|
citb0in
|
 |
February 08, 2024, 04:40:04 PM |
|
if you like the maximum possible speed than you need to go for C. This is primarily because C is a compiled language, while Python is an interpreted language. That means C code is compiled directly into machine code, which can be executed directly by the computer's hardware. On the other hand, Python code is interpreted, meaning that it's translated into bytecode by the Python interpreter and executed line by line at runtime. Additionally Python utilizes automatic memory management via garbage collection which can introduce overhead.
Frankly speaking, go for C if you like to achieve the best performnce. While C tends to be faster than Python in terms of raw performance, Python offers advantages such as ease of use. And as already mentioned, Rust is also interesting because it combines the performance of languages like C with the safety and concurrency features of modern languages.
|
.
.HUGE. | | | | | | █▀▀▀▀
█
█
█
█
█
█
█
█
█
█
█
█▄▄▄▄ | ▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀
.
CASINO & SPORTSBOOK
▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ | ▀▀▀▀█
█
█
█
█
█
█
█
█
█
█
█
▄▄▄▄█ | | |
|
|
|
|
|
Advertised sites are not endorsed by the Bitcoin Forum. They may be unsafe, untrustworthy, or illegal in your jurisdiction.
|
vklimin
Newbie

 Offline Offline
Activity: 4
Merit: 0

|
 |
February 08, 2024, 06:52:40 PM |
|
Thank you, colleagues, for suggesting Rust and C  , but for educational purposes, what is specifically required is Python code for CUDA that can brute-force keys. |
|
|
|
|
nomachine
Member
 
 Offline Offline
Activity: 243
Merit: 12

|
 |
February 09, 2024, 12:09:02 PM
Last edit: February 09, 2024, 12:28:52 PM by nomachine |
|
Thank you, colleagues, for suggesting Rust and C  , but for educational purposes, what is specifically required is Python code for CUDA that can brute-force keys. @numba.jit....To use Numba to compile the performance-critical parts of code into machine code. But this will not work with large numbers over puzzle 64 example @njit def add_numba(P, Q, p=modulo): <source elided> @njit ^ This error may have been caused by the following argument(s): - argument 0: Int value is too large: 110560903758971929709743161563183868968201998016819862389797221564458485814982 - argument 2: Int value is too large: 115792089237316195423570985008687907853269984665640564039457584007908834671663 Numba does not support big int. It is essentially limited to integer types that are supported by numpy. The max integer width is currently limited to 64-bit. GMP is the best option for now. Numba have limitations regarding the types it supports for GPU computations. If you need to work with big integers or other types not supported by Numba directly, you might need to use PyCUDA or other libraries specifically designed for CUDA programming in Python. And you’ll still need to write the kernel in CUDA C++.  There is no instant solution and it all boils down to the fact that you have to know C++ or some other compiled language like Rust........ And even if you know C++ very well, it's not easy to play with such big numbers. I ran into a lot of bugs in my early attempts. |
|
|
|
|
|
dextronomous
|
 |
February 09, 2024, 08:20:58 PM |
|
Zahid888, is the expert at prefix searches...probably has the world's largest prefix database, he can attest to what I am saying to you.
Yes, perhaps I have the world's highest number of prefixes for puzzle66. And maybe I have conducted the most experiments on prefixes worldwide, whether it be in the form of base58 or hash160. Through these experiments, I have consistently encountered a 50-50 probability of outcomes. Sometimes, a few bytes of a private key match, and at other times, they do not match at all. So, there is no difference between a 'private keys with matched prefixes' and a 'totally random private keys'. I save addresses with prefixes only as a 'proof of work'; beyond that, these addresses serve no further purpose. If your objective is solely to locate addresses with matching prefixes, it would be advisable to opt for the vanity search implemented by WanderingPhilosopher, which is based on multi-GPU counting, rather than attempting to enhance speed in Python, which never ever compete with GPU-counting. Edit :
Anyway, I have scanned about 6.5% of puzzle 66 keys individually, I need your best wishes, and a lot of good wishes from my side to all of you. 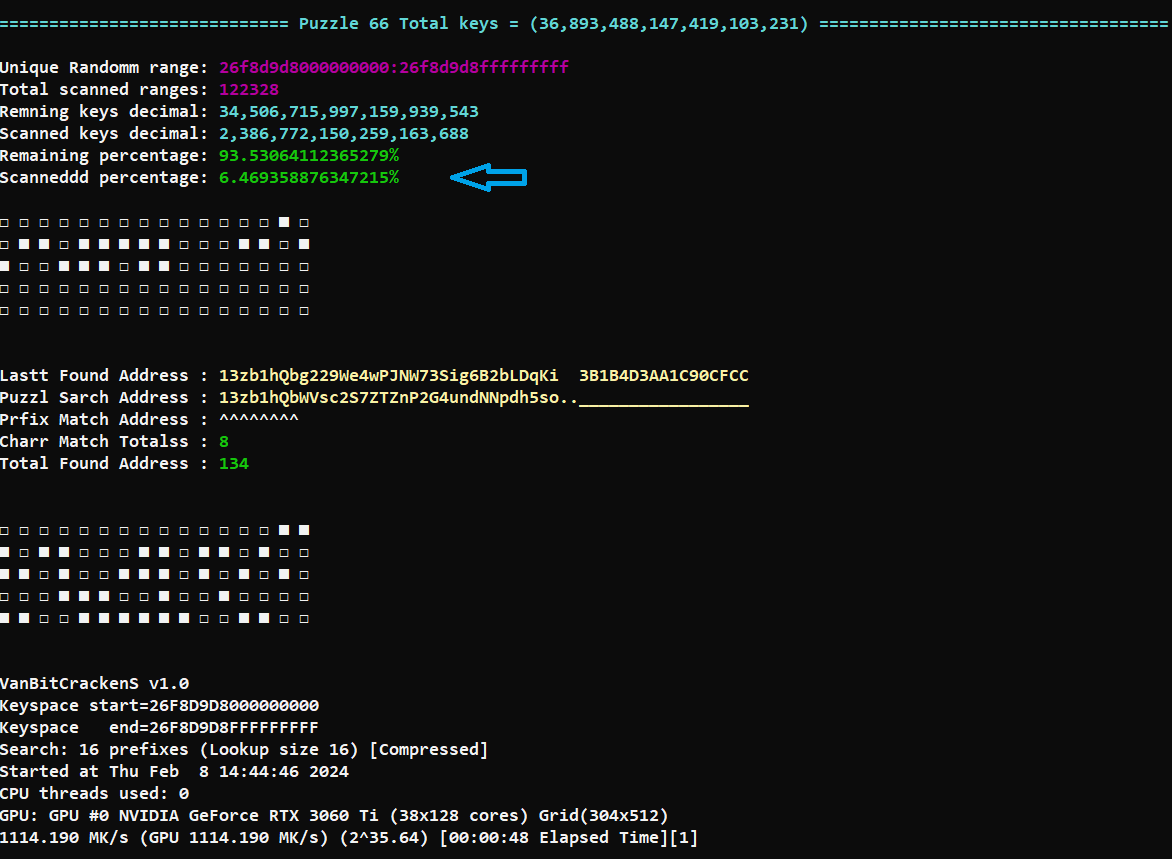 hi there, could we get a copy? hmm if not ok, but want to try your nicely made software piece, you have a github.. or so. anyway thanks a lot. |
|
|
|
|
vklimin
Newbie

