My congratulations to Blue Tyrant and Toughit. You gave me a run for my bits! Following is what I wrote up after Bitcoin gave me advance notice. When I saw the “while you were typing” warning for the official announcement, I had to go back and review the spreadsheet...
Well, hello, aa5a6f6fd078f76dea8d16d5841b53699cca4a593f9304f206471e495e726627. Frankly, I didn’t have a great week—though it was certainly better than the week before! I think I made a strong start, then got sucked back into drama which went to a new nadir: It's amazing how you went from "verified by theymos" to "red trust from theymos" to "banned by theymos"!
In case someone wonders what happened to alia_alt2, see modlog: Autoban user: N/A in topic #0 by member #1924085 Not only did that consume much time (both on and off the forum), but it also had me largely preoccupied for a few days. Some of the other contestants put on a very strong showing. Good game, folks—you had me worried! New rule request: The winner each week has to suggest his top post as a learning experience, (and maybe expound on it if there is interest)
Out of my 90 posts, although many were good in their own right, I count 8 which I think are exemplary outside the strictly limited situation of aforestated drama: Of course, the judges’ opinion was what mattered here! Cheers, all. |
|
|
|
Note: The principal purpose of my suggestion is to facilitate bidirectional PGP-encrypted communications between users. PGP is important to me—so much so, that I am now CM for my very own 256% AIRDROP BOUNTY SIGNATURE SPAM old-school CRYPTO campaign. Everybody is familiar with this warning on the “Send message” page of the forum’s PM system: Note: PM privacy is not guaranteed. Encrypt sensitive messages.
As one who has attempted to follow that advice, I can attest that it is flat-out impractical. I endure extreme inconvenience (and oftentimes, monetary loss) for the sake of privacy. If I can’t handle the mind-numbing, error-prone tedium of copypasting manually encrypted/decrypted significant numbers of messages in and out of the forum’s PM system, then the above warning to “encrypt” is but a mockery. Please improve the forum to make it feasible for privacy-conscious users to use PGP for every message, all the time.
Like a post office here on the forum? I do agree on this since i'm trying to be more private but i have a question. Will this be managed by a group of people or a programmed bot?
If by a group of people, time would be their enemy.
If by a programmed bot, then good choice, but the thing is, can it handle a huge load of PMs circulating daily?
Of course, this function would be performed in software. Not what would usually be considered a bot: A daemon, or more likely, daemons plural (mailer-daemon plus something to integrate the mailer with the PM system). I do not even see how it would be possible for humans to—what, manually select and move messages between the PM and e-mail systems? If ordinary MTAs can easily handle millions of messages, and the forum’s PM system can handle what it does now, I do not see where any scaling concerns would arise unless the system were implemented by monkeys.
PMs received (except those sent by newbies, in terms of content) can be sent via email, and will contain the content of said PM, which can be encrypted if the sender takes steps to do so.
However: (0) You can’t simply hit “reply” to those messages. (1) There is no way to send PMs by e-mail; the only means to send a PGP PM is manual copypaste with a web browser (!). (2) PGP/MIME cannot be sent through the PM system. (3) The message header fields are not set to values conducive to comfortably reading PMs in your e-mail; the From: and Subject: fields in particular would need to be more informative. The forum acting as a remailer would also open the possibility of more phishing scam attempts, it would make it difficult to prevent this, and would make it difficult to track who is behind these types of scams. The same is true for other types of spam.
How? Given proper upfront identification of messages as being from a user (via Bitcoin Forum), I don’t see how this would significantly assist phishing. As stated below, it should be obvious that I do not suggest that messages should be blindly passed through the system. Logging could and should be performed for abuse response purposes. Logging and rate-limiting could be used to combat spam, just as same are used now. Another issue is the sender would need to expose their email address in order to send another member a message.
From the term “remailer” (as opposed to “forwarder”) and my discussion of many users’ reluctance to expose their mail addresses, I deemed it obvious that the sender address would be rewritten. E.g., mail from me through the system would be received with a From: header of "nullius via Bitcoin Forum" <976210@users.bitcointalk.org> (or nullius@users.bitcointalk.org—but likely the numeric address, since forum usernames can contain characters problematic in mail address box parts). SMTP envelope FROM should be a VERP (Variable Envelope Return Path), as used by mailing lists to catch bounces. Note: Some of my discussion here requires an understanding of how Internet mail works.Essentially, I am suggesting some form of Type 1 Remailer. Overall this would give an incremental amount of convenience in maintaining privacy for the recipient, while making things much easier for scammers and spammers.
How?
Emphasis: I did suggest that the receiving end of the system should be opt-in for those users who want to receive all PMs by e-mail. The only change for those who did not willingly opt-in would be that they may receive PMs which originated in the mail system. Of course, sending into the system must be restricted to the e-mail address associated with a username; and mail should show up in the PM system as being “from” a username, just as it does now. |
|
|
|
Please make sure to reapply to Round 2 if you haven’t already.
I’d been waiting for 2018-03-12 03:00 UTC: BitcoinTalk Username: nullius (#976210) Starting Post Count (including this one): 865 Current Rank: Member BTC Address ( edited): 3CxsuDpbariuRG8t35cPMmkwBYLuNQ73Ld N.b., Activity Period 1257 will begin Tuesday, 13 March 2018 at 19:40:00 UTC. I expect to change rank soon after that; and others may, too. Does it matter to the campaign if the provided information does not remain valid all week?
