|
kkurtmann
|
 |
July 19, 2014, 09:06:05 PM |
|
good job, I was hoping for the (beer-proof) black one though
|
|
|
|
|
|
|
|
|
|
|
|
|
"With e-currency based on cryptographic proof, without the need to
trust a third party middleman, money can be secure and transactions
effortless." -- Satoshi
|
|
|
Advertised sites are not endorsed by the Bitcoin Forum. They may be unsafe, untrustworthy, or illegal in your jurisdiction.
|
|
|
|
stick
|
 |
July 20, 2014, 10:04:57 AM |
|
good job, I was hoping for the (beer-proof) black one though
The "First Edition" engraving looks SO much better on white one. |
|
|
|
|
AussieHash
|
 |
July 20, 2014, 11:13:30 AM |
|
good job, I was hoping for the (beer-proof) black one though
It would be awesome if we could choose black or white |
|
|
|
|
dnaleor
Legendary

 Offline Offline
Activity: 1470
Merit: 1000
Want privacy? Use Monero!

|
 |
July 20, 2014, 11:17:02 AM |
|
The thing is... I like the white 'clean' look, problem is that white can easily become dirty grey... But really, I want to use my Trezor  The color doesn't matter |
|
|
|
|
Kprawn
Legendary

 Offline Offline
Activity: 1904
Merit: 1073

|
 |
July 20, 2014, 11:52:10 AM |
|
Hope there are talks with Dell to incorporate the Trezor in the next version of their notebooks, seeing that they joined the Bitcoin wave now. I would like to something like this, be part of hardware, we use every day.  Once it's built in, a sticker must say, "Bitcoin enabled" That is my vision for Trezor. |
|
|
|
ghgr
Newbie

 Offline Offline
Activity: 59
Merit: 0


|
 |
July 20, 2014, 01:15:35 PM |
|
Good job! I hope to get one one day, too  What I couldn't find is the answer to the following two questions (or maybe it is buried somewhere in these 84 pages), not even in their official site: 1) What happens if someone steals the device, dumps its memory and bruteforce the 10000 PINs offline? Is the memory protected, like in a Smart Card? Is the encryption key hardened (like after 100,000 rounds of sha256? Or is it a race between the attacker and the owner to move the funds? 2) How is the interface Trezor-Computer? There must be bidirectional communication (to receive the unsigned transaction and send the signed back). How is it carried out? Is like a network interface? Does it simulate a keyboard, like the Yubikey? In this last case, how does Trezor receive the transaction from the computer? What is the worst that a compromised driver can do to the wallet? I would love to see these questions answered in the main site (since probably I am not the only one wondering this). For the rest, kudos to you two and keep up the good work! |
|
|
|
|
|
hibr3d
|
 |
July 20, 2014, 02:09:55 PM |
|
Very nice project right there! I am going to order one soon. This should stop BTC stealling from other's people' wallets.  |
|
|
|
|
klokan
|
 |
July 20, 2014, 06:26:15 PM |
|
Good job! I hope to get one one day, too  What I couldn't find is the answer to the following two questions (or maybe it is buried somewhere in these 84 pages), not even in their official site: 1) What happens if someone steals the device, dumps its memory and bruteforce the 10000 PINs offline? Is the memory protected, like in a Smart Card? Is the encryption key hardened (like after 100,000 rounds of sha256? Or is it a race between the attacker and the owner to move the funds? 2) How is the interface Trezor-Computer? There must be bidirectional communication (to receive the unsigned transaction and send the signed back). How is it carried out? Is like a network interface? Does it simulate a keyboard, like the Yubikey? In this last case, how does Trezor receive the transaction from the computer? What is the worst that a compromised driver can do to the wallet? I would love to see these questions answered in the main site (since probably I am not the only one wondering this). For the rest, kudos to you two and keep up the good work! 1/ To "dump this device memory" you need expensive laboratory equipment and time. I'm not sure how much time you have, but it should be enough to transfer the BTC if the device is lost/stolen. One more comment on this topic: You should still take care of the physical security yourself. But if you do, then with this device you can safely send/receive BTC what was not possible pre-Trezor, because you used (potentially) unsecure PCs. 2/ Thezor connects as Human Interface Device (HID) and sends Google protocol buffers over the USB wire. It does not need driver on PC. When it received data over USB, it parses and validates protobufs and invalid data are rejected. Interface does not allow private keys to leave the device so any valid reqest that is answered by the device cannot leak the keys. The worst what "malitious driver" can do is getting your public keys and btc adresses and it can send various requests to the device that will prompt you for pin entry and confirmation. These include: signing transactions or wiping the device. |
|
|
|
|
|
|
ghgr
Newbie

