The concept of a logarithm was invented just a few centuries ago and immediately changed engineering as we know it.
import math
from mpmath import mp
def calculate_log2(decimal_value):
log2_value = mp.log(decimal_value, 2)
return log2_value
def calculate_reverse_log2(log2_value):
decimal_value = mp.power(2, log2_value)
return decimal_value
target_numbers = [
(1, 1), (2, 3), (3, 7), (4, 8), (5, 21), (6, 49), (7, 76), (8, 224), (9, 467), (10, 514),
(11, 1155), (12, 2683), (13, 5216), (14, 10544), (15, 26867), (16, 51510),
(17, 95823), (18, 198669), (19, 357535), (20, 863317), (21, 1811764),
(22, 3007503), (23, 5598802), (24, 14428676), (25, 33185509),
(26, 54538862), (27, 111949941), (28, 227634408), (29, 400708894),
(30, 1033162084), (31, 2102388551), (32, 3093472814), (33, 7137437912),
(34, 14133072157), (35, 20112871792), (36, 42387769980), (37, 100251560595),
(38, 146971536592), (39, 323724968937), (40, 1003651412950),
(41, 1458252205147), (42, 2895374552463), (43, 7409811047825),
(44, 15404761757071), (45, 19996463086597), (46, 51408670348612),
(47, 119666659114170), (48, 191206974700443), (49, 409118905032525),
(50, 611140496167764), (51, 2058769515153876), (52, 4216495639600700),
(53, 6763683971478124), (54, 9974455244496707), (55, 30045390491869460),
(56, 44218742292676575), (57, 138245758910846492), (58, 199976667976342049),
(59, 525070384258266191), (60, 1135041350219496382), (61, 1425787542618654982),
(62, 3908372542507822062), (63, 8993229949524469768),
(64, 17799667357578236628), (65, 30568377312064202855)
]
mp.dps = 20 # Set the high decimal precision
for ordinal, decimal_value in target_numbers:
log2_result = calculate_log2(decimal_value)
reverse_result = calculate_reverse_log2(log2_result)
print(f"Puzzle:{ordinal}: Log(2) for {decimal_value} is approximately {log2_result}. Reverse calculation: {reverse_result}")
Look result of this madness:
Puzzle:1: Log(2) for 1 is approximately 0.0. Reverse calculation: 1.0
Puzzle:2: Log(2) for 3 is approximately 1.5849625007211561815. Reverse calculation: 3.0
Puzzle:3: Log(2) for 7 is approximately 2.8073549220576041074. Reverse calculation: 7.0
Puzzle:4: Log(2) for 8 is approximately 3.0. Reverse calculation: 8.0
Puzzle:5: Log(2) for 21 is approximately 4.3923174227787602889. Reverse calculation: 21.0
Puzzle:6: Log(2) for 49 is approximately 5.6147098441152082149. Reverse calculation: 49.0
Puzzle:7: Log(2) for 76 is approximately 6.2479275134435854938. Reverse calculation: 76.0
Puzzle:8: Log(2) for 224 is approximately 7.8073549220576041074. Reverse calculation: 224.0
Puzzle:9: Log(2) for 467 is approximately 8.8672787397096619133. Reverse calculation: 467.0
Puzzle:10: Log(2) for 514 is approximately 9.0056245491938781069. Reverse calculation: 514.0
Puzzle:11: Log(2) for 1155 is approximately 10.173677136303419893. Reverse calculation: 1155.0
Puzzle:12: Log(2) for 2683 is approximately 11.389631339260521112. Reverse calculation: 2683.0
Puzzle:13: Log(2) for 5216 is approximately 12.348728154231077553. Reverse calculation: 5216.0
Puzzle:14: Log(2) for 10544 is approximately 13.364134655008051742. Reverse calculation: 10544.0
Puzzle:15: Log(2) for 26867 is approximately 14.713547616912692731. Reverse calculation: 26867.0
Puzzle:16: Log(2) for 51510 is approximately 15.652564919610652675. Reverse calculation: 51510.0
Puzzle:17: Log(2) for 95823 is approximately 16.548084361224413154. Reverse calculation: 95823.0
