shelby0930
Newbie

 Offline Offline
Activity: 24
Merit: 4

|
 |
March 27, 2024, 11:59:40 PM |
|
So who has reached the closest to 130 puzzle?
|
|
|
|
|
|
|
|
|
|
|
|
Remember that Bitcoin is still beta software. Don't put all of your money into BTC!
|
|
|
Advertised sites are not endorsed by the Bitcoin Forum. They may be unsafe, untrustworthy, or illegal in your jurisdiction.
|
|
|
|
|
|
|
|
albert0bsd
|
 |
March 28, 2024, 02:55:13 AM |
|
So who has reached the closest to 130 puzzle?
There is no way to know, only until you hit the key |
|
|
|
Feron
Jr. Member

 Offline Offline
Activity: 42
Merit: 1

|
 |
March 28, 2024, 08:32:40 AM |
|
which processor is faster amd ryzen or intel in python intel core i9 14900hx---intel core i9-13980hx---amd ryzen 9 7945hx, does anyone have any experience with how fast your processors with iceland secp256k1 library go
I know it depends on the code settings, but it would be nice to know such approximate information
|
|
|
|
|
AndrewWeb
Jr. Member

 Offline Offline
Activity: 43
Merit: 1

|
 |
March 28, 2024, 09:07:25 AM |
|
There are private keys , public keys and addresses. These are three different things.
You can use BSGS or Kangaroo modes only on public keys but not on addresses.
The known public keys in this whole challenge were intentionally released by it's creator.
If you see an outgoing transactions in given address history you can easily check it's public key and try the BSGS or Kangaroo modes.
When you have just address without any outgoing transactions your only method is to blindly guessing private keys in hope you will find one which corresponds to address.
Currently finding 66bit privkey without knows public key can be considered as hard as finding 130bit privkey with public key known.
Ok, but what is it that makes having the public key so much easier to find the privat key ? What role does the public key play ? What is it about the public key, that helps the program find the privat key ? What does the public key tell the program, that makes is easier to find the privat key ? Does the letters and numbers of the public key have anything to say, or what is it ? Why is it not blindly when you have the public key ? What do you see, when you have the public key ? |
|
|
|
|
|
albert0bsd
|
 |
March 28, 2024, 11:26:13 AM |
|
Ok, but what is it that makes having the public key so much easier to find the privat key ? What role does the public key play ? What is it about the public key, that helps the program find the privat key ? What does the public key tell the program, that makes is easier to find the privat key ? Does the letters and numbers of the public key have anything to say, or what is it ? Why is it not blindly when you have the public key ? What do you see, when you have the public key ?
We can do some basic arithmetic operations (blindly) with them. But this is only useful when you know some information about the privatekey like the range ( smallest ranges are easy) Please read : https://andrea.corbellini.name/2015/06/08/elliptic-curve-cryptography-breaking-security-and-a-comparison-with-rsa/ |
|
|
|
satashi_nokamato
Jr. Member

 Offline Offline
Activity: 49
Merit: 3

|
 |
March 28, 2024, 02:16:45 PM |
|
What do you see, when you have the public key ?
What do you see here? 3+2= 5, 3*2= 6, 6/3= 2, 2-3= 1, 3-2= -1. Now we have public key of 1, 2, 3, 4, 5, 6. Add, divide, subtract and multiply, it all works the same whether you do it with public keys of the private keys, or you just do them directly with private keys. In other words, if you have the public key of private key 89, then by having 1 up to 9 public keys saved, you could solve the private key after subtracting G 80 times from 89, when you reach public key of 9 after 80 steps then you know the target's value. It works the same with multiplying, dividing etc. |
|
|
|
|
unclevito
Jr. Member

 Offline Offline
Activity: 74
Merit: 4


|
 |
March 28, 2024, 02:37:17 PM |
|
What do you see, when you have the public key ?
What do you see here? 3+2= 5, 3*2= 6, 6/3= 2, 2-3= 1, 3-2= -1. Now we have public key of 1, 2, 3, 4, 5, 6. Add, divide, subtract and multiply, it all works the same whether you do it with public keys of the private keys, or you just do them directly with private keys. In other words, if you have the public key of private key 89, then by having 1 up to 9 public keys saved, you could solve the private key after subtracting G 80 times from 89, when you reach public key of 9 after 80 steps then you know the target's value. It works the same with multiplying, dividing etc. “if you knew the magnificence of 3, 6 and 9, you would have a key to the universe.” Nikola Tesla |
|
|
|
|
nomachine
Member
 