 Offline Offline
Activity: 59
Merit: 0


|
 |
July 20, 2014, 08:06:34 PM |
|
1/ To "dump this device memory" you need expensive laboratory equipment and time. I'm not sure how much time you have, but it should be enough to transfer the BTC if the device is lost/stolen. One more comment on this topic: You should still take care of the physical security yourself. But if you do, then with this device you can safely send/receive BTC what was not possible pre-Trezor, because you used (potentially) unsecure PCs.
Good to know that imaging the device is not as simple as plugging the internal memory (SD Card for example) into a PC and bruteforcing the PIN in seconds. I think that should be stated more clearly in the website. You say that the attacker would need expensive laboratory equipment, can you please be more specific, or point me to the doc where they describe this point? It would be important to discard this attack surface. In any case it would be a good idea to have another Trezor at home ready to send all the funds to a paper wallet, just in case the main one 'disappears'. 2/ Thezor connects as Human Interface Device (HID) and sends Google protocol buffers over the USB wire. It does not need driver on PC. When it received data over USB, it parses and validates protobufs and invalid data are rejected. Interface does not allow private keys to leave the device so any valid reqest that is answered by the device cannot leak the keys. The worst what "malitious driver" can do is getting your public keys and btc adresses and it can send various requests to the device that will prompt you for pin entry and confirmation. These include: signing transactions or wiping the device.
If the first point is solved, and considering that the integrity of the device can be verified by providing a test seed and checking the generated addresses, the only attack surface I can think of is the validation of the data sent by the computer to the device. I'll take a look at how Google's protobuf works. Is there any reason why they went with BIP 0032 instead of simply SHA256(SEED+idx) or similar? The added complexity of BIP 0032 is justified when we need 'watch only' wallets for example, but in the use case of Trezor, where there is a single user and the privates keys are not supposed to be leaked I don't understand the reason. Maybe they plan to allow Trezor to only receive payments, but not send them? (for example, for waiters in a restaurant). I find some points unclear in their FAQ. For example, how does the passphrase work? They only say that it sits "on top of the PIN". So am I supposed to write it in the computer's keyboard? Also, in their sentence "[...] we have implemented a safe way of entering PIN, so no keylogger can be used to spy on your PIN" there is no information. I finally found in reddit a video showing how the PIN input works (but not yet the passphrase). |
|
|
|
|
Anon136
Legendary