Puzzle:18: Log(2) for 198669 is approximately 17.600007248708430135. Reverse calculation: 198669.0
Puzzle:19: Log(2) for 357535 is approximately 18.447724952285439321. Reverse calculation: 357535.0
Puzzle:20: Log(2) for 863317 is approximately 19.719530872026151871. Reverse calculation: 863317.00000000000001
Puzzle:21: Log(2) for 1811764 is approximately 20.788963611792287227. Reverse calculation: 1811764.0
Puzzle:22: Log(2) for 3007503 is approximately 21.520134745822105762. Reverse calculation: 3007503.0
Puzzle:23: Log(2) for 5598802 is approximately 22.416686729787820277. Reverse calculation: 5598802.0
Puzzle:24: Log(2) for 14428676 is approximately 23.782435585948494073. Reverse calculation: 14428676.0
Puzzle:25: Log(2) for 33185509 is approximately 24.984050066697330736. Reverse calculation: 33185509.0
Puzzle:26: Log(2) for 54538862 is approximately 25.700781261712878111. Reverse calculation: 54538862.0
Puzzle:27: Log(2) for 111949941 is approximately 26.738278526958637998. Reverse calculation: 111949941.0
Puzzle:28: Log(2) for 227634408 is approximately 27.762143403294801415. Reverse calculation: 227634408.0
Puzzle:29: Log(2) for 400708894 is approximately 28.577979290797464122. Reverse calculation: 400708894.0
Puzzle:30: Log(2) for 1033162084 is approximately 29.944419458082398243. Reverse calculation: 1033162084.0
Puzzle:31: Log(2) for 2102388551 is approximately 30.969382178280594153. Reverse calculation: 2102388551.0
Puzzle:32: Log(2) for 3093472814 is approximately 31.526580209327912218. Reverse calculation: 3093472814.0
Puzzle:33: Log(2) for 7137437912 is approximately 32.732759144627864676. Reverse calculation: 7137437912.0000000001
Puzzle:34: Log(2) for 14133072157 is approximately 33.718356052472843908. Reverse calculation: 14133072157.0
Puzzle:35: Log(2) for 20112871792 is approximately 34.22740003868583903. Reverse calculation: 20112871792.0
Puzzle:36: Log(2) for 42387769980 is approximately 35.302929017096708804. Reverse calculation: 42387769980.000000001
Puzzle:37: Log(2) for 100251560595 is approximately 36.544833738746849477. Reverse calculation: 100251560595.0
Puzzle:38: Log(2) for 146971536592 is approximately 37.096745824716051977. Reverse calculation: 146971536592.0
Puzzle:39: Log(2) for 323724968937 is approximately 38.235977688802476225. Reverse calculation: 323724968937.0
Puzzle:40: Log(2) for 1003651412950 is approximately 39.868395419757349213. Reverse calculation: 1003651412950.0
Puzzle:41: Log(2) for 1458252205147 is approximately 40.407377394423366271. Reverse calculation: 1458252205147.0
Puzzle:42: Log(2) for 2895374552463 is approximately 41.396887129359569265. Reverse calculation: 2895374552463.0
Puzzle:43: Log(2) for 7409811047825 is approximately 42.752573892536879788. Reverse calculation: 7409811047825.0
Puzzle:44: Log(2) for 15404761757071 is approximately 43.808441604030467369. Reverse calculation: 15404761757071.0
Puzzle:45: Log(2) for 19996463086597 is approximately 44.184810076602017917. Reverse calculation: 19996463086597.0
Puzzle:46: Log(2) for 51408670348612 is approximately 45.547076931749783679. Reverse calculation: 51408670348612.0
Puzzle:47: Log(2) for 119666659114170 is approximately 46.766014580697737785. Reverse calculation: 119666659114170.0
Puzzle:48: Log(2) for 191206974700443 is approximately 47.442128478217754077. Reverse calculation: 191206974700443.0
Puzzle:49: Log(2) for 409118905032525 is approximately 48.539513532885657356. Reverse calculation: 409118905032525.00001