 Offline Offline
Activity: 255
Merit: 12

|
 |
March 28, 2024, 02:47:22 PM
Last edit: March 28, 2024, 02:58:07 PM by nomachine |
|
which processor is faster amd ryzen or intel in python intel core i9 14900hx---intel core i9-13980hx---amd ryzen 9 7945hx, does anyone have any experience with how fast your processors with iceland secp256k1 library go
I know it depends on the code settings, but it would be nice to know such approximate information
This is a demonstration and test of how slow Python is. Even if it's a few million keys per second. Random sequence: from multiprocessing.pool import Pool
from subprocess import check_output
from tqdm import tqdm
from tqdm.contrib.concurrent import process_map
import secp256k1 as ice
import math
import random
import sys
div=16384
start=0x20000000000000000
end=0x3ffffffffffffffff
rng=0x3ffffffffffffffff-0x20000000000000000
stepout=int(rng/div)
stepin=0x200000000
right='13zb1hQbWVsc2S7ZTZnP2G4undNNpdh5so'
sys.stdout.write("\033[01;33m")
print('[+] target: '+right)
def int_to_bytes3(value, length = None): # in: int out: bytearray(b'\x80...
if not length and value == 0:
result = [0]
else:
result = []
for i in range(0, length or 1+int(math.log(value, 2**8))):
result.append(value >> (i * 8) & 0xff)
result.reverse()
return bytearray(result)
def pvk_to_addr(pvk):
return ice.privatekey_to_address(0, True, pvk)
global c
c = 0
def go(r):
global c
if c % 100 == 0:
print(f'[+] {c:,} Keys\r'.replace(',', ' '), end='')
c = c + 1
by = int_to_bytes3(r, 32)
pvk = int.from_bytes(by, byteorder='big') # Convert bytearray to integer
ad = pvk_to_addr(pvk)
# print('\r'+ad,end='')
if ad == right:
print('found!')
print(r)
print(hex(r))
HEX = "%064x" % int(r)
wifc = ice.btc_pvk_to_wif(HEX)
print(wifc)
print('\a')
with open('found.txt', 'w') as f:
f.write(str(r))
f.write('\n')
f.write(hex(r))
f.write('\n')
f.write(wifc)
f.write('\n')
f.flush()
sys.exit(0)
return
def n(a,b):
return list(range(a,b))
s=int(rng/div)
pool = Pool(10)
u=1048576
while True:
ra=random.randint(start,end-u)
rb=ra+u
print(f'\r[+] from: {hex(ra)} to: {hex(rb)} range: {hex(u)}={u}')
#global c
c=0
pool.map(go, range(ra,rb), chunksize=32768)
pool.close()
pool.join() Sequential sequence: from multiprocessing.pool import Pool
from subprocess import check_output
from tqdm import tqdm
from tqdm.contrib.concurrent import process_map
import secp256k1 as ice
import math
import random
import sys
div=16384
start=0x20000000000000000
end=0x3ffffffffffffffff
rng=0x3ffffffffffffffff-0x20000000000000000
stepout=int(rng/div)
stepin=0x200000000
right='13zb1hQbWVsc2S7ZTZnP2G4undNNpdh5so'
sys.stdout.write("\033[01;33m")
print('[+] target: '+right)
def int_to_bytes3(value, length = None): # in: int out: bytearray(b'\x80...
if not length and value == 0:
result = [0]
else:
result = []
for i in range(0, length or 1+int(math.log(value, 2**8))):
result.append(value >> (i * 8) & 0xff)
result.reverse()
return bytearray(result)
def pvk_to_addr(pvk):
return ice.privatekey_to_address(0, True, pvk)
global c
c = 0
def go(r):
global c
if c % 100 == 0:
print(f'[+] {c:,} Keys\r'.replace(',', ' '), end='')
c = c + 1
by = int_to_bytes3(r, 32)
pvk = int.from_bytes(by, byteorder='big') # Convert bytearray to integer
ad = pvk_to_addr(pvk)
# print('\r'+ad,end='')
if ad == right:
print('found!')
print(r)
print(hex(r))
HEX = "%064x" % int(r)
wifc = ice.btc_pvk_to_wif(HEX)
print(wifc)
print('\a')
with open('found.txt', 'w') as f:
f.write(str(r))
f.write('\n')
f.write(hex(r))
f.write('\n')
f.write(wifc)
f.write('\n')
f.flush()
sys.exit(0)
return
def n(a,b):
return list(range(a,b))
s=int(rng/div)
pool = Pool(10)
u = 1048576
for ra in range(start, end - u + 1, u):
rb = ra + u
print(f'\r[+] from: {hex(ra)} to: {hex(rb)} range: {hex(u)}={u}')
c = 0
pool.map(go, range(ra, rb), chunksize=32768)
pool.close()
pool.join() You can test with this... Very slow. About a million keys per core. Just for the sake of comparison, I have about 40 Mkeys/s on BSGS with 12 Cores in address mode..... |
|
|
|
|
AliBah
Newbie