 Offline Offline
Activity: 1722
Merit: 1217

|
 |
July 20, 2014, 10:48:06 PM |
|
Password managers look totally silly and insecure compared to Trezor or similar devices. any plans to adapt them to this utility as well? i suppose the imputes would be more on software developers to adapt their software to work with trezors, but none the less there could be some collaboration. Perhaps I should have phrased this differently. Its great that you guys are making it imposable for hackers to steal bitcoins, but could this also be applied to make it possible to tie a facebook account to a single trezor so only the person with that trezor could ever access that facebook account? or insert any internet service that requires a login. If this is possible than would they need assistance from your end or could they just build software to meet this need around the hardware that you have designed? |
Rep Thread: https://bitcointalk.org/index.php?topic=381041If one can not confer upon another a right which he does not himself first possess, by what means does the state derive the right to engage in behaviors from which the public is prohibited? |
|
|
|
klokan
|
 |
July 20, 2014, 11:10:57 PM |
|
Good to know that imaging the device is not as simple as plugging the internal memory (SD Card for example) into a PC and bruteforcing the PIN in seconds. I think that should be stated more clearly in the website. You say that the attacker would need expensive laboratory equipment, can you please be more specific, or point me to the doc where they describe this point? It would be important to discard this attack surface.
In any case it would be a good idea to have another Trezor at home ready to send all the funds to a paper wallet, just in case the main one 'disappears'.
If the first point is solved, and considering that the integrity of the device can be verified by providing a test seed and checking the generated addresses, the only attack surface I can think of is the validation of the data sent by the computer to the device. I'll take a look at how Google's protobuf works.
Is there any reason why they went with BIP 0032 instead of simply SHA256(SEED+idx) or similar? The added complexity of BIP 0032 is justified when we need 'watch only' wallets for example, but in the use case of Trezor, where there is a single user and the privates keys are not supposed to be leaked I don't understand the reason. Maybe they plan to allow Trezor to only receive payments, but not send them? (for example, for waiters in a restaurant).
I find some points unclear in their FAQ. For example, how does the passphrase work? They only say that it sits "on top of the PIN". So am I supposed to write it in the computer's keyboard? Also, in their sentence "[...] we have implemented a safe way of entering PIN, so no keylogger can be used to spy on your PIN" there is no information. I finally found in reddit a video showing how the PIN input works (but not yet the passphrase).
1/ To read flash of MCU, you need to open it and read it under the microscope. This article is quite old, but gives an idea what needs to be done: http://www.bunniestudios.com/blog/?page_id=40 . Trezor uses STM32F205RE MCU but I did not find anything specific for it online. 2/ https://code.google.com/p/nanopb/3/ BIP32 allows you to do a lot of cool stuff with a single device. You can have unlimited number of accounts for various crypto-currencies and those don't share the same addresses. You can support message signing, secure login and more. Also, BIP44 provides extensible, secure and standardized way of doing things right instead of doing single-purpose hack to make things work. These standards for example promote no-reuse of addresses, something many multi-sig approaches don't have. Also, this allows offline account discovery. I.e. once your account public BIP32 node is stored in your PC, you don't need your Trezor connected to see the balance. 4/ I agree that the passphrase functionality should be better documented. |
|
|
|
|
Anon136
Legendary

 Offline Offline
Activity: 1722
Merit: 1217

|
 |
July 20, 2014, 11:21:07 PM |
|
You can support message signing, secure login and more. that would appear to have answered my question. thanks. |
Rep Thread: https://bitcointalk.org/index.php?topic=381041If one can not confer upon another a right which he does not himself first possess, by what means does the state derive the right to engage in behaviors from which the public is prohibited? |
|
|
|
|
|
cor
|
 |
July 21, 2014, 08:02:49 PM |
|
I find some points unclear in their FAQ. For example, how does the passphrase work? They only say that it sits "on top of the PIN". So am I supposed to write it in the computer's keyboard? Also, in their sentence "[...] we have implemented a safe way of entering PIN, so no keylogger can be used to spy on your PIN" there is no information. I finally found in reddit a video showing how the PIN input works (but not yet the passphrase).
We are working on a better documentation for the users, so here you go: Multi-passphrase encryption (hidden volumes)Security researchers have a habit of coming up with spicy names for simple attacks. One such attack is referred to as the $5 wrench attack. 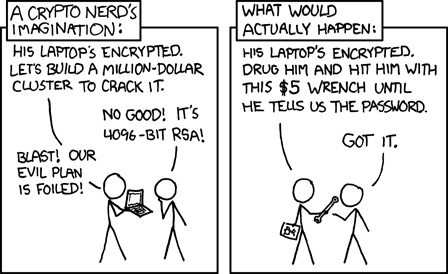 If you have your passphrase memorized and you haven’t written it down anywhere, attackers with physical access to your TREZOR may still be able to extract the passphrase with a $5 wrench. In order to mitigate this risk it is possible to set up your TREZOR multiple times with multiple passphrases. The goal is to have one “spoof” setup that only holds a few bitcoins or bitcents and one “real” setup that holds your fortune. In order to do this all you need to do is setup your TREZOR with a passphrase, then unplug and replug your TREZOR and enter a different passphrase. Here’s an example: I setup my TREZOR with the passphrase “lonelypumpkins” and load a large number of bitcoins onto my device. I unplug/replug my TREZOR and enter the passphrase “funnyspirit”. I then send a few bitcents to the “funnyspirit” account. When the thugs come and steal my TREZOR, I can now safely tell them that my passphrase is “funnyspirit”. They will be able to steel a few bitcents from me, but they won’t be able to get at my fortune or even determine that a second passphrase exists. PIN entry in TREZOR will be explained as well. Meanwhile to get an idea you can watch a video done by molecular https://www.youtube.com/watch?v=vMUfDKfsMFI |
|
|
|
molecular
Donator
Legendary