Puzzle:50: Log(2) for 611140496167764 is approximately 49.118497410306637905. Reverse calculation: 611140496167764.0
Puzzle:51: Log(2) for 2058769515153876 is approximately 50.870703748687580964. Reverse calculation: 2058769515153876.0
Puzzle:52: Log(2) for 4216495639600700 is approximately 51.904965885818221825. Reverse calculation: 4216495639600700.0
Puzzle:53: Log(2) for 6763683971478124 is approximately 52.586730675690989872. Reverse calculation: 6763683971478124.0
Puzzle:54: Log(2) for 9974455244496707 is approximately 53.147159473916182081. Reverse calculation: 9974455244496706.9998
Puzzle:55: Log(2) for 30045390491869460 is approximately 54.737993190511333013. Reverse calculation: 30045390491869460.0
Puzzle:56: Log(2) for 44218742292676575 is approximately 55.295507509568065689. Reverse calculation: 44218742292676575.0
Puzzle:57: Log(2) for 138245758910846492 is approximately 56.940012835374135824. Reverse calculation: 138245758910846492.0
Puzzle:58: Log(2) for 199976667976342049 is approximately 57.472609298293031082. Reverse calculation: 199976667976342049.0
Puzzle:59: Log(2) for 525070384258266191 is approximately 58.865288438176815787. Reverse calculation: 525070384258266190.99
Puzzle:60: Log(2) for 1135041350219496382 is approximately 59.977450564669282481. Reverse calculation: 1135041350219496382.0
Puzzle:61: Log(2) for 1425787542618654982 is approximately 60.306464728992728608. Reverse calculation: 1425787542618654982.0
Puzzle:62: Log(2) for 3908372542507822062 is approximately 61.761273698209320329. Reverse calculation: 3908372542507822061.9
Puzzle:63: Log(2) for 8993229949524469768 is approximately 62.963545065677060031. Reverse calculation: 8993229949524469767.8
Puzzle:64: Log(2) for 17799667357578236628 is approximately 63.948484083037149251. Reverse calculation: 17799667357578236628.0
Puzzle:65: Log(2) for 30568377312064202855 is approximately 64.728673773273428832. Reverse calculation: 30568377312064202855.0
So, puzzle 66 private key is from
65.000000000000000000 log(2)
to
66.000000000000000000 log(2)You can test puzzle 15 (or any) with this formula :
from mpmath import mp
import random
import secp256k1 as ice
import sys
def calculate_reverse_log2(log2_value):
decimal_value = mp.power(2, log2_value)
return decimal_value
mp.dps = 20 # Set the decimal precision to a sufficiently high value
target = "1QCbW9HWnwQWiQqVo5exhAnmfqKRrCRsvW"
while True:
random_log2_value = mp.mpf(random.uniform(14.0, 15.0))
reverse_result = calculate_reverse_log2(random_log2_value)
HEX = "%064x" % int(reverse_result)
dec = int(HEX, 16)
caddr = ice.privatekey_to_address(0, True, dec)
message = "[+] {}".format(dec);messages = [];messages.append(message);output = ''.join(messages) + "\r";sys.stdout.write(output);sys.stdout.flush()
if target in caddr:
wifc = ice.btc_pvk_to_wif(HEX)
print(f"\n\033[32m[+] PUZZLE SOLVED: {wifc} \033[0m")
break
Result is instant.
I can not see pattern here... Can you see ??

You can even do regression analysis
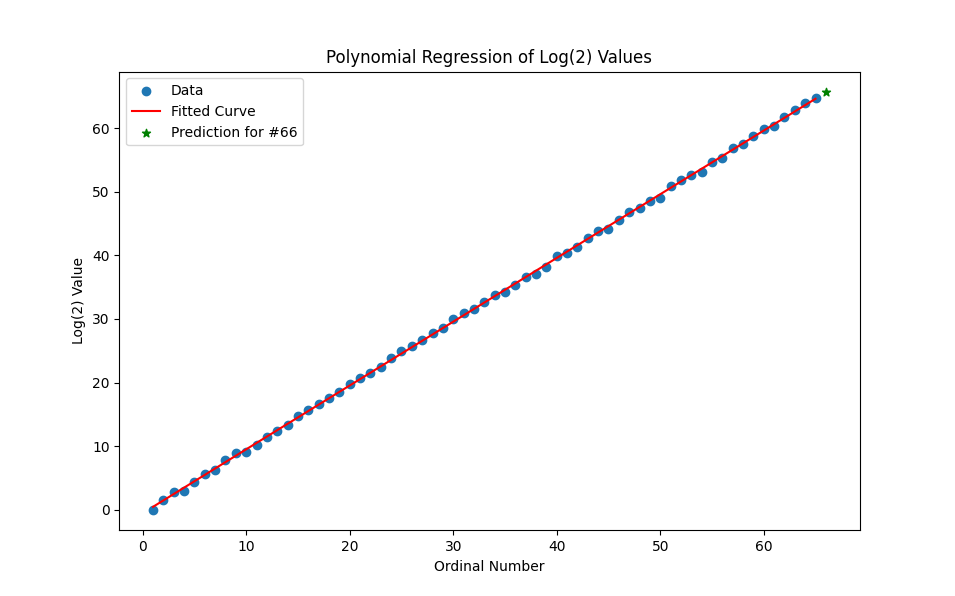
I'm lost between the size of the numbers and the precision required here . . .
There is no pattern. But it's not random either according to the polynomial analysis. There is an exact math formula for making this puzzle with some script, errors = ZERO. With high decimal precision (mp.dps = 20 at least)
And the formula is in the creator's mind.