Yes, as it is not a paid sig campaign  unless you can put a value on privacy, which I believe to be priceless. Indeed, priceless! Campaign payment rules agree: Airdrop Bounty Shill Payola Terms: In exchange for your participation in this campaign, you will receive 2 256%* airdrop bounty spam payola consisting of pretty good privacy for yourself and those with whom you communicate. (* All airdrop percentages herein stated apply the same quality of maths as seen in a typical scamcoin.)Privacy is one of the most valuable things you can have in this world. It is priceless! I will soon work in a link touting the virtues of Joe’s Signatureless Challenge. |
|
|
|
@BTCforJoe, is my new signature campaign compatible with yours? I think it is. Payment for my campaign consists of a 2 256% airdrop of pure privacy, plus pride in being cypherpunk chic. If you will permit people to participate in both campaigns (as I already am), then I will add a plug to Joe’s Signatureless Challenge to my ANN thread’s OP. Behold, the best spam campaign this forum has ever seen: 😈😈😈 PGP 256% AIRDROP BOUNTY SIGNATURE SPAM CAMPAIGN! Old-school CRYPTO 😈😈😈
|
|
|
|
|
Reserved for metadata (if any).
|
|
|
|
😈😈😈 CAMPAIGN PARTICIPANTS 😈😈😈 Listed in chronological order. Further explanation/rules will be added here and in OP. (WIP) Note: All signatures have been verified by me. Timestamps given are the timestamps claimed in the signature, not the post timestamp. (Though if I see evidence of somebody playing games with this, I will use post timestamp for that person instead.) |
|
|
|
Announcing the.nym.zone’sAirdrop Bounty Shill Payola Terms: In exchange for your participation in this campaign, you will receive 2 256%* airdrop bounty spam payola consisting of pretty good privacy for yourself and those with whom you communicate. (* All airdrop percentages herein stated apply the same quality of maths as seen in a typical scamcoin.)Privacy is one of the most valuable things you can have in this world. It is priceless! And the more you participate in this campaign, the more privacy you will get airdropped to you by virtue of natural consequences. This is without a doubt the #1 most honestly highest-paying spam campaign ever seen on this forum! By participating, you will also show off that you are elite and cypherpunk chic. Laugh at the n00bs who think that “crypto” means a knock-off shitcoin scam. You will be using old-school crypto, 90s cypherpunk style. Remember that the more you spam for the pro-PGP, pro-privacy message of this campaign, the more elite you will be!Incentives for posting: The more high-quality posts you make (as judged by the merit they earn) while participating in this campaign, the more awesome you will be. This will make you rightfully proud. Bonus giveaway: Replying in this thread with a post which is both witty and PGP-signed will give you a chance to show off! (Non-PGP-signed replies may be nuked by me, at my discretion.) To be eligible for airdrop, users must follow these rules: 0x0. Use PGP. 0x1. Use PGP! 0x2. Add at least one (1) PGP fingerprint to your signature. A longid/ shortid does not suffice: You must devote space in your signature to at least one full fingerprint, at normal or greater font size. To qualify, the pertinent key MUST be available through sks-keyservers.net. Of course, it MUST be a fingerprint for your own key, as verified through below requirements. It MUST contain uid(s) with valid e-mail address(es) which people can use to contact you privately, using PGP from any other mailserver in the world ( Protonmail is unacceptable). If you are able to place links in your signature, then your PGP fingerprint MUST hyperlink to EITHER your key on sks-keyservers.net, OR on a website belonging to you or to some group or company of which you are a part ( not on Keybase). See my own signature for an example. Note for those who already display full PGP fingerprints in their signatures: I suggest that you follow the above-described format. But if you don’t want to change your signature, I will consider it “grandfathered” if you post a link to an archive on web.archive.org or archive.is, showing a post of yours with your signature before the original timestamp of this post. Of course, you will still need to follow the other rules, including a PGP-signed joinder message in this thread per Rule 0x4 below. Privacy note for n00bs: As true whenever you distribute a PGP key, your e-mail address(es) will be available through your key’s uid(s). This is how the Internet is supposed to work: You give out an e-mail address, so that people can contact you. People connect. Magic happens! — I do realize that not everybody on a Web forum wishes to expose an e-mail address. Thus, I suggest two solutions: Consider using a mail provider with excellent spam blocking. Support my feature request for a forum remailer, in lieu of PM. 0x3. Add the words, “Use PGP!” (or another pro-PGP message of your creative choice) to your signature. If you are able to place links in your signature, then the text must hyperlink to this thread. 0x4. Make a post in this thread to join the campaign. Requirements are further stated below. 0x5. Spam the forum with high-quality posts which earn merit. Users who fail to spam the forum with meritorious high-quality posts may be kicked out of this campaign, at my exclusive discretion. 0x6. Spam your friends by PM, e-mail, knocking on their doors, etc., to preach to them the good word that they should Use PGP!0x7. Spam the hell out of Twitter, Facebook, Telegram, Reddit, and every other “social media” site and communications channel, with messages promoting PGP use! Note: I don’t use any of these sites, so I can’t check up on this requirement. 0x8. If you show patent evidence of having failed to read the rules, then you will be banned from the campaign for a duration at my discretion (likely permanent). If you include a Bitcoin address in your PGP-signed joinder statement, then you will be permabanned from the campaign. If you have negative trust, then you may be banned from the campaign at my discretion. I may ban anybody for any reason or no reason, at my discretion. 0x9. These rules may be changed by me at any time. 0xa. Use PGP for your personal correspondence, your business correspondence— all your online corespondence, all the time! If any of your correspondents do not use PGP, then you should send them a PGP-signed message explaining to them they should use PGP.0xb. (Optional) Staple copies of the Cyphernomicon, The Crypto Anarchist Manifesto, A Cypherpunk’s Manifesto, and other suitable propaganda to local lamp-posts, trees, goldfish, etc. 0xc. (Optional) If you are female and attractive, use PGP-encrypted e-mail to express your intense desire for me. Otherwise, just send me a PGP-encrypted “hello”. 0xd. (* Required) Use Bitcoin. Bitcoin is cypherpunk money. Satoshi Nakamoto fulfilled a decades-old yearning when he invented Bitcoin!0xe. (RECOMMENDED) Take the next steps to securing all your communications, such as by using OTR for instant messaging. 0xf. Use PGP!
