another wallet ( i know, pubkey...) but with a super high tx fee, like extremely high.
|
|
|
|
|
AliBah
Newbie

 Offline Offline
Activity: 24
Merit: 0

|
 |
March 29, 2024, 08:49:02 AM |
|
I tried to import a private key into bitcoin core but i got this error :
Only legacy wallets are supported by this command (code -4)
what should i do now?
|
|
|
|
|
cloakdagger
Newbie

 Offline Offline
Activity: 25
Merit: 0

|
 |
March 29, 2024, 12:25:59 PM |
|
Looks like the method involves selecting a random number within a specified range defined by the number of bits of entropy. E.g. each output (or Bitcoin address) corresponds to a private key that was generated by selecting a random number within the range of (2^n-1) to (2^n)-1 , where n is the number of bits of entropy designated for that particular key. So that range ensures that the selected number has exactly n bits when represented in binary form matching the pattern of increasing entropy with each subsequent address. Each subsequent address uses a private key with one additional bit of entropy than the previous one.
The selection of the specific private key within that range is random. To generate or guess the next unclaimed output's private key (e.g., for the address with a 51-bit key), one would theoretically need to try all possible values within the range from (2^50) to (2^51)-1. By using a sufficiently high number of entropy bits, a quantum machine might be needed to brute-force through all possible keys in this range.