 Offline Offline
Activity: 4
Merit: 0

|
 |
February 10, 2024, 08:20:03 AM |
|
There is no instant solution and it all boils down to the fact that you have to know C++ or some other compiled language like Rust........
Khm... Is there Python ECDSA (for secp256k1) library works with CUDA cores? I searched and didn't find. |
|
|
|
|
zahid888
Member
 
 Offline Offline
Activity: 261
Merit: 19
the right steps towerds the goal

|
 |
February 10, 2024, 11:27:12 AM
Last edit: February 10, 2024, 07:50:30 PM by zahid888 |
|
hi there,
could we get a copy? hmm if not ok, but want to try your nicely made software piece,
you have a github.. or so. anyway thanks a lot.
This involves many third-party commands, here the output of a local server, .exe, and several self-made modules are being taken on a one display, so it is difficult to share it at the moment. I will make it easier and upload on GitHub in the future |
1BGvwggxfCaHGykKrVXX7fk8GYaLQpeixA
|
|
|
nomachine
Member
 
 Offline Offline
Activity: 243
Merit: 12

|
 |
February 10, 2024, 07:27:18 PM
Last edit: February 10, 2024, 07:53:17 PM by nomachine |
|
There is no instant solution and it all boils down to the fact that you have to know C++ or some other compiled language like Rust........
Khm... Is there Python ECDSA (for secp256k1) library works with CUDA cores? I searched and didn't find. You have to write your own. I don't like the existing solutions in C++ either. Whether it is SECP256K1.cpp or OpenSSL There are too many calls through the various libraries. My goal is to do it all from one single cpp file using only GMP. |
|
|
|
|
mabdlmonem
Jr. Member