Requirements for joinder post: To officially join this spam campaign, you must post in this thread a PGP clearsigned statement with the following information: - Lusername and forum uid
- Your PGP fingerprint
- URL where your PGP key can be easily downloaded by lusers who don’t know how to use keyservers, meeting the requirements stated above. KEYBASE LINKS DO NOT MEET THIS REQUIREMENT.
- Optional: If your primary key(s) are certification-only and kept exclusively on an airgap machine, you MAY say so for extra elite-points. Although there is no way for me to verify that you actually use an airgap machine, if you make such a statement, I will verify that you have a (C)-only primary key. n00bs, if using GnuPG: man gpg and look for --expert --full-generate-key and --export-secret-subkeys. As for advice if you can’t figure it out (but first, RTFM and try).
- Optional: Iff you plan to spam Twitter, etc. with messages promoting PGP use, please provide a link to your account so that others can follow you.
The statement MUST be PGP clearsigned. Those who post unsigned join requests will be banned from the campaign. You may enclose the statement in [code] tags if desired, or not if not desired. The important part is that I must be able to verify it. The statement MUST NOT contain any Bitcoin addresses, or other payment info. Those who post join requests containing payment addresses will be permabanned from this campaign. This rule is set so I can easily drop-kick bounty chasers who post in this thread without reading the rules. Other than this, you may include other info and/or witty remarks as you desire. Keybase links are not accepted, because I want to push people to get their keys out onto keyservers.A live example of a statement meeting the above requirements: -----BEGIN PGP SIGNED MESSAGE-----
Hash: SHA512
Lusername: nullius (#976210)
PGP fingerprint (ECC): 0xC2E91CD74A4C57A105F6C21B5A00591B2F307E0C
https://sks-keyservers.net/pks/lookup?op=get&search=0xC2E91CD74A4C57A105F6C21B5A00591B2F307E0C
Certification-only primary key on airgap machine: true
PGP fingerprint (RSA): 0xA232750664CC39D61CE5D61536EBB4AB699A10EE
https://sks-keyservers.net/pks/lookup?op=get&search=0xA232750664CC39D61CE5D61536EBB4AB699A10EE
Certification-only primary key on airgap machine: true
“‘If you’re not doing anything wrong, you have nothing to hide.’
No! Because I do nothing wrong, I have nothing to show.” — nullius
-----BEGIN PGP SIGNATURE-----
iHUEARYKAB0WIQSNOMR84IlYpr/EF5vEJ5MVn575SQUCWqXCiwAKCRDEJ5MVn575
SWOqAQCbAtG6sQ9UDkrViVuEjAXMHbOEbuk/D7c/sq77s8woTwEAocoR1d0hr8EE
UOnIWtWmB6dfZs86E0SfGdJKSolQSAE=
=dNtc
-----END PGP SIGNATURE-----
With that, I myself join this campaign!
Meta: Why am I doing this? I am sufficiently passionate about PGP use that I would put on a live public sex show to promote it. For a serious discussion, see “ On the virtue of Ciphersex”. Moreover, I struggle with an internal conflict over signature advertising campaigns. I like signature ads (or at least tolerate them) when they make it worthwhile, or even make it possible for smart people to devote huge chunks of their lives to an Internet forum. I highly respect some people who carry paid sig ads. And I myself may come to face a pragmatic necessity for a paid signature ad. But I really dislike the concept. The old-school net curmudgeon in me feels that the purpose of a signature is for PGP fingerprints, witty quotes, and links to one’s own personal/business websites. It’s a matter of culture; and culture is pervasive. When I recently saw this opinion about how the forum thrived before paid signature advertising was invented—yes, I get it: Would you also be happy if all the signature campaigns are removed from the forum ? That will make all the merits and ranks useless than right.
Radical solution lol, most users would be done using this forum. Nonsense. Five years ago there were no signature campaigns, and bitcoin was worth a few dollars. This forum thrived back then. Part of my motive behind this campaign is to create at least a modicum of positive social counter-pressure against monetary incentives. Taking myself as an example: The amount of money I could already get for a sig ad is very significant to me. It’s painful not to take it. One reason why I thus far don’t, is that I look at my PGP key fingerprints—and I get sad. Negativity against sig ads is only one part: I feel a positive urge to keep what I already have there. Money needs to compete with something which has non-monetary value to me. I want to induce others to feel the same way. #endif /* !FOURTH_WALL */
End-User License Agreement: By copying, quoting, or even reading this post, you irrevocably signify your agreement to be forever bound by the following terms and conditions: /**
* ----------------------------------------------------------------------------
* "THE BEER-WARE LICENSE" (Revision 42):
* <nullius@nym.zone> wrote this file. As long as you retain this notice you
* can do whatever you want with this stuff. If we meet some day, and you think
* this stuff is worth it, you can buy me a beer in return. "Michael Cassio"
* ----------------------------------------------------------------------------
*/
Credits:
|
|
|
|
Any suggestions for Tor users whom a merchant redirects by https to a Bitpay invoice page? I previously followed the instructions on the pertinent Bitpay support page, as described upthread. Otherwise, Bitpay was inaccessible to me. Neither BIP 70 nor any other Bitcoin standard is involved. I soon will need to make a Bitcoin payment at a Bitpay-using merchant who works this way. Did you try the Bitpay suggestion of "Vanilla Firefox over Tor"? It seems they are claiming that in your situation, you should be able to complete the captcha and see your invoice using this setup: This captcha issue appears to be specific to the Tor browser bundle and not to Tor in general. Our team has tested and confirmed that vanilla Firefox over Tor presents the Cloudflare captcha correctly and allows users to proceed to payment.