|
|
|
|
|
|
albert0bsd
|
 |
March 29, 2024, 12:55:24 PM |
|
What if someone found the key and spent the btc to another wallet ( i know, pubkey...) but with a super high tx fee, like extremely high.
Which key? puzzle key? 66? If the 66 key is spent it may enter in some bot fight each one will increase the fees compared to other until there is nothing left to spent but the final result is unknown Not always the higher fee wins, chek my previous reply to this: Just to mention that when the nodes have many FullRBF transacions not always win that one with more fee, here some examples, Dot with Green margin was mined, some are Testnet and other are mainnet 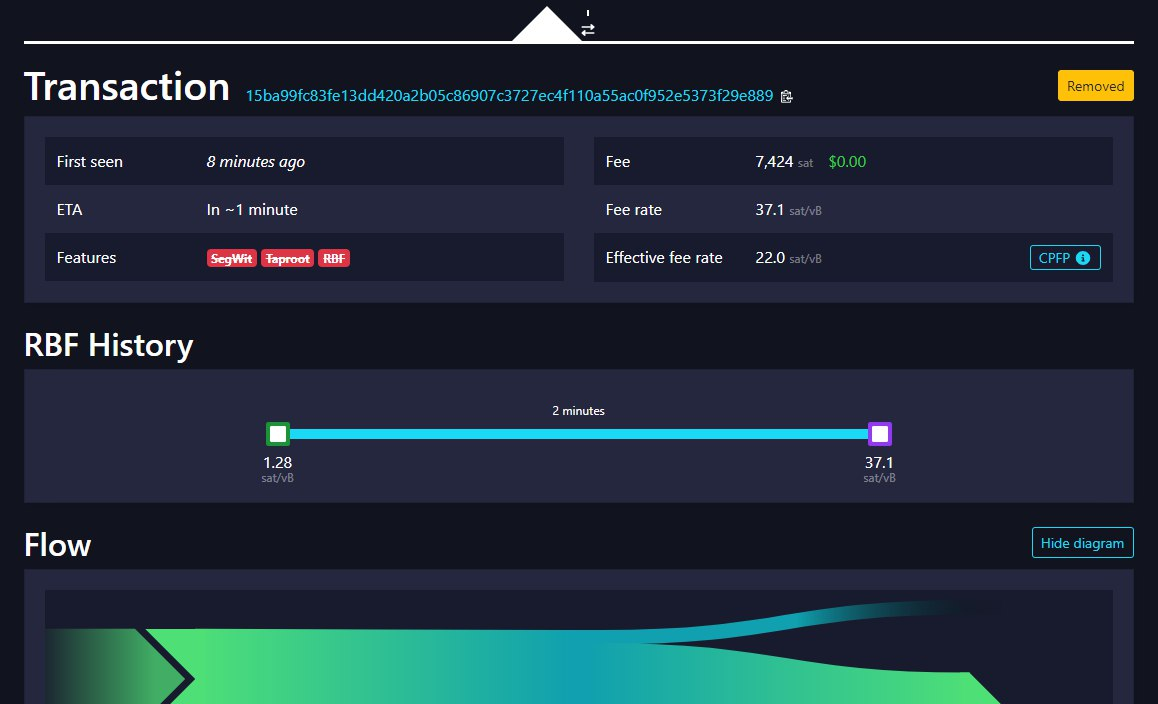 Here was mined a TX with 1 sat/vB instead of a 37 sat/vB 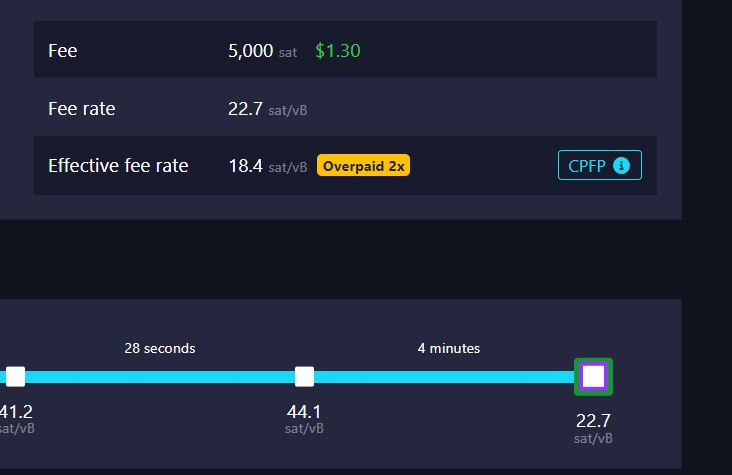 Here was mined a TX with 22 sat/vB instead of a 44 sat/vB 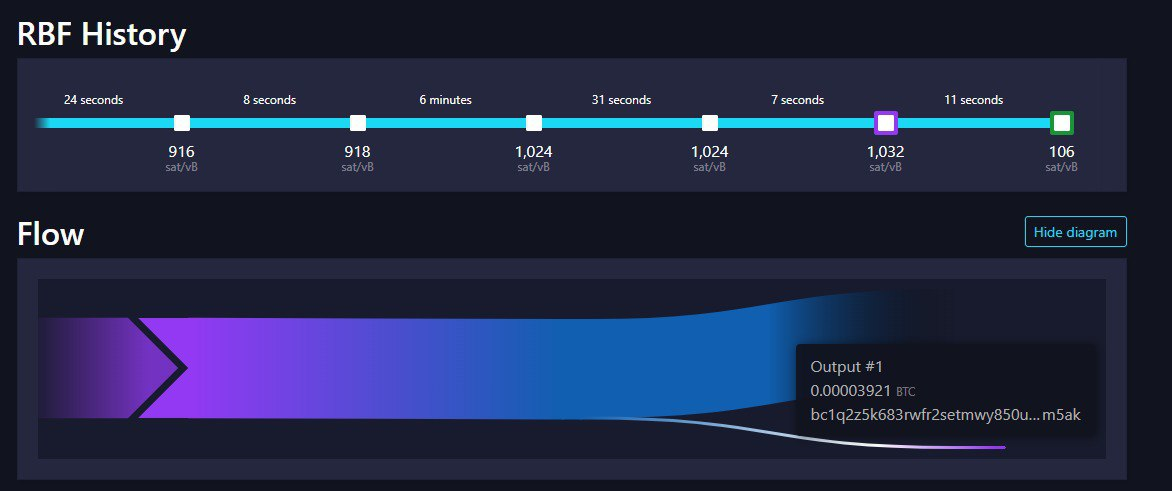 Here was mined a TX with 106 sat/vB instead of a 1032 sat/vB All depens of what is the transaction that the miner selected to work with his hardware. I tried to import a private key into bitcoin core but i got this error :
Only legacy wallets are supported by this command (code -4)
what should i do now?
If you don't show what command do you used, then there is no way to know what is wrong. What kind of address are you trying to import? it looks like it is not a legacy one. |
|
|
|
AliBah
Newbie