 Offline Offline
Activity: 25
Merit: 0

|
 |
March 28, 2024, 05:09:36 PM |
|
Ok, but what is it that makes having the public key so much easier to find the privat key ? What role does the public key play ? What is it about the public key, that helps the program find the privat key ? What does the public key tell the program, that makes is easier to find the privat key ? Does the letters and numbers of the public key have anything to say, or what is it ? Why is it not blindly when you have the public key ? What do you see, when you have the public key ?
We can do some basic arithmetic operations (blindly) with them. But this is only useful when you know some information about the privatekey like the range ( smallest ranges are easy) Please read : https://andrea.corbellini.name/2015/06/08/elliptic-curve-cryptography-breaking-security-and-a-comparison-with-rsa/for puzzle 66 i used bsgs with i7 7500U and that took 30 min to scan all the range. is it normal or i missed something to make my scan faster? |
|
|
|
|
|
albert0bsd
|
 |
March 28, 2024, 05:43:34 PM |
|
for puzzle 66 i used bsgs with i7 7500U and that took 30 min to scan all the range.
is it normal or i missed something to make my scan faster?
Well in the case of Keyhunt BSGS the speed is made by a combination of CPU Generation, Number of Thread and Memory available Also some other considerations Like: Is the blooom filter File already available? , with the -S parameter you triger the load or creation of files just to be available the next time of execution In mi case with bloom filter files available My laptop: "11th Gen Intel(R) Core(TM) i5-1145G7 @ 2.60GHz" with 8 GB of RAM and 8 threads the program found the test key in 5 minutes My PC: 13th Gen Intel Core i7-13700 with 32 GB of RAM and 24 threads the program found the test key in less than 1 minute and the same PC with the BSGS server the program found the test key in less than 20 seconds (The difference here is that the files are already loaded in memory) For keyhunt issues/doubts/talk please use the next topic: Keyhunt - development requests - bug reports |
|
|
|
AliBah
Newbie

 Offline Offline
Activity: 25
Merit: 0

|
 |
March 28, 2024, 06:12:13 PM |
|
for puzzle 66 i used bsgs with i7 7500U and that took 30 min to scan all the range.
is it normal or i missed something to make my scan faster?
Well in the case of Keyhunt BSGS the speed is made by a combination of CPU Generation, Number of Thread and Memory available Also some other considerations Like: Is the blooom filter File already available? , with the -S parameter you triger the load or creation of files just to be available the next time of execution In mi case with bloom filter files available My laptop: "11th Gen Intel(R) Core(TM) i5-1145G7 @ 2.60GHz" with 8 GB of RAM and 8 threads the program found the test key in 5 minutes My PC: 13th Gen Intel Core i7-13700 with 32 GB of RAM and 24 threads the program found the test key in less than 1 minute and the same PC with the BSGS server the program found the test key in less than 20 seconds (The difference here is that the files are already loaded in memory) For keyhunt issues/doubts/talk please use the next topic: Keyhunt - development requests - bug reports Yes the the bloom filter file is ready, and my cpu is 7th Gen and Ram is 8. for puzzle 130 my speed is (10Pkeys/s) Im using this command : .\keyhunt.exe -m bsgs -f keys.txt -b 130 -t 4 -s 10 -k 256 -S should i change something or this is my power and i cant do anything more ? |
|
|
|
|
|
albert0bsd
|
 |
March 28, 2024, 06:16:41 PM |
|
Im using this command :
.\keyhunt.exe -m bsgs -f keys.txt -b 130 -t 4 -s 10 -k 256 -S
should i change something or this is my power and i cant do anything more ?
Your problem is the .exe and windows stuff Don use it on windows, compile it your self in a WSL environment or native linux The lastest version is Version 0.2.230519 Satoshi Quest it provide an increment of speed X2 compared with previous version |
|
|
|
AliBah
Newbie