I just tested this... and sure enough, The cloudflare captcha page is displayed in Firefox (over Tor) when the merchant redirects to " https://www.bitpay.com/i/TXID" and it redirected to the bitpay website after completing (NOTE: tested using egifter.com as it is the only bitpay merchant I know!) It would be just like Bitpay to make such a suggestion! Of course, I did not try this. Thanks for trying to help—but I must state the matter plainly: “Vanilla Firefox over Tor” will kill your privacy. “Vanilla Firefox” is highly distinguishable from Tor Browser. It reduces your anonymity set to the negligible number of people who use exactly the same Firefox on the same platform (with the same fonts, etc., etc.) through Tor—likely reducing your anonymity set to 1 right there. Even worse, it lacks Tor browser’s anti-fingerprinting features—almost certainly letting your anonymity set be reduced to 1. Although I am not affiliated with the Tor Project and can’t speak for them, I have spent enough time on Tor Project sites and mailing lists to know that their strictly stated official recommendation is to use only Tor Browser for web browsing through Tor. Please protect your privacy, and do not do this. I hope that you did not try it with any payment for which you have strong privacy or pseudonymity requirements.
Edit to add: I would not be surprised if Tor Browser’s fingerprinting resistance is exactly what “breaks” things here. Cloudflare loves to cavity-search your browser. Just an educated guess... caveat. |
|
|
|
I hereby suggest a forum remailer to integrate with and complement the PM system. Why? - Privacy. It is infeasible to use PGP for each and every PM. Good mail clients integrate neatly with PGP/GPG, making secure communications convenient and nearly transparent; but many forum users will decline to give out an e-mail address, even if I suggest a good e-mail provider for this purpose. A forum remailer would facilitate PGP use, provided that it must pass PGP/MIME without mangling it.
- Usability. The PM interface is—suboptimal, to put the matter politely. (Frankly, I hate it.) With e-mail, people have a choice of clients and can choose their own user interfaces.
- Resources. A remailer would only need to store spooled messages for long enough to pass them on to their destinations. The PM system must store messages for as long as a user desires not to delete them.
It is difficult for me to make a specific suggestion as to how this should work, when I do not know anything about the forum’s internals. Conceptually, I think a remailer could dovetail with the PM system. For receiving, users could choose to opt-in to the remailer—whereafter they would no longer receive PMs, and all remailed messages plus PMs would be (only) forwarded to their registered e-mail addresses. For sending, users could unilaterally send mail to uid@users.bitcointalk.org; the recipient would receive the message as a PM, or via the remailer if opted in for it. Note: The message format for “remailed” PMs would need to be much different from the format currently used for “new personal message” e-mail notifications. It would need to preserve formatting, respect MIME parts for messages sent to the uid@ address, and provide From/Reply-To information which would automatically cause replies to pass through the remailer. Making this non-ugly is actually the biggest practical problem I can think of. I have previously suggested this here in Meta, off-the-cuff: Re drafts - e.g. if I open a VM for Bitcointalk I will probably use it for a few days so good enough for me although TBH I'm not into long essays. Sometimes when I need to save it for longer I send it in a PM to myself.
PMs here are a disaster, in my opinion. Feature suggestion for a “crypto” forum: An opt-in remailer, which would let me send mail to suchmoon@users.bitcointalk.org—or maybe 234771@, since usernames here can contain charcters which are problematic. (Problematic, despite being allowed by the original RFC 822.) Spam could be curtailed by requiring SMTP envelope FROM the registered e-mail address, and obeying SPF records, etc. That way, I could use the very convenient PGP functionality of my mail client. Plus its drafts box.I should start a new Meta topic. Watch for it. |
|
|
|
RETRACTION In 2019, mailbox.org stopped accepting Bitcoin after Bitpay shutdown its operations in Germany. I hereby retract my review, which is left unedited below, for the record. This was insightful: Very interesting article nullius, thanks. I think the one Negative bit is just too much to overcome at the moment (BitPay). The issue with wanting a good service, especially one so important as a pseudonymous email, isn't with the price but with the ease of maintaining it. BitPay is impossible for me to use (and I want to avoid it anyway). Bitpay is is commonly known as “Shitpay”, for a reason—actually, for many reasons. Do you want to rely on it for your business? For business owners, including Heinlein Support GmbH (owners of mailbox.org), I suggest the following: - Best: In-house Bitcoin competency. However, I understand that not all businesses have this.
- Better: BTCPay Server, an open-source drop-in replacement that is API-compatible with Bitpay. It is almost like having an in-house Bitcoin expert set up your payment processing, but without the in-house Bitcoin expert.
- If you really cannot handle being your own bank: Use some outsourced Bitcoin payment acceptance that is not Bitpay.
mailbox.org users who needed Bitcoin payments have been left in the lurch. I should know. Don’t do that to your customers—your paying customers, who want to pay you money! In today’s Internet world, where freebies are demanded (and oft given under “you are the product” schemes à la Google), it is both common decency and business savvy to show your loyal paying customers the respect of not suddenly yanking Bitcoin payments out from under them.
Unedited original post follows:
This review is neither solicited, nor compensated. I have no affiliation with mailbox.org, other than as a happy customer.
It is no secret that I use mailbox.org: Their mailer hostnames are in the MX and related records for nym.zone, plus in the headers of all mail received from me (including by publicly archived mailing lists). Although mailbox.org is popular on some other “crypto” forums, the only discussion I could find here is a German thread from 2015. Thus, I wish to tell Bitcoin Forum users of my experience with this service. Rather than writing a wall of prose, I will reduce the major points to three separate bulleted lists: Positive, Neutral, and Negative.Note: mailbox.org offers a plethora of features, most of which are unused and untested by me. I can only review their core service: E-mail, sent from/downloaded to my own localhost. TL;DR: Overall, highly recommended for pseudonymous users who want reliable service and strong anti-spam for €1/month, payable in Bitcoin.
Positives:- Friendly to anonymous/pseudonymous customers. They explicitly state that “anonymous registration at mailbox.org is absolutely possible”. The only information they ask at signup is a name—which they explicitly hint that they cannot verify—plus a country for VAT reporting purposes (also unverifiable), and a language for the Web app user interface.