 Offline Offline
Activity: 24
Merit: 0

|
 |
March 29, 2024, 02:44:04 PM
Last edit: March 31, 2024, 08:30:38 PM by Mr. Big |
|
What if someone found the key and spent the btc to another wallet ( i know, pubkey...) but with a super high tx fee, like extremely high.
Which key? puzzle key? 66? If the 66 key is spent it may enter in some bot fight each one will increase the fees compared to other until there is nothing left to spent but the final result is unknown Not always the higher fee wins, chek my previous reply to this: All depens of what is the transaction that the miner selected to work with his hardware. I tried to import a private key into bitcoin core but i got this error :
Only legacy wallets are supported by this command (code -4)
what should i do now?
If you don't show what command do you used, then there is no way to know what is wrong. What kind of address are you trying to import? it looks like it is not a legacy one. I tried to test this: HEX fffffffffffffffffffffffffffffffebaaedce6af48a03bbfd25e8cd0364140 WIF(c) L5oLkpV3aqBjhki6LmvChTCV6odsp4SXM6FfU2Gppt5kFLaHLuZ9 WIF(u) 5Km2kuu7vtFDPpxywn4u3NLpbr5jKpTB3jsuDU2KYEqetqj84qw by this command : importprivkey
Finally i found how to import wallets, but whats this error now... errors killing me haha importdescriptors "[{\"desc\": \"wpkh(L5oLkpV3aqBjhki6LmvChTCV6odsp4SXM6FfU2Gppt5kFLaHLuZ9)#c9eja2dd\", \"timestamp\": 0}]" [ { "success": false, "error": { "code": -1, "message": "Rescan failed for descriptor with timestamp 0. There was an error reading a block from time 1711177032, which is after or within 7200 seconds of key creation, and could contain transactions pertaining to the desc. As a result, transactions and coins using this desc may not appear in the wallet. This error could be caused by pruning or data corruption (see bitcoind log for details) and could be dealt with by downloading and rescanning the relevant blocks (see -reindex option and rescanblockchain RPC)." } } ] |
|
|
|
|
mkd097
Newbie

 Offline Offline
Activity: 1
Merit: 0

|
 |
March 29, 2024, 04:09:27 PM |
|
What program supports bulk HEX range list for scanning Bitcoin addresses?
|
|
|
|
|
jacky19790729
Jr. Member

 Offline Offline
Activity: 56
Merit: 8

|
 |
March 29, 2024, 07:56:10 PM
Last edit: March 29, 2024, 08:17:49 PM by jacky19790729 |
|
Address = 13zb1hQbWVuYdZoAkztVrNrm65aReL2pYD
Message = I own this address
Signature = HxSDzJj3BhS8lh7qoU1L9zJsymorFkJv8/roi8o6+269PEDPr8psAE1QEOerWAWKv/ypXss7hhXEe0FutUR4b0s=
your address: 13zb1hQbWVuYdZoAkztVrNrm65aReL2pYD public key: 03f3fb41f466d9893e5af7dfd788211b0503eb38d49615a19aa22b419ed4ff308d private key: 0x2CA8A08241FC8D6EF    10 char match #66 |
|
|
|
|
jacky19790729
Jr. Member