 Offline Offline
Activity: 25
Merit: 0

|
 |
March 28, 2024, 06:26:37 PM |
|
Im using this command :
.\keyhunt.exe -m bsgs -f keys.txt -b 130 -t 4 -s 10 -k 256 -S
should i change something or this is my power and i cant do anything more ?
Your problem is the .exe and windows stuff Don use it on windows, compile it your self in a WSL environment or native linux The lastest version is Version 0.2.230519 Satoshi Quest it provide an increment of speed X2 compared with previous version thank you, i will try |
|
|
|
|
nomachine
Member
 
 Offline Offline
Activity: 255
Merit: 12

|
 |
March 28, 2024, 07:22:02 PM
Last edit: March 28, 2024, 07:47:45 PM by nomachine |
|
# ./keyhunt -m bsgs -f 65.txt -t 12 -k 4096 -l compress -b 65 -S -q -S -e - Version 0.2.230519 Satoshi Quest, developed by AlbertoBSD
- Threads : 12
- K factor 4096
- Search compress only
- Quiet thread output
- Endomorphism enabled
- Mode BSGS sequential
- Opening file 65.txt
- Added 1 points from file
- Bit Range 65
- -- from : 0x10000000000000000
- -- to : 0x20000000000000000
- N = 0x100000000000
- Bloom filter for 17179869184 elements : 58890.60 MB
- Bloom filter for 536870912 elements : 1840.33 MB
- Bloom filter for 16777216 elements : 57.51 MB
- Allocating 256.00 MB for 16777216 bP Points
- Reading bloom filter from file keyhunt_bsgs_4_17179869184.blm .... Done!
- Reading bloom filter from file keyhunt_bsgs_6_536870912.blm .... Done!
- Reading bP Table from file keyhunt_bsgs_2_16777216.tbl .... Done!
- Reading bloom filter from file keyhunt_bsgs_7_16777216.blm .... Done!
- Thread Key found privkey 1a838b13505b26867
- Publickey 0230210c23b1a047bc9bdbb13448e67deddc108946de6de639bcc75d47c0216b1b
All points were found It takes about 10 seconds to find after the files are loaded. AMD Ryzen 5 3600 / 64GB RAM *It even depends on how it is compiled for which platform - for example: gcc -Q -march=native --help=target | grep -E '^\s+-.*(sse|march)' -march= znver2 -mfpmath= sse -mno-sse4 [disabled] -msse4.2 [enabled] -msse4a [enabled] -msse5 -mavx -msseregparm [disabled] -mssse3 [enabled] Makefile g++ -m64 -march=native -mtune=native -msse4.2 ...etc... |
|
|
|
|
AliBah
Newbie

 Offline Offline
Activity: 25
Merit: 0

|
 |
March 28, 2024, 07:44:44 PM |
|
Im using this command :
.\keyhunt.exe -m bsgs -f keys.txt -b 130 -t 4 -s 10 -k 256 -S
should i change something or this is my power and i cant do anything more ?
Your problem is the .exe and windows stuff Don use it on windows, compile it your self in a WSL environment or native linux The lastest version is Version 0.2.230519 Satoshi Quest it provide an increment of speed X2 compared with previous version Thank you for your advise , now im in WSL and i did everything exactly from your github, but after 10 min the processing is sill in 0 ali@DESKTOP-HVET2KH:~/keyhunt$ ./keyhunt -m bsgs -f key.txt -b 130 -t 4 -s 5 -k 256 -S - Version 0.2.230519 Satoshi Quest, developed by AlbertoBSD
- Threads : 4
- Stats output every 5 seconds
- K factor 256
- Mode BSGS sequential
- Opening file key.txt
- Added 1 points from file
- Bit Range 130
- -- from : 0x200000000000000000000000000000000
- -- to : 0x400000000000000000000000000000000
- N = 0x100000000000
- Bloom filter for 1073741824 elements : 3680.66 MB
- Bloom filter for 33554432 elements : 115.02 MB
- Bloom filter for 1048576 elements : 3.59 MB
- Allocating 16.00 MB for 1048576 bP Points
- processing 0/1073741824 bP points : 0%
whats the problem now? |
|
|
|
|
|
|
hellishgoblin234
Newbie