- Excellent anti-spam protection. The company which provides this service, Heinlein Support GmbH, does antispam as their bread and butter. I have been freely spreading my address nullius@nym.zone around the Web and on mailing lists, with no attempt to obfuscate it. I receive very little spam; and whatever spam I have recently received seems to be targeted to Bitcoin Forum users (ICO spam).
- Anti-spam system properly rejects with SMTP 5xx. No junk folder to silently eat false-positive messages! (I think they may (?) have recently added a “junk folder” option; but if so, it is optional and opt-in. Avoid.)
- .onion site, kqiafglit242fygz.onion, for access to POP, IMAP, and XMPP services—albeit not for the Web interface, which is necessary to control account settings and payment. They also run their own Tor exit, which can be pinned; I myself don’t do this. Their Tor information page discusses both their exit and their .onion.
- Reliable service. In my time as a customer thus far, I have never seen the service go down, or show any other signs of unreliability.
- Located in Berlin, Germany, without connection to the Land of the
Free NSL. Servers physically located in Berlin. Subject to German data protection laws. Clear Data Privacy Statement. - Well-established company. mailbox.org was started in 2013; but the people running it have been providing some form of network services since 1989 (!). The providing company has existed since 1992. In an era fraught with flaky startups, I feel more comfortable knowing that my e-mail will not likely disappear due to dumb hipster “founder” kids either flaking out, or getting “acqui-hired” by Google.
- TLS certificates verifiable through DANE. (Untested by me, since DANE does not work through Tor; I’d need to make as special effort.)
- Network-level communiations privacy between servers can help lessen the exposure of metadata (not protected by PGP) to network observers. To this end, mailbox.org attempts to use TLS for all incoming and outgoing SMTP sessions with other MXes. They also provide an option through which you may refuse all mail not sent over TLS; however, this can cause you to be unable to communicate with people who use incompetently managed mailservers.
All mailbox users also have a special alias which can only receive mail via SMTP over TLS; mine is <nullius@secure.mailbox.org>. If you want to test whether your mailserver can do outgoing TLS properly, try sending me a “hello” at that address, and see if it gets rejected! - Use your own domain. No extra charge. If you set up a domain with a catch-all alias, you can download mail, filter on envelope-recording headers, and inject it into your own local mail system.
- Reasonable prices. For those who download and delete mail, unless you need lots of aliases for domains, it should never be necessary to buy more than the €1/month service level with a 2 GB mail quota. Webmail users who need more space (or those who use the “Office” features I have not tested) have many other service options, all of which seem cost-effective for the resources provided.
- Paid service. Yes, that’s a positive. So-called “free” e-mail never is: If you’re not the (paying) customer, then you are the product. I am a mailbox.org customer.
- Payable in Bitcoin (but see negative below: Bitpay).
- 30-day free trial.
Neutral characteristics:- Webmail “Guard” PGP features. I myself do not use this, and have not tested it. I think that overall, against real-world threats, it looks about as trustworthy as Protonmail; yet it has the significant advantage that unlike Protonmail, you can use it to communicate with all PGP users in the world, not only local users of the same service. I think that this is a good “medium security” solution for people who need userfriendly webmail. I would recommend that paid Protonmail users switch, and save some money: For 5GB of quota, mailbox.org costs €2.50/month, whereas Protonmail costs €5/month (€4/month if paid annually). Those who need or desire high security MUST always use private keys which never in any way leave their own hardware. This German-language discussion seems savvy.
Side note: I myself would prefer to correspond with security experts who use their own keys on their own hardware. However, knowing one’s correspondent is integral to opsec; and I know that I can only assess the expertise of a correspondent by evaluating the human element. I would rather suggest that n00bs use mailbox.org Guard from their malware-infested PCs than try to tell them how to manage PGP private keys on the same computers from which their bitcoins get stolen.
Negatives:- Last-minute addition: Bitpay is currently broken in a way which will effectually prohibit Tor users.
- Bitpay. #NO2X, “WE WILL NEVER FORGET.” I don’t totally boycott all Bitpay services; but a service must be truly excellent for me to endure grinding my teeth whilst sending precious bitcoins to a Bitpay address. @mailbox.org, please consider setting up your own node!
- Even for POP/IMAP users, the Web interface must be used for account settings and payment purposes; and the Web interface requires Javascript, lots of Javascript. Besides being unfriendly to people who disable Javascript for security reasons, the gobs of Javascript are slow to download over Tor.
- Google CAPTCHA required (only) at signup. (They actually apologize for this on the signup page.)
- “Guard” PGP features (untested/unused by me) require some level of trust in mailbox.org. As said above, I think overall their setup looks about as safe as Protonmail. With Protonmail, the server could perform a targeted attack by provoding Javascript which phones home the decrypted private key; with mailbox.org Guard, the server decrypts the private key, and could keep it that way if desired. Really, what’s the substantive difference?