 Offline Offline
Activity: 2772
Merit: 1019

|
 |
July 21, 2014, 08:06:12 PM |
|
The thing is... I like the white 'clean' look, problem is that white can easily become dirty grey...
don't you love the aged beige of old IBM pcs? |
PGP key molecular F9B70769 fingerprint 9CDD C0D3 20F8 279F 6BE0 3F39 FC49 2362 F9B7 0769
|
|
|
molecular
Donator
Legendary

 Offline Offline
Activity: 2772
Merit: 1019

|
 |
July 21, 2014, 08:09:41 PM |
|
Good job! I hope to get one one day, too  What I couldn't find is the answer to the following two questions (or maybe it is buried somewhere in these 84 pages), not even in their official site: 1) What happens if someone steals the device, dumps its memory and bruteforce the 10000 PINs offline? Is the memory protected, like in a Smart Card? Is the encryption key hardened (like after 100,000 rounds of sha256? Or is it a race between the attacker and the owner to move the funds? pro tip regarding this: it is possible to setup a passphrase that is "added" to the seed (you have to enter this on the wallet host). That way the passphrase has to be brute-forced, too (or key-logged beforehand). That passphrase is not stored on trezor. You can even use multiple different ones (resulting in different wallets) for plausible deniability. |
PGP key molecular F9B70769 fingerprint 9CDD C0D3 20F8 279F 6BE0 3F39 FC49 2362 F9B7 0769
|
|
|
|
xeroc
|
 |
July 21, 2014, 08:13:14 PM |
|
pro tip regarding this: it is possible to setup a passphrase that is "added" to the seed (you have to enter this on the wallet host). That way the passphrase has to be brute-forced, too (or key-logged beforehand). That passphrase is not stored on trezor. You can even use multiple different ones (resulting in different wallets) for plausible deniability.
AWESOME!!!! |
|
|
|
|
|
cor
|
 |
July 21, 2014, 08:22:52 PM |
|
The thing is... I like the white 'clean' look, problem is that white can easily become dirty grey...
don't you love the aged beige of old IBM pcs? The plastic material we use for trezor is of a good quality and should be color-stable so I hope (and we were promised) white won't turn beige. Anyway I have a black notebook and it's getting light-grey dirty all the time. I also have a white phone and it looks ehmm lets say not white after few months. But that's something i throw in my bags with a lot of ladies' stuff. Most Trezor users will be very organized and will keep their devices in a nice clean and safe place  Just kidding... Simply, use a PC cleaning wipe if trezor gets dirty. |
|
|
|
molecular
Donator
Legendary

 Offline Offline
Activity: 2772
Merit: 1019

|
 |
July 21, 2014, 08:29:39 PM |
|
In order to mitigate this risk it is possible to set up your TREZOR multiple times with multiple passphrases.
The goal is to have one “spoof” setup that only holds a few bitcoins or bitcents and one “real” setup that holds your fortune.
better make that 2 spoof setups. ;-) |
PGP key molecular F9B70769 fingerprint 9CDD C0D3 20F8 279F 6BE0 3F39 FC49 2362 F9B7 0769
|
|
|
|