 Offline Offline
Activity: 56
Merit: 8

|
 |
March 29, 2024, 08:19:43 PM |
|
I tried to test this:
HEX fffffffffffffffffffffffffffffffebaaedce6af48a03bbfd25e8cd0364140
WIF(c) L5oLkpV3aqBjhki6LmvChTCV6odsp4SXM6FfU2Gppt5kFLaHLuZ9
WIF(u) 5Km2kuu7vtFDPpxywn4u3NLpbr5jKpTB3jsuDU2KYEqetqj84qw
by this command : importprivkey
importprivkey L5oLkpV3aqBjhki6LmvChTCV6odsp4SXM6FfU2Gppt5kFLaHLuZ9 "" false |
|
|
|
|
|
albert0bsd
|
 |
March 29, 2024, 08:22:30 PM
Last edit: March 29, 2024, 08:34:32 PM by albert0bsd |
|
your address: 13zb1hQbWVuYdZoAkztVrNrm65aReL2pYD
Try to quote from the person who post it in first place. Good that you also found the key, but you spoil it. You just removed the fun for others. It would be better another signed message no? Quoting to the user who post it: Address = 13zb1hQbWVuYdZoAkztVrNrm65aReL2pYD
Message = I own this address
Signature = HxSDzJj3BhS8lh7qoU1L9zJsymorFkJv8/roi8o6+269PEDPr8psAE1QEOerWAWKv/ypXss7hhXEe0FutUR4b0s=
|
|
|
|
hellishgoblin234
Newbie

 Offline Offline
Activity: 4
Merit: 0

|
 |
March 30, 2024, 07:12:21 PM |
|
Not always the higher fee wins, chek my previous reply to this:
Thank you, very interesting. Yes, regarding puzzle #66. So, what would be the safest way to spend the coins to another wallet then? I mean, what is even the point of spending time & resources on finding the privkey if it is then impossible to spend the coins (or at least most of them) to another wallet safely because an army of monitoring agents will attempt to steal the coins by cracking the privkey using kangoroo with the newly avail. pubkey. |
|
|
|
|
AndrewWeb
Jr. Member

 Offline Offline
Activity: 43
Merit: 1

|
 |
March 30, 2024, 09:01:15 PM |
|
Thank you, very interesting.
Yes, regarding puzzle #66. So, what would be the safest way to spend the coins to another wallet then?
I mean, what is even the point of spending time & resources on finding the privkey if it is then impossible to spend the coins (or at least most of them) to another wallet safely because an army of monitoring agents will attempt to steal the coins by cracking the privkey using kangoroo with the newly avail. pubkey.
Solve a Bitcoin block, then include your transaction within the block you solved. If you're not a Bitcoin miner, find a Bitcoin miner to do it for you. |
|
|
|
|
brainless
Member
 
 Offline Offline
Activity: 318
Merit: 34

|
 |
March 31, 2024, 03:46:13 PM |
|
Thank you, very interesting.
Yes, regarding puzzle #66. So, what would be the safest way to spend the coins to another wallet then?
I mean, what is even the point of spending time & resources on finding the privkey if it is then impossible to spend the coins (or at least most of them) to another wallet safely because an army of monitoring agents will attempt to steal the coins by cracking the privkey using kangoroo with the newly avail. pubkey.
Solve a Bitcoin block, then include your transaction within the block you solved. If you're not a Bitcoin miner, find a Bitcoin miner to do it for you. Or you can share coins with me for safe tx |
13sXkWqtivcMtNGQpskD78iqsgVy9hcHLF
|
|
|
Feron
Jr. Member

 Offline Offline
Activity: 42
Merit: 1

|
 |
March 31, 2024, 05:00:56 PM |
|
when someone solves it, they just take it, no stress
|
|
|
|
|
satashi_nokamato
Jr. Member

 Offline Offline
Activity: 48
Merit: 2

|
 |
March 31, 2024, 05:13:17 PM |
|
Finally i found how to import wallets, but whats this error now... errors killing me haha
importdescriptors "[{\"desc\": \"wpkh(L5oLkpV3aqBjhki6LmvChTCV6odsp4SXM6FfU2Gppt5kFLaHLuZ9)#c9eja2dd\", \"timestamp\": 0}]"
[
{
"success": false,
"error": {
"code": -1,
"message": "Rescan failed for descriptor with timestamp 0. There was an error reading a block from time 1711177032, which is after or within 7200 seconds of key creation, and could contain transactions pertaining to the desc. As a result, transactions and coins using this desc may not appear in the wallet. This error could be caused by pruning or data corruption (see bitcoind log for details) and could be dealt with by downloading and rescanning the relevant blocks (see -reindex option and rescanblockchain RPC)."
}
}
]
I believe Bitcoin core client refuses to import 1 and -1 keys, so you can't import those 2 keys. |
|
|
|
|
zahid888
Member
 