I will update this review if/as necessary from further experience with mailbox.org. Version history: 2018-03-11: Initial post. This thread is self-moderated for reason that due to experience with spam and trolls, I self-moderate all threads started by me unless there be a good reason to do otherwise. |
|
|
|
Does anyone have an updated solution for this matter? How to extract the normal form of a BTC adress from the bitcoin:?r=https://bitpay.com/i/TXID form? I have the same problem, does anyone have a solution? Enter your bitpay URL at https://decoder.bip70.org to get a normal BTC address to pay to. Remember to pay transaction fees on top of the amount given. Any suggestions for Tor users whom a merchant redirects by https to a Bitpay invoice page? I previously followed the instructions on the pertinent Bitpay support page, as described upthread. Otherwise, Bitpay was inaccessible to me. Neither BIP 70 nor any other Bitcoin standard is involved. I soon will need to make a Bitcoin payment at a Bitpay-using merchant who works this way. |
|
|
|
Hello guys, I m still using bitpay, and as of today - the noscript link doesnt work. Apparently their team isn t asleep and are working on fixing bugs that we could use to simplify our lifes.... Does anyone have an updated solution for this matter? How to extract the normal form of a BTC adress from the bitcoin:?r=https://bitpay.com/i/TXID form? Oh, no! The page which I referenced here: Bitpay’s support page for Tor users may currently bear the date of “January 04, 2018 02:28”; but it’s had substantially the same text for a very long time, including the same talk of “developing a fix” and an “immediate workaround”: ...now bears the updated date of “March 10, 2018 17:58”. And the only apparent difference is that more than half the page has been deleted. It still says, “There is an immediate workaround detailed at the bottom of this post.” But the “workaround” you report as non-working has now vanished down the memory hole! Evidently, they must know that their system is broken, and are choosing not to inform customers who visit that support page. ( Archive of current version. Unfortunately, I did not take an archive in January; and there does not seem to be one. Upthread, I quoted the pertinent portion from what is now missing.) This is a big problem. Unfortunately, many companies are still reliant on Bitpay. As a customer of other companies who sometimes needs to make payments through the horrid Bitpay, this could seriously affect me even though I never wanted anything to do with Bitpay. They had better fix their broken garbage. |
|
|
|
So, to Killyou72/73, what's the end game with this giant thread of accusations of people using merit in a way that others deem in appropriate? Are summarizing the list? Proposing some penalty? Preparing a review from the Admin crowd?
Perhaps I may be wildly wrong; but if I were a gambling man, I’d wager that the “end game” is to accrue evidence so that merit abusers can be permanently dyed blood-red. The merit system is most likely to be abused by those who seek rank primarily for financial gain; and negative trust is inimical to that objective. Thus, going out on a limb here, I mildly suggest that this sort of makes sense. In my humble opinion. Given that there is already such a penalty, I am moderately unsurprised by apparent lack of proposals here for another one. The longer this thread goes on with out action, the closer it gets to becoming a safe haven for spam.
Is there really inaction? Surf any trust pages lately? Also, where’s the spam? |
|
|
|
[Insert curse words here.]It means now we can use avatar campaign in the bounty. But what is the requirement of enabling the images in the profile. Newbie can now turn to Junior member in 30 days.
“cryptohacker29@”, what is the maximum price you would pay for an avatar?
@theymos, thank you for your wisdom in NOT making avatars a standard feature of Copper Membership.I must severely revise and correct what I said here:For personal use in an account expected to “rank up” normally within a few months, as I said in my post: When I was a Newbie Copper Member, I myself would have paid extra to sport an avatar—say, the equivalent of $10 more.
The business use case could be different. For example, consider a role account which functions as a fully disclosed alt, and mostly just does occasional announcements. Such an account may never reach Full Member status—and it certainly shouldn’t play evil games to bump up posts/merit for that purpose! At present, there exists no means at all for such an account to display a simple graphical business logo. For that use case, I think a fair avatar add-on price would be 50–100% of the current price of Copper Membership (thus making the total price 150–200% of Copper’s current price). If avatars are in-demand for bounty-chasers, then offering a reasonably inexpensive paid avatar option would likely increase the spam level. Forget what I said about a $10 avatar for personal use. Well-intended users will understand and appreciate the need to control incentives to spam. For ordinary accounts, people can just rank up. I’ll be proud to wear an avatar for the first time, just over 48 hours from now! New suggestion:Accounts at Full Member rank or higher should be able to grant an “avatar blessing” to accounts which they openly disclose as their alts. It would be reasonable to charge a modest, nonrefundable fee for the administrative overhead required to prevent this from being abused by account sellers (and/or people who would simply sell their “blessing”). An express condition of such a scheme must be that the “blessing” is only valid as long as the same person controls both accounts. Example use case (other than mine): For example,if i post ICO Project in Altcoin Announcements my images will not displayed if i don't pay this little fee?
Almost the same question here. If I buy this status can I start ANN with images? Yes, I have it on my organization profile. It works well for including images in posts. Best regards, Ben Otherwise, any paid avatar option must be made too expensive for people who are seeking free money. That should be balanced against not making it too expensive for individuals who are trying to bootstrap a small business on a shoestring budget ( cough). I think that at current rates, around 0.01 – 0.02 BTC would be a reasonable business-class expense (even for small business) while hopefully being cost-prohibitive to a Newbie who just wants to “use avatar campaign in the bounty”.
|
|
|
|
I am using firefox latest version, i didn't have a problem until yesterday, i have to solve 20 recaptcha and mind you i have to select sometimes street signs in a photo without any street signs! this is ridiculous and annoying.
For me it is slow to load and sometimes asks two or three times ... Also it is quite boring... Instead of traffic signs and roads and cars it could be about telling if it is a character from Star Trek or Star Wars ... or if it is a men´s or a woman´s legs or ...
Seriously, it is slow, but I don´t know if there is anything out there that offers the same level of safety and is faster.
As a Tor user, I quickly found the site totally unusuable when I was at Newbie rank. One fine day, after I was forced to try 17 (seventeen) different Tor circuits before I could even get a CAPTCHA thrown at me (!), I finally found a (not very good) workaround: Well, write off hours wasted trying to coerce fresh Tor Browser to do exactly what I wanted with my precious seventeenth-circuit login cookies (as recovered from the browser console). I finally gave up, and installed a persistent browser exclusively for Bitcointalk.org. After checking the appropriate boxes and “only” trying three circuits to get a CAPTCHA, I am now allegedly logged in until the year 2023; oh yes, I backed up those cookies! I thus hope to not be the canary in the CAPTCHA anymore; but I do care about this issue, and I will continue trying to adduce a workable solution. So... I suppose the least-evil current answer is, check the box to stay logged in; and back up those precious cookies! There, in this thread, and elsewhere, I have repeatedly made noises about a better solution: Any which way, if any popular forum has users who can handle public-key crypto, it should be Bitcointalk.org!