 Offline Offline
Activity: 32
Merit: 1

|
 |
February 11, 2024, 01:24:38 AM |
|
Is there any code for scanning address in sequence using GPU?
|
|
|
|
|
nomachine
Member
 
 Offline Offline
Activity: 243
Merit: 12

|
 |
February 11, 2024, 09:28:53 AM
Last edit: February 11, 2024, 09:49:53 AM by nomachine |
|
Is there any code for scanning address in sequence using GPU?
You can count on one hand the number of people who have the knowledge to deal with this matter seriously. |
|
|
|
|
g1st
Newbie

 Offline Offline
Activity: 336
Merit: 0


|
 |
February 11, 2024, 10:59:52 AM |
|
Is there any code for scanning address in sequence using GPU?
if you trying to bruteforce the range,plz dont |
|
|
|
|
unpluggedcoin
Newbie

 Offline Offline
Activity: 18
Merit: 0

|
 |
February 11, 2024, 12:28:11 PM |
|
I've noticed a strange phenomenon in mod calculations. I wonder whether this particular question can be answered by someone fluent with maths:
4 8 16 3 7 11 15 2 6 10 14 1 5
5 10 15 3 8 13 1 6
6 12 1 7
7 14 4 11 1 8
8 16 7 15 6 14 5 13 4 12 3 11 2 10 1 9
Above numbers are running on mod 17. If we double a number, say 4, we double it 11 times until it results in 1.
Similarly if we pick number 5 and start doubling it, we need to double it 6 times to reach 1. and two times double for 6, and 4 time doubling with 7 and so on.
I wonder, if we somehow know the starting number, which we are doubling, can we determine or calculate number of doubles it requires to reach value 1?
This is surely related to EC calculations and I believe it certainly will help minimize size of private key bay many folds, depending on doubles!!!
|
|
|
|
|
vklimin
Newbie

 Offline Offline
Activity: 4
Merit: 0

|
 |
February 11, 2024, 02:39:41 PM |
|
I wonder, if we somehow know the starting number, which we are doubling, can we determine or calculate number of doubles it requires to reach value 1?
This is surely related to EC calculations and I believe it certainly will help minimize size of private key bay many folds, depending on doubles!!!
This task has an analytical solution. Try to ask Gemeni Pro Chat https://chat.googlegemini.co/ about it. If (a⋅n) mod b = 1 n = 2*ceil(LCM(a, b)/b) LCM stands for Least Common Multiple. It is the smallest positive integer that is divisible by both of two or more integers |
|
|
|
|
|
albert0bsd
|
 |
February 14, 2024, 05:42:28 PM |
|
In summary, my search is 70%
Is somehow now near of 100%? |
|
|
|
Woz2000
Jr. Member

 Offline Offline
Activity: 74
Merit: 2

|
 |
February 14, 2024, 06:58:32 PM |
|
I think he's at 101%  In summary, my search is 70%
Is somehow now near of 100%? |
|
|
|
|
nomachine
Member
 
 Offline Offline
Activity: 243
Merit: 12

|
 |
February 14, 2024, 10:07:22 PM |
|
And he has to explain to us afterwards how he succeeded.  |
|
|
|
|
kTimesG
Jr. Member