 Offline Offline
Activity: 4
Merit: 0

|
 |
March 29, 2024, 06:54:42 AM |
|
Hi
What if someone found the key and spent the btc to another wallet ( i know, pubkey...) but with a super high tx fee, like extremely high.
|
|
|
|
|
AliBah
Newbie

 Offline Offline
Activity: 25
Merit: 0

|
 |
March 29, 2024, 08:49:02 AM |
|
I tried to import a private key into bitcoin core but i got this error :
Only legacy wallets are supported by this command (code -4)
what should i do now?
|
|
|
|
|
cloakdagger
Newbie

 Offline Offline
Activity: 25
Merit: 0

|
 |
March 29, 2024, 12:25:59 PM |
|
Looks like the method involves selecting a random number within a specified range defined by the number of bits of entropy. E.g. each output (or Bitcoin address) corresponds to a private key that was generated by selecting a random number within the range of (2^n-1) to (2^n)-1 , where n is the number of bits of entropy designated for that particular key. So that range ensures that the selected number has exactly n bits when represented in binary form matching the pattern of increasing entropy with each subsequent address. Each subsequent address uses a private key with one additional bit of entropy than the previous one.
The selection of the specific private key within that range is random. To generate or guess the next unclaimed output's private key (e.g., for the address with a 51-bit key), one would theoretically need to try all possible values within the range from (2^50) to (2^51)-1. By using a sufficiently high number of entropy bits, a quantum machine might be needed to brute-force through all possible keys in this range.