However, I never did the writeup I intended on a practical suggestion for achieving that. Back in early December, I hit a stone wall when I researched the topic. Sadly, idiot browser vendors have deprecated the <keygen> tag reasonably needed for userfriendly not horridly unfriendly setup of TLS client certificates. TLS client certs have other problems, too—not least of which is privacy toward other sites which could fish around for your bitcointalk.org cert; but what else is there? I thought of SSH tunnels, OpenVPN, ad hoc copypasting of challenges signed with a PGP or Bitcoin key... There are not any good options here. Another problem is, per my repeated inquiries upthread, the purpose of the login CAPTCHA is unclear. If, as I tend to presume, the purpose is to prevent online bruteforce of weak luser passwords (inevitably followed by “HELP CYRUS THEYMOS IM HACKED” threads), then pubkey auth would be an excellent solution. But if the purpose of the CAPTCHA is to inhibit mass login by spambots, as many others assume—well, then pubkey auth would fix nothing. If this is not a sensitive security question, I ask that theymos provide clarification.
half a month necro/
Half a month isn’t really necro, even for a less important thread; and this thread is very important. I hope that this thread will remain semi-active until a better solution is found. |
|
|
|
#HIPPOCRITE COPPER MEMBER Well, that’s amusing non sequitur. It will probably remain all the moreso if I don’t ask you to explain the relevance of my Copper Membership. Also amusing: Don't like my opinions so they left me negative feedback. But they are the one that had to buy "Whitelist" or a title. #HIPPOCRITE You don’t realize, I collect those petty little retaliations from petty little people. I haven’t earned one in awhile. Thanks. It may help your writing if you were to buy a dictionary, and learn the spelling and definition of the word “hypocrite”. Also, if you were not stupid. But that’s beside the point, given your reprehensible attitude. The merit system has a dual purpose, positive and negative. Its positive component is to reward people like me for making posts which others find valuable; the number below my name speaks for me on that point. Its negative component is to chase snowflakes like you away from the forum, so that you don’t spoil it for others. The system is doing its job, on both sides of the coin!
Edit to add: *plonk* (I believe these occasional public examples to be a social necessity; but now, there is nothing more to see here.) |
|
|
|
https://web.archive.org/web/20180311002810/https://bitcointalk.org/index.php?topic=2818350.msg32023727#msg32023727Fuck it. why not just buy merits. I mean if account sales are allowed, so should merit sales. For real, if Theymos can charge for being able to make more posts as newbie by buying a copper membership, why don't he just sale merit rank ups. Oh but it could never come to that could it? Before the Copper membership came around, that wasn't possible either was it? I don't know when he implemented buying whitelist, but that probably could have never happened either though before it did. SELL MERIT RANK UP'S THEYMOS Real Talk, I'd be interested in buying because I won't be able to. Yeah my posts aren't that great, I know that. But look through my history, I rarely do anything else but sell misc. digital items. EDITMerit me for this so once he does do this, I won't have to buy them  ; I’ve been slack lately, but no longer: #917001 “xBoxLive” advocated buying and selling of merits, *and* simultaneously begged for merit. FOR SHAME. As the Latin etymology of the word implies, *merit* is to be EARNED.
This feedback is made consistently with my trust feedback policy:
https://bitcointalk.org/index.php?topic=3009256.0
|
|
|
|
See also: Techniques to reduce transaction feesUse SegWit and enjoy lower fees (Giant-sized Segwit ad credit: ETFbitcoin.)
yup the price now of BITCOIN IS HIGH and I don't be surprised of the fees. my CONVERSION from 180 USD to btc is about 20 Dollars .. in my local money ranging form .00904636 coins. My earnings from ICO is just alloted to fees . Undecided exchanging tokens to eth to convert to BTC is just meh. fees are so high .same as me well and I think it is also a part of commission of exchanger sites fees are 0.001BTC
____C A S H B A G____ │ THE CASH BACK CRYPTOCURRENCY | Get it on Google Play
PRE-SALE OPEN | Get 40% Bonus
● WHITEPAPER ● TWITTER ● FACEBOOK ● TELEGRAM ● What you are describing are EXCHANGE FEES, not the Bitcoin miner’s fee. If your “CONVERSION” fee is high, then you are using an expensive EXCHANGE. Switch to a different EXCHANGE, and stop the ignorant whining about Bitcoin. Bitcoin’s own fees are low right now.Also, ICOs are all scams; thus, I am not surprised you don’t make much money there. I suggest that you drop the sigspam for a stupid shitcoin, and learn something about Bitcoin. Perhaps you may even come to know the difference between getting ripped off by an expensive exchange, and the Bitcoin transaction fee.
|
|
|
|
I think it's temporary and was probably implemented slightly quicker than the devs may have wanted due to the increased demand and work load over Xmas. Transaction congestion needed to be eased. Although long term a new solution will need to be found segwit is a needed aid even when operating in the way it does at the moment
This is what happens when you do what is politely called “making stuff up as you go along”, or more commonly referred to as pulling it out of your—nostrils. You should not spread misinformation like this. A two-phased migration to Segwit was planned at least as far back as 2015. After playing around with `git blame` on various parts of BIP 141, I finally just grabbed this early pre-BIP draft from the year 2015:https://github.com/bitcoin/bips/blob/a208f3de00a7a79cf5cdc1731b6f7d166e799e37/bip-codeshark-jl2012-segwit.mediawikiWallets will be able to migrate in two phases:
P2SH compatibility
Witness programs are hashed to 256 bit "redeemscripts" which are then hashed to 160 bit P2SH. This format is fully compatible with currently existing wallets that support P2SH. Upgraded wallets will be able to send and receive to and from older wallets without any problems.
Native outputs
Witness programs are hashed to a 256 bit output. This format will not be compatible with older wallets but will require less block space and will have better security due to increased collision resistance.