 Offline Offline
Activity: 261
Merit: 19
the right steps towerds the goal

|
 |
April 01, 2024, 03:03:19 PM |
|
from cryptography.fernet import Fernet
from cryptography.hazmat.backends import default_backend
from cryptography.hazmat.primitives import hashes
from cryptography.hazmat.primitives.kdf.pbkdf2 import PBKDF2HMAC
import base64
import os
import getpass
# Function to generate a key from the password
def key_from_password(password, salt):
kdf = PBKDF2HMAC(
algorithm=hashes.SHA256(),
length=32,
salt=salt,
iterations=100000,
backend=default_backend()
)
key = base64.urlsafe_b64encode(kdf.derive(password.encode()))
return key
# Encrypt the message
def encrypt_message(message, password):
salt = os.urandom(16)
key = key_from_password(password, salt)
fernet = Fernet(key)
encrypted = fernet.encrypt(message.encode())
return encrypted, salt
# Decrypt the message
def decrypt_message(encrypted_message, password, salt):
key = key_from_password(password, salt)
fernet = Fernet(key)
try:
decrypted = fernet.decrypt(encrypted_message).decode()
return decrypted
except Exception as e:
return "Error: " + str(e)
# Main interface
if __name__ == "__main__":
choice = input("Do you want to encrypt or decrypt a message? (encrypt/decrypt): ")
if choice == "encrypt":
secret_message = input("Enter your secret message: ")
password = getpass.getpass("Enter a password for encryption: ")
encrypted_message, salt = encrypt_message(secret_message, password)
print("Your encrypted message is:")
print(encrypted_message.decode())
print("Your salt (needed for decryption) is:")
print(base64.b64encode(salt).decode())
elif choice == "decrypt":
encrypted_message_input = input("Enter the encrypted message: ")
salt_input = base64.b64decode(input("Enter the salt: "))
password = getpass.getpass("Enter the password for decryption: ")
decrypted_message = decrypt_message(encrypted_message_input.encode(), password, salt_input)
print("Your decrypted message is:")
print(decrypted_message)
else:
print("Invalid choice. Please type 'encrypt' or 'decrypt'.")
Example:Encrypted message is: gAAAAABmCsIhWZe1vm94Ma4p6v3hv8LmP5JuvhsA1qI65TK_X2LolyNqEFr2y2yZyORoi5KuVubjyay nScTIfAKrqBka17jslzoHfVTB7-c1fgx-qjbjTbDEDUG5vlCE0qy5uOgqBYG4jt5b9gxnhBdVLL3qc2e7nw==-c1fgx-qjbjTbDEDUG5vlCE0qy5uOgqBYG4jt5b9gxnhBdVLL3qc2e7nw== Salt (needed for decryption) is: IJZVtFg2B1u5r/A1bsk/TA== The password for decryption is: password
Whoever manages to obtain the private key for Puzzle 66. Is requested to encrypt it using this script and post the encrypted message here. Post only the encrypted message, and keep the salt and password to yourself. Then, proceed to complete your transaction process after few days. If, for any reason, the transaction fails to validate and someone else hijacks it, You are encouraged to post your salt and password here as evidence that you had solved Puzzle 66. This will enable the entire community to potentially pursue legal action against the thief. Therefore, anyone attempting to undermine someone else's hard work is hereby warned. @alberto or any other member, if you discover any vulnerabilities here or are capable of cracking this script, please inform us. Additionally, if there are any alternative implementations, kindly share those as well. |
1BGvwggxfCaHGykKrVXX7fk8GYaLQpeixA
|
|
|
|