|
|
|
|
|
|
albert0bsd
|
 |
March 29, 2024, 12:55:24 PM |
|
What if someone found the key and spent the btc to another wallet ( i know, pubkey...) but with a super high tx fee, like extremely high.
Which key? puzzle key? 66? If the 66 key is spent it may enter in some bot fight each one will increase the fees compared to other until there is nothing left to spent but the final result is unknown Not always the higher fee wins, chek my previous reply to this: Just to mention that when the nodes have many FullRBF transacions not always win that one with more fee, here some examples, Dot with Green margin was mined, some are Testnet and other are mainnet 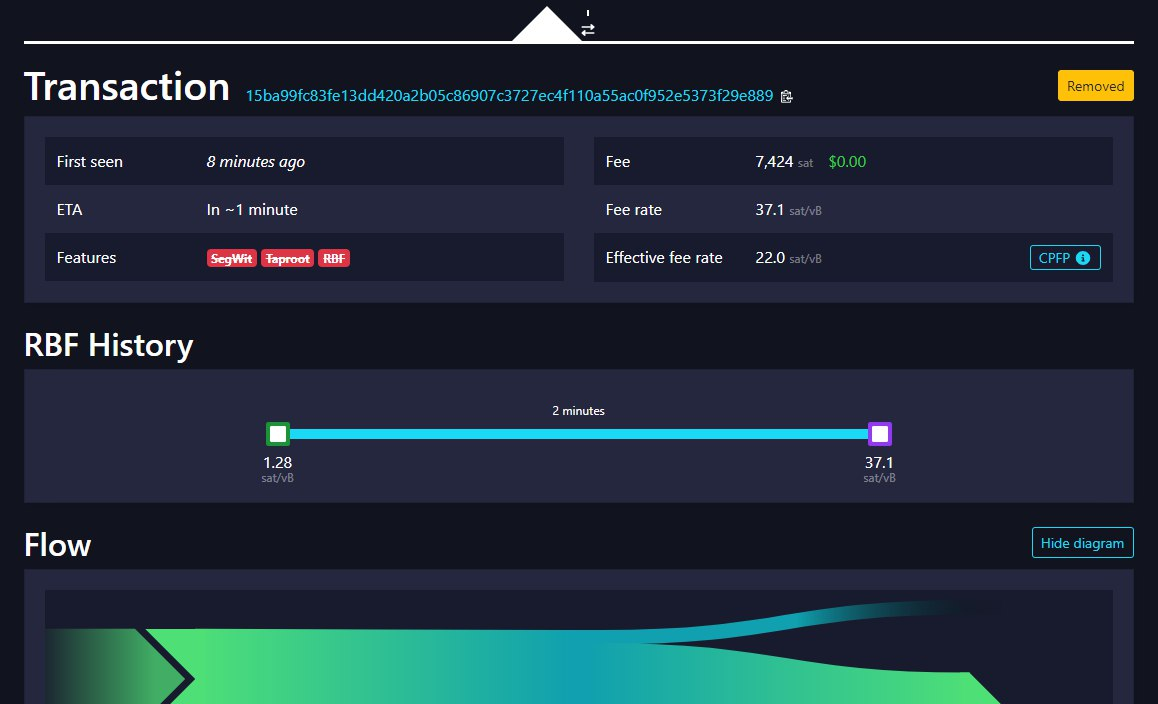 Here was mined a TX with 1 sat/vB instead of a 37 sat/vB 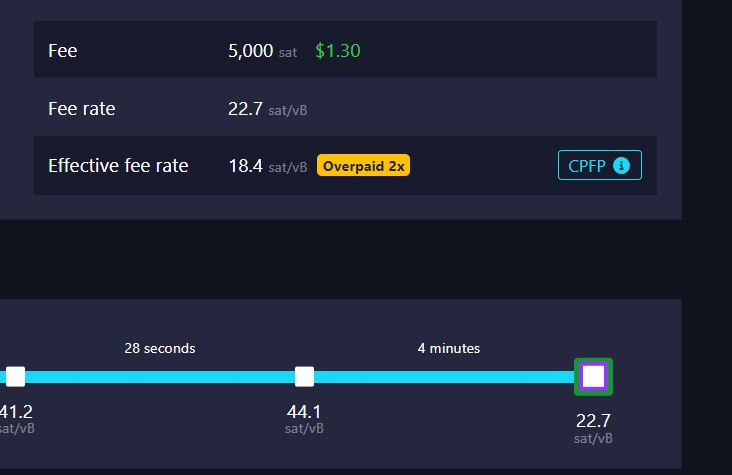 Here was mined a TX with 22 sat/vB instead of a 44 sat/vB 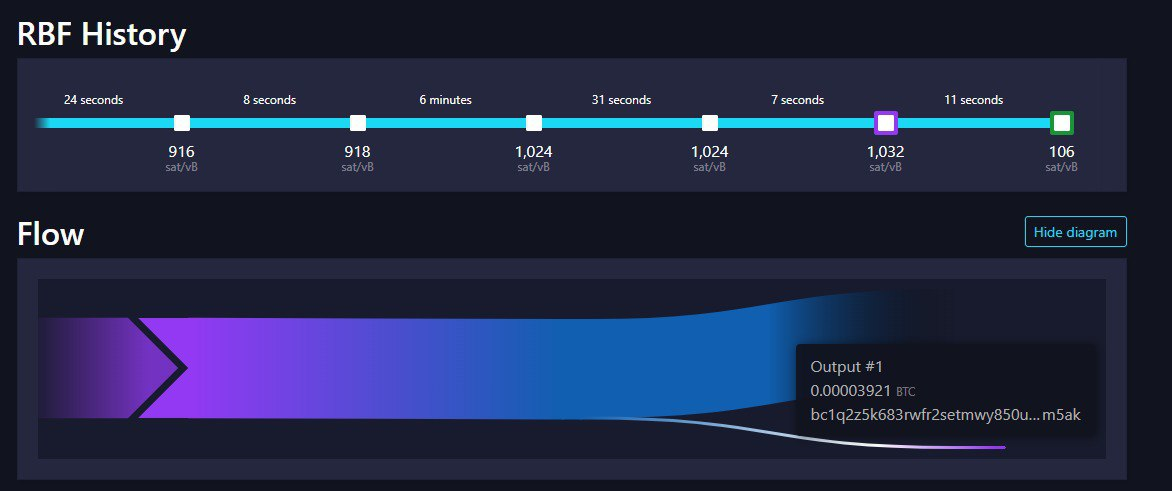 Here was mined a TX with 106 sat/vB instead of a 1032 sat/vB All depens of what is the transaction that the miner selected to work with his hardware. I tried to import a private key into bitcoin core but i got this error :
Only legacy wallets are supported by this command (code -4)
what should i do now?
If you don't show what command do you used, then there is no way to know what is wrong. What kind of address are you trying to import? it looks like it is not a legacy one. |
|
|
|
|