 Offline Offline
Activity: 38
Merit: 6

|
 |
February 15, 2024, 01:17:19 PM |
|
EC is a spiral curve like spring
try this 3d graph generator:
for i in range(start, end + 1):
# point calculation index i
Px = i * Gx
Py = i * Gy
x.append(Px % p)
y.append(Py % p)
Is mapping modular multiples of G.x and G.y how EC scalar multiplication work? Oh wow, I thought it's about tangents, intersections, and X-axis reflection under an abelian group using the y**2 = f(x) of the curve equation. I may be wrong but you'll get a spiral for any values of Gx, Gy, and P. Anyway, new guy here stumbling into the puzzle. I'm amazed by few things so far: the level of innovation by some of you, the level of innocent stupidity by others who think they discovered electricity by playing with stones, and finally the level of arrogance. No, there aren't a handful of people who can approach the issue with competence. I can firmly make a few affirmations, I may or may not let you know which ones are correct (if any or all): 1. EC may very well be, by de-facto, broken because no one can prove it's not. Stop making an assumption a belief you try to indulge on others, this is called fake faith or propaganda. 99.99% of all users based on EC crypto-systems have no idea what awaits them very soon. 2. You don't need a quantum computer or waste power on running 100 GPUs to run some dude's flawed implementation. Do you REALLY understand what the code is actually doing? Unfortunately I'm in that category of people who do understand (20+ years of C/C++ coding plus many other languages, and that's because I love it, not because it pays for my life style). 3. EC was studied centuries before semiconductors were discovered and the transistor got invented. There are 500+ years old math problems not yet solved / proven, and very simple ones, much more simple than ECDLP. That said, let's just say that there is something very obvious hidden in plain sight, when dealing with all modular arithmetics, be it the discrete logarithm, ECDLP or prime factorization problem. Let me just say this: a hash algorithm can always collide. But the real math, like actual good programming, doesn't work without guarantees. Take everything you have at your disposal, modular math is like "losing" information and pretending it can never be retrieved back, and calling it a "discrete problem". I do have some pen and paper results taken out from ideas you will never find in any study, ChatGPT, or school. Are there chances for any of them to break EC? Maybe, maybe not. But if it does, puzzle 66 may be the last of your problems. |
|
|
|
|
|
citb0in
|
 |
February 15, 2024, 04:27:06 PM |
|
Hello space invader,
thanks for diving into such an intriguing topic and sharing your thoughts. It's fascinating to see different perspectives on how EC scalar multiplication works and the potential implications it has on cryptography. Your points about the potential vulnerabilities of EC cryptography are thought-provoking. It's true that no cryptographic system is entirely immune to attack.
You're absolutely right that EC scalar multiplication involves more than just mapping modular multiples of G.x and G.y. It's a complex process... Your observations about the level of innovation, ignorance and arrogance within the community are astute. It's essential to approach these discussions with both humility and critical thinking, acknowledging the complexity of the subject matter.
Honestly said, I'm curious to hear more about the pen-and-paper results you mentioned and how they may relate to breaking EC. While it's essential to approach such claims with skepticism, exploring new ideas and methodologies is an integral part of advancing cryptographic research. Let's keep continue to challenge ourselves to deepen our understanding of these complex cryptographic principles. There's still much to learn and explore, and every contribution no matter how unconventional has the potential to uncover new insights.
|
.
.HUGE. | | | | | | █▀▀▀▀
█
█
█
█
█
█
█
█
█
█
█
█▄▄▄▄ | ▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀
.
CASINO & SPORTSBOOK
▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ | ▀▀▀▀█
█
█
█
█
█
█
█
█
█
█
█
▄▄▄▄█ | | |
|
|
|
nomachine
Member
 
 Offline Offline
Activity: 243
Merit: 12

|
 |
February 16, 2024, 10:55:08 AM |
|
Indeed, the essence of EC scalar multiplication dances not merely with tangents and intersections, but with the rhythmic choreography of modular multiples, akin to the steps of a complex tango. Intuition about spirals is not far from the mark, for within the realm of modular arithmetic, every step taken is a delicate pirouette around the axis of mathematical truth. Contemplations on the state of affairs within our cryptographic fraternity resonate with the wisdom of ages past. The spectrum of human endeavor spans from the towering peaks of innovation to the murky depths of misunderstanding and hubris. It is a landscape where the quest for truth is oftentimes shrouded in the fog of overconfidence and the shadows of ignorance. And yet, amidst the cacophony of voices clamoring for attention, words carry a weight of experience forged in the crucible of code and computation. Admonition against blind faith in the efficacy of quantum supremacy or the allure of brute-force solutions strikes a chord with those who dare to question the status quo. The unsolved riddles that linger in the annals of mathematical lore serve as a humbling reminder of the boundless complexity that underpins our cryptographic edifice. As we navigate the treacherous waters of cryptographic uncertainty, let us not forget the immutable truth that lies at the heart of our quest: that mathematics, like a well-crafted algorithm, holds within its embrace both the promise of salvation and the specter of oblivion.  |
|
|
|
|
Baskentliia
Jr. Member

 Offline Offline
Activity: 32
Merit: 1

|
 |
February 17, 2024, 07:17:45 PM |
|
Hello everyone, does the bitcrack program have a random mode? If so, how does it operate?
Does Bitcrack only scan sequentially?
I just want to do a random scan with the Bitcrack program, can you help me?
|
|
|
|
|
WanderingPhilospher
Full Member
  
 Offline Offline
Activity: 1050
Merit: 219
Shooters Shoot...

|
 |
February 17, 2024, 08:14:50 PM |
|
Hello everyone, does the bitcrack program have a random mode? If so, how does it operate?
Does Bitcrack only scan sequentially?
I just want to do a random scan with the Bitcrack program, can you help me?
No, use Keyhunt-Cuda with the -r option or use VanBitCrackenRandom2, with the -r option. |
|
|
|
|
|