(Note: Do NOT rely on this document for any technical information about Segwit. It is an early draft, presented for historical purposes only. Much has changed. Refer to the final BIP 141 for technical information on the Segwit consensus layer.)Were I to dig further, I could find the original bitcoin-dev discussion of native Segwit vs. nested-in-P2SH. Segwit was designed thoughtfully, carefully, through the close cooperation of several of the best Bitcoin developers in the world. It could and should have been deployed much earlier than its eventual activation date of 24 August 2017. Segwit was delayed, and the whole Bitcoin network suffered detriment, because a canaille of world-class scammers spread malicious disinformation—the latter being backed up by patent ignorance such as you have here displayed. It is outrageous for you to suggest that anything in the design of Segwit was slapped together “due to the increased demand and work load over Xmas” (!). Moreover, what you say implies that Core has the amazing ability to travel in time: After several years of design and development, the consensus layer was activated 24 August 2017; yet due to demand “over Xmas”, they tossed out some temporary quick-fix? That itself shows how much you know whereof you speak ( i.e. NULL). |
|
|
|
Still asking about non-public communications with Alia on the date of 1 March 2018 (UTC).
You're being too evasive for your own good and making this whole story seem unnecessarily murky.
I use samouri which means I get a new address per transaction
Every reasonable modern wallet gives a new address for each transaction.
What's the exact BTC amount you sent to alia?
Edit: and the date?
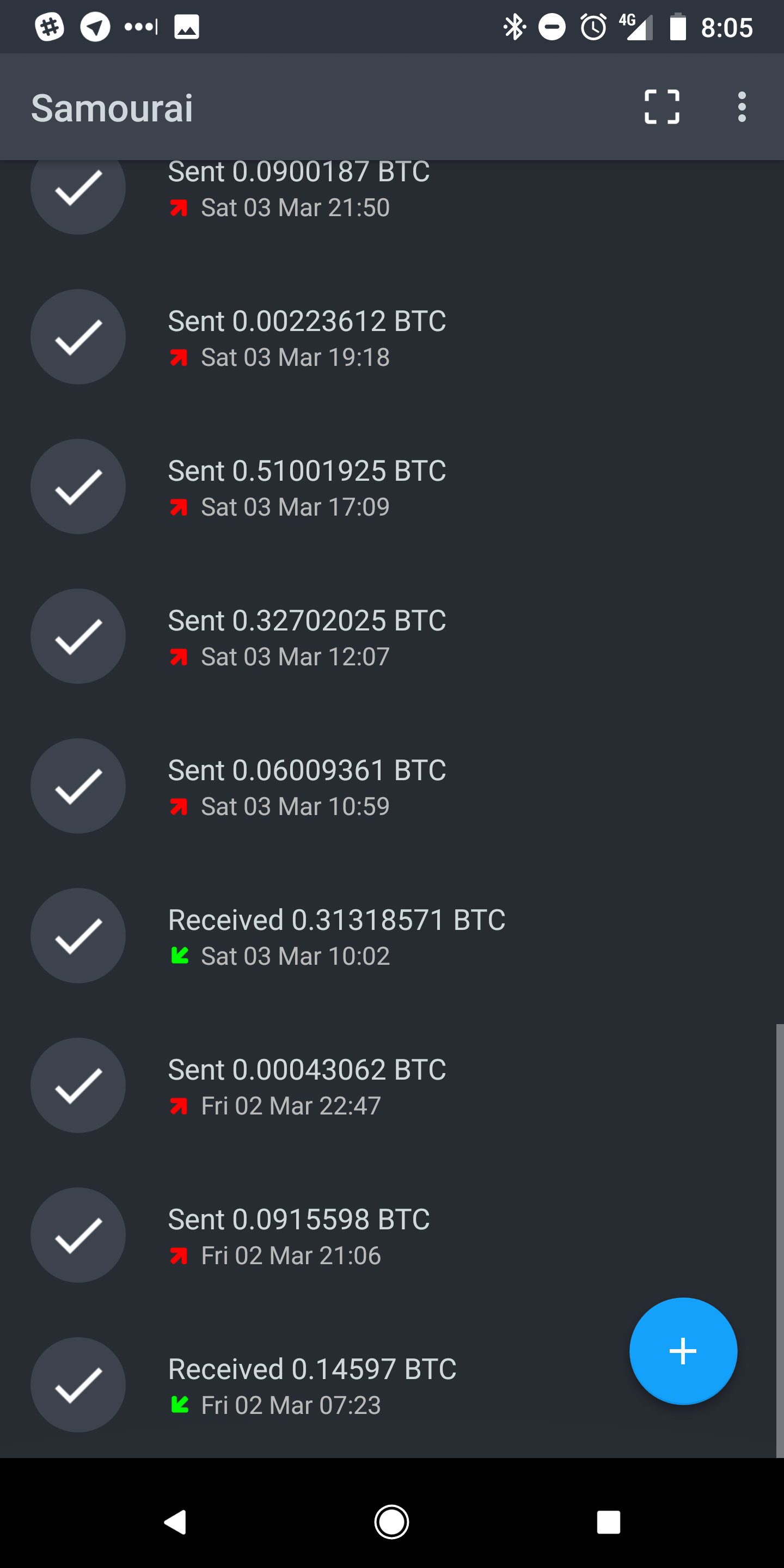
Lemme check... Not having access to past transactions isn't good. I also got to run in 40 minutes. No, it’s not good—especially if you have a business to run! What if someone denied receiving payment from you and accused you of scamming, and you needed to prove the tx? Would it be so difficult to produce a txid? What if one of your less-honest customers from various threads sees this, realizes you can’t see tx history before 2 March, and makes a false scam claim against you for a transaction before that? (Rhetorical questions.)
(Quoted out of order to not break up text flow with image.) Here is the screenshot I sent ibminer https://imgur.com/a/lHk6YEdit to add - the grey slider on the side shows that it's reached the end. For ease of reference:
|
|
|
|
|


 unless you can put a value on privacy, which I believe to be priceless.
unless you can put a value on privacy, which I believe to be priceless.